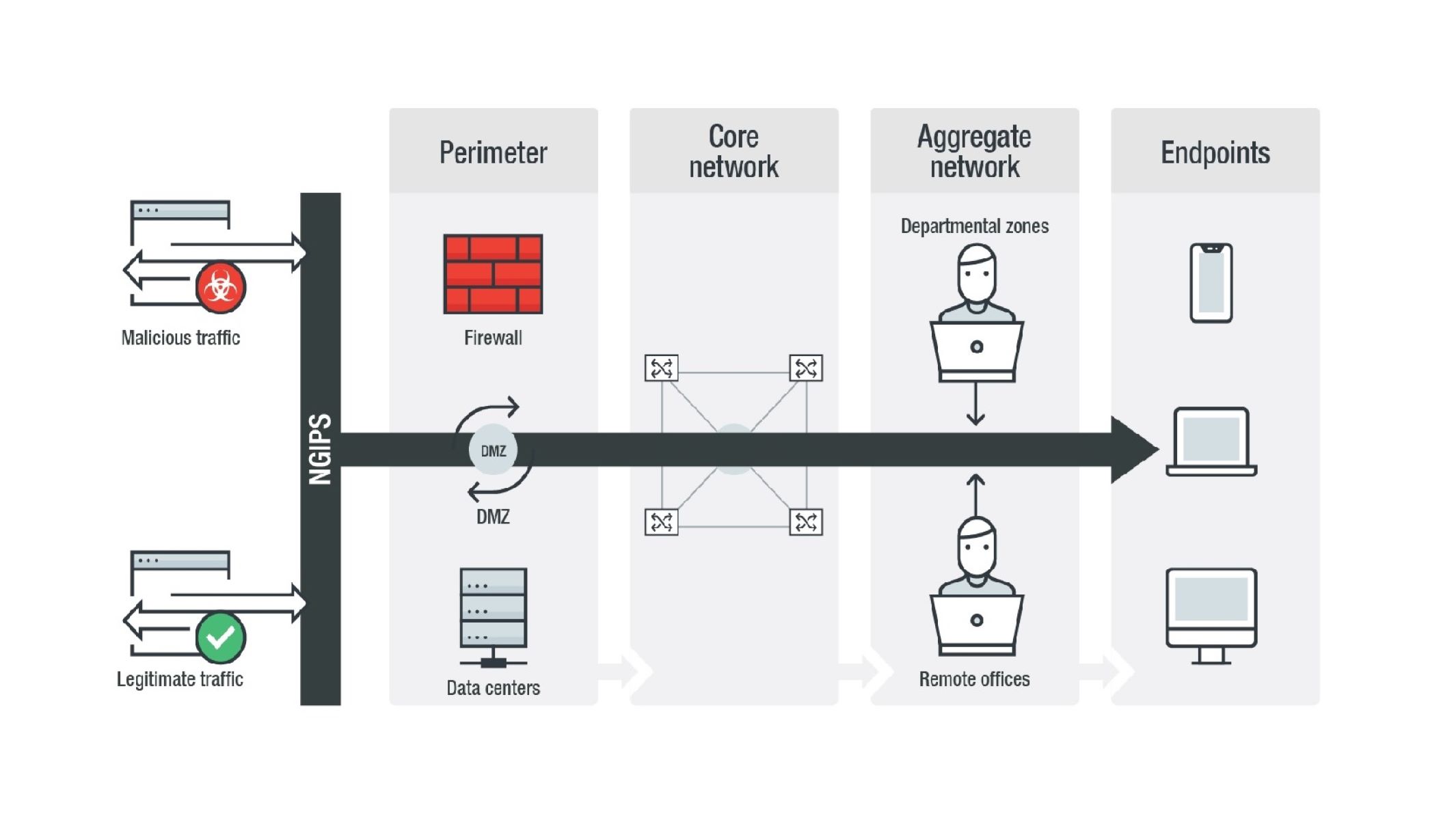
What Is a Perimeter Firewall?
A perimeter firewall is a network security solution that acts as the first line of defense against external threats. It is a specialized type of firewall that is positioned at the edge of a network, forming a protective barrier between the internal network and the outside world.
This type of firewall examines all incoming and outgoing network traffic, carefully analyzing the data packets and determining whether to allow or block them based on predefined security rules and policies. It acts as a filter, preventing unauthorized access to the network and safeguarding sensitive information from potential cyberattacks.
