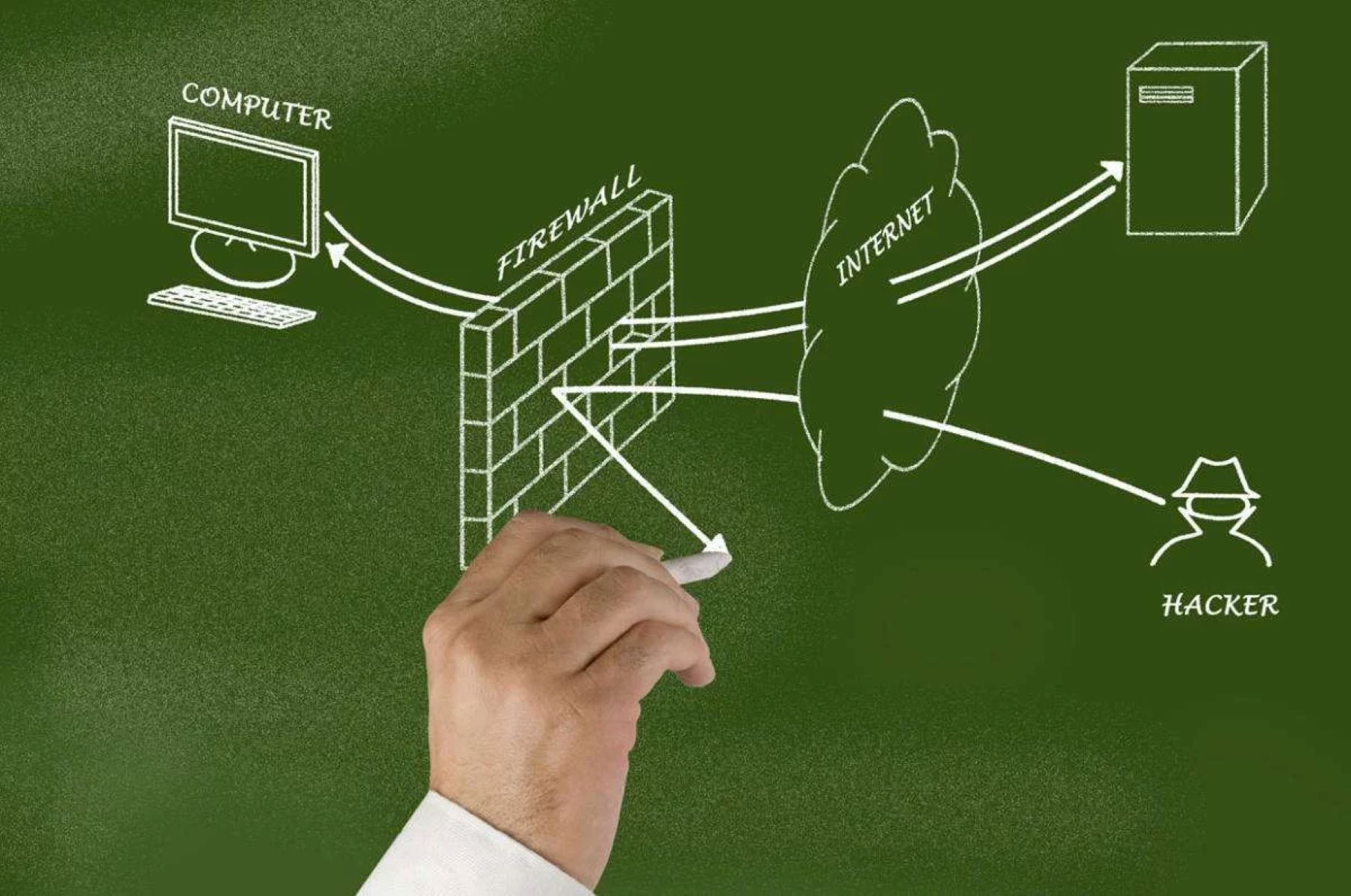
What Is a Network Firewall?
A network firewall is a crucial component of a comprehensive cybersecurity strategy. It acts as a barrier between a trusted internal network and external networks, monitoring and controlling network traffic based on a set of predetermined security rules. Essentially, it serves as the first line of defense against unauthorized access, malicious activities, and potential threats from the internet.
The primary purpose of a network firewall is to establish and enforce security policies, helping to prevent unauthorized communication and ensure the confidentiality, integrity, and availability of data. It accomplishes this by examining every packet of information that passes through it and determining whether to allow or block the transmission based on specific criteria.
