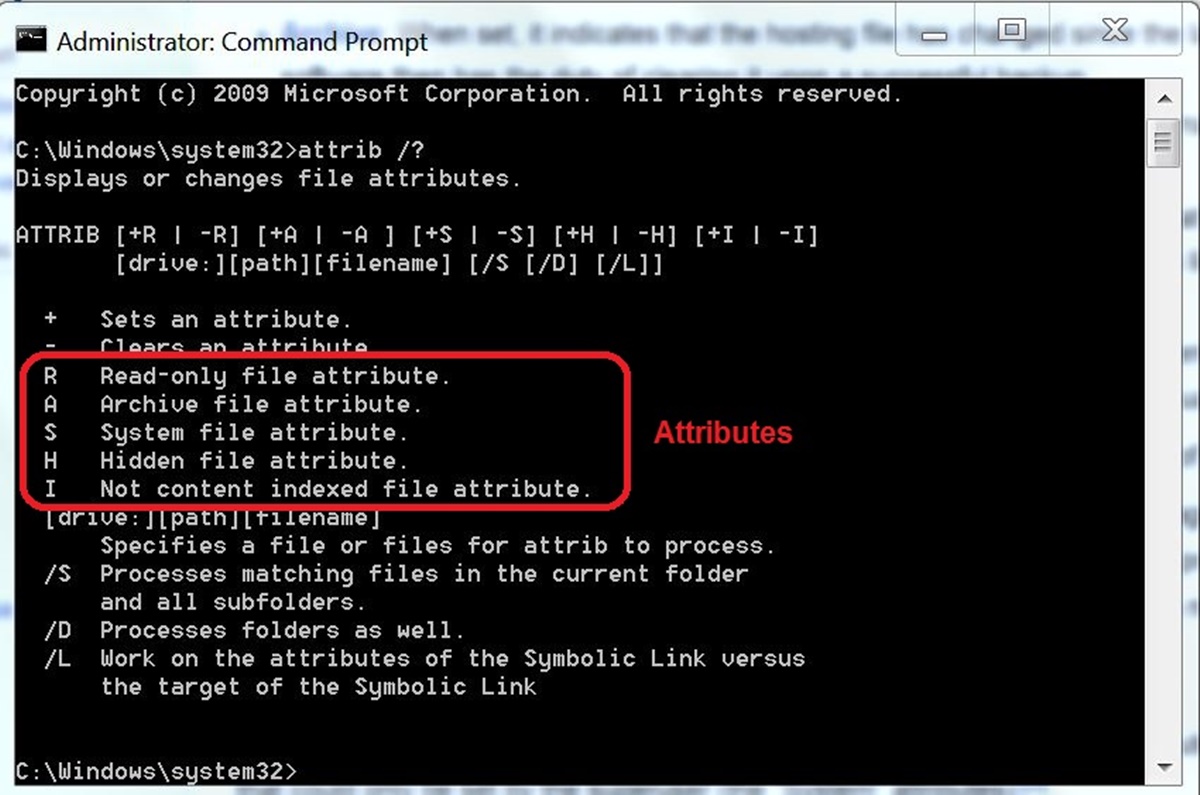
File Attributes
When working with files on a computer system, you may have come across the term “file attributes.” But what exactly are file attributes? File attributes are metadata values that provide information about a file. They define various characteristics and properties of a file, such as its permissions, visibility, and functionality.
Understanding file attributes is important as they play a crucial role in how files behave and interact with the operating system. By modifying these attributes, you can control the file’s behavior and customize its properties according to your needs.
There are several common file attributes that you may encounter when managing files. These attributes determine how files are accessed, displayed, and manipulated. Let’s take a closer look at some of the most frequently used file attributes:
- Read-Only Attribute: This attribute sets a file as read-only, preventing any modifications or changes from being made to the file.
- Hidden Attribute: The hidden attribute makes a file invisible in normal directory listings, providing a level of privacy and preventing accidental deletion or modification.
- Archive Attribute: This attribute indicates whether a file has been modified since it was last backed up, allowing backup software to prioritize files that need to be saved.
- System Attribute: Setting the system attribute marks a file as a crucial part of the operating system, indicating that it should not be modified or deleted.
- Compressed Attribute: This attribute indicates that a file has been compressed to reduce its size, saving storage space without losing any data.
- Encrypted Attribute: Encrypting a file adds a layer of security by converting its contents into a form that can only be accessed with the correct decryption key.
These are just a few examples of commonly used file attributes. Depending on the operating system and file system in use, there may be additional attributes available with specific functionalities. Understanding and utilizing these attributes can help you better manage and organize your files, ensuring they behave in the desired manner.
