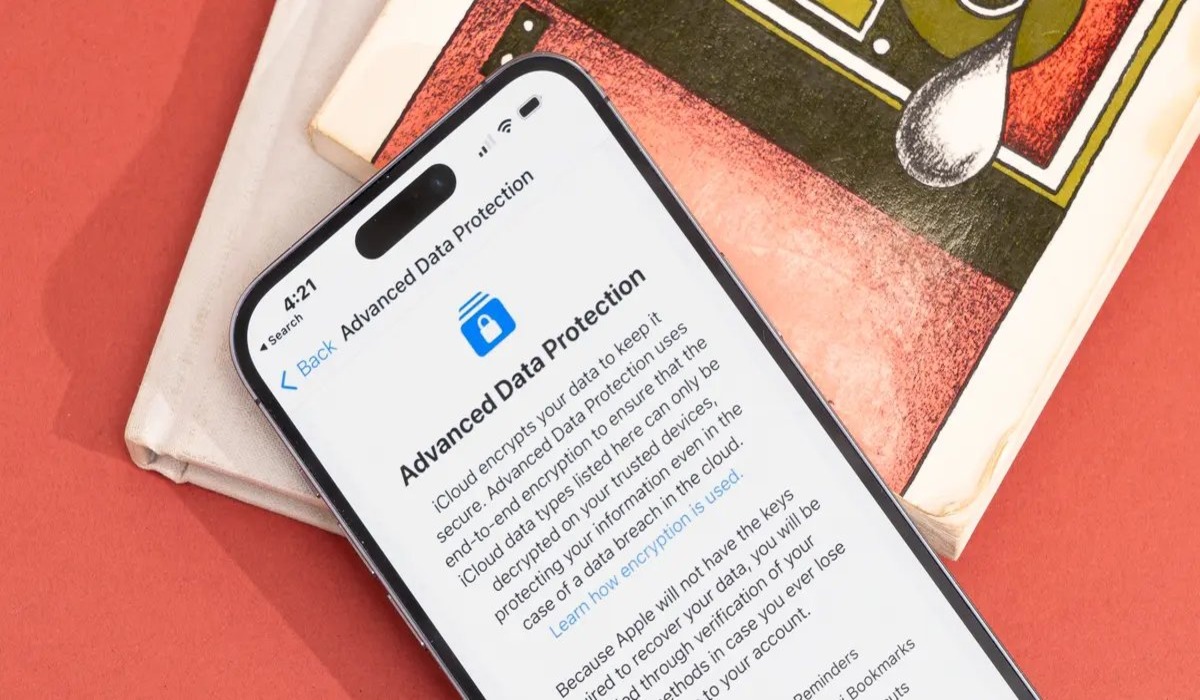
Apple Introduces iCloud Data Encryption
In a recent move to prioritize user data privacy and security, Apple has introduced iCloud data encryption. This enhancement means that data stored in iCloud will now be protected with robust encryption algorithms, making it significantly more challenging for unauthorized individuals to access or decrypt users’ personal information.
With the rise in cyber threats and data breaches in recent years, this move by Apple is a step in the right direction towards ensuring the confidentiality and integrity of user data. By implementing iCloud data encryption, Apple aims to give users peace of mind and reassurance that their sensitive information, such as documents, photos, and app data, is safeguarded from prying eyes.
To implement iCloud data encryption, Apple uses advanced algorithms to convert data into encrypted code that can only be deciphered with a unique decryption key. This encryption process renders the data unreadable to anyone without authorized access, even if it is intercepted during transmission or stored in the cloud.
Apple’s iCloud data encryption employs end-to-end encryption, which means that the data is encrypted on the user’s device before it is uploaded to iCloud servers, ensuring that even Apple itself cannot access the encrypted data. This approach ensures that no one, including government agencies or unauthorized third parties, can access user data without the encryption key.
The introduction of iCloud data encryption brings multiple benefits to users. First and foremost, it provides an additional layer of security to the data stored in iCloud, which may include personal photos, sensitive documents, and confidential emails. By encrypting this data, Apple ensures that even if there is a security breach, the encrypted information remains protected and inaccessible to unauthorized parties.