A perimeter firewall controls the flow of network traffic by implementing various security measures such as packet filtering, stateful inspection, and application-level gateway. It ensures that only legitimate and authorized traffic is allowed to pass through, while malicious or suspicious traffic is blocked.
The primary purpose of a perimeter firewall is to protect the network from external threats, including hackers, malware, and unauthorized access attempts. It acts as a barrier that shields the internal network infrastructure, servers, and devices from potential security breaches.
By monitoring and analyzing network traffic, a perimeter firewall helps to identify and mitigate potential security risks, including unauthorized access attempts, malware infections, and suspicious activities. It provides organizations with greater control over their network, allowing them to enforce security policies and regulations effectively.
Moreover, a perimeter firewall plays a crucial role in preventing distributed denial-of-service (DDoS) attacks. It can detect and block excessive traffic from multiple sources, protecting the network from being overwhelmed and ensuring the availability of resources for legitimate users.
How Does a Perimeter Firewall Work?
A perimeter firewall works by examining and filtering network traffic based on predefined rules and policies. It acts as a barrier between the internal network and the outside world, protecting the network infrastructure from potential threats.
When data packets enter the network through the perimeter firewall, they are inspected at the packet level. The firewall analyzes various attributes of the packet, such as source and destination IP addresses, port numbers, and protocols. It compares these attributes against its ruleset to determine whether the packet should be allowed or blocked.
The most basic form of filtering done by a perimeter firewall is packet filtering. In this method, the firewall examines each incoming or outgoing packet and compares its attributes to a set of rules, such as allowing packets from a specific IP range or blocking packets with a certain port number. If the packet matches the criteria, it is allowed to pass through; otherwise, it is dropped.
In addition to packet filtering, perimeter firewalls also employ stateful inspection. This technique keeps track of the state of network connections, allowing the firewall to make more informed decisions when filtering packets. By maintaining a record of the connections, the firewall can differentiate between legitimate packets belonging to an established connection and suspicious or malicious packets.
Another important aspect of perimeter firewalls is application-level gateway functionality. This involves inspecting the actual data within the packets, rather than just examining the packet headers. The firewall can analyze the content of the data and apply more advanced filtering rules based on the protocols being used, such as HTTP or FTP.
To enhance the effectiveness of a perimeter firewall, organizations often implement Intrusion Prevention Systems (IPS) and Virtual Private Networks (VPNs). An IPS can detect and prevent potentially harmful network traffic, such as known attack patterns or suspicious behavior. VPNs, on the other hand, provide a secure and encrypted tunnel for remote users to access the internal network, ensuring that data transmission remains protected.
Overall, a perimeter firewall acts as a crucial line of defense for a network, continuously monitoring and filtering network traffic to protect against unauthorized access, malware, and other external threats. Its functionality and effectiveness can be further customized and enhanced based on the specific security requirements of each organization.
Types of Perimeter Firewalls
Perimeter firewalls come in various types, each offering different features and capabilities. Understanding the different types can help organizations choose the most suitable solution for their network security needs. Here are the most common types of perimeter firewalls:
Hardware Perimeter Firewalls: Hardware firewalls are dedicated devices designed to provide network security. They are typically deployed at the edge of the network and offer robust security features. Hardware firewalls offer high-performance packet filtering, stateful inspection, and application-level gateway functionality. They can handle large amounts of network traffic and often come with additional security features like VPN support and intrusion detection capabilities.
Software Perimeter Firewalls: Software firewalls, also known as host-based firewalls, are software applications installed on individual computers or servers. These firewalls provide protection at the operating system level, allowing users to define and enforce security rules for inbound and outbound network traffic. Software firewalls are commonly used in small-scale environments or for securing individual systems.
Cloud-Based Perimeter Firewalls: Cloud-based firewalls are a newer form of perimeter firewall that are hosted and managed in the cloud. Instead of being deployed on-premises, these firewalls are accessible through a cloud service provider. Cloud-based firewalls offer the advantage of scalability and flexibility, as they can adapt to changing network demands. They are particularly useful for organizations with distributed networks or those utilizing cloud infrastructure.
Next-Generation Firewalls (NGFW): Next-generation firewalls combine the functionalities of traditional firewalls with advanced features like deep packet inspection, application awareness, and intrusion prevention capabilities. NGFWs go beyond simple port and protocol filtering and offer more granular control over network traffic. They can identify and block potential threats in real-time, providing enhanced security for the network.