Firewalls can be implemented using hardware or software solutions, depending on the specific needs of an organization. Hardware firewalls are physical devices that are installed between the internet and the internal network, while software firewalls are installed on individual computers or servers.
Network firewalls can be configured to perform various types of filtering, including packet-filtering, proxy, next-generation, and unified threat management (UTM) filtering. Each type has its own unique capabilities and strengths.
Overall, network firewalls are essential for protecting the network infrastructure and sensitive information from unauthorized access and potential cyber threats. They play a critical role in safeguarding an organization’s network from malicious activities, such as hacking attempts, malware infections, and data breaches. By implementing a network firewall, organizations can minimize the risk of security incidents and ensure the confidentiality and security of their data.
The Role of a Network Firewall
A network firewall plays a crucial role in maintaining the security and integrity of a computer network. Its primary purpose is to monitor and control incoming and outgoing network traffic, ensuring that only authorized and safe communication is allowed. Here are some key roles that a network firewall serves:
- Access Control: One of the main functions of a network firewall is to enforce access control policies. It examines each packet of data entering or exiting the network and determines whether to allow or deny its transmission based on predefined rules. By blocking unauthorized traffic, a firewall acts as a gatekeeper, preventing malicious entities from gaining access to the network.
- Threat Detection and Prevention: Firewalls are equipped with advanced threat detection mechanisms that can identify and block suspicious or potentially harmful traffic. They use various techniques, such as signature-based detection, anomaly detection, and behavior analysis, to detect and mitigate potential threats, including malware, viruses, and denial-of-service (DoS) attacks.
- Network Monitoring and Logging: Firewalls provide valuable insights into network activity by monitoring and logging all incoming and outgoing traffic. This information is essential for network administrators to analyze and understand any potential security incidents or breaches. Firewall logs can be used for forensic investigations, compliance audits, and identifying patterns of malicious behavior.
- Privacy and Data Protection: Network firewalls play a vital role in ensuring the privacy and protection of sensitive data. By inspecting and filtering network traffic, they prevent unauthorized access to confidential information and protect against data breaches or unauthorized data transfers. Firewalls can also enforce encryption policies and secure communication channels to maintain data integrity.
- Content Filtering: Many firewalls offer content filtering capabilities that allow organizations to control the types of content that can be accessed from their network. This feature enables administrators to block certain websites, restrict access to specific applications or protocols, and prevent the transmission of sensitive data outside the network.
Types of Network Firewalls
Network firewalls come in various types, each with its own unique features and advantages. Here are the most common types of network firewalls:
- Packet-Filtering Firewalls: Packet-filtering firewalls operate at the network layer (Layer 3) of the OSI model. They examine individual packets of data based on predefined rules, such as source and destination IP addresses, port numbers, and protocol types. While these firewalls are fast and efficient, they lack the ability to inspect the content and context of data packets, making them less effective against more sophisticated attacks.
- Proxy Firewalls: Proxy firewalls act as intermediaries between clients and servers, intercepting and analyzing network traffic on behalf of the end devices. They establish separate connections with both the client and server, making it difficult for attackers to directly access the internal network. Proxy firewalls provide advanced security features, including content filtering, application-level inspection, and better control over network traffic. However, they can introduce latency and may not be suitable for high-performance networks.
- Next-Generation Firewalls: Next-generation firewalls (NGFWs) combine the functionalities of traditional firewalls with additional advanced features, such as application-level inspection, intrusion prevention systems (IPS), and deep packet inspection (DPI). NGFWs provide enhanced visibility and control over network traffic by identifying and blocking threats based on the application, user, content, and other contextual information. They offer better protection against modern and complex threats but may require more processing power and configuration.
- Unified Threat Management (UTM) Firewalls: UTM firewalls integrate multiple security features into a single device, combining the functionalities of firewalls, intrusion detection and prevention systems (IDS/IPS), antivirus software, virtual private networks (VPNs), and more. These all-in-one solutions are cost-effective and suitable for small to medium-sized businesses that require comprehensive security without the complexity of managing multiple devices. However, due to their multifunctionality, UTM firewalls may not offer the same level of performance and customization as specialized devices.
It is important to assess your specific security requirements and choose the appropriate type of network firewall that aligns with your organization’s needs and budget. Additionally, regular updates, patches, and proper configuration are essential to ensure the effectiveness and reliability of any network firewall solution.
