What Is a Checksum?
A checksum is a value that is calculated from a set of data, typically a file or a message, and is used to detect errors or ensure data integrity. It acts as a digital fingerprint, allowing you to verify the validity and accuracy of the data.
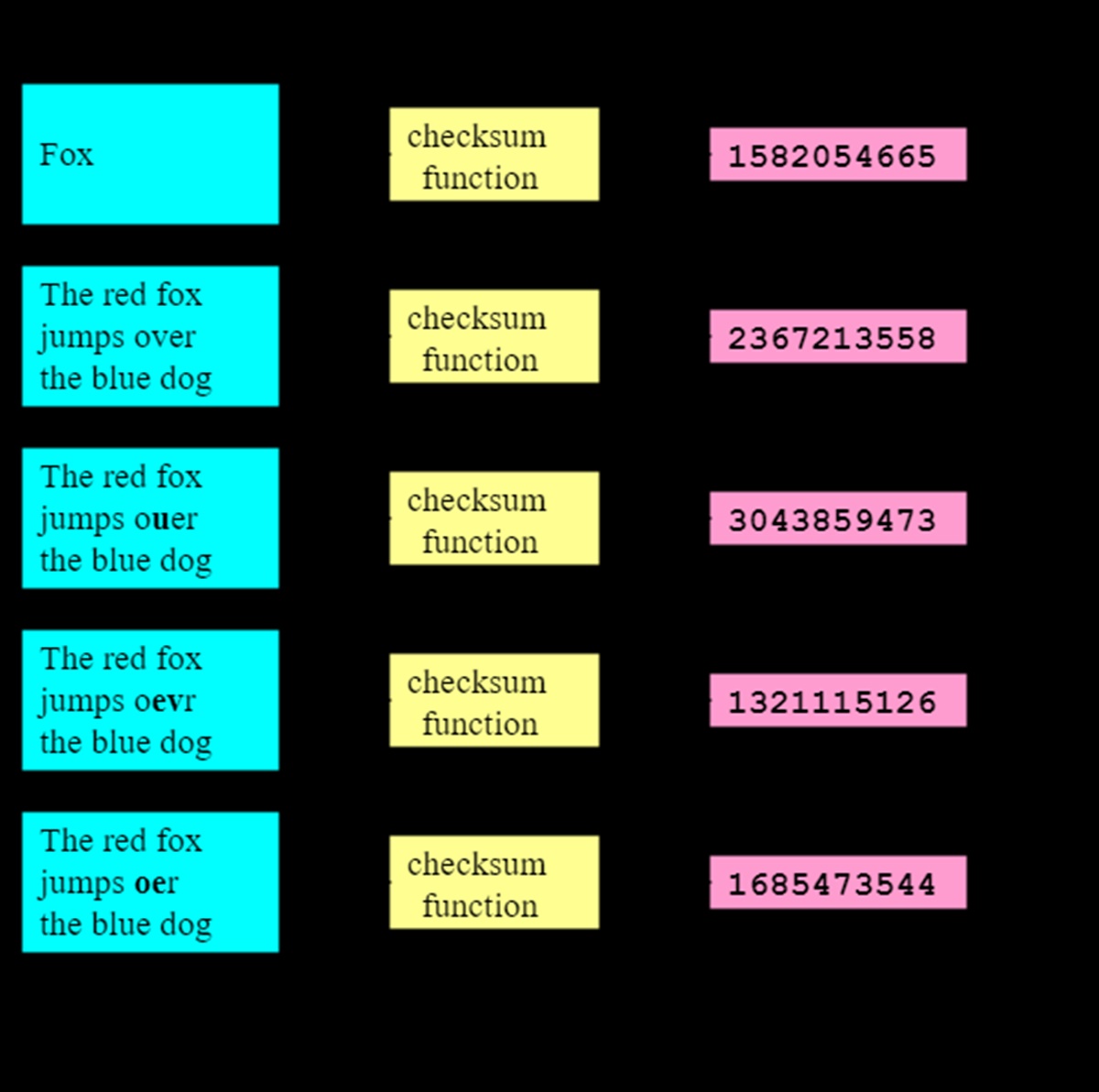
A checksum is generated by applying a mathematical algorithm to the data. This algorithm produces a fixed-size output that is unique to the specific set of data. Any changes to the data, no matter how small, will result in a different checksum.