Furthermore, iCloud data encryption helps to maintain user trust in Apple’s services. With privacy concerns becoming increasingly prevalent, ensuring the security of user data is crucial for maintaining a positive brand image. By prioritizing user privacy through cutting-edge encryption measures, Apple demonstrates its commitment to protecting user information.
Overall, the introduction of iCloud data encryption by Apple is a significant step towards enhancing user data security and privacy. By employing advanced encryption techniques, Apple aims to provide users with peace of mind and a higher level of protection for their sensitive information. The benefits of this encryption outweigh the potential risks, making it a valuable addition to Apple’s range of privacy and security features.
Next, let’s explore how iCloud data encryption actually works and the benefits it provides to users.
How iCloud Data Encryption Works
iCloud data encryption utilizes a combination of encryption techniques to ensure the security and confidentiality of user data. When data is uploaded to iCloud, it goes through a series of processes to protect it from unauthorized access. Let’s dive into how iCloud data encryption works.
To start, Apple employs end-to-end encryption, which means that data is encrypted on the user’s device before it is sent to the iCloud servers. This ensures that the data remains confidential and unreadable throughout its transfer to and storage within the cloud.
The encryption process begins by converting user data into ciphertext using strong encryption algorithms. The data is scrambled and disguised, making it unintelligible without the decryption key. Apple uses AES (Advanced Encryption Standard) with 256-bit encryption, which is widely regarded as highly secure and virtually unbreakable.
Once the data is encrypted, it is transmitted to the iCloud servers over a secure connection. This ensures that even if the data is intercepted during transmission, it remains inaccessible to unauthorized individuals. iCloud utilizes industry-standard protocols such as SSL/TLS to guarantee the integrity and confidentiality of the data in transit.
Upon arrival at the iCloud servers, the encrypted data is stored in its encrypted form. This ensures that even Apple employees cannot access the data without the encryption key. The encryption key itself is derived from the user’s login credentials and is never stored on Apple’s servers. This means that only the user has access to the encryption key, further enhancing the security and privacy of the iCloud data.
When a user wishes to access their data, such as retrieving photos or documents from iCloud, the encrypted data is transmitted back to their device. The user’s credentials are used to authenticate and decrypt the data locally, allowing them to access their information securely. This decryption process is seamless and transparent to the user, ensuring a smooth user experience.
Overall, iCloud data encryption provides users with a robust and secure mechanism to protect their data. By employing end-to-end encryption and strong encryption algorithms, Apple ensures that user data remains confidential and inaccessible to unauthorized individuals throughout its transfer to and storage within the iCloud servers.
Now that we understand how iCloud data encryption works, let’s explore the benefits it provides to users and their data security.
Benefits of Encrypting iCloud Data
Encrypting iCloud data brings several significant benefits to users, enhancing their data security and privacy. Let’s explore these benefits in detail.
1. Protection against unauthorized access: One of the primary advantages of encrypting iCloud data is the increased protection it offers against unauthorized access. With encryption, even if a hacker manages to intercept or gain access to the encrypted data, they will be unable to decrypt and comprehend the information without the encryption key.
2. Confidentiality of sensitive information: iCloud data often includes personal photos, sensitive documents, and other confidential information. By encrypting this data, users can rest assured that even in the event of a data breach or unauthorized access, their sensitive information will remain secure and confidential.
3. Compliance with privacy regulations: Data privacy regulations, such as the General Data Protection Regulation (GDPR), require businesses to ensure the security and confidentiality of personal data. Encrypting iCloud data helps users comply with these regulations by offering an additional layer of protection.
4. Prevention of data tampering: Encryption also guards against data tampering. By encrypting iCloud data, any alteration or unauthorized modification of the encrypted information becomes nearly impossible, as the decryption process would fail, indicating that the data has been tampered with.
5. Preservation of user trust: Incorporating encryption into iCloud services demonstrates Apple’s commitment to protecting user data, ultimately fostering trust among its user base. The knowledge that their personal information is encrypted and secured can instill confidence in users, encouraging them to continue using Apple’s services and products.
6. Peace of mind: Encrypting iCloud data provides users with peace of mind, knowing that their sensitive and personal information is safeguarded against unauthorized access. This assurance allows them to store important files, documents, and memories in the cloud with the confidence that their data is protected.
