What Is a DMZ?
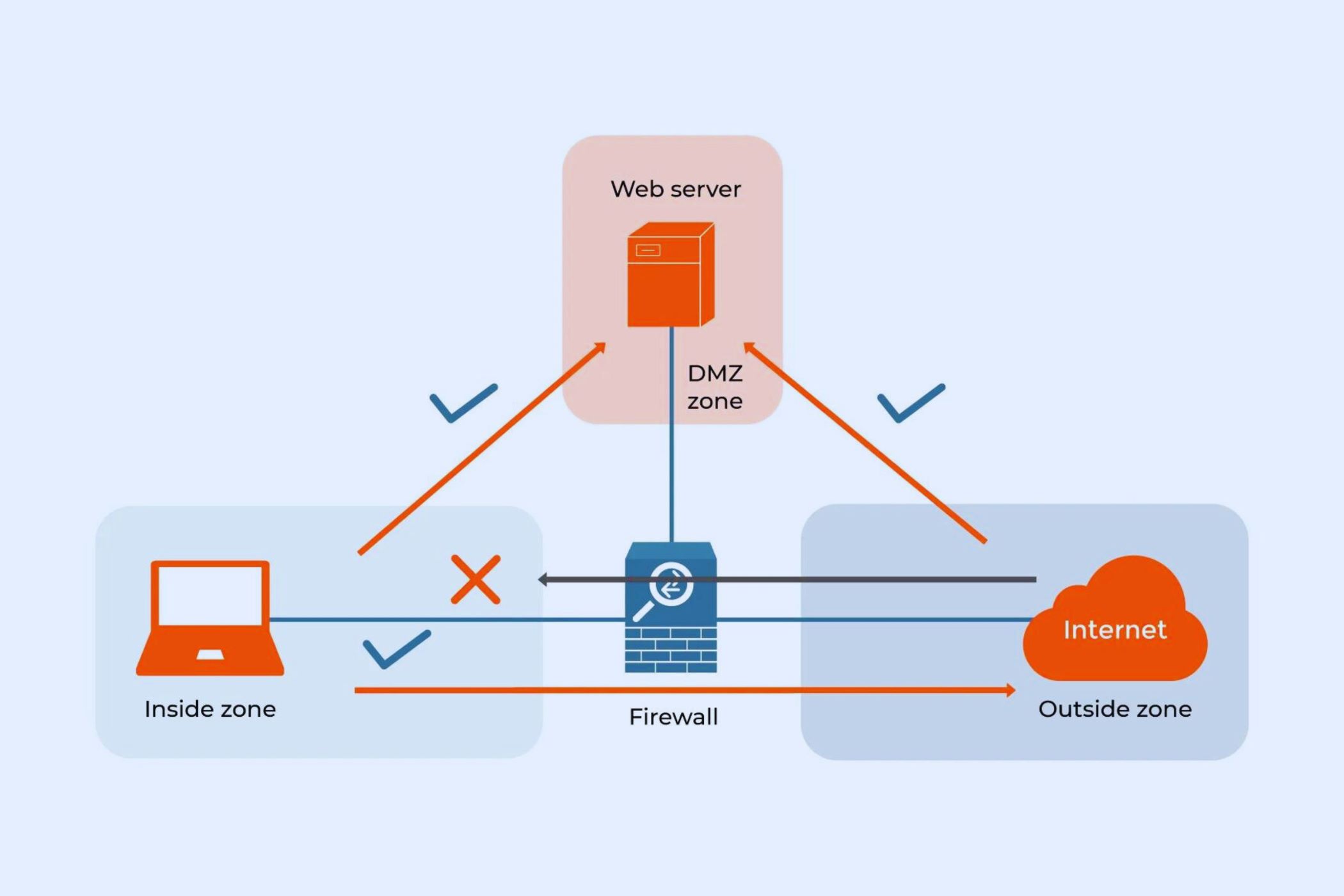
A DMZ, which stands for Demilitarized Zone, is a network segment that acts as a buffer zone between an organization’s internal network and the outside world, typically the internet. It serves as an additional layer of security, protecting sensitive information and critical systems from unauthorized access.