The main purpose of a checksum is to detect errors during data transmission or storage. It provides a way to quickly verify if the data has been corrupted or modified in any way. By comparing the generated checksum with the original checksum, you can determine if errors have occurred during transmission or if the data has been tampered with.
Checksums are widely used in various fields, including network communication, file integrity checking, and data storage. They play a crucial role in ensuring the accuracy and reliability of data in these contexts.
In network communication, checksums are often used to verify the integrity of data packets sent between devices. Each packet contains a checksum that allows the receiving device to check if the data has been corrupted during transmission. If the checksum does not match, the data is considered unreliable, and the packet may be discarded or retransmitted.
File integrity checking is another common use case for checksums. A checksum can be calculated for a file using its contents. This checksum can then be compared to the calculated checksum of the file at a later time to check if the file has been modified or corrupted.
Checksums can be generated using different algorithms, such as CRC (Cyclic Redundancy Check) and MD5 (Message Digest Algorithm 5). Each algorithm has its own advantages and disadvantages, making them suitable for different applications.
By incorporating checksums into data transmission and storage processes, it is possible to enhance data integrity and minimize the risk of errors or tampering. Checksums provide a reliable and efficient way to ensure the accuracy and consistency of data, giving users confidence in the reliability of their information.
How Does a Checksum Work?
A checksum works by applying a specific algorithm to a set of data to generate a fixed-size value. This value, known as the checksum, is used to verify the integrity and accuracy of the data. The checksum is typically appended to the data or transmitted separately.
The checksum algorithm processes the data in a systematic way, taking into account the individual bits or bytes of the data. This algorithm calculates a unique value based on the data’s contents. Even a slight change in the data will produce a significantly different checksum.
When the data is received, the same algorithm is applied to the received data to generate a new checksum. This checksum is then compared to the original checksum sent with the data. If the two checksums match, it indicates that the data has been transmitted or stored without any errors. However, if the checksums don’t match, it indicates that changes or errors have occurred.
The process of comparing checksums is straightforward. If the checksums match, the data is considered valid and can be trusted. If the checksums don’t match, it means that the data has been altered or corrupted in some way.
Checksums can be used at different stages of data handling. For example, in network communication, a sender can calculate a checksum for each data packet before transmitting it. The receiver then verifies the integrity of the received packet by calculating the checksum and comparing it to the transmitted checksum. If they match, the packet is deemed error-free. If not, the packet may be discarded or retransmitted.
In file integrity checking, a checksum is calculated for the entire file. This checksum is stored separately or compared to a previously calculated checksum. If the checksums match, it indicates that the file has not been tampered with. However, if the checksums differ, it suggests that the file has been modified or corrupted.
Checksums are designed to be quick and efficient. They can be calculated and verified rapidly, making them a practical solution for real-time data validation. Various algorithms, such as CRC, Adler-32, and SHA (Secure Hash Algorithm), are commonly used to generate checksums.
Types of Checksums
There are several types of checksums that are commonly used, each with its own advantages and applications. The choice of checksum algorithm depends on the specific requirements of the data handling process. Here are some of the widely used types of checksums:
- CRC (Cyclic Redundancy Check): CRC is a popular checksum algorithm used in various fields, including network communication and error detection. It is based on polynomial division and generates a fixed-size checksum. CRC algorithms come in different variations, such as CRC-16, CRC-32, and CRC-64, each offering different levels of error detection capabilities.
- MD5 (Message Digest Algorithm 5): MD5 is a widely used checksum algorithm that produces a 128-bit checksum. While it is primarily used for data integrity checking, MD5 has also been used for password hashing and digital signatures. However, it has been found to have vulnerabilities that make it less secure for critical security applications.
- SHA (Secure Hash Algorithm): SHA is a family of secure hash functions designed by the National Security Agency (NSA) in the United States. SHA-1, SHA-256, and SHA-512 are some of the commonly used variants. These algorithms generate a fixed-size checksum and are widely used in cryptographic applications, including digital signatures and data integrity checking.
- Adler-32: Adler-32 is a checksum algorithm that is relatively simple and fast to calculate. It generates a 32-bit checksum and is commonly used in file integrity checking and error detection for data transmission.