Packet-Filtering Firewalls
Packet-filtering firewalls, also known as network layer firewalls, are one of the first types of firewalls to be developed. They operate at the network layer (Layer 3) of the OSI model and examine individual packets of data based on predefined rules. These rules typically include information such as source and destination IP addresses, port numbers, and protocol types.
The primary function of packet-filtering firewalls is to determine whether to allow or block network traffic based on these predefined rules. This filtering process occurs as each packet enters or exits the network. If a packet matches an allowable rule, it is forwarded to its destination; otherwise, it is discarded.
The key advantages of packet-filtering firewalls are their simplicity and efficiency. They are relatively quick at examining packets, as they only inspect the packet header information. This makes them suitable for high-speed networks where low latency is crucial.
However, packet-filtering firewalls have limitations. They lack the ability to inspect the content and context of data packets, making them less effective against more sophisticated attacks. For example, if a packet is allowed based on its source IP address, an attacker may be able to exploit this trust and send malicious data within allowed packets.
Another limitation of packet-filtering firewalls is that they do not have built-in support for tracking and maintaining stateful connections. This means they cannot differentiate between packets that are part of an established communication session and those that are initial connection attempts. As a result, they may allow unwanted traffic to enter the network, leading to potential security risks.
To mitigate these limitations, administrators can implement additional security measures, such as combining packet-filtering firewalls with other types of firewalls or using intrusion detection systems (IDS) to detect and prevent malicious activities.
Proxy Firewalls
Proxy firewalls, also known as application layer firewalls, provide an extra layer of security by acting as intermediaries between clients and servers. Unlike packet-filtering firewalls that operate at the network layer, proxy firewalls work at the application layer (Layer 7) of the OSI model.
When a client initiates a connection with a server, the proxy firewall intercepts the traffic and establishes a separate connection with the client and server on behalf of each other. This makes it challenging for attackers to directly access the internal network since they interact with the proxy firewall rather than the actual end devices.
One of the key advantages of proxy firewalls is their ability to inspect and filter traffic at the application level. They have a deep understanding of network protocols and can analyze the content and context of data packets, including application-specific data. This allows them to enforce granular security policies based on more than just source and destination IP addresses or port numbers.
In addition to providing enhanced security, proxy firewalls offer other benefits. They can improve performance by caching frequently requested content. When a client requests information, the proxy firewall can serve the requested data from its cache rather than fetching it from the server, reducing network latency and improving efficiency.
Furthermore, proxy firewalls can enable content filtering capabilities. Administrators can define policies to block specific websites, restrict access to certain applications or protocols, and prevent the transmission of sensitive information outside the network. This allows organizations to enforce security policies and protect against potential data leaks or compliance violations.
However, proxy firewalls can introduce some disadvantages as well. They may introduce additional latency due to the extra processing and analysis required for each connection. This can impact network performance, especially in high-volume environments. Additionally, proxy firewalls may not be suitable for environments with complex network architectures or where high-speed data transfer is required.
Despite these limitations, proxy firewalls remain an essential tool in network security, providing advanced application-level inspection and control to safeguard organizations from various threats.
Next-Generation Firewalls
Next-generation firewalls (NGFWs) represent a significant advancement in network security technology. They combine the functionalities of traditional firewalls with additional features that provide more comprehensive protection against modern and sophisticated threats.
NGFWs operate at the network layer (Layer 3) and the application layer (Layer 7) of the OSI model, allowing them to inspect network traffic at both levels. They utilize various techniques, such as stateful packet inspection, intrusion prevention systems (IPS), and deep packet inspection (DPI), to provide enhanced visibility and control over network traffic.
One of the key features of NGFWs is application-level inspection. Unlike traditional firewalls that only examine packet headers, NGFWs have a deep understanding of network protocols and can analyze the content and context of data packets. This enables them to identify and block potential threats based on the application, user, content, and other contextual information.
In addition, NGFWs incorporate IPS functionality, which allows them to detect and prevent known vulnerabilities and attacks. They use signature-based detection and behavior analysis to identify suspicious patterns and block malicious traffic in real-time. By combining firewall and IPS capabilities, NGFWs offer a proactive defense mechanism against a wide range of threats.
NGFWs also employ deep packet inspection (DPI) to scrutinize network packets at a granular level. This enables them to detect and block specific types of content or specific actions within an application. For example, they can identify and block file transfers containing sensitive data, prevent unauthorized access to certain websites or applications, and enforce data loss prevention policies.