Unified Threat Management (UTM) Firewalls: UTM firewalls are comprehensive security solutions that integrate several security features into a single device. They combine the functionalities of firewall, intrusion prevention, antivirus, web filtering, and virtual private network (VPN) capabilities. UTM firewalls provide simplified security management and are often used by small and medium-sized businesses that require a cost-effective all-in-one solution.
When choosing a perimeter firewall, it’s important to consider the specific security requirements, network infrastructure, and budget constraints of your organization. Evaluating the features and capabilities of different firewall types can help determine the best fit for your network security needs.
Hardware Perimeter Firewalls
Hardware perimeter firewalls are dedicated devices designed to provide robust network security. These firewalls are typically deployed at the edge of the network and act as the primary defense against external threats. They offer a wide range of features and capabilities to ensure the protection of the network infrastructure.
One of the key advantages of hardware perimeter firewalls is their high-performance packet filtering capability. They can process large amounts of network traffic by examining each packet and comparing it against a set of predefined rules. This allows the firewall to determine whether the packet should be allowed or blocked based on factors such as source and destination IP addresses, port numbers, and protocols.
In addition to packet filtering, hardware firewalls also employ stateful inspection. This technique keeps track of the state of network connections by maintaining a record of established connections. By doing so, the firewall can make more informed decisions when filtering packets, ensuring that legitimate traffic is allowed while suspicious or malicious traffic is blocked.
Another essential feature of hardware perimeter firewalls is application-level gateway functionality. This allows the firewall to analyze the content of the packets and apply more advanced filtering rules based on the protocols being used. For example, the firewall can inspect HTTP traffic to detect and block specific types of web-based attacks.
Hardware firewalls often come with additional security features to enhance protection. Many models offer built-in virtual private network (VPN) support, allowing secure remote access to the internal network. This enables employees to connect to the network securely from remote locations, ensuring the confidentiality and integrity of data transmission.
Intrusion prevention capabilities are another common feature found in hardware perimeter firewalls. These firewalls can detect and prevent potential security breaches by analyzing network traffic for known attack patterns or suspicious behavior. Intrusion prevention systems (IPS) can be seamlessly integrated into hardware firewalls to provide an extra layer of protection.
Hardware perimeter firewalls are designed for scalability and high performance. Organizations can choose models that match the requirements of their network in terms of throughput, number of interfaces, and overall capacity. As the network grows, the hardware firewall can be easily upgraded or expanded to accommodate increased traffic.
Overall, hardware perimeter firewalls are highly effective in providing network security. Their dedicated nature, high-performance capabilities, and additional features make them a preferred choice for organizations looking to protect their network infrastructure from external threats.
Software Perimeter Firewalls
Software perimeter firewalls, also known as host-based firewalls, are software applications that provide network security by protecting individual computers or servers. Unlike hardware firewalls, software firewalls are installed directly on the systems they are intended to protect, allowing users to define and enforce security rules for inbound and outbound network traffic.
One of the advantages of software perimeter firewalls is their flexibility and adaptability. They can be easily customized to meet the specific security requirements of each system or user. By configuring the firewall settings, users can define which applications and services are allowed to communicate over the network, ensuring that only authorized traffic is permitted.
Software firewalls offer packet filtering capabilities, similar to hardware firewalls. They examine each incoming and outgoing packet based on preconfigured rulesets, such as allowing packets from specific IP addresses or blocking packets with specific port numbers. This filtering process helps to prevent unauthorized access and protect the system from potential threats.
In addition to packet filtering, software firewalls often include advanced features like intrusion detection and prevention. These features monitor network traffic for suspicious activity or known attack patterns, providing an additional layer of security. When potential threats are detected, the firewall can take immediate action to block or alert the user, preventing further damage.
Software perimeter firewalls also have the advantage of being able to protect systems outside of the local network, such as laptop computers or remote workers. These firewalls provide security wherever the system is connected to the internet, ensuring that the same level of protection is maintained regardless of location.
One consideration when using software firewalls is the potential impact on system performance. Since the firewall operates directly on the system, it relies on the system’s processing power and resources. In some cases, particularly on older or less powerful systems, the firewall may introduce a slight performance impact. It is important to ensure that the system meets the requirements of the software firewall to ensure efficient and effective protection.
Cloud-Based Perimeter Firewalls
Cloud-based perimeter firewalls are a newer form of network security solution that are hosted and managed in the cloud. Instead of being deployed on-premises, these firewalls are accessible through a cloud service provider, offering organizations a flexible and scalable security option.
