What Is a PEM File?
A PEM (Privacy-Enhanced Mail) file is a format used to store and transport cryptographic security keys, certificates, and associated data. It is widely used in the field of secure communication protocols, such as SSL/TLS (Secure Sockets Layer/Transport Layer Security) for securing websites, email systems, and other network-based applications.
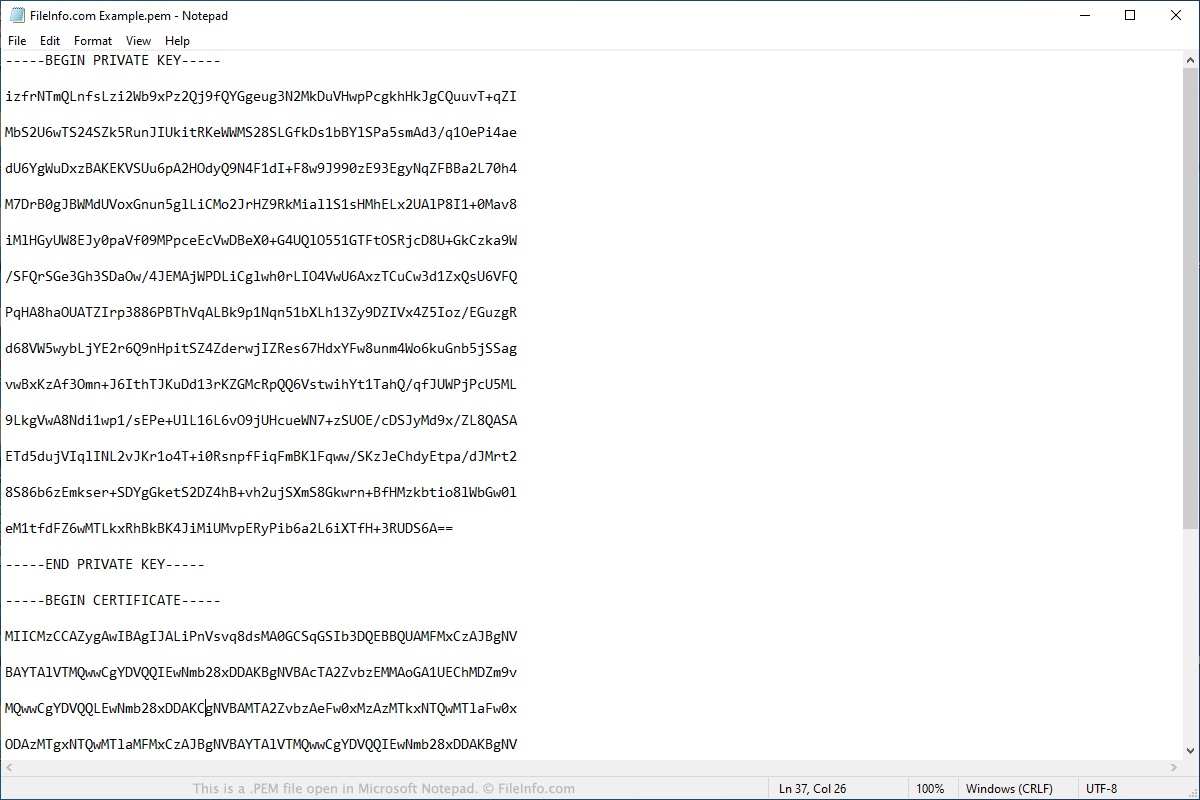
A PEM file is a text file that can be opened and read by humans, as it contains ASCII-encoded data. It is named after the original use case, which was to secure email communication. However, over time, the format has evolved to be used for various cryptographic purposes.
PEM files typically have a “.pem” file extension, although they can also use extensions like “.crt”, “.key”, or “.p12”. The content of a PEM file is encoded using the Base64 algorithm, making it easy to transfer and share between different systems and applications.
PEM files are organized into sections, each delimited by “—–BEGIN” and “—–END” markers. These markers indicate the type of data contained within the section, such as certificates, private keys, or certificate signing requests (CSRs). The actual data is enclosed between these markers, and the sections can be arranged in any order within the file.
When opened in a text editor, a PEM file may look like a jumble of characters, but it contains essential cryptographic information that enables secure communication. The file can be accessed, read, and modified by authorized users and applications, facilitating the implementation of various security measures.
In the next section, we will explore what PEM stands for and delve deeper into the purpose and use cases of PEM files in the realm of secure communication protocols.
What Does PEM Stand For?
PEM stands for Privacy-Enhanced Mail. It is a file format that was originally designed to secure email communication. However, its usage has expanded beyond emails to include various cryptographic operations and secure communication protocols.