Another advantage of NGFWs is the ability to integrate with threat intelligence feeds and security information and event management (SIEM) systems. This allows them to receive up-to-date information about emerging threats and indicators of compromise, enhancing their ability to identify and mitigate potential attacks.
However, it is important to note that NGFWs may require more processing power and configuration compared to traditional firewalls due to their advanced features. They may also involve a higher cost, both in terms of licensing and hardware requirements. Organizations considering the implementation of NGFWs should carefully assess their security requirements, performance needs, and budget constraints.
Unified Threat Management (UTM) Firewalls
Unified Threat Management (UTM) firewalls offer comprehensive security solutions by integrating multiple security features into a single device. They combine the functionalities of traditional firewalls with other security technologies, such as intrusion detection and prevention systems (IDS/IPS), antivirus software, virtual private networks (VPNs), and content filtering.
UTM firewalls provide a centralized approach to network security, making them particularly suitable for small to medium-sized businesses that require robust protection without the complexity of managing multiple devices. By consolidating multiple security functions into a single device, UTM firewalls simplify deployment, configuration, and ongoing maintenance.
Here are some key features typically found in UTM firewalls:
- Firewall: UTM firewalls have the core firewall capabilities found in traditional firewalls, such as packet inspection, access control, and network security policy enforcement.
- Intrusion Detection and Prevention: UTM firewalls include IDS/IPS functionality, which helps detect and prevent known vulnerabilities and attacks by analyzing network traffic patterns and identifying suspicious behavior.
- Antivirus and Antimalware: UTM firewalls incorporate antivirus and antimalware engines to scan incoming and outgoing network traffic for malware, viruses, and other malicious content, providing an additional layer of protection.
- Virtual Private Networks (VPNs): UTM firewalls often include VPN capabilities, allowing secure remote access for users connecting to the network from outside locations, ensuring sensitive data remains encrypted and protected.
- Content Filtering: UTM firewalls enable organizations to enforce content filtering policies, preventing access to malicious or inappropriate websites, restricting specific applications, and controlling data transmission.
- Centralized Management: UTM firewalls typically provide centralized management interfaces, allowing administrators to configure and monitor all security functions from a single console, simplifying the overall management process.
While UTM firewalls offer convenience and a wide range of security features, they may not provide the same level of performance and customization as specialized devices. Organizations with advanced networking needs or high-performance requirements may opt for separate dedicated firewall and security devices.
It is important to carefully evaluate the specific security requirements of an organization and consider factors such as scalability, performance, ease of management, and cost-effectiveness when deciding whether a UTM firewall is the right solution for their network security needs.
Intrusion Detection System (IDS) vs. Firewall
Both intrusion detection systems (IDS) and firewalls are essential components of network security, but they serve different purposes and play different roles in protecting against unauthorized access and potential threats.
A firewall acts as a barrier between a trusted internal network and external networks, monitoring and controlling network traffic based on predefined security rules. Its primary function is to prevent unauthorized communication and determine whether to allow or block the transmission of packets based on specific criteria, such as source and destination IP addresses, port numbers, and protocol types. Firewalls provide a first line of defense by enforcing access control policies and ensuring the confidentiality, integrity, and availability of data.
On the other hand, an intrusion detection system (IDS) monitors network and system activities for signs of potential malicious activity or policy violations. IDSs are designed to detect and alert administrators to potential security incidents, such as unauthorized access attempts, malware infections, or unusual network behavior. While firewalls prevent unauthorized access, IDSs provide additional visibility into the network, helping identify and investigate security breaches.
The key differences between IDS and firewalls can be summarized as follows:
- Function: Firewalls focus on preventing unauthorized access by examining and controlling network traffic based on predefined rules. IDSs, on the other hand, monitor network activities to detect and alert administrators about potential security incidents.
- Level of Analysis: Firewalls operate at the network layer and primarily inspect packet headers, while IDSs operate at a higher layer, analyzing network and system activities at a more granular level, including the content and context of data packets.
- Response Capability: Firewalls can actively block or allow network traffic based on predefined rules. IDSs do not actively block traffic but provide alerts to administrators, allowing them to take appropriate action in response to potential security incidents.
- Preventive vs. Detective: Firewalls are preventive security measures, aiming to stop unauthorized access and maintain network security. IDSs are detective measures, helping identify and investigate security breaches after they have occurred.