One of the key advantages of cloud-based perimeter firewalls is their scalability. Since the firewall is hosted in the cloud, it can easily adapt to changing network demands without requiring additional hardware or infrastructure. This makes cloud-based firewalls particularly useful for organizations with distributed networks or those utilizing cloud infrastructure, as they can effortlessly scale their security measures to match the growth of their network.
Cloud-based firewalls work by intercepting network traffic before it reaches the organization’s internal network. When traffic flows through the cloud-based firewall, it is inspected and filtered based on preconfigured rules and policies. These rules can be updated and modified centrally, allowing for consistent and efficient security management across the entire network.
One of the advantages of cloud-based firewalls is their ability to leverage threat intelligence from multiple sources. Cloud service providers can collect and analyze data from various organizations, allowing them to identify and respond to emerging threats in real-time. This collective intelligence helps to enhance the security measures of cloud-based firewalls, often providing more robust protection compared to individual on-premises firewalls.
Another benefit of cloud-based perimeter firewalls is their ease of deployment and management. Since the firewall is hosted in the cloud, there is no need for organizations to invest in dedicated hardware or perform complex setup procedures. Administrators can access the firewall through a user-friendly interface provided by the cloud service provider, allowing for efficient management and configuration of security policies.
Cloud-based firewalls also offer organizations the advantage of offloading the responsibility of firewall maintenance and updates to the cloud service provider. This reduces the burden on internal IT teams and ensures that the firewall remains up-to-date with the latest security patches and enhancements.
One consideration when using cloud-based perimeter firewalls is the reliance on an internet connection. Organizations must ensure that they have a stable and reliable internet connection to ensure continuous protection. Additionally, it is crucial to choose a reputable and trustworthy cloud service provider to ensure the security and privacy of the network traffic passing through the firewall.
Benefits of Using a Perimeter Firewall
A perimeter firewall offers several benefits for organizations seeking to enhance their overall network security. By acting as the first line of defense against external threats, a perimeter firewall helps protect sensitive data and safeguard the integrity of the network infrastructure. Here are some key benefits of using a perimeter firewall:
Enhanced Network Security: A perimeter firewall plays a crucial role in strengthening network security by monitoring and controlling inbound and outbound network traffic. It acts as a barrier, preventing unauthorized access to the network and filtering out potentially malicious or suspicious traffic. By implementing security measures such as packet filtering, stateful inspection, and application-level gateway, a perimeter firewall helps to mitigate risks and fortify the overall security posture of the network.
Protection Against External Threats: The primary function of a perimeter firewall is to protect the network from external threats, such as hackers, malware, and unauthorized access attempts. It acts as a shield, preventing unauthorized individuals or malicious software from gaining access to the network infrastructure. By carefully analyzing network traffic and enforcing security policies, the firewall helps to identify and block potential security breaches, safeguarding sensitive information from being compromised.
Effective Monitoring and Reporting: Perimeter firewalls offer robust monitoring and reporting capabilities, allowing administrators to gain insights into network traffic and security events. The firewall logs and stores information about network activity, helping administrators to track and investigate potential security incidents. Event logging, alerting, and reporting functionalities enable timely detection and response to potential security breaches, enhancing the overall incident response capability of the organization.
Flexible and Scalable Security Solution: Perimeter firewalls can be tailored to meet the specific security requirements of the organization. They offer flexibility in terms of defining and enforcing security policies, allowing organizations to adjust the level of protection according to their needs. Additionally, perimeter firewalls can scale along with the organization’s growth, accommodating increased network traffic and evolving security demands. This scalability makes perimeter firewalls suitable for small businesses as well as large enterprises.
Regulatory Compliance: Many industries and organizations are subject to compliance regulations regarding the protection of sensitive data. Perimeter firewalls help organizations in achieving compliance by implementing security controls that are necessary to meet regulatory requirements. By establishing a secure perimeter and enforcing access control measures, perimeter firewalls contribute to the overall compliance framework of an organization.
Enhanced Network Security
Enhancing network security is a critical concern for organizations in today’s digital landscape. A strong network security infrastructure helps protect sensitive data, prevent unauthorized access, and ensure the integrity of the network. One essential component of a robust network security strategy is implementing a perimeter firewall. A perimeter firewall plays a vital role in enhancing network security in several ways.
First and foremost, a perimeter firewall acts as a barrier between the internal network and the outside world. It carefully monitors and controls the flow of network traffic entering and exiting the network, inspecting each data packet and making decisions on whether to allow or block it based on predefined security rules. By implementing security measures such as packet filtering, stateful inspection, and application-level gateway, a perimeter firewall helps mitigate risks and fortify the overall security posture of the network.