The term “Privacy-Enhanced Mail” was coined in the 1990s when the IETF (Internet Engineering Task Force) introduced the PEM format as a standardized way to protect the privacy and security of email transmissions. The format aimed to provide a secure communication channel between email clients and servers, ensuring that sensitive information transmitted over the internet remained confidential and tamper-proof.
While PEM was initially created for email security, its flexible design made it adaptable for other cryptographic purposes as well. Its success in securing email communication led to its adoption and incorporation into other security protocols and applications.
PEM files, also known as PEM encodings, enable the storage and transport of cryptographic keys, certificates, and other related data. These files use ASCII encoding, allowing them to be easily read and manipulated by humans. The Base64 algorithm is used to convert binary data into a textual format within the PEM file.
Today, PEM files are widely used in the implementation of SSL/TLS protocols to secure websites, web applications, and other network-based services. They serve as containers for cryptographic information, including public and private keys, X.509 certificates, certificate signing requests (CSRs), and intermediate certificates.
PEM files have become a standard format for interoperability between different security systems, providing a common language for secure communication. They simplify the sharing and transport of cryptographic data, ensuring compatibility across platforms and applications.
In the following sections, we will explore the purpose of PEM files and how they are used in SSL/TLS protocols, as well as the differences between PEM and other certificate formats.
What Is the Purpose of a PEM File?
The purpose of a PEM file is to store and transport cryptographic security keys, certificates, and associated data in a format that is readable by both humans and machines. PEM files serve as containers for essential information used in secure communication protocols like SSL/TLS.
One of the primary purposes of a PEM file is to securely store private keys. Private keys are used in asymmetric encryption algorithms to decrypt data that has been encrypted with the corresponding public key. They play a crucial role in establishing secure connections between clients and servers, ensuring that data transmitted over the network remains confidential.
PEM files are also used to store X.509 certificates, which contain a public key and additional information about the entity it belongs to, such as the website owner or certificate authority. These certificates are essential in establishing trust and verifying the authenticity of the communication parties.
Another purpose of PEM files is to store certificate signing requests (CSRs). When a website owner wants to obtain an SSL/TLS certificate from a certificate authority, they generate a CSR that includes their public key and information about their organization. This CSR is then sent to the certificate authority, which uses it to issue a signed certificate that can be used to encrypt communication.
PEM files can also store intermediate certificates, which are certificates that sit between the end-entity certificate and the root certificate. These intermediate certificates help establish the trust chain, allowing the client to verify the authenticity of the end-entity certificate.
The beauty of PEM files lies in their flexibility. They can store multiple types of cryptographic data within a single file, making it easier to manage and transfer the necessary components for secure communication. By utilizing the Base64 encoding format, the files can be easily read, shared, and transported across different platforms and systems.
How Are PEM Files Used in SSL/TLS?
PEM files play a crucial role in the implementation of SSL/TLS protocols, which are used to secure websites, web applications, and other network-based services. They are used in various aspects of SSL/TLS, including key management, certificate storage, and establishing secure connections between clients and servers.
One of the main uses of PEM files in SSL/TLS is for storing the private key, which is necessary for encrypting and decrypting data in asymmetric encryption algorithms. The private key is securely stored in a PEM file and is used by the server to decrypt data that has been encrypted with the corresponding public key.
PEM files are also used to store X.509 certificates, which contain the public key and other information about the entity that owns the certificate, such as the website owner or certificate authority. The server presents its certificate to the client during the SSL/TLS handshake process, allowing the client to verify the identity of the server and establish a secure connection.
In addition to the server certificate, PEM files can also store intermediate certificates. These intermediate certificates form a chain of trust between the server’s certificate and the root certificate, allowing the client to verify the authenticity of the server’s certificate. The server sends both the server certificate and any necessary intermediate certificates during the SSL/TLS handshake.
When a website owner wants to obtain an SSL/TLS certificate, they generate a certificate signing request (CSR), which is also stored in a PEM file. The CSR contains the public key and details about the organization requesting the certificate. The website owner sends the CSR to a certificate authority, who uses it to issue a signed certificate that can be installed on the server.
PEM files are commonly used in web servers to configure SSL/TLS settings. When setting up SSL/TLS on a server, the administrator specifies the paths to the PEM files containing the private key, server certificate, and intermediate certificates. The web server software then uses these files to establish secure connections with clients.
By utilizing PEM files, SSL/TLS implementations can seamlessly manage and store the necessary cryptographic components for secure communication. The flexibility of PEM files, their compatibility with various systems and applications, and the ASCII encoding format make them a popular choice for securing websites and other network-based services.
How Are PEM Files Different from Other Certificate Formats?