What Is an Attribute?
An attribute, in the context of computer science and information technology, refers to a characteristic or property that defines and provides additional information about an object or element. In the case of files, an attribute is a metadata value that describes various aspects of the file.
Attributes play a crucial role in organizing, managing, and manipulating files on a computer system. They provide valuable information about the file, such as its permissions, visibility, and behavior. By modifying these attributes, users can control how the file is accessed, displayed, and interacted with.
File attributes can be classified into different categories based on their functionalities. Some common categories of file attributes include:
- Permission Attributes: These attributes determine whether a file can be read, written to, or executed by specific users or groups. They help enforce access control and protect sensitive information.
- Visibility Attributes: These attributes control whether a file is visible or hidden from regular directory listings. Hiding a file can provide privacy and prevent accidental modifications or deletions.
- Functional Attributes: These attributes define the behavior and functionality of a file. They can include attributes like read-only, archive, system, compressed, encrypted, and more.
File attributes are essential for managing files effectively. They allow users to customize and tailor the properties of files according to their specific needs. For example, setting a file as read-only prevents accidental modifications, while marking a file as hidden ensures it remains invisible to unauthorized users.
Common File Attributes
File attributes are an integral part of managing, organizing, and controlling files on a computer system. They provide valuable information about a file and define its behavior and properties. There are several commonly used file attributes that you may encounter when working with files. Let’s explore some of these attributes:
- Read-Only Attribute: This attribute sets a file as read-only, meaning it cannot be modified or edited. It protects the integrity of the file and prevents accidental changes. This attribute is useful for files that should not be altered, such as system files or important documents.
- Hidden Attribute: The hidden attribute allows you to hide a file from regular directory listings. Hidden files are not readily visible, protecting them from accidental deletion or modification. This attribute is commonly used for system files or files that contain sensitive information.
- Archive Attribute: The archive attribute is used to determine whether a file has been modified since it was last backed up. When a file is modified, the archive attribute is set to indicate that the file needs to be included in the next backup operation. This attribute is often used by backup software to determine which files to include in a backup.
- System Attribute: Setting the system attribute marks a file as a vital part of the operating system. It designates files that should not be modified or deleted, as doing so might cause system instability or errors. System files typically have this attribute enabled.
- Compressed Attribute: The compressed attribute indicates that a file has been compressed to reduce its size. Compressing files can help save disk space and improve file transfer times. Compressed files are automatically decompressed when accessed or opened by compatible applications.
- Encrypted Attribute: The encrypted attribute provides an additional layer of security by encrypting the contents of a file. Encrypted files can only be accessed with the correct encryption key, ensuring that sensitive information remains protected from unauthorized access.
These are just a few examples of common file attributes. Each attribute serves a specific purpose in managing files and helps ensure the security, integrity, and functionality of the file system. Understanding these attributes allows you to effectively control and customize the behavior of your files according to your needs.
Read-Only Attribute
The read-only attribute is a file attribute that can be assigned to files on a computer system. When a file is set as read-only, it means that it cannot be modified, edited, or deleted. This attribute is useful for protecting important files and preventing accidental changes or deletions.
Files with the read-only attribute enabled can still be accessed and viewed, but any attempts to modify or delete them will be blocked by the operating system. This attribute acts as a safeguard, ensuring the integrity and stability of critical files.
The read-only attribute is commonly used for various file types, including system files, configuration files, and important documents. By setting these files as read-only, administrators and users can prevent unintentional alterations that could disrupt the functioning of software or compromise data integrity.
Enabling the read-only attribute is a straightforward process. On Windows systems, you can right-click on a file, go to the properties menu, and check the “Read-only” box. On Unix-based systems, you can use the “chmod” command in the terminal and specify the file permissions to include read-only access.
It’s important to note that the read-only attribute does not provide absolute protection against file modification. Skilled users or processes with sufficient permissions can still circumnavigate the read-only attribute and make changes to the files. However, it serves as a deterrent and helps prevent accidental modifications by ordinary users.
Files with the read-only attribute can still be copied, moved, and renamed. This allows you to create backups or transfer files to different locations without altering the original file. Additionally, special permissions can be granted to specific users or groups to override the read-only attribute, ensuring authorized modifications are still possible.
When working with read-only files, it’s important to remember that the read-only attribute pertains to the file itself and not its contents. This means that if a read-only file contains another file or folder, those items can still be modified or deleted unless they have their own individual read-only attributes.
By utilizing the read-only attribute, you can protect important files from unintended changes and maintain the integrity of your data. It is an effective way to prevent accidental modifications and ensure the stability of critical files in your computer system.
