What is a Hidden File?
A hidden file is a file or folder that is not displayed or easily accessible to users through the usual file browsing interfaces. These files are purposely kept hidden to prevent accidental modification or deletion, protect sensitive information, or maintain system integrity.
When a file is hidden, it remains present on the system but is not visible in regular file listings. The file is typically marked with a specific attribute that tells the operating system to omit it from view. This attribute can be set by the system or by the user.
Hidden files often have names that begin with a period (.) on Unix-based systems or have the “hidden” attribute enabled on Windows systems. While hidden files are not immediately visible, they can still be accessed and manipulated by users or programs that know their location or have the appropriate permissions.
Hidden files can contain a wide range of data, including configuration files, sensitive user information, system files, or files related to installed applications. These files may also include temporary files, cache data, or backup files that are not intended for direct user access.
It’s important to note that hidden files are not inherently malicious or dangerous. They exist to serve specific purposes and can be essential for the proper functioning of an operating system or installed software.
In certain cases, hidden files may also be used by applications to store user-related data or application-specific settings that users don’t need to see or modify directly. This helps maintain a clean and clutter-free user interface while keeping important files tucked away and out of sight.
Why Are Some Files Hidden?
There are several reasons why files are hidden on a computer or any other digital device:
- Protection of sensitive information: Hidden files are often utilized to store sensitive data, such as passwords, financial information, or personal documents. By hiding these files, users can add an extra layer of security against unauthorized access.
- Prevention of accidental modification or deletion: Sometimes, certain files or folders need to be protected from accidental changes or deletion. Hiding them reduces the likelihood of accidentally altering or deleting important system files or crucial user data.
- Maintaining system integrity: Certain system files or configurations are hidden to prevent users from modifying them unintentionally. These hidden files help maintain the stability and functionality of the operating system or installed software.
- Organizational purposes: Hidden files can also be used for organizational purposes. By hiding files that are not frequently accessed or are system-related, users can keep their file browsing interfaces clean and reduce clutter.
- Managing system performance: Some hidden files are used to store temporary data or cache files. These files are not typically meant for direct user access but serve important functions, such as speeding up application startup or improving overall system performance.
The decision to hide files ultimately depends on the needs and preferences of the user. While hidden files do provide benefits in terms of security, organization, and system performance, it is important to remember that they can also pose risks if mishandled.
Understanding why some files are hidden helps users make informed decisions and take appropriate actions when it comes to managing their digital files and maintaining the overall health and functionality of their devices.
How Are Files Hidden?
Files can be hidden on a computer or digital device using various methods and techniques. Here are some common ways in which files are hidden:
- Setting the hidden attribute: One way to hide files is by setting the hidden attribute for a file or folder. This attribute is a flag that tells the operating system not to display the file in normal file browsing interfaces. Depending on the operating system, users can set this attribute by right-clicking on a file or folder, accessing the “Properties” or “Get Info” option, and enabling the hidden attribute.
- Using a file manager or command-line interface: File managers or command-line interfaces provide options to hide files. In a file manager, users can typically access the “View” menu or preferences to enable the option of showing or hiding hidden files. In a command-line interface, users can use specific commands, such as “ls -a” in Unix-based systems or “dir /a” in Windows, to reveal hidden files.
- Changing file extensions: Another way to hide files is by changing their file extensions. For example, a user can change the extension of a file from “.txt” to “.xyz”. This can make the file appear as if it is of a different type and less likely to be opened or accessed by unintended users.
- Using third-party software: There is specialized software available that enables users to hide files and folders. These applications often provide additional features such as password protection or encryption for added security. However, it is crucial to use reputable and trusted software to avoid any potential risks or vulnerabilities.
- Hiding files within other files: Steganography is a technique where files are hidden within other files, such as images or audio files. These hidden files are embedded in a way that makes them indistinguishable from the original file. This method is often used for covert communication or to protect sensitive information.
It’s worth mentioning that hiding files does not guarantee complete security or privacy. Knowledgeable users or individuals with malicious intent can still discover hidden files, especially if they have access to the system or use specialized techniques.