PEM files are different from other certificate formats in several ways, including the encoding method, file extension, and the ability to store multiple types of cryptographic data within a single file.
One key difference is the encoding method used in PEM files. PEM files use Base64 encoding, which converts binary data into ASCII text. This encoding ensures that the files can be easily read and manipulated by both humans and machines. In contrast, other certificate formats like DER (Distinguished Encoding Rules) use binary encoding, which is more compact but not human-readable.
Another difference is the file extension. PEM files typically have a “.pem” extension, but they can also use extensions like “.crt”, “.key”, or “.p12”. On the other hand, other certificate formats have their own distinct extensions, such as “.der” for DER-encoded certificates or “.pfx” for Personal Information Exchange format.
One unique characteristic of PEM files is their ability to store multiple types of cryptographic data within a single file. For example, a PEM file could contain a private key, a server certificate, intermediate certificates, and even a certificate signing request (CSR), all organized into separate sections. This flexibility allows for convenient management and transport of all the necessary components in one file.
In contrast, other certificate formats usually store a specific type of data. For example, DER and PKCS#12 formats are more focused on storing a single type of information, such as a certificate or a private key. While these formats can also include multiple certificates or keys, they usually require separate files for each component.
Furthermore, PEM files’ ASCII encoding makes it easier to copy and share the data within the file. They can be opened and edited with a text editor, shared via email or other messaging platforms, and easily transferred between different systems and applications without any binary-to-text conversion.
However, one potential drawback of PEM files is their larger file size compared to binary formats like DER. Base64 encoding inflates the size of the file, requiring additional storage and bandwidth resources. This can be a consideration when optimizing resources in certain situations.
Overall, PEM files stand out by offering human-readability, multi-purpose capabilities, and compatibility with various systems. These qualities have made them a widely used format in the field of secure communication protocols like SSL/TLS.
How Do I Create a PEM File?
Creating a PEM file involves generating or obtaining the necessary cryptographic components and encoding them in the PEM format. Here are the steps to create a PEM file:
- Generate or obtain the private key: The first step is to generate or obtain the private key that will be used for encryption and decryption. This can be done using various tools or libraries, depending on the specific requirements of your system.
- Create a certificate signing request (CSR): If you need to obtain an SSL/TLS certificate from a certificate authority, you’ll need to create a CSR. The CSR includes your public key and some information about your organization. You can generate a CSR using tools provided by your web server or a certificate management tool.
- Obtain the certificate: After submitting the CSR to a certificate authority, you will receive a signed certificate. This certificate, along with any intermediate certificates, will be used to establish trust with clients.
- Create the PEM file: To create a PEM file, you need to combine the private key, certificate, and any intermediate certificates into a single file. Open a text editor and create a new file. Begin each section with the appropriate “—–BEGIN” marker and end it with the corresponding “—–END” marker. Ensure that each section is properly labeled and that the order is correct.
- Save the file with the correct extension: When saving the file, use the appropriate extension for a PEM file, such as “.pem” or “.crt”. This will help distinguish it as a PEM-encoded file.
Once you have created the PEM file, you can use it in your SSL/TLS configuration by specifying the path to the file in your web server configuration. The server will then use the private key and certificate stored in the PEM file to establish secure connections with clients.
It’s important to keep the PEM file secure and properly backed up. Treat the private key with utmost care and ensure that only authorized individuals have access to the file. Protecting the PEM file helps maintain the integrity and security of your SSL/TLS-enabled application or website.
By following these steps, you can create a PEM file containing the necessary cryptographic components for secure communication.
How Do I Convert a PEM File to Other Formats?
If you have a PEM file and need to convert it to a different format for compatibility or specific requirements, there are several methods you can use. Here are some common conversion options:
- Using OpenSSL: OpenSSL is a widely-used tool that provides a command-line interface for handling various cryptographic operations. To convert a PEM file to another format, you can use OpenSSL’s commands. For example, to convert a PEM file to DER format, you can use the following command:
openssl x509 -outform der -in certificate.pem -out certificate.der. Replacecertificate.pemwith the path to your PEM file andcertificate.derwith the desired output file name. - Using online conversion tools: There are various online tools available that allow you to convert PEM files to different formats. These tools typically have a simple user interface where you can upload your PEM file and select the desired output format. Be cautious when using online tools, as they will require you to upload sensitive cryptographic data. Make sure to choose a reputable and secure tool to protect your data.
- Writing a script or program: If you have programming knowledge, you can write a script or program to convert a PEM file to the desired format. There are libraries available in different programming languages that provide functionalities for working with cryptographic data and file formats. Using such libraries, you can write custom logic to read the PEM file content, perform the necessary conversions, and save the result in the desired format.
