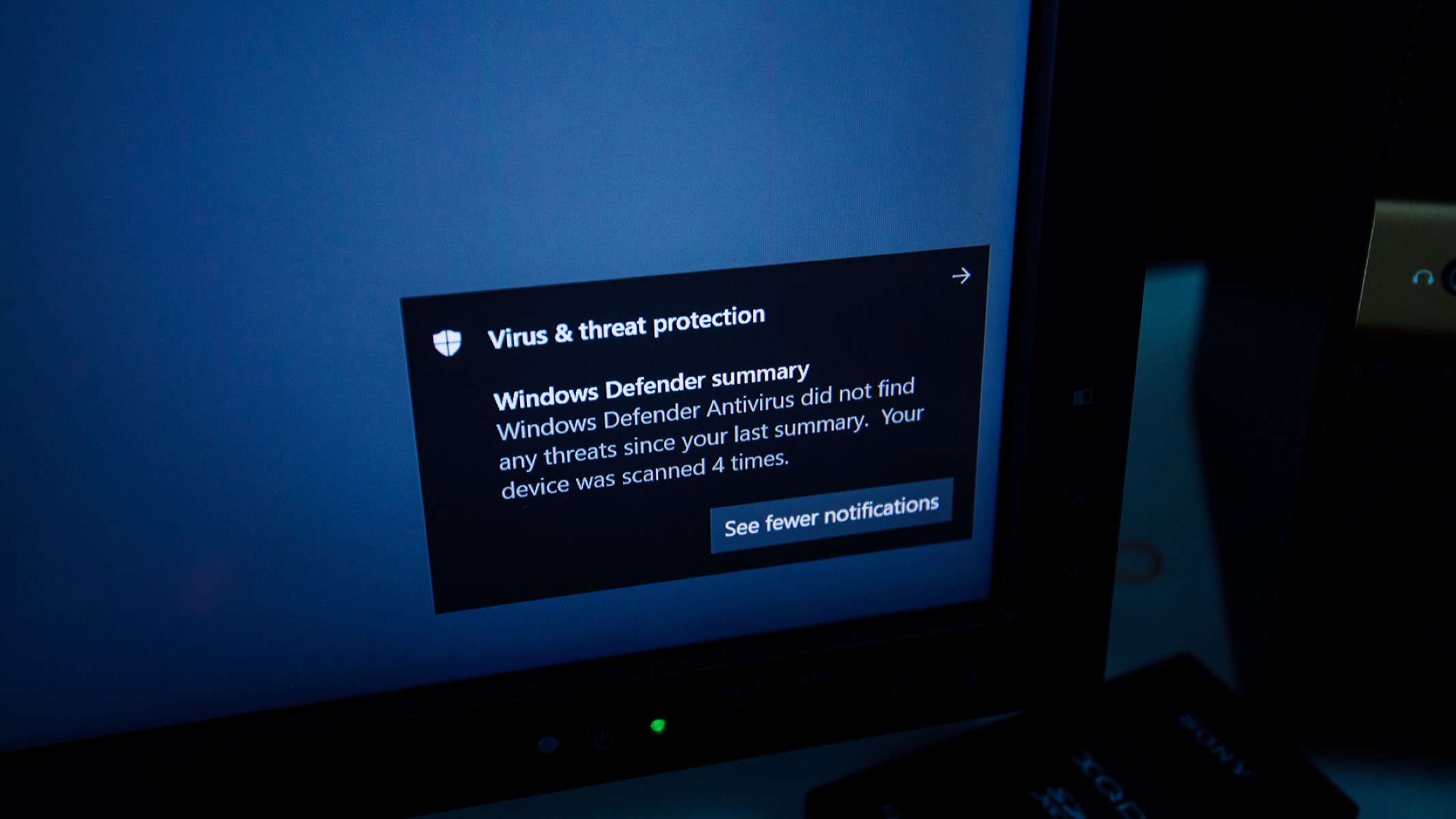
Install an Antivirus Program
Protecting your device from malware starts with installing a reliable antivirus program. Antivirus software is designed to detect and remove malicious software, such as viruses, worms, and trojans, from your computer or mobile device. Here are some important steps to follow when installing an antivirus program:
- Research and choose a reputable antivirus software provider. Look for well-known brands with positive reviews and a proven track record in providing strong malware protection.
- Visit the official website of the antivirus software provider and download the latest version of the program.
- Run the downloaded installer file and follow the on-screen instructions to complete the installation process.