Hidden Attribute
The hidden attribute is a file attribute that allows you to hide files from regular directory listings. When the hidden attribute is enabled for a file, it becomes inaccessible or invisible to users by default. This attribute is often used to protect sensitive files, system files, or files that should not be modified or deleted unintentionally.
By designating files as hidden, you can prevent accidental modifications or deletions that may occur when users are browsing or managing files on their computer system. Hidden files are typically not displayed when viewing directories or file listings in file browsers or file managers.
The hidden attribute provides an additional layer of privacy and security for certain files. It helps safeguard sensitive information and prevents inadvertent access by unauthorized users. Though hidden files are not readily visible, they can still be accessed if users specifically choose to view hidden files or if the file path is known.
To set a file as hidden, you can take different actions based on your operating system. On Windows, you can right-click on a file, go to the properties menu, and check the “Hidden” box. On Unix-based systems, you can rename a file by adding a period (.) at the start of its filename to make it hidden.
It’s important to note that enabling the hidden attribute does not provide absolute protection for the file. Users with sufficient permissions or knowledge of the file’s location can still access and modify hidden files. However, the hidden attribute serves as a deterrent and helps prevent accidental modifications or deletions by users who are unaware of the file’s existence.
When working with hidden files, it’s essential to remember that the visibility of the files may vary depending on the settings of the user’s file browser or operating system. Some operating systems may have an option to show hidden files, while others may not display them by default.
It’s also worth mentioning that hidden files can be useful for organizing and managing system files or files that are not typically accessed by end-users. System configuration files, temporary files, or files associated with specific software programs are common examples of files that may be designated as hidden.
The hidden attribute provides a practical way to protect sensitive or critical files from accidental modifications or deletions. By using this attribute, you can maintain the confidentiality and integrity of your files, ensuring that they remain secure and accessible only to authorized individuals.
Archive Attribute
The archive attribute is a file attribute that indicates whether a file has been modified since it was last backed up. When a file is modified, the archive attribute is automatically set, indicating that the file needs to be included in the next backup operation. This attribute is commonly used by backup software to determine which files need to be saved or updated during the backup process.
The archive attribute simplifies the process of backing up files by keeping track of the changes made to them. It allows backup software to identify files that have been modified since the last backup, ensuring that only the necessary files are included in the backup operation. By selectively backing up files with the archive attribute enabled, backup processes can be more efficient and time-saving.
Typically, when a file is backed up, the backup software clears the archive attribute, indicating that the file has been successfully included in the backup. This process ensures that subsequent backups only capture new or modified files, rather than duplicating the entire file collection.
Enabling the archive attribute does not change the functionality or accessibility of the file. It simply serves as a flag, indicating that the file needs to be included in a backup. This attribute is independent of other file attributes, such as read-only or hidden, and can coexist with them.
When a file is modified after a backup, the archive attribute is set, indicating that the file needs to be backed up again to reflect the changes. By using this attribute, organizations can easily track and manage their backup processes, ensuring that critical files are properly safeguarded.
It’s worth noting that the archive attribute is specific to certain file systems and backup software. Not all operating systems or backup solutions utilize the archive attribute to manage backups. However, for those systems that do support it, the archive attribute provides a convenient way to identify and track file changes for backup purposes.
Managing the archive attribute is typically handled automatically by backup software. However, in some cases, users or administrators can manually set or clear the archive attribute for specific files if necessary.
The archive attribute plays a vital role in the backup and recovery process, allowing organizations to efficiently manage and safeguard their valuable data. By utilizing this attribute, backups can be tailored to include only files that require updating, saving time and storage space while ensuring data integrity.
System Attribute
The system attribute is a file attribute that designates a file as an essential part of the operating system. When a file is marked with the system attribute, it indicates that the file should not be modified, deleted, or tampered with as it has crucial functions for the proper functioning of the system.
The system attribute provides a way to protect critical files and maintain the integrity and stability of the operating system. These files are typically vital components, configurations, or libraries that are necessary for the system’s operation. Modifying or deleting system files can lead to system errors, malfunctions, or even system crashes.
By designating files as system files, the operating system can prioritize and protect them from unintended alterations. This attribute allows the system to differentiate between ordinary user files and files that are integral to the functioning of the operating system.
Typically, system files are hidden and not shown in regular directory listings. This additional level of protection helps prevent accidental modifications or deletions by users who might be unaware of the files’ importance.
Enabling the system attribute is typically done by the operating system itself or by certain administrative tools. Users without the necessary permissions cannot modify or remove the system attribute from files, ensuring the files’ integrity remains intact.
It’s important to note that the system attribute does not mean that the file cannot be read or accessed by users. Users with appropriate permissions can still view and access the contents of system files. However, modifying or deleting these files may have serious consequences on the overall stability and functionality of the operating system.