The purpose of a DMZ is to isolate and segregate different types of network resources based on their security needs. It allows organizations to selectively expose certain services to the internet while keeping the internal network hidden and protected. By using a DMZ, organizations can achieve a balance between providing services to external users and maintaining the security of their internal assets.
Within a DMZ, there are typically three distinct zones or segments:
- External DMZ: This is the zone that faces the internet and provides access to services that need to be available to the public, such as web servers, FTP servers, or email gateways.
- Internal DMZ: This zone is typically separated from the external DMZ by another layer of security, such as a firewall or an intrusion detection system. It contains resources that require a higher level of protection but still need to be accessible to specific users or systems.
- Internal Network: This is the core network that houses an organization’s most sensitive systems and data. It is isolated from both the external DMZ and the internal DMZ, ensuring maximum security and restricted access.
By implementing a DMZ, organizations can provide controlled access to external users while minimizing the risk of exposing their entire infrastructure to potential attacks. It acts as a barrier, preventing unauthorized access to critical assets and reducing the attack surface.
A properly configured DMZ is a vital component of a network security infrastructure, as it provides an additional layer of defense against external threats. It allows organizations to securely host web services, email servers, or other public-facing applications, knowing that even if these services were compromised, the internal network and critical systems would remain protected.
Overall, a DMZ plays a crucial role in an organization’s cybersecurity strategy by providing a secure environment for hosting external-facing services and separating them from internal assets. It helps organizations strike a balance between accessibility and security, ensuring the confidentiality, integrity, and availability of their critical data and systems.
Why Is a Firewall DMZ Important?
A firewall DMZ is of utmost importance in today’s digital landscape where cyber threats are constantly evolving. It plays a vital role in protecting an organization’s network infrastructure, data, and systems from unauthorized access and malicious activities. Here are some key reasons why a firewall DMZ is crucial:
- Enhanced Network Security: A firewall DMZ acts as a secure buffer zone between the internet and an organization’s internal network. It effectively isolates public-facing services and resources from the more sensitive internal network. This segregation helps prevent direct access to critical systems and reduces the potential attack surface.
- Granular Access Control: With a firewall DMZ, organizations can exercise granular control over what services are exposed to the internet and how they are accessed. By defining strict access rules and policies, organizations can ensure that only necessary and authorized traffic is allowed in and out of the DMZ, minimizing the risk of unauthorized access.
- Protection Against External Threats: The Internet is filled with various threats, such as malware, viruses, and hackers, constantly looking for vulnerabilities to exploit. By placing public-facing services in the DMZ, organizations can mitigate the risk of these threats reaching their internal network. The DMZ acts as a line of defense, intercepting and analyzing incoming traffic, and filtering out potentially harmful or unauthorized requests.
- Secure Remote Access: A firewall DMZ can also facilitate secure remote access to internal resources. By implementing VPN (Virtual Private Network) gateways within the DMZ, organizations can provide authorized users with a secure and encrypted tunnel to access internal services while keeping the internal network isolated.
- Easier Compliance Management: Many industries and regulatory frameworks, such as the Payment Card Industry Data Security Standard (PCI DSS) or the Health Insurance Portability and Accountability Act (HIPAA), require organizations to implement strict security measures to protect sensitive data. A firewall DMZ helps organizations meet these compliance requirements by providing a secure and controlled environment for handling and transmitting sensitive data.
How Does a Firewall DMZ Work?
A firewall DMZ works by creating a secure network segment that acts as a buffer zone between the internet and an organization’s internal network. It strategically places public-facing services, such as web servers or email gateways, in the DMZ while keeping the sensitive internal network hidden and protected. Here’s how a firewall DMZ operates:
- Network Segmentation: The DMZ is created by dividing the network infrastructure into three distinct segments – the external DMZ, internal DMZ, and internal network. This segmentation ensures that different types of resources are isolated based on their security requirements. The external DMZ is designed to face the internet and hosts publicly accessible services, while the internal DMZ and internal network are shielded from direct external access.