Packet filtering is a fundamental aspect of perimeter firewalls. It involves analyzing the attributes of each packet, such as source and destination IP addresses, port numbers, and protocols, and comparing them against predefined rules. This process ensures that only legitimate traffic is allowed to pass through and that suspicious or malicious traffic is blocked. By filtering out potentially harmful packets, a perimeter firewall prevents unauthorized access attempts and protects the network from various external threats.
Stateful inspection is another critical feature of perimeter firewalls. This technique keeps track of the state of network connections by maintaining a record of established connections. By doing so, the firewall can differentiate between legitimate packets belonging to an established connection and those that are unauthorized or potentially harmful. Stateful inspection helps ensure that only valid and authorized traffic is allowed into the network, providing an added layer of security.
Furthermore, a perimeter firewall offers application-level gateway functionality, allowing it to inspect the actual data within packets, not just the header information. This deep packet inspection enables the firewall to analyze the content and behavior of specific applications, such as web browsers or email clients, and apply advanced filtering rules. For instance, the firewall can detect and block certain types of web-based attacks or suspicious attachments in emails, strengthening the overall security of the network.
Protection Against External Threats
Protection against external threats is a primary concern for organizations when it comes to network security. With increasing cyber threats and sophisticated attack methods, it is crucial to have robust measures in place to safeguard the network infrastructure. One of the key benefits of implementing a perimeter firewall is the protection it provides against external threats.
A perimeter firewall acts as the first line of defense, preventing unauthorized individuals or malicious software from gaining access to the internal network. By carefully examining and filtering incoming and outgoing network traffic, the firewall can identify and block potential security breaches. This includes blocking unauthorized access attempts, detecting and mitigating malware infections, and preventing various types of cyberattacks.
One of the primary functions of a perimeter firewall is to control and monitor inbound traffic. It evaluates every incoming packet against predefined security rules and policies, analyzing factors such as source IP addresses, port numbers, and protocols. This enables the firewall to differentiate between legitimate traffic and potential threats, promptly blocking any suspicious or unauthorized activity. By doing so, the firewall prevents unauthorized individuals from gaining access to sensitive data or compromising the integrity of the network.
Additionally, a perimeter firewall protects against various external threats, including hackers and cybercriminals. Hackers often attempt to exploit vulnerabilities in the network infrastructure or compromise user accounts to gain unauthorized access. By implementing a perimeter firewall, organizations can establish a strong defense against such attacks, preventing unauthorized individuals from infiltrating the network.
Moreover, perimeter firewalls play a crucial role in preventing malware infections. They can analyze incoming traffic for potential threats, including known malware signatures, malicious URLs, or suspicious file attachments. By detecting and blocking these threats at the network level, the firewall prevents malware from infiltrating the network and causing harm to systems and data.
Perimeter firewalls are also effective in protecting against distributed denial-of-service (DDoS) attacks. These attacks involve overwhelming a network or server with excessive traffic from multiple sources, rendering it inaccessible to legitimate users. Perimeter firewalls can detect and block abnormal traffic patterns associated with DDoS attacks, ensuring the availability of network resources and mitigating the impact of such attacks.
Effective Monitoring and Reporting
Effective monitoring and reporting are crucial aspects of network security management. Organizations need visibility into their network traffic and security events to detect and respond to potential threats in a timely manner. A perimeter firewall plays a significant role in providing effective monitoring and reporting capabilities, enhancing the overall network security posture.
A perimeter firewall logs and stores information about network activity, providing administrators with detailed insights into the network traffic patterns and potential security incidents. By analyzing these logs, administrators can gain a comprehensive understanding of the network’s behavior and identify any abnormal or suspicious activities. Monitoring network traffic allows for the early detection of potential security breaches or violations of security policies.
Not only does a perimeter firewall monitor network traffic, but it also generates alerts and notifications when specific events occur. These alerts can be based on predefined security rules, such as detecting potential intrusion attempts or identifying suspicious behavior. The firewall can notify administrators through email, SMS, or other means, ensuring that security issues are promptly addressed. By receiving real-time alerts, administrators can take immediate action to mitigate potential threats and minimize the impact on the network.
In addition to real-time alerts, a perimeter firewall provides comprehensive reporting capabilities. It can generate reports that summarize network activity, highlight potential security incidents, and identify trends or patterns. These reports provide valuable insights into the overall network security status and help administrators make informed decisions regarding security policies and measures.