- Once the installation is complete, launch the antivirus program and navigate to the settings. Ensure that the program is set to automatically update virus definitions and perform regular scans.
- Perform a full system scan to check for any existing malware on your device. If any threats are detected, follow the instructions provided by the antivirus program to remove them.
- Keep your antivirus program up to date by regularly installing the latest updates and patches provided by the software provider.
- Configure the antivirus program to run in the background, providing real-time protection against malware threats.
Remember, installing an antivirus program is just the first step. To ensure maximum protection, it is essential to keep your antivirus software updated and perform regular system scans. Additionally, combine this with other cybersecurity measures such as enabling a firewall, using strong and unique passwords, and being cautious when downloading files or visiting websites.
Update Your Operating System
Keeping your operating system up to date is crucial in protecting your device from malware attacks. Software developers regularly release updates and patches to fix security vulnerabilities and enhance the overall performance of the operating system. Here are some reasons why updating your operating system is important:
- Security: One of the primary reasons to keep your operating system updated is to ensure optimal security. Hackers and cybercriminals are constantly developing new methods to exploit vulnerabilities in outdated software. By installing updates, you can protect your device from potential malware threats.
- Stability: Operating system updates not only address security issues but also improve the stability of your device. Updates often include bug fixes and performance enhancements, resulting in a smoother and more reliable user experience.
- New Features: Updates often introduce new features and functionalities to your operating system, providing you with an enhanced computing experience. These features may include improved system performance, updated user interfaces, or additional security measures.
- Compatibility: Updating your operating system ensures that your device remains compatible with newer software versions and applications. Without updates, you may encounter compatibility issues that hinder the proper functioning of certain programs.
- Peace of Mind: By regularly updating your operating system, you can have peace of mind knowing that you are taking proactive measures to protect your device and personal information.
To update your operating system, follow these steps:
- On Windows: Click on the Start button, go to Settings, and click on Update & Security. Select Windows Update, and if updates are available, click on the Update button to install them.
- On Mac: Click on the Apple menu, go to System Preferences, and select Software Update. If updates are available, click on the Update Now button to install them.
- On Mobile Devices: Visit the Settings app and navigate to the Software Update section. If updates are available, follow the on-screen instructions to install them.
Remember to check for updates regularly and enable automatic updates whenever possible. This ensures that your operating system remains up to date, providing you with the latest security patches and enhancements.
Enable Firewall Protection
A firewall acts as a barrier between your device and the internet, monitoring and controlling incoming and outgoing network traffic. It acts as the first line of defense against unauthorized access and potential malware threats. Enabling firewall protection can greatly enhance the security of your device. Here are some key points to consider:
- Hardware Firewalls: Many routers and modems come with built-in firewall protection. Ensure that your router’s firewall is enabled by accessing the router’s configuration page. Consult your router’s manual or the manufacturer’s website for specific instructions.
- Software Firewalls: In addition to hardware firewalls, you can also enable software firewalls on your device. Most operating systems, such as Windows and macOS, have built-in firewall functionality that can be enabled through the system settings.
- Configuring Firewall Settings: Once enabled, it is essential to configure the firewall settings to suit your needs. You can choose to allow or block specific applications or specify network access rules for certain ports and protocols. Consult your firewall’s documentation or seek assistance from a knowledgeable source to properly configure your firewall settings.
Firewalls work by analyzing incoming and outgoing network traffic based on established rules and policies. They block suspicious connections and traffic that may potentially be harmful to your device. While a firewall can provide significant protection, keep in mind that it is not infallible. It is important to follow safe browsing and downloading practices and have additional layers of security in place.
Remember, enabling a firewall alone is not enough to guarantee your device’s security. It is crucial to keep your firewall software up to date and regularly check for updates from your firewall provider. Additionally, consider using a combination of antivirus software, strong passwords, and practicing caution when browsing the internet to maximize your overall security.
Use a Web Filter
Using a web filter is an effective way to protect your device and network from accessing potentially harmful or inappropriate websites. A web filter is a software or hardware tool that allows you to enforce browsing policies, block access to specific categories of websites, and prevent users from accidentally or intentionally visiting malicious or inappropriate sites. Here are some reasons why using a web filter is important:
- Malware Protection: Web filters can block access to websites known for distributing malware or engaging in phishing activities. This helps to prevent your device from becoming infected with harmful software that can compromise your sensitive information.