In summary, encrypting iCloud data offers a range of benefits that promote data security, privacy, and compliance with regulations. By protecting against unauthorized access, maintaining the confidentiality of sensitive information, preventing data tampering, and instilling user trust, encryption plays a crucial role in ensuring the safety of users’ data within the iCloud ecosystem.
Now that we have explored the benefits of encrypting iCloud data, let’s delve into the potential risks and vulnerabilities that may be associated with this encryption process.
Potential Risks of iCloud Data Encryption
While iCloud data encryption offers numerous benefits, it is essential to be aware of the potential risks and vulnerabilities that may arise in the process. Understanding these risks can help users make informed decisions and take necessary precautions. Let’s explore some potential risks of iCloud data encryption.
1. Loss of encryption key: If a user forgets or loses their encryption key, they may face challenges accessing their encrypted data. While this ensures that only the user has access to their information, it also means that there is no way to recover the data without the encryption key.
2. Complex password management: Encryption relies on strong and unique passwords or passphrases to protect the encryption key. However, managing complex passwords for multiple accounts can be challenging. Users may be tempted to use weak or reused passwords, which can compromise the security of their iCloud data.
3. Increased risk of data loss: If a user loses their encryption key and does not have a backup, the encrypted data becomes irretrievable. In such cases, it is important to regularly back up the encryption key or consider alternative solutions to avoid permanent data loss.
4. Cloud service vulnerabilities: While encryption safeguards data in transit and storage, it does not eliminate the risks associated with the cloud service itself. Weaknesses in cloud infrastructure, potential security breaches, or inadequate security practices by the cloud provider can still pose a risk to the encrypted data.
5. Third-party interception: Although end-to-end encryption ensures that data is encrypted on the user’s device and decrypted only on authorized devices, there is still a risk of interception during the encryption or decryption process if the device is compromised or if a third-party gains unauthorized access.
6. User error: User error can pose a risk to encrypted data. Mistakenly deleting or misplacing the encryption key, accidental sharing of the key or confidential information, or falling victim to phishing attempts can compromise the security of the iCloud encrypted data.
It is important to note that while these risks exist, Apple has implemented strong security measures to mitigate them. However, users should also take proactive steps to minimize these risks and ensure the safety of their encrypted iCloud data.
Now that we have examined the potential risks of iCloud data encryption, let’s explore the possible vulnerabilities that may be associated with this encryption process.
Possible Vulnerabilities in iCloud Data Encryption
While iCloud data encryption is designed to provide robust security, it is important to acknowledge the potential vulnerabilities that may exist within the encryption process. Understanding these vulnerabilities can help users make informed decisions and implement additional safeguards. Let’s explore some possible vulnerabilities in iCloud data encryption.
1. Weak passwords or passphrases: The strength of the encryption key is heavily reliant on the user’s chosen password or passphrase. If a user selects a weak or easily guessable password, it becomes easier for unauthorized individuals to gain access to their encrypted data.
2. Social engineering attacks: Even with encryption in place, attackers may attempt to exploit human vulnerabilities through social engineering. By tricking users into revealing their encryption key or other sensitive information, attackers can bypass the encryption and gain unauthorized access to the encrypted iCloud data.
3. Malware or spyware: Malicious software or spyware installed on a user’s device can compromise the security of their encrypted iCloud data. These types of malware can capture encryption keys or monitor keyboard input, potentially providing unauthorized access to the data.
4. Hardware vulnerabilities: Some vulnerabilities may stem from hardware-related issues. For example, a compromised device or a hardware flaw could enable unauthorized parties to access encryption keys or intercept data during the encryption or decryption process.
5. Insider threats: While Apple has stringent security measures in place, insider threats cannot be entirely ruled out. An insider with unauthorized access or improper intentions could potentially compromise the security of the iCloud data encryption system and access encrypted user data.
6. Encryption algorithm weaknesses: Although Apple employs advanced encryption algorithms, advances in technology and cryptographic research can sometimes expose weaknesses in these algorithms. If a vulnerability is discovered in the encryption algorithm used by iCloud, it could potentially undermine the security of the encrypted data.
It is crucial to note that while these vulnerabilities exist, Apple continually monitors and updates its security protocols to address any identified risks. Additionally, users can take active steps to further enhance the security of their encrypted iCloud data, such as using strong and unique passwords, keeping their devices and software up to date, and practicing good cybersecurity hygiene.