Effective monitoring and reporting also facilitate compliance with regulatory requirements. Many industries and organizations are subject to specific security and privacy regulations. A perimeter firewall can generate reports that demonstrate compliance with these regulations, ensuring that organizations meet the necessary security standards. This can simplify the process of auditing and demonstrating compliance with regulatory bodies or industry standards.
Furthermore, the monitoring and reporting capabilities of a perimeter firewall enable organizations to conduct post-incident analysis. In the event of a security breach or incident, the firewall’s logs and reports can be analyzed to determine the root cause, assess the impact, and identify any necessary remediation actions. This post-incident analysis helps organizations strengthen their security measures and prevent similar incidents from occurring in the future.
Flexible and Scalable Security Solution
A flexible and scalable security solution is crucial for organizations to adapt to the ever-evolving threat landscape and changing network requirements. A perimeter firewall offers the flexibility and scalability needed to meet the specific security needs of organizations, regardless of their size or infrastructure.
One of the key advantages of a perimeter firewall is its flexibility in defining and enforcing security policies. Organizations can customize the firewall’s settings based on their unique security requirements. They can specify which types of network traffic are allowed or blocked, set up rules for specific applications or services, and define access controls for different user groups. This flexibility allows organizations to tailor the firewall’s security measures to align with their business processes and protect their most critical assets.
Furthermore, a perimeter firewall offers the flexibility to adapt to changes in the network environment. As organizations grow or undergo infrastructure changes, the firewall can be easily reconfigured or updated to accommodate the evolving network requirements. It can be adjusted to support new applications, services, or network segments, ensuring that the security measures are consistently applied across the entire network infrastructure.
Scalability is another important aspect of a perimeter firewall. Whether an organization is a small business or a large enterprise, the firewall can be scaled accordingly to handle the increasing network traffic and security demands. Organizations can choose firewall models with varying throughput capacities, number of interfaces, and overall capacity, allowing them to upgrade or expand the firewall as their network grows. This scalability ensures that the firewall can continue to provide effective protection without becoming a bottleneck to network performance.
A perimeter firewall can also integrate with other security solutions, such as intrusion prevention systems (IPS) or virtual private networks (VPNs), further enhancing flexibility and scalability. IPS can work in conjunction with the firewall to detect and prevent potential threats in real-time, providing an additional layer of security. VPN support allows remote workers or branch offices to securely access the internal network, ensuring that data transmission remains protected even outside the organization’s physical premises.
Whether it is adapting to changing network requirements, customizing security policies, or accommodating growth, a flexible and scalable perimeter firewall provides organizations with a security solution that can evolve along with their changing needs. It offers the versatility needed to address the unique security challenges faced by organizations, making it a valuable component of a comprehensive network security strategy.
Considerations When Choosing a Perimeter Firewall
Choosing the right perimeter firewall is vital for organizations to ensure effective network security. With numerous options available in the market, organizations need to consider several factors before selecting a perimeter firewall that suits their specific requirements. Here are some key considerations to keep in mind:
Security Requirements: Assessing the organization’s security requirements is crucial when choosing a perimeter firewall. Consider the sensitivity of the data being transmitted, the level of protection needed, and any industry-specific compliance regulations that must be met. Understanding these requirements will help determine the necessary features, such as advanced threat detection, intrusion prevention, or web filtering, required in the firewall solution.
Scalability and Performance: Organizations should choose a perimeter firewall that can handle their current and future network traffic demands. Evaluate the firewall’s throughput capacity, number of interfaces, and overall performance to ensure sufficient scalability. Additionally, considering the impact on network performance is important to avoid any bottlenecks and maintain a smooth operation.
Budget and Cost: Determining a budget for the perimeter firewall solution is essential. Organizations should consider not only the initial cost of the firewall appliance but also the ongoing maintenance and support costs. It is important to strike a balance between the required features and the allocated budget to ensure a cost-effective solution without compromising network security.
Vendor Reputation and Support: Research the reputation and track record of the firewall vendor in the industry. Look for customer reviews, certifications, and industry recognition to ensure the vendor has a strong reputation and offers reliable products. Additionally, consider the level of support provided by the vendor, including technical assistance, software updates, and security patches.
Integration with Existing Infrastructure: Evaluate the compatibility of the perimeter firewall with the organization’s existing network infrastructure and security solutions. Ensure that the firewall can seamlessly integrate with other components, such as intrusion prevention systems, VPNs, or security information and event management systems (SIEM), to enhance the overall security posture.