Understanding the methods used to hide files can help users take appropriate precautions and make informed decisions when it comes to file management and protecting sensitive data.
Types of Hidden Files
Hidden files come in various forms and serve different purposes. Here are some common types of hidden files:
- Configuration files: These files contain settings and preferences for applications, operating systems, or specific hardware components. They are often hidden to prevent accidental modifications that could disrupt the functioning of the system or software.
- System files: System files are essential to the proper operation of an operating system. Some system files are hidden to prevent users from inadvertently removing or modifying them, which could lead to system instability or malfunction.
- Temporary files: Temporary files are generated by software or the operating system to store information temporarily. They can include cache files, temporary backups, or files used during software installations. These files are typically hidden to reduce clutter in file browsing interfaces and prevent accidental deletion.
- Hidden folders: In addition to individual files being hidden, entire folders can be hidden as well. These hidden folders may contain sensitive data, personal files, or specific application-related files that are not intended for direct user access. Hiding folders helps protect the privacy and security of the files they contain.
- Protected system files: Some operating systems have files designated as protected system files. These files are hidden by default to prevent users from accidentally modifying or deleting them. Making changes to these files can have serious consequences for the stability and functionality of the system.
- Hidden user files: Users may choose to hide specific files or folders containing personal or sensitive information. This provides an added layer of privacy, preventing unauthorized access to personal files or confidential data.
- Embedded files: Certain files can be hidden within another file using techniques like steganography. For example, an image file may have an embedded text file containing secret information. These hidden files can be accessed using specialized software or techniques.
Understanding the different types of hidden files can help users navigate their file systems more effectively and make informed decisions about their management and security. It’s important to be cautious when interacting with hidden files to avoid unintended consequences or accidental damage to the system or valuable data.
Reasons for Hiding Files
There are several valid reasons why individuals or organizations choose to hide certain files:
- Privacy protection: Hiding files can be a way to protect personal or confidential information from prying eyes. By keeping sensitive files hidden, users can prevent unauthorized access and maintain their privacy.
- Security purposes: Hiding files adds an extra layer of security to protect against potential threats. By keeping important files hidden, such as financial records, passwords, or proprietary data, users can reduce the risk of unauthorized access or data breaches.
- Preventing accidental modifications or deletions: Some files are hidden to prevent accidental changes or deletion. System files and configuration files, for example, are commonly hidden to protect the integrity and stability of the operating system and installed software.
- Maintaining a clean file system: Hiding files or folders can help keep the file system organized and uncluttered. By hiding files that are not frequently accessed or are system-related, users can streamline their file browsing experience and focus on the files they need.
- Compliance with regulations: In certain industries, there are legal or regulatory requirements to secure sensitive information. Hiding files that contain protected data can be a part of an organization’s strategy to comply with these regulations and avoid non-compliance penalties.
- Protecting intellectual property: Hiding files can be a way to protect intellectual property, such as copyrighted materials, proprietary software code, or trade secrets. By keeping these files hidden, individuals and companies can safeguard their valuable assets.
- Preventing unauthorized sharing or distribution: Hiding files can help prevent unauthorized sharing or distribution of copyrighted materials or confidential information. By keeping files hidden, users can minimize the risk of these files being accessed or shared without proper authorization.
It’s important to note that while hiding files can provide added security and privacy, it is not a foolproof method of protection. It should be used in conjunction with other security measures, such as strong passwords, encryption, and regular backups, to ensure the safety of sensitive data.
Understanding the reasons for hiding files allows individuals and organizations to make informed decisions about file management and security, balancing the need for accessibility and protection.
Benefits of Hidden Files
The use of hidden files offers several benefits in terms of security, privacy, and system organization. Here are some advantages of hiding files:
- Enhanced privacy: Hiding files can protect sensitive and personal information from unauthorized access. By keeping certain files hidden, individuals can have greater control over who has the ability to view and modify their private data.
- Added security: Hiding files adds an extra layer of security to protect against unauthorized access or malicious activities. By making files harder to find, it reduces the likelihood of them being targeted or tampered with by individuals with malicious intent.