- Using certificate management tools: If you are working with SSL/TLS certificates, certificate management tools like OpenSSL, Java’s keytool, or Microsoft’s Certificate Services can help you with format conversions. These tools often provide options to import and export certificates in various formats, including converting between PEM, DER, PKCS#12, and other formats supported by the tool.
When converting a PEM file to another format, ensure that you understand the requirements of the target system or application. Different formats may have specific limitations or prerequisites for compatibility. It’s also essential to keep the converted file secure and properly manage the private key associated with the certificate to maintain the integrity and security of your cryptographic assets.
By leveraging the available tools, libraries, and methodologies, you can easily convert a PEM file to the desired format and meet the specific requirements of your system or application.
How Do I Import a PEM File into a Web Server?
Importing a PEM file into a web server involves configuring the server to use the private key and certificate stored in the PEM file for establishing secure connections. The process varies depending on the web server software you are using, but here are the general steps:
- Access the server configuration: Log in to your web server and access the configuration file. The location and name of the configuration file can vary depending on the server software and operating system.
- Specify the private key and certificate paths: In the configuration file, locate the settings related to SSL or TLS. Look for directives like “SSLCertificateFile” or “SSLCertificateKeyFile” depending on your server software. Specify the paths to the PEM file containing the private key and certificate. For example, you might add lines like:
SSLCertificateFile /path/to/certificate.pem SSLCertificateKeyFile /path/to/privatekey.pem - Include any required intermediate certificates: If your certificate chain includes intermediate certificates, you’ll need to include them as well. Add directives like “SSLCertificateChainFile” or “SSLCACertificateFile” depending on your server software and provide the path to the PEM file containing the intermediate certificates.
- Save and restart the web server: Save the configuration file and restart the web server for the changes to take effect. The command to restart the server can vary depending on your operating system or server software. Ensure that the web server successfully starts after the restart.
- Test the configuration: Verify that the web server is using the correct private key and certificate by accessing your website using HTTPS (e.g., https://www.example.com). Check that the browser recognizes the certificate and indicates a secure connection. You can also use online SSL testing tools to check the validity and configuration of your SSL/TLS implementation.
It’s important to secure the PEM file and ensure that only authorized individuals have access to it. Protect the private key associated with the certificate as it controls access to the secured communication channels. Regularly update and renew the certificate as required to maintain secure connections.
Remember that the specific steps for importing a PEM file into a web server can differ based on your server software, so consult the documentation or seek specific instructions for your chosen server software to ensure the correct configuration.
By following these general steps and customizing them to your web server environment, you can import a PEM file and enable secure connections to your website or web application.
Are PEM Files Secure?
PEM files themselves are not inherently secure or insecure. The security of the information stored in PEM files depends on how they are generated, managed, and protected.
While PEM files use Base64 encoding, which makes them readable and transferable in ASCII format, the actual content within the file can include sensitive information such as private keys and certificates. Therefore, it is crucial to treat PEM files with the same level of security as any other sensitive data.
Here are some considerations to ensure the security of PEM files:
- Access control: Limit access to the PEM files to authorized users and systems. Ensure that only trusted individuals are granted permission to read, modify, and distribute the files. Regularly audit and review access permissions to minimize the risk of unauthorized access.
- Secure storage: Store PEM files in a secure location, such as a dedicated directory with restricted access permissions. Use encryption or other mechanisms to protect the files at rest, especially when they contain private keys or other highly sensitive information.
- Secure transmission: When transferring PEM files across networks, use secure channels such as SSH or encrypted file transfer protocols. Avoid sending PEM files via unencrypted email or other insecure means, as this could potentially expose the sensitive data to interception or unauthorized access.
- Proper backups: Regularly backup PEM files to prevent data loss and enable recovery in case of system failures or breaches. Store backups securely to ensure the integrity and availability of the files.
- Secure key management: Private keys stored in PEM files are critical for secure communication. Follow best practices for key management, such as generating strong, random keys, using password-based encryption or hardware security modules (HSMs) to protect the keys, and rotating keys periodically.
- Regular updates: Keep PEM files updated by renewing certificates when they expire. Regularly review and update the security configurations and practices surrounding the use of PEM files to stay current with best practices and mitigate any potential vulnerabilities.
A secure implementation of PEM files requires a comprehensive approach that includes secure access controls, storage, transmission, key management, and regular maintenance. Adhering to best practices and staying informed about evolving security standards will help ensure the security of the data stored in PEM files.
It’s important to note that the security of a system relies not only on PEM files themselves but also on other factors, such as secure server configurations, proper network infrastructure, and adherence to secure coding practices.