- Content Filtering: Web filters allow you to control the content that can be accessed on your device or network. This is particularly useful in environments like schools or workplaces, where there may be a need to restrict access to certain websites that are deemed inappropriate or non-productive.
- Parental Control: Web filters provide an effective tool for parents to monitor and control their children’s internet usage. By filtering out explicit, violent, or otherwise inappropriate content, parents can ensure a safer online experience for their children.
- Bandwidth Optimization: Web filters can help optimize network bandwidth by blocking access to resource-intensive websites or online activities, such as streaming video or file sharing. This ensures that network resources are allocated efficiently and that critical business operations are not disrupted.
- Regulatory Compliance: Some industries, such as healthcare or finance, have regulatory requirements that necessitate the implementation of web filtering measures. Using a web filter can help organizations comply with these regulations and protect sensitive customer data.
When choosing a web filter, consider the following:
- Features: Look for a web filter that offers a wide range of filtering options, including category-based filtering, keyword blocking, and real-time content analysis.
- Customization: Ensure that the web filter allows you to customize the filtering settings according to your specific needs. This includes the ability to create whitelists and blacklists and set filtering levels based on user profiles.
- Updates and Support: Regular updates are crucial for a web filter to effectively block new and emerging threats. Choose a web filter that provides regular updates and ongoing technical support.
Implementing a web filter in your device or network can provide an additional layer of security and control over internet access. By filtering out malicious or inappropriate content, you can protect your device and network from potential threats, ensure compliance with regulations, and create a safer online environment for yourself or your organization.
Be Mindful of Downloading and Opening Attachments
Downloading and opening email attachments or files from unfamiliar sources can expose your device to malware and other security threats. It is crucial to exercise caution and follow best practices when dealing with attachments to protect your device and personal information. Here are some important guidelines to keep in mind:
- Verify the Source: Before downloading an attachment, ensure that it is from a trustworthy and legitimate source. Be wary of emails or messages from unknown senders or those that appear suspicious or unsolicited.
- Scan for Malware: Use an antivirus program to scan attachments for potential malware before opening them. Even if an attachment seems legitimate, it is essential to perform a scan to detect any hidden threats.
- Be Skeptical of Email Attachments: Exercise caution when opening email attachments, especially if the email is unexpected or appears to be phishing. Be wary of attachments with file types commonly associated with malware, such as .exe or .vbs files.
- Don’t Trust File Extensions: Hackers often disguise malicious files by manipulating their file extensions. Avoid solely relying on file extensions to determine if an attachment is safe. Instead, verify the file’s integrity and authenticity through reliable sources.
- Avoid Unsecured Websites: Be cautious when downloading files from unsecured websites. Stick to reputable sites, such as official software providers or trusted online stores, to minimize the risk of downloading infected files.
- Keep Software Updated: Ensure that your operating system and applications, especially those used for handling attachments, are up to date. Developers regularly release security patches and updates to address vulnerabilities.
- Backup Your Data: Before opening any unfamiliar attachments, make sure to back up your important files. This will help protect your data in case of accidental malware infection or data loss.
- Use Online File Scanners: If you are unsure about the safety of a particular file, utilize online file scanning services. These services allow you to scan suspicious files for malware without having to download them.
By following these guidelines and being vigilant when it comes to downloading and opening attachments, you can significantly reduce the risk of malware infection and protect your device and personal information from potential security threats.
Enable Automatic Scans and Updates
Enabling automatic scans and updates is a crucial step in maintaining the security of your device and protecting it from malware. By automating these processes, you ensure that your software and antivirus program are always up to date and that regular scans are performed to detect and remove any potential threats. Here are some important considerations:
- Automatic Scans: Configure your antivirus software to automatically perform regular system scans. These scans help identify and eliminate any malware that may have infected your device, even if you are not actively using it.
- Scheduled Scans: Set up scheduled scans at convenient times when your device is typically idle, such as overnight or during non-working hours. This way, the process does not interfere with your regular activities and ensures thorough scans without interruption.
- Real-Time Protection: Enable real-time protection in your antivirus software. This feature continuously monitors incoming and outgoing files, emails, and web traffic, flagging any suspicious activity or potential malware.
- Automatic Updates: Enable automatic updates for your operating system, antivirus software, and other critical applications. Developers release updates to address security vulnerabilities and fix bugs that can be exploited by malware. Regular updates help ensure that your software is equipped with the latest security patches.