The system attribute is crucial for maintaining a secure and stable operating system environment. It ensures that critical files are protected from accidental or unauthorized modifications, safeguarding the overall integrity and reliability of the system.
Applying the system attribute to files should be done with caution and only by users or administrators who have a thorough understanding of the consequences. Modifying or tampering with system files without proper knowledge or authorization can lead to severe consequences, including system failures or security vulnerabilities.
By using the system attribute, operating systems can effectively manage and safeguard critical files, ensuring the smooth operation and security of the entire system.
Compressed Attribute
The compressed attribute is a file attribute that indicates a file has been compressed to reduce its size. Compression is the process of encoding data in a more efficient manner, resulting in smaller file sizes without losing any data or information. When a file is marked with the compressed attribute, it signifies that the file has undergone compression to save storage space.
The compressed attribute is commonly used for files that contain large amounts of data and can benefit from reduced storage requirements. Compressing files can be especially useful for documents, images, videos, and software applications, as it allows for more efficient storage and faster file transfers.
Files with the compressed attribute enabled are stored in a compressed format on the storage media. This compression is typically done using algorithms that analyze the file’s data and apply techniques to reduce its size. When accessing or using a compressed file, the operating system automatically decompresses it on the fly, making it accessible in its original form.
Enabling the compressed attribute for a file varies depending on the operating system and the tools available. Some operating systems have built-in compression features, while others require third-party software to apply compression and set the attribute.
It’s important to note that while compression reduces file size, it does not impact the file’s functionality or integrity. Compressed files can still be read, modified, and shared like any other file. The decompression process occurs transparently during file access, ensuring that users can work with the file seamlessly.
Compressed files may offer several benefits. First and foremost, compression reduces the amount of storage space required to store files, allowing users to accommodate more data within limited storage capacities. This is particularly useful for devices with finite storage, such as solid-state drives or cloud storage.
In addition to reducing file size, compression can also improve file transfer times. Smaller file sizes result in faster upload and download speeds, making it easier and quicker to share files across networks or send them as email attachments.
It’s worth noting that while compression offers storage benefits, it may incur a slight performance cost. Compressed files may take slightly longer to access and read due to the decompression process. However, modern computer systems and storage devices have become increasingly efficient at handling compressed files, minimizing any noticeable impact on performance.
The compressed attribute provides a valuable tool for managing files efficiently and optimizing storage resources. By utilizing compression techniques and enabling the compressed attribute, users can save space, improve file transfer speeds, and make the most out of their available storage capacity.
Encrypted Attribute
The encrypted attribute is a file attribute that indicates a file has been encrypted to protect its contents. Encryption is the process of converting data into a form that can only be accessed or read with the correct encryption key. When a file is marked with the encrypted attribute, it signifies that the file’s contents are securely encoded and can only be decrypted by authorized individuals or processes.
The encrypted attribute provides an additional layer of security for sensitive or confidential files. Encrypting files makes it extremely difficult for unauthorized users to access or view the information contained within the file, even if they manage to gain physical or unauthorized access to the file.
Encryption is particularly useful for files that contain sensitive information, personal data, or proprietary company information. By encrypting these files, organizations and individuals can mitigate the risk of data breaches and unauthorized access, ensuring that the contents of the file remain secure and confidential.
Enabling the encrypted attribute involves using encryption software or built-in encryption features provided by the operating system. Encryption algorithms and encryption keys are utilized to encode the contents of the file, rendering it unreadable without the corresponding decryption key.
Users can still access and use encrypted files as normal. When an encrypted file is accessed, the operating system or encryption software automatically prompts the user to provide the correct decryption key. Once the key is provided, the file is decrypted on the fly, allowing users to work with the file as they would with any other unencrypted file.
It’s crucial to note that encryption protects the contents of the file, but it does not impact other file attributes or file functionality. Encrypted files retain their original attributes, such as read-only or hidden, and can still be copied, moved, or renamed.
Encrypting files provides peace of mind, especially when storing or transferring sensitive information. In the event of unauthorized access or data leakage, encrypted files are significantly harder to decipher, ensuring that sensitive information remains protected.
It’s important to keep the encryption key secure and only share it with authorized individuals. Losing the encryption key can result in permanent data loss, as encrypted files cannot be decrypted without the correct key.
The encrypted attribute offers a powerful defensive measure to protect sensitive files. By utilizing encryption and enabling the encrypted attribute, users and organizations can enhance the security and confidentiality of their data, mitigating the risks of unauthorized access or data breaches.