- Firewall Configuration: A firewall is deployed to control the traffic flow between the DMZ segments and the internal network. The firewall acts as a barrier, filtering incoming and outgoing traffic based on predefined rules and policies. It allows authorized traffic to pass through while blocking unauthorized or suspicious traffic that could potentially compromise the internal network.
- Access Control Lists (ACLs): ACLs are implemented within the firewall to enforce strict access control between the DMZ and the internal network. These access control lists dictate which services or ports are allowed or denied for communication between the two segments. By carefully configuring ACLs, organizations can ensure that only necessary and secure connections are established.
- Network Address Translation (NAT): NAT is commonly used in a firewall DMZ to map the IP addresses of devices in the DMZ to public IP addresses. This provides an additional layer of security by hiding the actual IP addresses of the internal network devices from external users. It helps prevent potential attackers from directly targeting specific devices on the internal network.
- Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS solutions are often deployed within the DMZ to analyze incoming and outgoing traffic for any suspicious behavior or known attack patterns. These systems actively monitor the traffic flow, flagging and blocking any potentially malicious activity. This enhances the security of the DMZ and helps protect against both external threats and insider attacks.
By utilizing network segmentation, firewall configuration, ACLs, NAT, and IDS/IPS systems, a firewall DMZ provides comprehensive defense mechanisms to protect an organization’s network infrastructure. It ensures that public-facing services are isolated and secured, reducing the risk of unauthorized access and minimizing the impact of potential breaches.
Components of a Firewall DMZ
A firewall DMZ consists of several components that work together to provide a secure and controlled environment for hosting public-facing services while safeguarding the internal network. These components ensure the effectiveness and integrity of the DMZ. Let’s explore the key components of a firewall DMZ:
- Firewall: The firewall acts as the main component of the DMZ. It regulates and monitors network traffic between the internal network and the external DMZ, enforcing access control policies and preventing unauthorized access. The firewall is responsible for inspecting incoming and outgoing traffic, applying security rules, and filtering potentially harmful or suspicious traffic.
- Routers: Routers are used to direct network traffic between different segments of the DMZ. They play a crucial role in determining the path that data takes to reach its destination. Routers within the DMZ allow for efficient routing of traffic while maintaining network security.
- Switches: Switches are responsible for connecting devices within the DMZ and facilitating communication. They provide efficient and reliable data transfer between servers, routers, and other network devices within the DMZ.
- Proxy Servers: Proxy servers act as intermediaries between clients on the internet and servers within the DMZ. They enhance security by serving as a buffer between the external users and the internal network, filtering and managing traffic requests, and providing caching capabilities.
- Load Balancers: Load balancers distribute incoming network traffic across multiple servers within the DMZ. They ensure optimal performance and availability of services by evenly distributing the load and providing redundancy. Load balancers also enhance security by hiding the actual IP addresses of servers and providing a single entry point to the DMZ.
- Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS solutions actively monitor network traffic within the DMZ, detecting and preventing potential threats or attacks. They analyze incoming and outgoing traffic, identify abnormal patterns or malicious behavior, and take appropriate actions to mitigate risks.
- Logging and Monitoring Systems: Logging and monitoring systems are crucial for collecting and analyzing network activity within the DMZ. They provide real-time visibility into the network, assist in detecting security incidents, and aid in forensic investigations. These systems generate logs, alerts, and reports to help identify any anomalies or suspicious activities.
By integrating these components, a firewall DMZ establishes a strong defense mechanism to protect an organization’s internal network while allowing controlled access to public-facing services. The collaboration of firewalls, routers, switches, proxy servers, load balancers, IDS/IPS, and logging systems creates a secure and well-monitored environment within the DMZ.
Types of Firewall DMZ
There are different types of firewall DMZ configurations that organizations can choose from based on their specific security requirements and infrastructure design. Each type offers a different level of protection and functionality. Let’s explore some common types of firewall DMZ:
- Single-Homed Firewall DMZ: In a single-homed DMZ configuration, a firewall has two interfaces: one connected to the external network, and the other connected to the DMZ. This type of DMZ allows public-facing services to be deployed in the DMZ with restricted access to the internal network. The firewall controls traffic flow between the external network and the DMZ, providing a basic level of security.