- Complementary Role: Firewalls and IDSs are often used in conjunction with each other to provide a more robust network security infrastructure. Firewalls establish a first line of defense, while IDSs provide additional visibility and threat detection capabilities.
Ultimately, both IDSs and firewalls are essential components of a comprehensive network security strategy. While firewalls focus on prevention by controlling network traffic, IDSs provide an additional layer of detection and response, helping organizations identify and investigate potential security incidents.
How Network Firewalls Work
Network firewalls work by monitoring and controlling the flow of network traffic entering and leaving a network. They use a set of predefined security rules to determine whether to allow or block the transmission of packets based on specific criteria, such as source and destination IP addresses, port numbers, and protocol types. Here’s a general overview of how network firewalls work:
- Packet Inspection: When a packet travels through a network firewall, it examines the packet header information, including the source and destination IP addresses, port numbers, and protocol type. This process is known as packet inspection or packet filtering. The firewall compares the packet against its predefined rules to determine whether the packet should be allowed or blocked.
- Access Control: Based on the results of the packet inspection, the firewall enforces access control policies. If the packet matches an allowable rule, it is forwarded to its destination. If the packet violates any rules or matches a rule that is meant to block certain traffic, the firewall will discard or block the packet, preventing it from entering or leaving the network.
- Stateful Inspection: In addition to packet filtering, many network firewalls employ stateful inspection. Stateful firewalls keep track of the state of network connections, distinguishing between new connection requests and established connections. By maintaining session state, the firewall can determine whether a packet is part of an existing connection or a new connection attempt. This helps prevent unwanted traffic from entering the network and enhances security.
- Logging and Monitoring: Network firewalls provide logging and monitoring capabilities, allowing administrators to track and analyze network traffic. Firewalls log information about allowed and blocked packets, as well as other network activities. Monitoring firewall logs can help identify potential security incidents, track network usage patterns, and aid in forensic investigations.
- Security Updates and Configuration: To maintain their effectiveness, network firewalls require regular updates and ongoing configuration. Updates include security patches, firmware upgrades, and the latest threat intelligence feeds. Firewall rules and policies should also be regularly reviewed and adjusted to align with changing security requirements.
By implementing a network firewall, organizations can establish a secure boundary between the internal network and external networks, protecting against unauthorized access, malicious activities, and potential threats. Firewalls are a critical component of a layered security approach, providing an initial line of defense to safeguard network infrastructure and sensitive information.
Stateful vs. Stateless Firewalls
When it comes to network security, there are two main types of firewalls: stateful and stateless firewalls. While both serve the purpose of controlling and monitoring network traffic, there are notable differences in how they operate and the level of security they provide.
Stateful Firewalls:
A stateful firewall, also known as a dynamic packet-filtering firewall, goes beyond simple packet inspection. It maintains a state table that keeps track of the state of network connections. This means the firewall can differentiate between new connection requests and established connections, allowing it to make more informed decisions about packet transmission.
A stateful firewall examines not only the header information of each packet but also the content and context of the data. It considers factors such as source and destination IP addresses, port numbers, protocol types, and the sequence of packets within a connection. This enables the firewall to permit or deny packets based on the established state of a connection.
The advantage of a stateful firewall is that it offers more robust security. By keeping track of the state of connections, it can prevent malicious activities, such as unauthorized access or data injection attempts. It can also detect and block certain types of attacks, including unauthorized session hijacking or spoofing.
Stateless Firewalls:
Conversely, a stateless firewall, also known as a static packet-filtering firewall, examines each packet in isolation, without considering the context or the state of the connection. It filters packets based solely on predefined rules that specify criteria such as source IP address, destination IP address, port numbers, and protocol types.
Stateless firewalls are typically faster and more efficient compared to stateful firewalls because they do not need to maintain a state table. However, their simplicity comes at the cost of reduced security. Stateless firewalls cannot detect or prevent certain types of attacks that rely on inspecting the state or content of packets. They are also more susceptible to session hijacking or IP spoofing where an attacker can impersonate a trusted IP address.
Choosing the Right Firewall:
The choice between a stateful and stateless firewall depends on the specific security requirements and network environment. Stateful firewalls are ideal for environments that require higher security levels or handle sensitive data. They provide more advanced threat detection and protection capabilities. On the other hand, stateless firewalls are more suitable for simple network configurations or scenarios where speed and efficiency are critical.