- Parity Check: Parity check is a simple form of checksum that is used for error detection in computer memory systems and data transmission. It involves adding an extra bit (parity bit) to the data, which indicates whether the number of 1s in the data is odd or even. This allows for the detection of single-bit errors.
These are just a few examples of the many checksum algorithms available. The choice of checksum depends on factors such as the desired level of error detection, the size of the checksum, and the specific requirements of the application.
It is important to note that while checksums provide a reliable way to detect errors, they are not foolproof. In some cases, multiple errors can cancel each other out, resulting in a false validation. Therefore, it is always important to consider the limitations of checksums and implement additional error detection and correction mechanisms when necessary.
Example: Simple Checksum Calculation
To better understand how checksums work, let’s walk through a simple example of checksum calculation. Imagine we have a string of data: “Hello, world!”. We will use a basic checksum algorithm that adds up the ASCII values of all the characters in the string.
To calculate the checksum, we assign each character in the string a corresponding ASCII value. For example, the ASCII value of ‘H’ is 72, ‘e’ is 101, ‘l’ is 108, and so on. We add up all these ASCII values: 72 + 101 + 108 + 108 + 111 + 44 + 32 + 119 + 111 + 114 + 108 + 100 + 33 = 1,137.
Now, we need to convert this sum into a fixed-size checksum. Let’s say we decide to use a 16-bit checksum. We can simply take the remainder of the sum divided by 2^16: 1,137 mod 65536 = 1,137. Therefore, the checksum for the string “Hello, world!” using this algorithm is 1,137.
If we make any changes to the string, even a single character, the sum will be different, and hence the checksum will be different. For example, if we change the ‘o’ in “world” to an ‘i’, the sum becomes 1,135, and the checksum becomes 1,135 mod 65536 = 1,135.
During data transmission or storage, if the checksum of the received data matches the calculated checksum, we can be reasonably confident that the data has not been altered or corrupted. However, if the checksums do not match, it indicates that errors have occurred, and the data may need to be retransmitted or verified through other means.
This simple example demonstrates the basic concept of checksum calculation. In reality, more advanced algorithms and techniques are used to generate checksums. These algorithms are designed to offer better error detection capabilities and stronger data integrity assurance.
Example: Checksum in Network Communication
Checksums play a critical role in ensuring data integrity during network communication. Let’s explore an example to understand how checksums are used in this context.
Imagine you want to send a file from one computer to another over a network. Before sending the file, the sending computer divides the file into smaller packets. Each packet contains a portion of the file data, along with a checksum calculated for that specific packet.
When the receiving computer receives the packets, it calculates the checksum for each packet using the same algorithm as the sending computer. It then compares the calculated checksum with the received checksum. If they match, it indicates that the packet has been transmitted successfully without errors.
However, if the checksums don’t match, it implies that errors have occurred during transmission. The receiving computer can request the sending computer to resend the corrupted packet for reliable data transfer.
Let’s say we have a file divided into three packets: Packet A, Packet B, and Packet C. Each packet has its checksum calculated using a checksum algorithm like CRC or Adler-32.
Packet A and Packet B are transmitted successfully without any errors. The receiving computer obtains the correct checksums and validates the packets.
However, during the transmission of Packet C, some errors occur. When the receiving computer calculates the checksum for Packet C, it doesn’t match the received checksum. This indicates that Packet C has been corrupted.
In this case, the receiving computer can request the sending computer to retransmit Packet C. By using checksums in network communication, both the sending and receiving computers can quickly detect and recover from transmission errors, ensuring data integrity and reliable communication.
Moreover, checksums not only detect errors in individual packets but also provide an overall validation of the entire transmitted data. By comparing the checksum calculated for the complete received data with the expected checksum, the receiving computer can guarantee the accuracy of the entire file transmission.
The use of checksums in network communication is crucial for error detection and prevention. It ensures that data is transmitted accurately and reliably, minimizing the potential impact of data corruption and transmission errors.
Example: Checksum in File Integrity Checking
Checksums are widely used for file integrity checking to ensure that files have not been modified or corrupted. Let’s explore an example to understand how checksums are utilized in this scenario.