Index Attribute
The index attribute is a file attribute that indicates whether a file is indexed by the operating system’s file indexing service or search functionality. When a file is marked with the index attribute, it means that the file’s content has been indexed, making it easier and faster to search for files based on their content, keywords, or metadata.
The index attribute plays a crucial role in improving the efficiency of file searches. By indexing files, the operating system creates a searchable database or index that maps the content and properties of files. When users perform a search, the system consults this index to quickly locate the relevant files that match the search criteria.
Indexing is particularly useful for larger file systems or when working with a vast amount of files. Without indexing, searching for specific files or content within files could be time-consuming and require scanning through each file individually.
Enabling the index attribute is typically done automatically by the operating system or the indexing service. However, users can also manually enable or disable the index attribute for specific files or directories as needed.
It’s important to note that indexing files can occupy additional storage space and may impact system performance to a certain extent. The index database requires storage to store the indexed information, and updating the index periodically may consume system resources. However, the benefits of faster and more accurate file searches usually outweigh these considerations.
The index attribute is especially useful when searching for specific content within files, such as documents, spreadsheets, or emails. Users can enter specific keywords or phrases, and the system will utilize the index to locate the files that contain the relevant content.
It’s worth mentioning that not all file types may be indexed by default. The indexing service typically focuses on specific file formats or extensions that are commonly used for documents, multimedia, or emails. However, users can often configure the indexing service to include additional file types and directories as needed.
The indexing process runs in the background and continuously updates the index to reflect changes made to files. This ensures that the search results remain up to date and accurately reflect the current state of the indexed files.
By utilizing the index attribute and enabling file indexing, users can significantly improve the efficiency and effectiveness of file searches. Indexing allows for quicker retrieval of files based on their content, saving time and effort when locating specific information or documents within a file system.
Temporary Attribute
The temporary attribute is a file attribute that denotes a file as temporary or transient in nature. When a file is marked with the temporary attribute, it indicates that the file is intended for short-term use and is subject to being deleted or cleaned up after its purpose is fulfilled.
Temporary files are typically created and used by various applications and processes for storing temporary data or performing temporary tasks. These files are often generated during program execution, software installations, or when working with large datasets that require temporary storage.
The temporary attribute serves several purposes. First, it helps to ensure that temporary files do not consume unnecessary disk space by remaining on the system after their intended use. The attribute allows for easy identification and cleanup of files that are no longer needed.
Another important aspect of the temporary attribute is its impact on system performance. Since temporary files are short-lived, marking them as temporary allows the operating system or other cleanup tools to prioritize and remove them during routine system maintenance or disk cleanup activities.
Enabling the temporary attribute for files can be automated by the applications or processes that create them. In some cases, users may manually mark files as temporary, especially if they are working with files that are intended for short-term use and are not required to be stored permanently.
It’s important to note that the temporary attribute does not affect the functionality of the file or its accessibility. Users can read, modify, or delete temporary files as they would with any regular file. The attribute simply denotes the intended purpose and temporary nature of the file.
Temporary files are typically stored in temporary directories designated by the operating system or the application generating the files. These directories are often cleaned up periodically or during system reboots to remove any remaining temporary files.
Removing temporary files is beneficial in terms of disk space management, system performance optimization, and maintaining data privacy. These files are often non-essential and can be safely deleted without any impact on the functionality or integrity of the system or the user’s data.
However, it’s important to exercise caution when handling temporary files, as some may contain sensitive information or data that should not be accessible to unauthorized individuals. It’s recommended to use trusted applications or tools for managing and cleaning up temporary files to ensure the privacy and security of data.
By utilizing the temporary attribute for files, it allows for efficient management and cleanup of temporary data, ensuring system performance optimization and effective disk space utilization.
Offline Attribute
The offline attribute is a file attribute that indicates whether a file is available for offline use. When a file is marked with the offline attribute, it signifies that the file has been specifically designated to be accessible even when not connected to the original source or network.
The offline attribute is particularly useful for files that users may need to access when they are away from the network or working in environments with limited or no internet connectivity. By marking files as offline, users can ensure that they have uninterrupted access to critical files, regardless of their network status.
Enabling the offline attribute for files can be done manually by the user, or it can be automated by the operating system or specific file synchronization software. When a file is marked as offline, the operating system or synchronization software will ensure that a local copy of the file is stored on the user’s device. This local copy can be accessed and modified even when the device is offline.
The offline attribute is especially beneficial for mobile or remote workers who need access to certain files while on the go or in locations with limited connectivity. By utilizing the offline attribute, they can download and store important files locally before heading into areas with unreliable or no network access.
When the device regains network connectivity, any changes made to the offline files are synchronized with the original source. This allows users to seamlessly work on the files regardless of their online or offline status.