In practical terms, many modern firewalls incorporate both stateful and stateless filtering capabilities, offering a balance between security and performance. These next-generation firewalls combine the benefits of stateful inspection with additional features like intrusion prevention systems (IPS), deep packet inspection (DPI), and application-level filtering to provide a comprehensive security solution.
Ultimately, the choice of firewall depends on the unique needs and risk tolerance of an organization. A thorough evaluation of the network environment and a clear understanding of security requirements are crucial in selecting the appropriate type of firewall.
Important Features of a Network Firewall
A network firewall is a critical component of an organization’s cybersecurity infrastructure. It plays a pivotal role in securing networks by monitoring and controlling the flow of data traffic. To effectively protect against unauthorized access and potential threats, network firewalls incorporate various important features. Here are some key features to consider when evaluating a network firewall:
- Packet Filtering: This feature allows the firewall to examine packets of data based on specific criteria such as source and destination IP addresses, port numbers, and protocol types. By filtering packets, the firewall can determine whether to allow or block the transmission based on predefined security policies.
- Application-Level Inspection: Application-level inspection, also known as deep packet inspection (DPI), enables the firewall to analyze the content and context of packets. This feature allows the firewall to detect and prevent specific threats or unauthorized activities based on the application layer protocols or specific content within the packets.
- Intrusion Detection and Prevention: Many advanced firewalls incorporate intrusion detection and prevention systems (IDS/IPS). These systems detect and alert administrators about potential security incidents, such as unauthorized access attempts, malware infections, or suspicious network behavior. IPS functionality takes it a step further by actively blocking and pre-emptively preventing such attacks.
- Virtual Private Network (VPN) Support: VPN support allows the firewall to establish secure encrypted tunnels for remote access or site-to-site connections. This feature ensures that data transmitted over the network remains confidential and protected from eavesdropping or unauthorized access.
- Content Filtering: Content filtering capabilities enable the firewall to enforce policies controlling the types of content that can be accessed from the network. It allows administrators to block specific websites, restrict access to certain applications or protocols, and prevent the transmission of sensitive data.
- Logging and Reporting: Effective network firewalls provide logging and reporting functionalities, allowing administrators to monitor and analyze network traffic, security events, and policy violations. Comprehensive logging capabilities assist in forensic investigations, compliance audits, and the identification of potential security incidents.
- Centralized Management: Centralized management interfaces ease the configuration, monitoring, and administration of network firewalls. This feature allows administrators to have a unified view of all firewall devices, streamline policy management, and ensure consistent enforcement of security rules across the network.
- Automatic Updates and Threat Intelligence: Firewalls should regularly receive updates to ensure they can detect and protect against the latest threats. Automatic updates keep the firewall’s security features up to date, including the antivirus signatures, intrusion detection signatures, and other security intelligence feeds.
- High Availability and Load Balancing: For mission-critical systems, firewalls with high availability and load balancing capabilities ensure uninterrupted network security. Redundancy and failover mechanisms minimize downtime by seamlessly switching traffic to backup firewalls in the event of hardware failures or maintenance.
These features collectively contribute to the effectiveness and efficiency of a network firewall in protecting the organization’s network infrastructure, sensitive data, and critical assets. Evaluating these features can help organizations choose a firewall solution that aligns with their specific security requirements and enables them to respond effectively to evolving threats.
Common Network Firewall Configurations
Network firewalls can be configured in various ways to meet the specific security needs and network architecture of an organization. The configuration of a firewall plays a crucial role in determining the level of protection it provides and how it interacts with network traffic. Here are some common network firewall configurations:
- Single Firewall Configuration: In this configuration, a single firewall acts as the primary point of defense between the internal network and the internet. It is placed at the network perimeter to monitor and control all incoming and outgoing traffic. While this setup provides a basic level of protection, it may not be sufficient for larger or more complex networks.
- Dual Firewall Configuration: A dual firewall configuration, also known as a “screened subnet” or “DMZ” configuration, provides an additional layer of security. It involves placing a second firewall, often referred to as a demilitarized zone (DMZ) firewall, between the external network and the internal network. This setup allows for more granular control over incoming and outgoing traffic by segregating the network into different security zones.
- Multi-Layer Firewall Configuration: A multi-layer firewall configuration combines multiple firewalls, each operating at different network layers, to create a more robust and comprehensive security infrastructure. For example, an organization might deploy a stateful packet-filtering firewall at the network layer to handle basic access control, while using a proxy firewall or next-generation firewall at the application layer for advanced inspection and content filtering.