Now that we have considered the vulnerabilities in iCloud data encryption, let’s explore the issue of third-party access to iCloud data and its implications for data security.
Third-Party Access to iCloud Data
One important aspect to consider when it comes to iCloud data encryption is the issue of third-party access to user data. While Apple has implemented robust security measures, it is crucial to understand the potential risks and implications of third-party access. Let’s delve into the topic of third-party access to iCloud data.
1. Legal obligations and government requests: Apple may be obligated to comply with legal requests from government entities, such as court orders or subpoenas, for access to user data. These requests could potentially bypass the encryption measures in place and grant third-party access to iCloud data.
2. Security breaches or exploitation: Despite Apple’s stringent security protocols, there is still a risk of security breaches by hackers or other malicious actors who may exploit vulnerabilities to gain unauthorized access to iCloud data. Such breaches can potentially grant third parties access to encrypted data.
3. Third-party apps and services: Although Apple implements end-to-end encryption for iCloud data, it is important to consider the security practices of third-party apps and services that may interact with iCloud. If users grant access to their iCloud data to third-party apps or services with inadequate security measures, it could potentially compromise the confidentiality and integrity of their encrypted data.
4. Cloud storage providers: While iCloud is a secure storage service provided by Apple, other cloud storage providers may have different security measures in place. If users choose to store their encrypted data on third-party cloud storage platforms, it is important to assess the security standards of those providers as they may have access to the encrypted data.
To mitigate the risks associated with third-party access to iCloud data, it is essential for users to take proactive steps to protect their data. This includes using strong and unique passwords, regularly updating devices and software, being cautious when granting access to third-party apps, and implementing additional security measures such as two-factor authentication.
Apple’s commitment to user privacy and data security is evident in its efforts to minimize third-party access to iCloud data. By implementing end-to-end encryption and providing users with greater control over their data, Apple aims to ensure that users’ encrypted iCloud data remains secure and protected.
Now that we have examined the implications of third-party access to iCloud data, let’s explore how iCloud data encryption may impact the performance of the service.
The Impact of Encryption on iCloud Performance
One important consideration when implementing data encryption is its potential impact on performance. While encryption is crucial for data security, it can introduce additional overhead that may affect the speed and efficiency of iCloud services. Let’s explore the impact of encryption on iCloud performance.
1. Increased processing time: Encrypting and decrypting data requires computational resources, which can lead to increased processing time when uploading, downloading, or accessing encrypted data in iCloud. The encryption and decryption processes add an extra step, affecting the overall performance of iCloud services.
2. Larger file sizes: Encryption can result in larger file sizes since the encrypted data includes additional metadata and cryptographic information. This increase in file size can impact the amount of storage space needed in iCloud and may affect transfer speeds when working with encrypted files.
3. Network bandwidth consumption: Encrypting data typically requires additional data to be transmitted over the network. This increased data transmission can lead to higher network bandwidth consumption, potentially impacting the speed and responsiveness of iCloud services, especially in situations with limited network resources.
4. Synchronization delays: The encryption process can introduce delays in synchronizing changes across multiple devices. When a change is made on one device, it needs to be encrypted, transmitted securely, and decrypted on other devices. These additional steps can cause synchronization delays and impact the real-time accessibility of data across devices.
5. Device performance: The process of encrypting and decrypting data can put a strain on device resources, especially on older or less powerful devices. This can result in slower device performance and increased battery consumption, particularly when handling large amounts of encrypted data.
Apple strives to strike a balance between data security and performance. Despite the potential impact on performance, Apple has implemented optimizations in iCloud to ensure efficient data encryption and decryption processes. These optimizations aim to minimize the impact on performance while still providing robust encryption measures.
It is important to note that the impact of encryption on iCloud performance may vary depending on various factors, such as the device used, the size and type of data being encrypted, and the available network resources. Users may experience different levels of performance impact based on their specific use cases and circumstances.
Now that we have examined the impact of encryption on iCloud performance, let’s explore best practices for ensuring data security with iCloud encryption.
Ensuring Data Security with iCloud Encryption
While iCloud data encryption provides a robust security measure for protecting user data, it is essential for users to take additional precautions to further enhance data security. By implementing best practices, users can ensure the maximum level of protection for their encrypted data stored in iCloud. Let’s explore some key practices for ensuring data security with iCloud encryption.