- Prevention of accidental modifications or deletions: Hiding files helps prevent accidental modifications or deletions, especially for critical system files or important user data. By requiring users to intentionally reveal and manipulate hidden files, it reduces the risk of unintentional actions that could have detrimental consequences.
- Improved system organization: Keeping certain files hidden can help maintain a clean and organized file system. By hiding files that are not frequently accessed or are system-related, users can avoid clutter and focus on the files that matter most without distractions.
- Protection of intellectual property: Hiding files can be beneficial for protecting intellectual property, such as copyrighted materials or proprietary information. By limiting visibility, it reduces the chance of unauthorized distribution or misuse of these valuable assets.
- Compliance with regulations: In industries where data security is crucial, hiding files can aid in compliance with legal and regulatory requirements. By hiding files that contain sensitive information, organizations can demonstrate their commitment to protecting confidential data and adhere to applicable regulations.
- Preservation of system integrity: Hiding system files and configurations helps maintain the stability and proper functioning of the operating system and installed software. This prevents accidental modifications that could disrupt system processes, ensuring a smooth user experience.
It is important to note that while there are clear benefits to hiding files, it is equally important to remember that incorrectly managing hidden files can lead to difficulties in file recovery or make troubleshooting more challenging. Therefore, it is essential to maintain a balance between hiding files for security and privacy purposes while still ensuring accessibility and ease of maintenance.
By understanding and utilizing the benefits of hidden files, individuals and organizations can strengthen their data security, improve organization, and protect valuable assets.
Risks and Dangers of Hidden Files
While hiding files can provide benefits in terms of security and privacy, it’s important to be aware of the potential risks and dangers associated with hidden files. Here are some considerations to keep in mind:
- Accidental loss of data: Hiding files can make it easier to accidentally overlook or forget about important data. If files are hidden without proper documentation or organization, there is a risk of permanently losing access to valuable information.
- Increased vulnerability to malware: Hidden files can be exploited by malware or malicious software to hide their presence on a system. Malware may use hidden files to avoid detection by traditional security measures, making it more challenging to detect and remove the threat.
- Unauthorized data access: While hiding files can help protect sensitive information, it does not guarantee complete security. Knowledgeable users or attackers who gain access to a system can still find and access hidden files, especially if they have sufficient privileges or access rights.
- Data loss during system upgrades or transfers: If hidden files are not properly managed during system upgrades or file transfers, there is a risk of losing access to the hidden files. This can result in data loss or the inability to retrieve important information after the transfer or upgrade process.
- Difficulty in troubleshooting: Hidden files can complicate the troubleshooting process, especially when trying to diagnose system issues or errors. System administrators or technical support personnel may have difficulties locating hidden files that may be causing problems, leading to delays in resolving technical issues.
- Potential for misuse: Hidden files can be used for malicious purposes, such as hiding malware, illegal content, or unauthorized software. Users with malicious intent may leverage hidden files to conceal their activities and bypass detection systems, posing potential risks to the system and its users.
- Loss of file visibility: In some cases, hidden files that are essential for system operations may become accidentally hidden or lost due to user error or software glitches. This can result in system instability or loss of functionality until the hidden files are properly restored.
Understanding the risks and dangers associated with hidden files enables users to take appropriate precautions and implement necessary security measures to mitigate these risks. It is important to strike a balance between utilizing hidden files for legitimate purposes and ensuring the accessibility and security of the entire system.