User-Friendly Interface: Consider the usability and management capabilities of the perimeter firewall. Look for a firewall solution that offers an intuitive and user-friendly interface, making it easy for administrators to configure security policies, monitor network traffic, and generate reports. This helps streamline firewall management and reduces the potential for human error.
Future Proofing: Anticipate future security requirements and technological advancements when selecting a perimeter firewall. Consider the vendor’s commitment to research and development, as well as their ability to keep the firewall solution up-to-date with new security threats and industry standards. Future-proofing the firewall helps organizations avoid the need for frequent replacements or upgrades, ensuring long-term reliability and protection.
Taking these considerations into account allows organizations to make an informed decision when choosing a perimeter firewall that aligns with their specific security needs and budget. By selecting the right firewall solution, organizations can enhance their network security posture and protect their valuable data and resources.
Security Requirements
Assessing and understanding the security requirements of an organization is vital when selecting a perimeter firewall. Different organizations have varying levels of sensitivity and criticality when it comes to their data and network resources. Considering the security requirements allows organizations to choose a firewall solution that aligns with their specific needs and provides the necessary protection. Here are some key factors to consider regarding security requirements:
Data Sensitivity: Determine the level of sensitivity of the data being transmitted across the network. Organizations that deal with highly sensitive information, such as personal or financial data, may require stronger security measures. In such cases, features like advanced threat detection, encryption, and data loss prevention may be necessary to protect sensitive data from unauthorized access or potential breaches.
Compliance Regulations: Evaluate any industry-specific compliance regulations that the organization must adhere to. Certain sectors, such as healthcare or finance, have specific security and privacy standards that must be met. Organizations need to ensure that the chosen perimeter firewall can help comply with these regulations by providing the necessary security controls and functionalities required for compliance.
Threat Landscape: Analyze the current threat landscape and the specific threats that the organization may face. This includes considering the types of potential attacks, such as malware, phishing, or DDoS. Understanding the primary threats allows organizations to select a perimeter firewall that provides effective countermeasures against these specific threats. It may involve features like intrusion prevention, web filtering, or application-level inspection to mitigate the risks effectively.
Remote Access: Assess the need for secure remote access to the network. If remote workers or branch offices need to connect to the internal network, the perimeter firewall should support secure virtual private network (VPN) functionality. This ensures that data transmitted between remote locations and the organization’s network remains encrypted and protected, regardless of the remote user’s location.
User Access Control: Evaluate the organization’s requirements for user access control. Depending on the sensitivity of data and the organization’s security policies, the firewall should have the ability to enforce granular access controls. User authentication methods, user-based policies, and role-based access control (RBAC) should be considered to ensure that only authorized individuals can access specific network resources.
Availability and Redundancy: Consider the requirements for high availability and redundancy. Organizations that cannot afford downtime in their network operations need to ensure that the chosen firewall solution offers features such as failover and redundancy. This ensures continuous and uninterrupted network connectivity even in the event of a hardware failure or disruption.
Scalability: Assess the scalability requirements of the organization’s network. If the organization anticipates future growth or expects increased network traffic, selecting a perimeter firewall that can scale with the organization’s needs is crucial. This allows for seamless expansion of the network security infrastructure without compromising performance or security.
By evaluating these security requirements, organizations can make an informed decision when selecting a perimeter firewall. Understanding the unique security needs allows organizations to choose a firewall solution that aligns with their specific requirements and provides the necessary level of protection.
Scalability and Performance
Scalability and performance are crucial factors to consider when selecting a perimeter firewall for an organization’s network security needs. As network traffic increases and evolves, a firewall must be able to handle the growing demands while providing efficient and effective security measures. Here are key considerations regarding scalability and performance:
Throughput Capacity: Organizations must evaluate the throughput capacity of a perimeter firewall, which refers to the amount of network traffic the firewall can handle without compromising performance. It is important to choose a firewall that can accommodate the current volume of network traffic and has room for future growth. Organizations should consider factors such as the number of users, the size of the network, and the anticipated increase in network traffic.
Number of Interfaces: The number of interfaces a perimeter firewall supports is important, as it determines the connectivity options and the ability to segment the network. Evaluate the organization’s network topology and consider the need for different network segments or VLANs. A firewall with multiple interfaces enables better network segmentation and control, making it easier to manage security policies based on specific network segments.