- Dual-Homed Firewall DMZ: A dual-homed DMZ employs two firewalls – one facing the external network and another facing the internal network. This configuration adds an extra layer of security by creating a clear separation between the outside world and the internal network. Public-facing services reside in the DMZ, and traffic is controlled by both firewalls, ensuring that only authorized traffic reaches the internal network.
- Triple-Homed Firewall DMZ: The triple-homed DMZ configuration consists of three firewalls – one facing the external network, one facing the internal network, and one separating the DMZ from the internal network. This type of DMZ offers the highest level of security by providing a clear perimeter between the internet, the DMZ, and the internal network. It ensures strict access control and prevents direct communication between the internet and the internal network.
- Screened Subnet DMZ (also known as “Three-Legged Firewall”): In a screened subnet DMZ, two firewalls are deployed – an external “choke” firewall facing the internet and an internal “screening” firewall facing the internal network. The DMZ resides between these two firewalls. Incoming traffic from the internet passes through the choke firewall and is restricted to only necessary services in the DMZ. Outgoing traffic from the DMZ to the internal network is controlled by the screening firewall, ensuring that only authorized traffic is allowed.
- Host-Based DMZ: In a host-based DMZ configuration, instead of using dedicated network devices like firewalls, the DMZ is created by placing public-facing services on separate physical or virtual machines. Each service is isolated and protected using host-based firewall software or network segmentation techniques. This type of DMZ offers flexibility and scalability, allowing organizations to customize security measures for each individual service.
Each type of firewall DMZ configuration has its own advantages and considerations. The choice depends on factors such as the organization’s security requirements, budget, and resources. It is essential for organizations to carefully evaluate their specific needs and consult with security experts to determine the most suitable type of firewall DMZ for their environment.
Advantages of Using a Firewall DMZ
Implementing a firewall DMZ provides numerous advantages for organizations in terms of network security, accessibility, and risk reduction. Let’s explore some key advantages of using a firewall DMZ:
- Enhanced Security: A firewall DMZ acts as a buffer zone between the external network (typically the internet) and the internal network. It provides an additional layer of protection by isolating public-facing services within the DMZ, preventing direct access to the more sensitive internal resources. This segregation minimizes the attack surface, reducing the risk of unauthorized access and potential security breaches.
- Controlled Access: By configuring access control lists (ACLs) and implementing strict security policies, organizations can exercise granular control over the traffic allowed between the DMZ and the internal network. This allows for selective exposure of necessary services, ensuring that only authorized connections are established. Controlled access helps prevent unauthorized users from gaining access to critical resources and sensitive data.
- Improved Performance: Placing public-facing services in the DMZ allows organizations to optimize performance by offloading resource-intensive tasks to dedicated servers. This separation alleviates the burden on the internal network, ensuring smooth and efficient operation for both external users and internal network users.
- Reduced Impact of Attacks: In the event of a security breach or a successful attack on a public-facing service within the DMZ, the isolation provided by a firewall DMZ helps contain the impact. Since the DMZ is separate from the internal network, any compromise or unauthorized access is limited to the resources within the DMZ, preventing the attacker from directly accessing critical internal assets.
- Compliance with Regulatory Standards: Many industries and regulatory frameworks require organizations to adhere to strict security standards to protect sensitive data. By implementing a firewall DMZ, organizations can meet these compliance requirements, enabling secure hosting of public-facing services and enhancing data protection. Compliance with industry standards builds trust among customers, partners, and regulators.
- Scalability and Flexibility: With a firewall DMZ, organizations have the flexibility to deploy and scale public-facing services without disrupting the internal network. As business needs evolve, new services can be added to the DMZ and security measures can be adjusted accordingly. The modular nature of a DMZ allows for easy adaptability to changing requirements.
- Simplified Network Management: Separating public-facing services within a DMZ simplifies network management and troubleshooting. It provides a clear distinction between external and internal network components, allowing network administrators to focus on securing and maintaining the DMZ without impacting the core internal network.