Suppose you have downloaded a file from the internet and want to verify its integrity before using it. To do this, you can calculate a checksum for the downloaded file using a checksum algorithm like MD5 or SHA. This checksum represents the unique fingerprint of the file.
When you download the file, it comes with a pre-calculated checksum that was generated by the file provider. You can compare this checksum with the checksum you calculated for the downloaded file. If they match, it indicates that the file has been downloaded accurately without any modifications or corruption.
For example, let’s say you downloaded a software installation file. After the download is complete, you calculate the checksum for the downloaded file using an algorithm like SHA-256. You then compare this checksum with the published checksum provided by the software provider. If they match, it confirms the integrity of the downloaded file.
If the checksums do not match, it suggests that the file has been modified or corrupted during the download process. In this case, it is recommended to redownload the file to ensure that you have a valid and intact version.
Furthermore, checksums are not limited to file downloads. They can also be used for ongoing file integrity checking. For example, you can calculate a checksum for a file at regular intervals or before and after performing certain operations on the file. By comparing these checksums, you can detect any changes or corruption that may have occurred.
Checksum-based file integrity checking is widely used in scenarios where data integrity is crucial, such as in critical system files, sensitive documents, or important backups. By validating the checksums, you can have confidence in the integrity and reliability of your files.
The use of checksums in file integrity checking provides a reliable and efficient method to verify data integrity. It helps protect against unauthorized modifications, accidental corruption, or even malicious tampering of files, ensuring that you can trust the integrity of your files and maintain the integrity of your data.
Checksum Calculators
Checksum calculators are tools that simplify the process of generating and verifying checksums for files, messages, or data sets. These calculators automate the checksum calculation process using various algorithms, saving time and effort for users. They come in both online and offline forms to cater to different needs and preferences.
Checksum calculators offer a user-friendly interface where you can input the data you want to calculate the checksum for. They then perform the necessary calculations using the selected algorithm and provide you with the resulting checksum.
These tools are especially useful when you want to verify the integrity of a file or verify the correctness of a transmitted message. Instead of manually performing checksum calculations, you can rely on the calculator to do it accurately and efficiently.
Online checksum calculators are web-based tools accessible through a browser. They are convenient and can be accessed from any device with an internet connection. Online calculators often allow you to choose from a range of checksum algorithms, such as CRC, MD5, SHA, or Adler-32. Some online calculators even provide additional features like batch processing for multiple files and the ability to validate checksums.
On the other hand, offline checksum calculators are software applications that you install on your computer or device. They offer similar functionality to online calculators but can be used without an internet connection. Offline calculators often come with the advantage of faster processing speeds and may offer additional features like file comparison or integration with file managers.
Checksum calculators are available for different platforms, including Windows, macOS, and Linux, ensuring compatibility with various operating systems. They provide a reliable way to generate and verify checksums, enhancing data integrity and security.
Whether you choose an online or offline checksum calculator, these tools simplify the process of checksum calculation and verification. They are invaluable for users who frequently need to validate data integrity or ensure the accuracy of transmitted information.
With the help of checksum calculators, you can quickly and easily generate checksums, allowing you to confidently verify the integrity and accuracy of your data, files, or messages.
Online Checksum Calculators
Online checksum calculators are web-based tools that allow users to easily generate checksums for files, messages, or data sets. These calculators provide a convenient and accessible way to perform checksum calculations without the need for additional software installation.
One of the key advantages of online checksum calculators is their accessibility. They can be accessed from any device with an internet connection and a web browser. This makes them particularly useful for users who do not have access to dedicated checksum calculator software or prefer not to install additional applications on their devices.
Online checksum calculators typically support a variety of checksum algorithms, such as CRC, MD5, SHA, and Adler-32. Users can select the desired algorithm and input the data for which they want to calculate the checksum. The calculator then performs the necessary calculations and presents the resulting checksum.
These calculators often offer additional features to enhance their usability. Some online checksum calculators allow users to perform batch processing, meaning they can calculate checksums for multiple files simultaneously. This is particularly useful when dealing with a large number of files or when conducting bulk verification of data integrity.
Moreover, online checksum calculators may provide the ability to validate checksums. Users can input both the data and the checksum and verify if they match. This feature is valuable for ensuring the accuracy and integrity of transmitted data or downloaded files, as it allows users to confirm the reliability of the received checksum.