It’s important to regularly synchronize offline files with the original source to ensure that the most up-to-date versions are available. This synchronization process updates the local copies of the files with any changes made on the network or by other users.
Using the offline attribute can improve productivity and streamline workflows for users who frequently work in locations with unstable internet connections or limited network access. It allows them to continue working on critical files without disruptions or delays.
It’s worth noting that the offline attribute should be used judiciously. Enabling the offline attribute for a large number of files can consume storage space on the user’s device, especially if the files are large in size. It’s essential to strike a balance between having the necessary offline access and managing available storage capacity.
By using the offline attribute, users can ensure uninterrupted access to important files, regardless of their network connectivity. It provides flexibility and convenience for users who need to work with files while away from the network, improving overall productivity and efficiency.
Sparse Attribute
The sparse attribute is a file attribute that indicates a file contains sparse data. Sparse data refers to files that have sections with large amounts of empty or zero-filled data. When a file is marked with the sparse attribute, it signifies that the file’s content is optimized to efficiently handle these large empty or zero-filled sections.
The sparse attribute is particularly useful for files that involve the storage of large, sparse matrices or datasets. Instead of allocating physical disk space to represent empty or zero-filled sections, the sparse attribute allows the file system to optimize storage by efficiently representing and managing these sections.
By utilizing the sparse attribute, the file system can perform intelligent compression and storage techniques to minimize the actual storage space required for the file. This optimization helps reduce disk usage and improves overall system performance when working with files containing sparse data.
Enabling the sparse attribute for files can be done manually by the user or automatically by software that deals with sparse data. When the sparse attribute is enabled, the file system understands that specific sections within the file contain sparse data and treats them accordingly to save storage space.
It’s important to note that working with sparse files may have implications for file manipulation and storage considerations. Although sparse files can appear to be much larger than their actual disk footprint, copying, moving, or transferring sparse files may still require transferring the entire file size, including the empty or zero-filled sections.
Applications that interact with sparse files need to be designed to handle these files efficiently. They should be able to recognize and process sparse data appropriately to maximize performance and storage optimization. Some software programs and file systems provide built-in support for handling sparse files and optimizing their usage.
The sparse attribute is particularly beneficial for optimizing storage efficiency for files that contain large amounts of empty or zero-filled sections. It allows users to work with these files while minimizing the required disk space and ensuring efficient utilization of storage resources.
It’s important to understand that the sparse attribute is specific to certain file systems and may not be universally supported. Compatibility with the sparse attribute may vary depending on the operating system and the software applications being used.
By utilizing the sparse attribute, users can efficiently manage files with sparse data, reduce disk usage, and improve overall system performance when working with these types of files.
Not Content Indexed Attribute
The not content indexed attribute is a file attribute that indicates that the content of a file should not be included in the operating system’s content indexing service. When a file is marked with the not content indexed attribute, it signifies that the file’s content should not be considered for search purposes or included in the index generated by the operating system’s search functionality.
The not content indexed attribute is particularly useful for files that contain non-textual data or files that do not require indexing for search purposes. Examples of such files include binary files, multimedia files, or files that contain encrypted or compressed data.
By applying the not content indexed attribute to files, users or administrators can exclude these files from being processed by the content indexing service. This helps optimize the indexing process by reducing the resources required to index and maintain the search database.
Enabling the not content indexed attribute can be done manually by the user or automatically by the operating system or specific file management tools. It allows users to customize which files are considered for search purposes and exclude files that are not relevant or do not require indexing.
Files marked with the not content indexed attribute are typically not searchable through the operating system’s built-in search functionality. However, it’s important to note that this attribute does not impact the file’s accessibility or functionality. Users can still access and work with these files as they would with any other file, even though their contents may not be included in search results.
This attribute is useful for files that do not contain textual content or files with data that is not intended to be searched or indexed, ensuring that searches focus on files that are relevant and improve the efficiency of the search process.
It’s worth mentioning that not all file systems support the not content indexed attribute, and compatibility may vary depending on the operating system or file management tools used. Some file systems or search engines may have their own mechanisms for excluding certain file types from indexing.
The not content indexed attribute provides a way to fine-tune the indexing process and exclude files from search results that are not necessary or relevant. By utilizing this attribute, users can optimize the search functionality, focusing on files that contain textual content or require indexing for search purposes.
Reparse Point Attribute
The reparse point attribute is a file attribute that indicates the presence of a reparse point within a file. A reparse point is a special marker or tag that redirects the access or handling of a file to a different location or a specific software or driver handler.
Reparse points are commonly used for advanced file system features, such as symbolic links, junction points, or mount points. They allow files or directories to appear as if they exist in one location while physically residing elsewhere, providing flexibility and convenience for file organization or redirection purposes.