By leveraging the advantages of a firewall DMZ, organizations can significantly improve their network security posture, protect sensitive data, and ensure the availability and performance of public-facing services. It acts as a critical component of a comprehensive cybersecurity strategy, safeguarding an organization’s resources against external threats while enabling controlled and secure access for authorized users.
Considerations for Setting Up a Firewall DMZ
Setting up a firewall DMZ requires careful planning and consideration to ensure its effectiveness and security. Organizations must take various factors into account when implementing a DMZ. Here are some key considerations:
- Network Architecture: Analyze the existing network architecture and identify the optimal placement of the DMZ. Determine how the DMZ will be connected to the external network and the internal network, ensuring that traffic flows smoothly while maintaining security boundaries.
- Service Requirements: Assess the specific services that need to be hosted in the DMZ and define their access requirements. Determine the necessary protocols, ports, and traffic patterns for each service. Consider any dependencies or interactions between services to ensure proper functionality within the DMZ.
- Security Policies and Access Control: Develop comprehensive security policies and access control rules for the DMZ. Define authorized users, their privileges, and the traffic allowed both to and from the DMZ. Implement strict access controls to limit exposure and prevent unauthorized access to critical resources.
- Firewall Configuration: Select an appropriate firewall solution that fits the organization’s needs. Configure the firewall to enforce access control, traffic filtering, and intrusion detection/prevention mechanisms. Regularly update firewall rules and policies to address emerging threats and vulnerabilities.
- DMZ Segmentation: Determine the level of segmentation required within the DMZ. Consider separating services with different security requirements into different segments or virtual LANs to minimize the potential impact of a security breach or compromise.
- Logging and Monitoring: Implement robust logging and monitoring systems within the DMZ to track and analyze network activities. Regularly review logs, monitor traffic patterns, and set up alerts for suspicious or abnormal behavior. This ensures timely detection and response to potential security incidents.
- Network Address Translation (NAT): Plan the usage of NAT within the DMZ to hide the internal network’s IP addresses and ensure proper communication with external users. Carefully configure and manage NAT rules to prevent IP address leakage and maintain network security.
- Backup and Disaster Recovery: Develop a comprehensive backup and disaster recovery plan for the DMZ. Regularly back up configurations, data, and services hosted within the DMZ. Test and validate the recovery process to ensure business continuity in the event of a network or security incident.
- Regular Assessments and Audits: Conduct regular security assessments and audits of the DMZ to identify any vulnerabilities or misconfigurations. Perform penetration testing to identify potential weaknesses and address them promptly. Regularly review and update security policies and access control to align with evolving threats and business needs.
By considering these factors when setting up a firewall DMZ, organizations can ensure its effectiveness, scalability, and security. A well-designed and properly implemented DMZ provides an added layer of protection, segregates critical assets, and helps to maintain the integrity and confidentiality of the network infrastructure and sensitive information.
Best Practices for Securing a Firewall DMZ
Securing a firewall DMZ is crucial for maintaining network integrity and protecting sensitive data. Implementing best practices can significantly enhance the security posture of the DMZ. Here are some essential practices to consider:
- Implement Defense-in-Depth: Apply a layered security approach by deploying multiple security measures within the DMZ. This includes using firewalls, intrusion detection/prevention systems, logging and monitoring solutions, and strict access control policies. Layering security mechanisms helps mitigate various types of threats and reduces the chance of a single point of failure.
- Regularly Update and Patch Systems: Keep all systems within the DMZ up to date with the latest security patches and software updates. This ensures that known vulnerabilities are addressed, reducing the risk of exploitation by attackers. Establish a patch management process to stay vigilant against emerging threats.
- Practice Least Privilege: Follow the principle of least privilege for all access control policies within the DMZ. Grant only the necessary access rights to each user or service based on their specific requirements. Regularly review and update access permissions to prevent unauthorized access and limit exposure to potential security risks.
