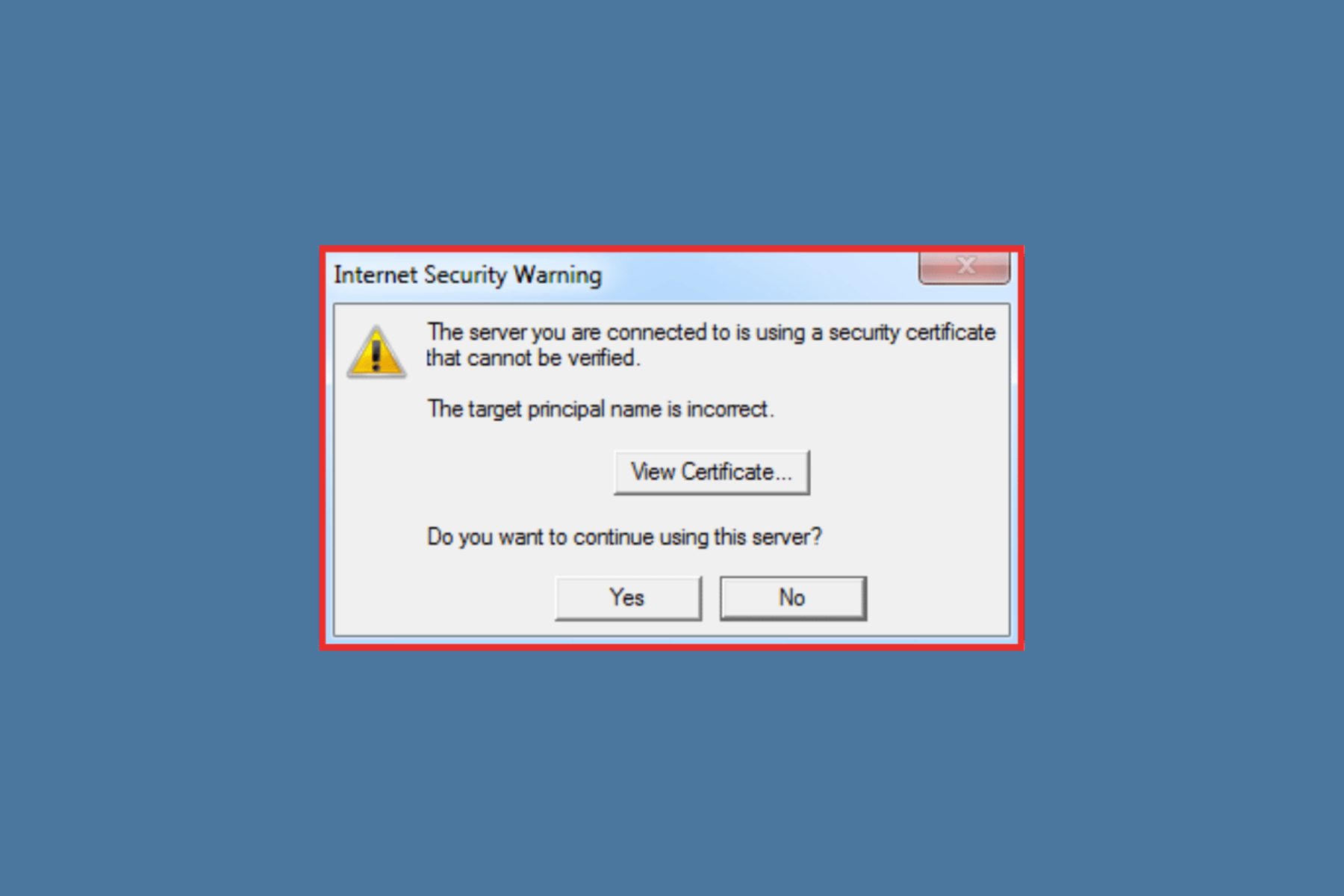
Understanding Internet Security Certificates
Internet Security Certificates, also known as SSL/TLS certificates, play a crucial role in securing data transmitted over the internet. They are essentially digital documents that verify the authenticity and integrity of websites, encrypting the connection between a user’s browser and the web server they are communicating with.
When you visit a secure website, you may notice a padlock icon in the address bar, indicating that the site is protected by an SSL/TLS certificate. This certificate establishes trust between the user and the website, ensuring that sensitive information such as login credentials, credit card details, and personal data remain confidential and secure.
The certificate includes key information about the website, such as its domain name, the entity it is associated with, and the issuing certificate authority (CA). CAs are trusted third-party organizations that validate the identity of the certificate holder and issue the certificate. Web browsers maintain a list of trusted CAs and verify the authenticity of certificates during the browsing session.
Certificates use a cryptographic protocol to establish secure communication between the browser and the web server. This prevents malicious actors from intercepting or tampering with the data exchanged between the user and the website. By encrypting the connection, certificates provide confidence that the data transmitted over the internet remains private and cannot be deciphered by unauthorized individuals.
It is essential to understand that internet security certificates have an expiration date. Typically, certificates are issued for a specific period, commonly ranging from one to three years. When a certificate expires, it will no longer be considered valid, and the website may display a security warning to users.
In addition to expiration dates, certificates can also be revoked if any security vulnerabilities or compromises are found. This means that even if a certificate is still within its validity period, it may be considered invalid if it has been revoked. Web browsers regularly check for certificate revocations to ensure that users are protected against potentially unsafe websites.
Errors related to internet security certificates can occur due to a variety of reasons, including incorrect system date and time settings, issues with the browser cache, outdated browser versions, or misconfigured security settings. In the following sections, we will explore some common causes of certificate errors and how to address them effectively.