Security is a key consideration when using online checksum calculators. Reputable online calculators use secure connections (HTTPS) to safeguard the privacy and integrity of the generated checksums. It is recommended to choose trusted and established online calculators to ensure your data remains secure during the calculation process.
Overall, online checksum calculators are valuable tools that offer a convenient and user-friendly way to calculate checksums for data verification. They are accessible from various devices, support multiple algorithms, and often provide additional features like batch processing and checksum validation. Online checksum calculators are ideal for users who require an on-the-go solution for data integrity checking and want a hassle-free checksum calculation process.
Offline Checksum Calculators
Offline checksum calculators are standalone software applications that allow users to generate and verify checksums for files, messages, or data sets directly on their computers or devices. These calculators offer a reliable and efficient way to perform checksum calculations without requiring an internet connection.
One of the key advantages of offline checksum calculators is their independence from internet access. Users can install these applications on their computers or devices and use them anytime, even when offline. This provides convenience and ensures consistent access to checksum calculation capabilities.
Offline checksum calculators offer a user-friendly interface that simplifies the process of calculating checksums. Users can usually select the desired algorithm, input the data or file for which they want to calculate the checksum, and generate the resulting checksum with a simple click or command.
These calculators often provide support for a wide range of checksum algorithms, including CRC, MD5, SHA, and Adler-32, among others. Users can choose the appropriate algorithm based on their specific needs or the industry requirements of the data they are working with.
Furthermore, offline checksum calculators may offer additional features to enhance their functionality. For example, some calculators allow users to compare the checksums of two files to determine if they are identical or different. This can be useful when verifying the integrity of backups or comparing different versions of a file.
Another advantage of offline checksum calculators is their faster processing speed compared to online calculators. Since the calculations are performed locally on the user’s device, the time required to calculate checksums is typically reduced, especially for large files or data sets.
Security is an important consideration when using offline checksum calculators. Users should ensure they download reputable and trusted calculators from reliable sources to minimize the risk of compromised applications. Additionally, it is recommended to verify the integrity of the calculator itself using checksums provided by the software provider.
Checksum Tools for Different Platforms
Checksum tools are available for different platforms, including Windows, macOS, and Linux, catering to the diverse needs and preferences of users. These tools provide an easy way to generate and verify checksums on specific operating systems, ensuring compatibility and convenience.
For users on Windows, there are various checksum tools available. These tools offer a range of features and support different checksum algorithms. Some notable examples include HashCalc, QuickHash, and MD5 Checker. These tools provide intuitive interfaces and allow users to calculate checksums for files or input text, as well as verify the accuracy of checksums.
Mac users also have access to dedicated checksum tools that are designed specifically for macOS. One popular option is the built-in Terminal application, which enables users to generate checksums using commands such as ‘md5’ or ‘shasum’. Additionally, there are third-party checksum tools available, such as HashTab and ChecksumUtility, which provide graphical user interfaces for calculating and verifying checksums.
Linux users benefit from the flexibility and customizability of open-source software. Command-line tools like ‘md5sum’, ‘sha1sum’, and ‘sha256sum’ are commonly available on Linux distributions, allowing users to calculate checksums easily. GUI-based tools, such as GtkHash, provide a more user-friendly approach for those who prefer a graphical interface on their Linux systems.
Cross-platform checksum tools are also available, providing compatibility across different operating systems. These tools are typically web-based or use Java to ensure they can be used on Windows, macOS, and Linux. Examples of cross-platform checksum tools include Checksum Validator, HashMyFiles, and Checksums.
Additionally, many file management applications, such as Total Commander, FreeCommander, and FileZilla, integrate checksum functionality directly into their interfaces, allowing users to calculate and verify checksums seamlessly within their chosen file management software.
It is important to note that regardless of the platform, users should exercise caution when downloading and using checksum tools. It is recommended to obtain them from trusted sources and verify the integrity of the tools themselves to ensure they have not been compromised.
Checksum tools for different platforms offer a wide range of options to suit users’ needs. Whether it is through dedicated applications, command-line tools, or integration with file management software, these tools make it convenient and reliable to generate and verify checksums, enhancing data integrity and security.