- High Availability (HA) Firewall Configuration: High availability firewall configurations involve deploying redundant firewall devices to ensure continuous network security in the event of hardware failures or maintenance. Redundant firewalls are synchronized to ensure that when one fails, the other seamlessly takes over, minimizing downtime and maintaining uninterrupted network protection.
- Virtual Firewall Configuration: Virtual firewall configurations leverage virtualization technology to provide security for virtualized environments. Virtual firewalls are deployed as software instances, allowing for the isolation and protection of virtual networks and ensuring that virtual machines maintain appropriate security policies.
- Remote Access VPN Configuration: Firewalls can also be configured to provide secure remote access to a network through virtual private network (VPN) connections. This configuration enables authorized users to connect securely to the internal network from remote locations, ensuring secure transmission of data over untrusted networks.
- Perimeter and Internal Firewall Configuration: To enhance security, organizations may implement both perimeter firewalls and internal firewalls. Perimeter firewalls protect the network from external threats, while internal firewalls segment the internal network into zones, enforcing stricter access control policies and preventing lateral movement in case of a breach.
The choice of network firewall configuration depends on factors such as the size and complexity of the network, the level of security required, and the specific security policies and compliance requirements of the organization. It is important to regularly review and update firewall configurations to adapt to changing network environments and emerging threats.
Best Practices for Configuring a Network Firewall
Configuring a network firewall properly is essential for ensuring effective network security. Implementing best practices not only enhances the firewall’s ability to protect against unauthorized access and potential threats but also helps avoid misconfigurations that could leave the network vulnerable. Here are some best practices for configuring a network firewall:
- Define Clear Security Policies: Clearly define and document the organization’s security policies, including network access control, acceptable use, and content filtering. These policies will provide a foundation for configuring firewall rules and ensuring consistent enforcement.
- Minimize Rule Complexity: Keep firewall rule sets as simple as possible to avoid confusion and possible misconfigurations. Regularly review and remove any unnecessary or outdated rules to maintain a clean and manageable rule base.
- Adopt the Principle of Least Privilege: Apply the principle of least privilege when creating firewall rules. Only allow the minimum necessary access for each network service or user. Limit inbound connections to only the required ports and protocols to reduce potential attack surfaces.
- Implement Deny-All Rule: Consider implementing a “deny-all” rule at the end of the rule set as a catch-all measure. This ensures that any traffic not explicitly allowed is blocked, reducing the risk of unauthorized access.
- Regularly Update and Patch: Keep the firewall up to date with the latest firmware, security patches, and vendor updates. Regularly check for updates and apply them promptly to address any known vulnerabilities or weaknesses.
- Enable Logging and Monitoring: Configure logging and monitoring features to log firewall activities and generate alerts for security events or policy violations. Regularly review and analyze log data to detect any suspicious activities or potential threats.
- Test and Validate Rules: Before deploying or modifying firewall rules, thoroughly test and validate them in a controlled environment. Conduct regular security assessments and penetration testing to identify any potential issues or gaps in the firewall’s configuration.
- Backup and Disaster Recovery: Regularly back up the firewall’s configuration and settings to enable easy recovery in the event of a failure or misconfiguration. Store backups in secure locations to prevent unauthorized access or loss.
- Implement Change Management Process: Establish a formal change management process for firewall configuration changes. Require proper authorization and documentation for any modifications made to the firewall rules or configurations.
- Stay Informed and Educated: Stay up to date with the latest network security trends, emerging threats, and industry best practices. Continuously educate yourself and your team about new firewall features and technologies to ensure that your firewall configuration remains effective.
Following these best practices will help ensure that the network firewall is configured securely and efficiently, providing effective protection for the organization’s network infrastructure and data assets.
Benefits and Limitations of Network Firewalls
Network firewalls offer several benefits in protecting against unauthorized access and potential threats. However, they also have limitations that organizations should be aware of. Understanding both the benefits and limitations of network firewalls is crucial for implementing an effective network security strategy. Here are some key benefits and limitations:
Benefits:
- Access Control: Perhaps the most significant benefit of network firewalls is their ability to enforce access control policies. By examining and filtering network traffic, firewalls determine which packets are allowed or blocked based on predetermined rules, preventing unauthorized communication.
- Threat Detection and Prevention: Firewalls offer threat detection and prevention capabilities. They can detect and block known threats, such as malware, viruses, and hacking attempts. Firewalls equipped with intrusion detection/prevention systems (IDS/IPS) provide additional layers of security by detecting and alerting administrators about potential security incidents.