- Push Notifications: Configure your antivirus software to send push notifications or alerts whenever it detects a potential threat or when an update is available. This way, you stay informed about any security issues and can take immediate action.
- Keep Your Device Powered On: To ensure that automated scans and updates are performed as scheduled, keep your device powered on or in sleep mode during the designated time slots. This allows the software to run its tasks without interruption.
Enabling automatic scans and updates is a proactive measure that reduces the risk of malware infection and keeps your device protected. By maintaining the latest security updates and regularly scanning for potential threats, you enhance your device’s overall security and minimize the chances of falling victim to malware attacks.
Educate Yourself on Safe Online Practices
Knowledge about safe online practices is essential in protecting yourself and your device from malware and other cybersecurity threats. By educating yourself on how to navigate the online world securely, you can minimize the risk of falling victim to phishing attempts, malware downloads, and other online scams. Here are some key points to consider:
- Recognize Phishing Attempts: Be vigilant when it comes to suspicious emails, messages, or websites that may try to trick you into revealing personal information. Look for red flags such as misspellings, grammatical errors, and unfamiliar senders.
- Use Strong and Unique Passwords: Create strong, complex passwords for your online accounts. Avoid using easily guessable information such as birthdates or names. Additionally, use a unique password for each account to prevent unauthorized access if one of your passwords is compromised.
- Enable Two-Factor Authentication: Utilize two-factor authentication whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a fingerprint or a unique code sent to your mobile device, to access your accounts.
- Avoid Clicking on Suspicious Links: Be cautious when clicking on links in emails, messages, or on websites. Hover over the link to see the actual URL before clicking, and only click on links from trusted sources.
- Update Your Privacy Settings: Review and adjust the privacy settings on your social media platforms and other online accounts. Limit the amount of information you share publicly and only connect with people you trust.
- Be Cautious When Downloading Apps: Before downloading apps to your device, especially from third-party sources, read reviews, check permissions, and ensure the app is from a reputable source.
- Secure Your Wi-Fi Network: Protect your home Wi-Fi network with a strong password and encryption. Regularly change the default login credentials for your router to prevent unauthorized access.
- Regularly Review Bank and Credit Card Statements: Keep an eye on your bank and credit card statements for any unauthorized transactions. Report any suspicious activity to your financial institutions immediately.
Staying informed and continuously educating yourself about safe online practices is crucial as cyber threats evolve over time. Regularly keep yourself updated on the latest security tips, news, and best practices to protect your personal information and maintain a secure online presence.
Utilize Browser Security Features
Your web browser offers built-in security features that can help protect you from online threats. By taking advantage of these features, you can enhance your browsing security and minimize the risk of malware infections and unauthorized access to your personal information. Here are some key browser security features to utilize:
- Enable Pop-up Blockers: Pop-up windows can be used to display misleading ads or even spread malware. Enable your browser’s pop-up blocker to prevent these windows from appearing and potentially compromising your device’s security.
- Use Phishing and Malware Detection: Many modern browsers have built-in phishing and malware detection systems. These features alert you if you visit a known phishing website or attempt to download a file that could potentially contain malware.
- Keep Your Browser Up to Date: Regularly update your browser to the latest version to ensure that you have the most up-to-date security patches and features. Developers release these updates specifically to address security vulnerabilities.
- Manage Privacy and Security Settings: Review your browser’s privacy and security settings and customize them according to your preferences. Adjust cookie and tracking settings, enable Do Not Track, and consider blocking third-party cookies to protect your online privacy.
- Utilize Incognito/Private Browsing Mode: When browsing in incognito or private mode, your browser does not store your browsing history, cookies, or form data. This can be useful when accessing sensitive information or when using public computers.
- Disable Auto-fill and Saved Passwords: While convenient, auto-fill and saved password features can pose a security risk if your device falls into the wrong hands. Disable these features to prevent unauthorized access to your personal accounts.
- Consider Browser Extensions and Add-ons: Browse the available browser extensions and add-ons to enhance your security. Consider installing reputable ad-blockers, antivirus toolbars, or script blockers to further protect your browsing experience.
- Use HTTPS: Look for the padlock icon in the address bar and make sure the website you are visiting uses HTTPS (Hypertext Transfer Protocol Secure). This encryption protocol ensures that data exchanged between your browser and the website is secure.
By utilizing these browser security features, you can significantly enhance your online security. However, it is important to note that these features do not provide foolproof protection. Practicing safe browsing habits, keeping your devices and software updated, and using additional security tools such as antivirus software are crucial for maintaining a safe online experience.