Hardware Resources: Assess the hardware resources available in the perimeter firewall. High-performance firewalls often have dedicated processors, memory, and storage to efficiently handle security functions. The availability of hardware resources impacts the firewall’s speed and responsiveness when analyzing network traffic and enforcing security rules. Adequate hardware resources ensure that the firewall can perform its security functions effectively without degrading network performance.
Connection Capacity: Consider the connection capacity of the firewall, which refers to the maximum number of concurrent connections it can handle. Organizations with a large number of users, remote workers, or customer-facing applications may require a firewall with high connection capacity. A firewall with the ability to handle more connections ensures that network traffic flows smoothly and does not experience delays or bottlenecks during peak usage.
Latency: Evaluate the latency introduced by the firewall. While it is important for the firewall to provide robust security measures, it should not significantly increase latency in network communications. A firewall with low latency ensures that there is minimal delay in data transmission, supporting real-time applications and maintaining a smooth user experience across the network.
Load Balancing and Redundancy: Consider the firewall’s ability to distribute network traffic evenly across multiple devices, providing load balancing and ensuring high availability. Load balancing efficiently distributes the network load among multiple firewalls, allowing for better performance and scalability. Redundancy ensures that if one firewall fails, another can seamlessly handle the network traffic, avoiding any disruptions to network connectivity.
Management Capabilities: Assess the scalability of the firewall’s management capabilities. With a larger network and increased security demands, the firewall’s management interface should be able to handle the additional workload. The firewall’s management system should provide effective monitoring, configuration, and reporting functionalities without affecting the performance of the firewall or overwhelming network administrators.
Choosing a perimeter firewall with scalability and performance capabilities that meet the organization’s specific needs ensures that the firewall can grow along with the network and effectively protect against evolving threats. Scalability and performance are essential for maintaining a secure and efficient network infrastructure.
Budget and Cost
Considering the budget and cost is a crucial aspect when selecting a perimeter firewall for network security. Organizations need to strike a balance between the level of protection required and the resources allocated for their network security infrastructure. Here are key considerations regarding budget and cost:
Initial Investment: Assess the upfront cost of implementing a perimeter firewall, including the cost of the firewall appliance or software licenses. Firewall solutions can vary widely in price, depending on the features, performance, and vendor. It is essential to allocate a budget for acquiring the firewall solution that meets the organization’s security requirements.
Maintenance and Support: Consider the ongoing costs associated with the maintenance and support of the perimeter firewall. Firewalls require regular updates to ensure they are equipped with the latest security patches and firmware updates. Additionally, evaluating the level of support provided by the vendor, such as technical assistance and access to software updates, is important. Organizations should consider these costs when budgeting for their network security infrastructure.
Scalability and Upgrades: Anticipate potential scalability needs and the associated costs. If the organization expects future growth or increased network traffic, selecting a firewall that can scale accordingly is essential. However, organizations should be mindful of the potential costs of upgrading or expanding the firewall solution as the network expands. Ensure that the scalability options align with the organization’s budget constraints.
Total Cost of Ownership (TCO): Take into account the total cost of ownership (TCO) when evaluating different firewall solutions. The TCO includes not only the initial investment but also the ongoing operating costs, such as maintenance, upgrades, and support. Comparing the TCO of different firewall options over the expected lifespan of the firewall solution can provide a better understanding of the long-term cost implications.
Return on Investment (ROI): Consider the potential return on investment (ROI) associated with the chosen perimeter firewall. While network security is essential, organizations should evaluate the benefits and value that the firewall solution brings compared to its cost. Assess how the firewall solution contributes to the organization’s overall security posture, potential cost savings from avoiding security breaches, compliance requirements, and improved productivity.
Vendor Options: Compare different vendors and their pricing models. Different vendors may offer varying pricing structures or packaging options for their firewall solutions. Consider aspects such as the reputation, expertise, and track record of the vendor. Evaluate whether the vendor offers cost-effective solutions without compromising the necessary security functionalities required by the organization.
Future Cost-Effectiveness: Analyze the long-term cost-effectiveness of the chosen firewall solution. Consider factors such as the vendor’s commitment to research and development, their ability to address emerging threats, and their agility in adapting to industry changes. Choosing a firewall solution that remains up-to-date and capable of addressing future security challenges can potentially reduce long-term costs and increase the overall value of the investment.
By considering the budget and cost factors, organizations can select a perimeter firewall that offers the desired level of protection while staying within the allocated resources. Evaluating the full cost spectrum of implementing and maintaining a firewall solution helps organizations make informed decisions for their network security infrastructure.