How to View Hidden Files
Viewing hidden files is necessary at times to access important data or troubleshoot system issues. Here are some methods to view hidden files on different operating systems:
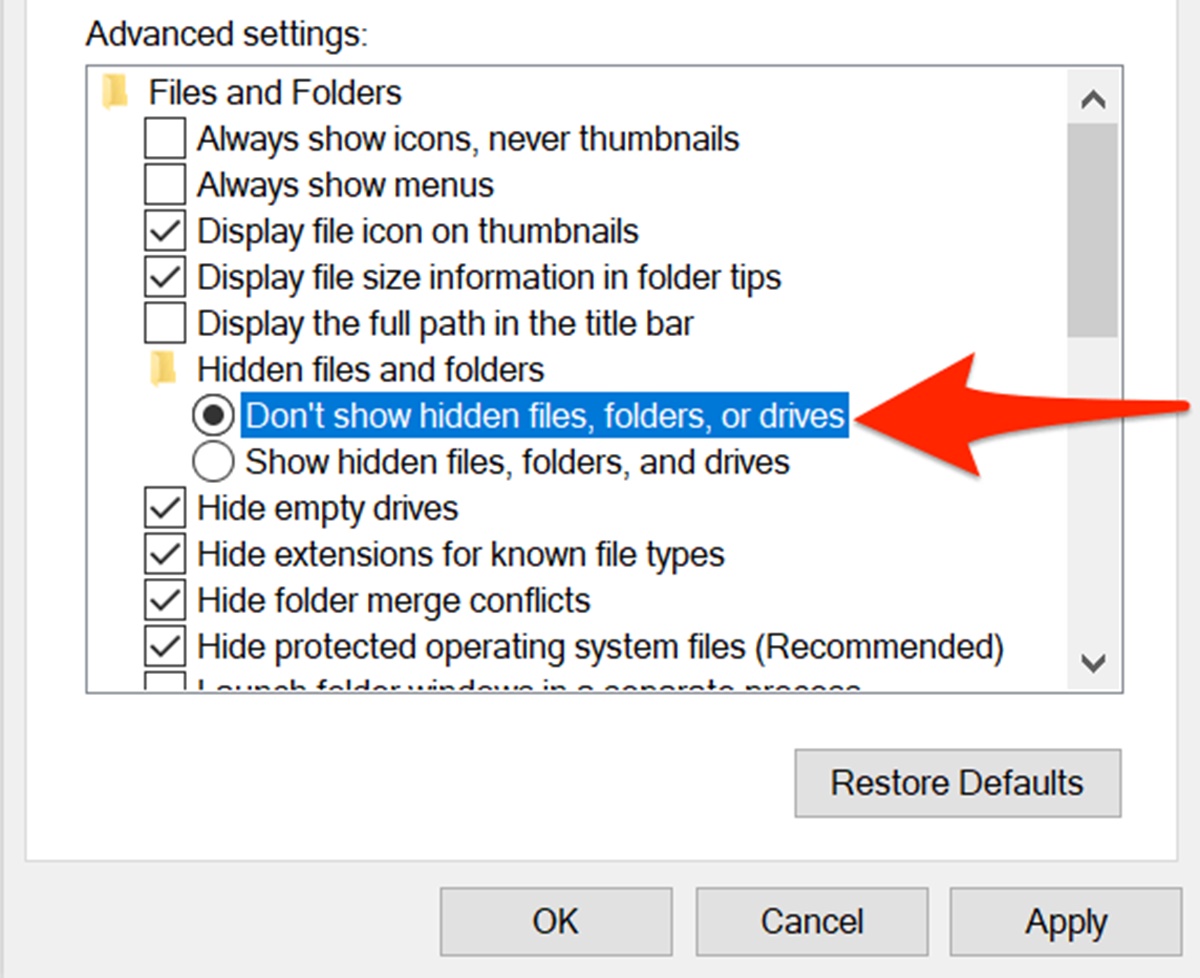
- Windows: To view hidden files on Windows, open File Explorer and go to the “View” tab. Check the “Hidden items” box in the “Show/hide” section. Hidden files and folders will now appear in File Explorer.
- macOS: On macOS, open Finder and go to the desired folder. Press Command + Shift + Period (.) to reveal hidden files. Hidden files will be displayed with a slight transparency in Finder.
- Linux: In most Linux distributions, you can press Ctrl + H in the file browser to toggle the visibility of hidden files. Alternatively, you can use the ls command with the -a option in the terminal to reveal hidden files.
- Command line: On both Windows and macOS, you can use the command line interface to view hidden files. In Windows, open the Command Prompt and use the dir /ah command to display hidden files. On macOS, open Terminal and use the ls -a command to show hidden files.