Regularly Back Up Your Data
Regularly backing up your data is a crucial step in safeguarding your information and protecting it from loss or damage. Unexpected events such as hardware failure, malware infections, or accidents can result in data loss, but having backups ensures that you can recover your important files. Here are some reasons why regularly backing up your data is essential:
- Data Protection: Backing up your data protects it from accidental deletion, hardware failure, or natural disasters. It serves as a safety net, ensuring that you can recover your important documents, photos, videos, and other critical files if something happens to your device.
- Malware Recovery: In the unfortunate event of a malware infection, having recent backups allows you to restore your system to a previous clean state. This helps mitigate the damage caused by malware and prevents the loss of valuable data.
- Easy Transition to New Devices: When upgrading to a new device, having backups simplifies the process of transferring your data. You can easily restore your files and settings to the new device, allowing for a smooth transition.
- Accidental File Deletion: We all make mistakes, and accidental file deletion can happen. By regularly backing up your data, you can easily restore accidentally deleted files without much hassle or stress.
- Ransomware Protection: Ransomware attacks encrypt your files and demand payment for the decryption key. By having backups, you can avoid paying the ransom and restore your files from a safe and secure backup source.
Here are some best practices for backing up your data:
- Automate Backups: Set up automatic backup schedules to ensure that your data is consistently and regularly backed up without requiring manual intervention.
- Use External Storage: Utilize external hard drives, USB flash drives, or network-attached storage (NAS) devices to create backups. These physical storage devices provide an additional layer of protection against data loss.
- Cloud Storage: Take advantage of cloud storage services such as Google Drive, Dropbox, or OneDrive to store your important files. Cloud storage offers convenience, accessibility, and redundancy, as your data is replicated across multiple data centers.
- Verify and Test Backups: Regularly verify and test your backups to ensure that they are functioning correctly and that you can successfully restore your data if necessary.
- Keep Multiple Copies: Maintain multiple copies of your backups, including at least one offsite or in the cloud. This provides protection against physical damage or loss of your primary backup device.
Remember, data loss can occur at any time, so it is crucial to regularly back up your important files. By implementing a consistent backup routine and following best practices, you can maintain the security of your data and minimize the impact of unexpected events.
Be Wary of Suspicious Websites and Pop-ups
Navigating the internet can expose you to various threats, including malicious websites and pop-ups. It is crucial to exercise caution and be vigilant when interacting with unfamiliar websites or encountering pop-up windows. Being wary of these elements helps protect your device and personal information from potential malware infections and online scams. Here are some key points to consider:
- Verify Website Security: Before entering sensitive information or making online transactions, ensure that the website you are visiting is secure. Look for the padlock icon in the address bar and a URL that starts with “https://” which indicates an encrypted connection.
- Check for Trustworthy Sources: Stick to reputable websites and avoid clicking on links shared through suspicious emails, social media posts, or unfamiliar sources. These may lead to phishing websites or malicious downloads.
- Avoid Suspicious Websites: Be cautious when visiting websites that offer illegal downloads, pirated content, or suspicious offers. These websites are often host to malware or other harmful elements that can compromise your device’s security.
- Exercise Caution with Pop-ups: Be cautious when encountering pop-up windows, especially those that prompt you to download or install software, claim you have won a prize, or ask for personal information. Close pop-ups that appear suspicious or unexpected.
- Use Pop-up Blockers: Enable your browser’s pop-up blocker or install a reputable ad-blocking extension to prevent unwanted pop-ups from appearing. These tools help reduce the risk of inadvertently clicking on malicious or deceptive pop-up windows.
- Keep Your Browser Updated: Regularly update your browser to benefit from the latest security patches and enhancements. Developers frequently release updates to address vulnerabilities and protect against emerging threats.
- Use Browser Security Extensions: Consider utilizing browser security extensions that provide additional protection against malicious websites and pop-ups. These extensions can block known malicious sites, warn you about potential threats, and enhance your overall browsing security.
- Maintain a Security Mindset: Be skeptical and trust your instincts when browsing the internet. If something seems too good to be true or appears suspicious, it’s best to avoid engaging with it and exit the website or pop-up window.
By being cautious and vigilant when encountering suspicious websites and pop-ups, you can significantly reduce the risk of falling victim to malware infections, phishing attempts, and other online scams. Regularly updating your browser, utilizing security extensions, and practicing safe browsing habits are essential for maintaining a secure online experience.