- Perform Continuous Monitoring: Monitor network traffic, logs, and events within the DMZ continuously. Implement a robust logging and monitoring system to detect and respond to any suspicious activities promptly. Establish alerts and event correlation mechanisms to identify potential security incidents in real-time.
- Regularly Review Firewalls Rules and Policies: Perform periodic reviews of firewall rules and policies to ensure they align with the latest security standards and organizational requirements. Remove any unnecessary or obsolete rules to minimize the attack surface. Regularly test and validate the effectiveness of firewall settings.
- Encrypt Sensitive Data: Implement encryption for all sensitive data transmitted within the DMZ to protect it from unauthorized access. Utilize secure protocols such as HTTPS, TLS, or IPsec for data transmission between the DMZ and external users. Encrypt stored data to prevent unauthorized disclosure in case of a security breach.
- Regularly Conduct Penetration Testing: Perform regular penetration testing to identify and address potential vulnerabilities within the DMZ. Engage professional ethical hackers to simulate real-world attacks and identify possible weaknesses. Regularly update security controls and configurations based on test results to enhance network security.
- Separate Management Interfaces: Maintain separate management interfaces for devices within the DMZ. Restrict access to management interfaces to authorized personnel only. This prevents unauthorized individuals from tampering with the DMZ devices or gaining unauthorized control over the network.
- Educate and Train Employees: Provide comprehensive security training and awareness programs for employees working within the DMZ. Educate them about potential threats, social engineering techniques, and best practices for maintaining network security. Promote a strong security culture and encourage reporting of any suspicious activities.
By adhering to these best practices, organizations can strengthen the security of their firewall DMZ, minimize the risk of security breaches, and protect sensitive assets within the network. Regularly reassess and update security measures to address evolving threats and ensure ongoing protection.
Examples of Firewall DMZ Configurations
There are various ways to configure a firewall DMZ based on an organization’s specific requirements and security considerations. Here are a few examples of common firewall DMZ configurations:
- Single-Homed DMZ Configuration: In this configuration, a firewall is positioned between the external network and the DMZ. Public-facing services, such as web servers or email gateways, reside within the DMZ. The firewall allows traffic from the internet to reach the public services within the DMZ while preventing direct access to the internal network. This setup provides basic security and segregation between the DMZ and the internal network.
- Dual-Homed DMZ Configuration: In a dual-homed DMZ, two separate firewalls are deployed. One firewall separates the external network from the DMZ, while the second firewall isolates the DMZ from the internal network. Public services are hosted within the DMZ, and incoming traffic from the internet goes through the first firewall, then the DMZ, and finally reaches the internal network through the second firewall. This setup provides an additional layer of security by creating a clear separation between the internet, the DMZ, and the internal network.
- Screened Subnet DMZ Configuration: Also known as a “three-legged firewall,” this configuration employs two firewalls – one facing the external network and the other facing the internal network. The DMZ resides between these two firewalls. Public services are hosted within the DMZ, and incoming traffic from the internet is first filtered by the external firewall before reaching the DMZ. Outgoing traffic from the DMZ to the internal network is controlled by the internal firewall. This architecture provides a clear perimeter between the internet, the DMZ, and the internal network, enhancing security and access control.
- Host-Based DMZ Configuration: In a host-based DMZ configuration, public-facing services are deployed on separate physical or virtual machines within the DMZ. Each service is isolated and protected using host-based firewall software or network segmentation techniques. This setup provides flexibility and granular control over individual services within the DMZ, allowing specific security measures to be applied to each service separately.
- Remote Access DMZ Configuration: In this configuration, a DMZ is specifically designed for secure remote access to the internal network. It typically involves deploying a VPN (Virtual Private Network) gateway within the DMZ. External users can establish an encrypted connection to the DMZ via the VPN, which provides a secure entry point into the internal network. This setup allows remote users to access internal resources while maintaining network security.
Each configuration has its own strengths and considerations. Organizations should assess their specific security needs, scalability requirements, and budget constraints when choosing a firewall DMZ configuration. Regular monitoring, updates, and testing of these configurations are crucial to ensuring the ongoing effectiveness and security of the DMZ.