- Third-party file managers: There are several third-party file manager applications available that provide more advanced features for managing files, including the ability to easily view hidden files. Examples include Total Commander, FreeCommander, or Double Commander.
Please note that while viewing hidden files gives you access to them, exercise caution when interacting with these files, especially those that are critical to system operation. Modifying or deleting system files can cause system instability or other adverse effects.
It’s also worth mentioning that when you are done viewing hidden files, it is good practice to revert the settings to hide hidden files again. This helps to maintain system security and avoids accidental modifications or deletions.
By following these methods, users can view hidden files and navigate their file systems to access necessary files or troubleshoot system issues effectively.
How to Hide Files
If you have certain files that you want to keep hidden from prying eyes or secure sensitive information, you can use various methods to hide them. Here are some ways to hide files on different operating systems:
- Windows: Right-click on the file or folder you want to hide and select “Properties”. In the General tab, check the “Hidden” box under the Attributes section. Click “Apply” to save the changes. The file or folder will now be hidden from normal view in File Explorer.
- macOS: Select the file or folder you want to hide, press Command + I to open the Get Info window. In the General section, check the “Hidden” box. The file or folder will now be hidden from normal view in Finder.
- Linux: In Linux, you can rename the file or folder by adding a dot (.) at the beginning of the file or folder name. This convention hides the file or folder by default in file browsers.
- Third-party software: There are also third-party software solutions available that can provide more advanced hiding capabilities. These applications often offer additional features such as password protection or encryption for added security and privacy. However, it’s important to ensure that you use reputable and trustworthy software from reliable sources.
When hiding files, it’s important to note that while it may make them less visible, it does not guarantee absolute security or privacy. Knowledgeable users or individuals with malicious intent may still find ways to access hidden files. Therefore, it’s essential to combine hiding files with other security practices, such as strong passwords and encryption, to enhance data protection.
Remember that if you hide files, make sure to keep track of their location and use caution when interacting with them. It’s also important to maintain backups of important hidden files to prevent data loss in case of accidental deletion or system failure.
By following these methods and implementing additional security measures, you can effectively hide files and protect sensitive data from unauthorized access.
Tips for Managing Hidden Files
Managing hidden files effectively is essential to maintain system organization, ensure data security, and prevent accidental loss or misuse of valuable information. Here are some tips for managing hidden files:
- Create a system for organization: Develop a consistent and logical system for organizing hidden files. Use clear and descriptive names for hidden files and folders, making it easier to locate and manage them when needed.
- Keep track of hidden file locations: Maintain a record of the locations of your hidden files. This way, you can easily access them when necessary and avoid unintentionally forgetting or losing track of hidden files.
- Regularly review and update hidden files: Periodically review your hidden files to ensure they are still necessary. Remove any files or folders that you no longer need or that may pose security risks. Regularly updating hidden files can help maintain system organization and reduce clutter.
- Use backups: As with any important data, it is crucial to create regular backups of your hidden files. This ensures that you can recover your files in case of accidental deletion, hardware failure, or other unforeseen circumstances.
- Combine hiding with encryption: For increased security, consider encrypting your hidden files. Encryption adds an additional layer of protection to ensure that even if hidden files are accessed, the data inside remains secure and unreadable without the encryption key.
- Exercise caution with system files: When hiding system files, exercise caution and be careful not to modify or delete them without proper knowledge. Altering critical system files can lead to system instability or even cause the system to stop functioning correctly.
- Regularly update security measures: Keep your operating system and security software up to date to protect against potential vulnerabilities. Regularly updating your software ensures that you have the latest security patches and helps safeguard against new threats that may target hidden files.
- Document and share hiding practices: If you are managing hidden files in a shared environment or working with a team, document your hiding practices and ensure that others are aware of how to access or manage hidden files. This promotes consistency and ensures everyone understands the procedures for handling hidden files.
By following these tips, you can effectively manage your hidden files, maintain system organization, and protect sensitive data from unauthorized access or accidental loss.