- Content Filtering and Application Control: Network firewalls can enforce content filtering policies, restricting access to specific websites, applications, or protocols. They can also prevent the transmission of sensitive data outside the network, helping organizations maintain data privacy and compliance.
- Network Monitoring and Logging: Firewalls provide valuable visibility into network traffic through logging and monitoring features. Administrators can analyze logs to identify security incidents, track network usage patterns, and conduct forensic investigations in the event of a breach.
- Protection for Remote Access: Firewalls support secure remote access through virtual private network (VPN) connections. This allows authorized users to connect to the network securely from remote locations, ensuring data confidentiality even over untrusted networks.
Limitations:
- Encrypted Traffic: Firewalls face challenges in inspecting and filtering encrypted traffic. While newer firewalls have capabilities to handle encrypted traffic, encrypted data presents a limitation in examining the content for potential threats.
- Advanced Threats: Firewalls may struggle with detecting and preventing advanced threats, such as zero-day exploits or sophisticated targeted attacks. While some firewalls have advanced features like behavioral analysis, additional cybersecurity measures are necessary to mitigate these advanced threats.
- False Positives and False Negatives: Firewalls can generate false positives and false negatives, leading to either blocking legitimate traffic or allowing malicious traffic. Fine-tuning firewall rules and constant monitoring are necessary to minimize these potential errors.
- Unauthorized Insider Threats: Firewalls are primarily designed to protect against external threats. They offer limited protection against insider threats, such as malicious actions by employees with legitimate access to the network. Additional security measures, such as access controls and user monitoring, are needed to mitigate such risks.
- Operational Complexity: Configuring, managing, and maintaining firewalls require expertise and ongoing attention. Organizations must allocate resources for regular updates, patches, rule reviews, and monitoring to keep firewalls effective and up to date.
While network firewalls provide essential security features, they are not a stand-alone solution. Organizations should adopt a layered and holistic approach to network security by combining firewalls with other security measures, such as intrusion detection/prevention systems, endpoint protection, and user education, to address the limitations and build a robust defense against evolving threats.
Choosing the Right Network Firewall for Your Organization
Choosing the right network firewall is critical for establishing a strong network security infrastructure tailored to the specific needs of your organization. With numerous firewall options available, it is important to consider several key factors before making a decision. Here are some factors to consider when choosing a network firewall:
- Security Requirements: Evaluate your organization’s security requirements in terms of data sensitivity, industry regulations, and potential threats. Determine the level of protection needed, such as basic packet filtering, advanced threat detection, content filtering, or intrusion prevention.
- Scalability: Consider the scalability of the firewall solution. Assess whether it can accommodate growing network demands, such as an increasing number of users, expanding branch offices, or emerging technologies.
- Performance: Ensure that the firewall solution can handle the expected network traffic without causing latency or bottlenecks. Look for firewalls with high throughput capabilities and optimized performance for your specific network requirements.
- Technical Expertise: Assess the technical expertise within your organization. Determine whether you have the resources and skills to handle complex firewall configurations, updates, and ongoing management. If not, consider managed firewall services or outsourcing to a qualified third-party provider.
- Vendor Reputation and Support: Research and evaluate the reputation and track record of different firewall vendors. Consider their expertise, industry recognition, and the availability of reliable support and timely firmware updates to ensure long-term support and protection.
- Integration Capabilities: Assess how well the firewall integrates with your existing network infrastructure, including switches, routers, and other security solutions. Look for compatibility with virtualization technologies, cloud environments, and centralized management platforms if these are relevant to your organization.
- Usability and Management Interface: Consider the usability and intuitiveness of the firewall’s management interface. A well-designed and user-friendly interface can simplify the configuration and ongoing management of the firewall, reducing the likelihood of misconfigurations.
- Financial Considerations: Evaluate the total cost of ownership, including the initial purchase cost, licensing fees, maintenance, and ongoing support. Consider the long-term value and return on investment (ROI) the firewall solution can provide for your organization.
- Reviews and Recommendations: Seek feedback from industry experts, security professionals, and user reviews to gain insights into the strengths and weaknesses of different firewall solutions. Consider their experiences and recommendations when making your decision.
By carefully considering these factors, you can select a network firewall that aligns with your organization’s security requirements, network infrastructure, and resource capabilities. It is also important to regularly reassess your firewall needs as your business evolves and the threat landscape changes, ensuring that your security measures remain effective and up to date.