When a file is marked with the reparse point attribute, it indicates that the file system should interpret the file’s content or behavior based on the specific reparse point attached to it. This attribute allows the operating system or other software components to recognize and handle the file differently based on the defined reparse behavior.
The reparse point attribute is often used for symbolic links, which are files that serve as pointers to other files or directories. When a symbolic link is accessed, the reparse point redirects the access to the target location, allowing seamless navigation and accessing of files or directories.
Junction points are another use case for the reparse point attribute. They establish a virtual folder that links to a different location on the file system. This allows for folder redirection or organization without physically moving the files or directories.
Mount points are yet another example where the reparse point attribute is utilized. Mount points provide the ability to include a file system or volume within an existing directory structure, effectively merging file systems or volumes into a unified hierarchy.
Setting the reparse point attribute is typically done by specialized software or operating system commands. Users or administrators can create symbolic links, junction points, or mount points to configure the desired redirection or organization of files and directories.
It’s important to note that the reparse point attribute is specific to certain file systems and may not be universally supported. Compatibility with the reparse point attribute may vary depending on the operating system, file system, or software applications being used.
Reparse points offer flexibility and versatility in file system organization, redirection, and handling. By utilizing the reparse point attribute, users can create symbolic links, junction points, or mount points to optimize file organization, access, and integration within the file system.
Integrity Attribute
The integrity attribute is a file attribute used to verify the integrity and authenticity of a file’s content. When a file is marked with the integrity attribute, it means that measures have been taken to ensure that the file has not been tampered with or modified since its creation or last verified state.
This attribute is especially vital for files that contain sensitive data, such as software executables, system files, or critical configuration files. By applying the integrity attribute, organizations and users can verify that the file has not been compromised or modified by unauthorized individuals or malicious software.
The integrity attribute is typically associated with cryptographic algorithms that generate a unique hash or checksum value based on the content of the file. This hash or checksum value is calculated and stored along with the file. Subsequent integrity checks can then be performed by recalculating the hash or checksum value and comparing it to the stored value to verify the file’s integrity.
Ensuring file integrity helps detect unauthorized modifications or tampering attempts, providing an additional layer of security against attacks, malware, or data corruption. If the calculated hash or checksum value does not match the stored value, it indicates that the file has been altered, and its integrity may be compromised.
Enabling the integrity attribute for files can be a manual or automated process depending on the tools or operating systems used. Cryptographic algorithms, such as MD5, SHA-1, or SHA-256, are commonly employed to calculate the hash or checksum values required for integrity verification.
It’s important to note that the integrity attribute does not impact the accessibility or functionality of the file. Users can still access and use the file as they normally would. However, enabling this attribute allows for ongoing verification of the file’s integrity and enhances overall data security.
Integrity checks can be performed periodically or on-demand to ensure the file’s integrity remains intact. This process helps detect any potential unauthorized modifications or file corruption that may have occurred since the last integrity check.
In real-world applications, the integrity attribute is commonly used for ensuring the integrity of software installations, system files, firmware, or critical configuration files. By verifying the integrity of these files, organizations can detect any tampering attempts, software vulnerabilities, or system compromises.
It’s worth mentioning that verifying file integrity using the integrity attribute should be accompanied by other robust security measures, such as access control, encryption, and regular patching or updating. A multi-layered approach to security enhances overall protection and reduces the risk of unauthorized modifications or breaches to critical files.
The integrity attribute provides a means to ensure the authenticity and integrity of files, verifying that they remain unaltered and trustworthy. By utilizing this attribute and performing regular integrity checks, users and organizations can enhance the security and reliability of their files and data.
Virtual Attribute
The virtual attribute is a file attribute that denotes a file as virtual or pseudo-present, meaning it appears to exist within a file system but does not correspond to a physical file or directory. Files marked with the virtual attribute are essentially placeholders that reference data or resources located elsewhere in the system.
The virtual attribute allows for a flexible and efficient approach to file organization and resource management. It enables the creation of virtual files or directories that can be accessed and utilized as if they were physical entities, providing a unified view of data or resources without duplicating their storage.
Virtual files are commonly used for various purposes, including providing access to data from remote storage locations, dynamically generated content, or acting as custom views for data stored in different locations or formats. They allow for logical groupings or abstractions of data without the need for physically duplicating the content.
Enabling the virtual attribute for files can be achieved by utilizing specialized software or operating system functionality dedicated to managing virtual files. These tools allow users or administrators to create and configure virtual files or directories, specifying the underlying data or resource they represent.