1. Use strong and unique passwords: Create strong and unique passwords or passphrases for your iCloud account. Avoid using common or easily guessable passwords and consider using a password manager to securely store and generate unique passwords.
2. Enable two-factor authentication (2FA): Turn on two-factor authentication for your iCloud account. This adds an extra layer of security by requiring a verification code, in addition to your password, to access your account. This helps prevent unauthorized access, even if someone obtains your password.
3. Regularly update devices and software: Keep your devices and software up to date with the latest security patches and updates. This ensures that any known vulnerabilities are patched, minimizing the risk of unauthorized access to your encrypted iCloud data.
4. Be cautious with third-party apps: Exercise caution when granting access to third-party apps that interact with iCloud. Review the privacy and security practices of these apps, ensuring that they have appropriate security measures in place to protect your encrypted data.
5. Use device-level encryption: Use device-level encryption for your Apple devices, such as enabling FileVault on Mac or encrypting your iOS device. This provides an additional layer of encryption for your data, making it more secure in the event of physical theft or unauthorized access.
6. Back up your encryption key: Safely back up your encryption key or store it in a secure location. Losing or forgetting your encryption key can result in permanent data loss, so ensure that you have a backup method in place to prevent this.
7. Regularly review and maintain access privileges: Regularly review the access privileges granted to apps, devices, and individuals for your iCloud account. Remove any unnecessary access permissions and revoke access for devices or individuals that are no longer authorized to access your data.
By following these best practices, users can significantly enhance the security of their encrypted data stored in iCloud. With a proactive approach to data security, users can effectively leverage iCloud encryption to safeguard their sensitive information and ensure peace of mind.
Now that we have explored best practices for ensuring data security with iCloud encryption, let’s conclude our discussion and summarize the key points we have covered.
Best Practices for Protecting iCloud Data
Protecting your iCloud data goes beyond relying solely on encryption. Implementing best practices can add an extra layer of security and ensure the confidentiality, integrity, and availability of your data. Let’s explore some key best practices for protecting your iCloud data.
1. Regularly review privacy settings: Take the time to review and customize your iCloud privacy settings. Ensure that you understand the implications of each setting and adjust them according to your comfort level with sharing and syncing data.
2. Enable two-factor authentication (2FA): Two-factor authentication is a crucial security measure that helps prevent unauthorized access to your iCloud account. Enable 2FA to require a verification code, in addition to your password, when signing in or making account-related changes.
3. Use strong and unique passwords: Create strong and unique passwords for your iCloud account and avoid using the same password for multiple accounts. Consider using a password manager to generate and securely store your passwords.
4. Keep devices and software up to date: Regularly update your devices and software to ensure you have the latest security patches and bug fixes. This helps protect against known vulnerabilities that could be exploited by attackers.
5. Be cautious with third-party apps: When granting access to third-party apps, carefully review their privacy policies and permissions. Only grant access to apps from trusted sources, and periodically review the permissions granted to ensure they align with your privacy requirements.
6. Enable device-level encryption: Enable device-level encryption on your Apple devices, such as enabling FileVault on your Mac or encrypting your iOS device. This provides an additional layer of protection for your data, even if it falls into the wrong hands.
7. Regularly back up your data: Create regular backups of your important iCloud data. Consider using Apple’s Time Machine or iCloud Backup to ensure that your data is protected and can be easily restored in case of data loss or device damage.
8. Be vigilant against phishing attempts: Be cautious of suspicious emails, messages, or websites that attempt to trick you into revealing your iCloud login credentials. Always verify the authenticity of communication before providing any personal information.
9. Educate yourself about cybersecurity: Stay informed about the latest cybersecurity threats and best practices. Educate yourself on common attack techniques such as phishing, malware, and social engineering, and take appropriate measures to protect yourself.
10. Maintain access control: Regularly review the devices, apps, and individuals that have access to your iCloud account. Revoke access for any unauthorized or unused devices, apps, or individuals to minimize potential vulnerabilities.
By implementing these best practices, you can significantly enhance the security of your iCloud data. Protecting your data requires a proactive approach and an understanding of potential risks, allowing you to maintain control over your information and enjoy the benefits of iCloud without compromising your privacy or security.
Now that we have covered these best practices, you are well-equipped to protect your valuable iCloud data.