When accessing a virtual file, the system redirects the request to the appropriate location or retrieves the corresponding data or resource based on the virtual file’s configuration. This allows users or applications to work with the virtual file as if it were a physical file, even though the file’s content may be dynamically generated or located in a different storage location.
The virtual attribute provides considerable benefits in terms of efficient data management and resource utilization. It avoids the need for redundant data storage and allows for the creation of custom views or logical groupings of data without physically moving or duplicating files.
Virtual files are especially useful in situations where data needs to be accessed or presented in a specific way, such as aggregating data from multiple sources, providing a consistent view of distributed data, or enabling access to data stored remotely.
It’s important to note that the virtual attribute is unique to certain file systems and may not be universally supported. Compatibility and availability of virtual file management tools may vary depending on the operating system or software applications being used.
By utilizing the virtual attribute and creating virtual files, users can streamline data access and resource management. Virtual files provide a flexible approach to organizing and accessing data, allowing for efficient utilization of resources and simplifying complex data architectures.
EFS Attribute
The EFS (Encrypting File System) attribute is a file attribute that signifies a file has been encrypted using the Encrypting File System feature provided by certain operating systems. When a file is marked with the EFS attribute, it indicates that the file’s contents have been securely encoded to protect them from unauthorized access.
The EFS attribute provides a robust encryption mechanism that allows users to protect sensitive or confidential information stored in files. It encrypts the contents of the file using an encryption key tied to the user’s account, making the data unreadable to anyone without the proper decryption key.
Enabling the EFS attribute for files can be done manually by the user or automatically by specific file management tools or operating system functionalities. Once enabled, the encryption process is transparent to users and applications, allowing the encrypted files to be accessed and used normally when the user has the appropriate permissions.
Files marked with the EFS attribute can be accessed by the user who performed the encryption even when the file system is accessed by other users or administrators. This provides an additional layer of security, as only authorized individuals with the proper encryption keys can decrypt and access the file’s contents.
The EFS attribute is particularly useful for protecting sensitive files that contain personal information, confidential documents, or proprietary business data. By encrypting these files, organizations and individuals can ensure that even if the files are compromised or accessed without authorization, the encrypted data remains unintelligible.
It’s important to note that while the EFS attribute protects the file’s contents, it does not impact other file attributes or file functionality. Encrypted files retain their original attributes, such as read-only or hidden, and can still be copied, moved, or renamed, without compromising their encryption security.
Protecting files with the EFS attribute requires proper key management. The encryption key used to encrypt the file is tied to the user’s account, and if the user’s account is lost or unavailable, the encrypted file may become inaccessible. It is crucial to have a backup of the encryption key or have appropriate methods in place to recover encrypted files in case of key loss.
It’s also important to note that encryption provides an additional layer of security, but it should be used in conjunction with other security measures such as access control, strong passwords, and regular security updates to ensure comprehensive data protection.
By utilizing the EFS attribute, users and organizations can protect sensitive files and ensure the confidentiality and integrity of their data. Encrypted files remain secure even if they are accessed or compromised by unauthorized individuals or if the files are moved or transferred between different storage locations.
Summary
File attributes play a significant role in managing and organizing files within a computer system. They provide valuable information about files and determine their behavior, accessibility, and security. Understanding and utilizing file attributes can enhance file management, protect sensitive data, and optimize system performance.
Some common file attributes include the read-only attribute, which prevents file modifications, and the hidden attribute, which allows files to remain invisible in regular directory listings. The archive attribute indicates whether a file has been modified since the last backup, ensuring data integrity during backup operations. The system attribute marks files as crucial components of the operating system, protecting them from accidental modifications or deletions.
Compressed and encrypted attributes optimize storage space and improve data security respectively. The compressed attribute reduces file size through compression techniques, while the encrypted attribute protects file contents by encoding them using encryption algorithms. The index attribute ensures efficient file searches by enabling the indexing service to catalog file content for quick retrieval.
Furthermore, the temporary attribute marks files for short-term use, allowing for easier cleanup and storage efficiency. The offline attribute enables access to files even without network connectivity, providing continuity in remote or disconnected environments. The sparse attribute optimizes storage for files containing large empty or zero-filled sections by allocating space more efficiently.
The reparse point attribute facilitates advanced file system features such as symbolic links, junction points, and mount points, allowing for file redirection and organization. The integrity attribute assesses the integrity of files by calculating checksum values to detect unauthorized modifications. Lastly, the EFS attribute encrypts files to ensure confidential and secure storage of sensitive data.
By understanding and utilizing these various file attributes, users can enhance file management, safeguard sensitive data, improve system performance, and optimize storage efficiency. Each attribute serves a specific purpose and can be leveraged to customize and control file attributes based on specific needs and requirements.