Common Causes of Internet Security Certificate Errors
Internet security certificate errors can be frustrating and may prevent you from accessing certain websites securely. Understanding the common causes of these errors can help you troubleshoot and resolve them effectively. Here are some of the most common causes of internet security certificate errors:
- Expired Certificates: Internet security certificates have a validity period, typically one to three years. If a website’s certificate has expired, your browser will display an error message. Make sure to check the validity of the certificate to determine if it is the cause of the error.
- Missing or Incorrect Intermediate Certificates: intermediate certificates are necessary for establishing a chain of trust from the website’s SSL/TLS certificate to a trusted root certificate. If an intermediate certificate is missing or incorrectly configured, your browser may display a certificate error. Contact the website administrator to resolve this issue.
- Misconfigured Certificates: Certificates may be issued with incorrect or incomplete information, causing browsers to flag them as untrusted. Double-check the details of the certificate, including the website’s domain name, to ensure there are no configuration errors.
- Incorrect System Date and Time: Your system’s date and time need to be accurate for certificates to function properly. If your computer’s clock is incorrect, it may generate certificate errors. Adjust your system’s date and time settings to the correct values.
- Revoked Certificates: Certificate authorities can revoke certificates if they become compromised or if the certificate holder’s authorization is revoked. Browsers check for certificate revocations regularly, and if a certificate is revoked, it will trigger a security error. In such cases, there is usually nothing you can do except refrain from accessing the website.
- Browser Cache and Temporary Files: Stale or corrupted cache and temporary files can interfere with the validation of certificates. Clear your browser’s cache and temporary files to eliminate any potential issues.
These are just a few common causes of internet security certificate errors. Understanding these causes will help you pinpoint the issue and take appropriate steps to resolve it. In the following sections, we will explore various troubleshooting steps and solutions to fix these errors.
Checking the Date and Time on Your Device
One of the common causes of internet security certificate errors is an incorrect system date and time on your device. It is essential for your device’s clock to be accurately set to ensure the validity of certificates. Here are some steps to check and adjust the date and time settings on your device:
- Check the system date and time: Look at the date and time displayed on your device and make sure they are accurate. If they are incorrect, proceed to the next step.
- Adjust the date and time: Access the settings on your device to adjust the date and time. The process may vary slightly depending on your operating system. On Windows, right-click the clock in the taskbar and select “Adjust date/time,” while on macOS, go to System Preferences > Date & Time. On mobile devices, the date and time settings are typically found in the device’s general settings.
- Synchronize with an internet time server: To ensure the accuracy of your device’s clock, enable the option to synchronize with an internet time server. This option is usually available in the date and time settings. By synchronizing with a time server, your device will automatically update the date and time based on the server’s information.
- Restart your device and browser: After making changes to the date and time settings, restart your device to apply the updates. Additionally, close and reopen your web browser to ensure the changes take effect.
Checking and adjusting the date and time settings on your device can often resolve internet security certificate errors. It is also crucial to ensure that your device’s clock remains accurate, especially if it tends to drift or if you frequently travel across different time zones. By keeping your device’s date and time in sync, you can avoid potential certificate errors and enhance the overall security of your browsing experience.
Clearing the Browser Cache and Temporary Files
Clearing the browser cache and temporary files is another troubleshooting step that can help resolve internet security certificate errors. Stale or corrupted cache and temporary files can interfere with the validation of certificates, causing errors to occur. Here’s how you can clear the cache and temporary files in popular web browsers:
- Google Chrome: Click on the three-dot menu in the top-right corner, go to More Tools, and select Clear browsing data. In the Clear browsing data window, choose a time range (such as “All time”) and check the box next to “Cached images and files.” Click on the Clear data button to remove the cache.
- Mozilla Firefox: Click on the three-line menu in the top-right corner, go to Options, and select Privacy & Security. Scroll down to the Cookies and Site Data section and click on “Clear Data.” Make sure the box next to “Cached Web Content” is checked, and then click on the Clear button.
- Microsoft Edge: Click on the three-dot menu in the top-right corner, go to Settings, and select Privacy, search, and services. Under the Clear browsing data section, click on “Choose what to clear.” Check the box next to “Cached images and files” and click on the Clear button.
- Safari: Go to the Safari menu, select Preferences, and click on the Privacy tab. Click on “Manage Website Data” and then click on the Remove All button to clear the cache.
After clearing the cache and temporary files, close and reopen your web browser for the changes to take effect. This process will remove any stored information that might be causing certificate errors and allow your browser to retrieve fresh data from the websites you visit.
Keep in mind that clearing the cache and temporary files will also remove saved passwords, autofill data, and browsing history. However, it is a safe troubleshooting step that can help resolve certificate errors and improve the overall performance of your browser.
Updating Your Browser to the Latest Version
Keeping your web browser up to date is crucial for optimal performance, security, and compatibility with the latest internet security certificates. Outdated browser versions can sometimes lead to certificate errors and other browsing issues. Here’s why it’s important to regularly update your browser and how you can do it:
Why updating your browser matters:
- Security patches: Browser updates often include critical security patches that address vulnerabilities discovered in previous versions. By updating your browser, you ensure that you have the latest security measures in place to protect against potential threats.
- Certificate compatibility: Browsers need to recognize and trust new certificate authorities and cryptographic protocols. Updates help ensure that your browser remains compatible with the latest internet security certificates, allowing you to access websites without encountering certificate errors.
- Improved performance and features: Browser updates often include performance enhancements and new features that can enhance your browsing experience. By staying up to date, you can take advantage of these improvements and enjoy a smoother and more feature-rich browsing experience.
How to update your browser:
Updating your web browser is typically a straightforward process. Here’s a general guide on how to update some popular browsers:
- Google Chrome: Click on the three-dot menu in the top-right corner, go to Help, and select “About Google Chrome.” Chrome will automatically check for updates and install them if available. You may need to relaunch the browser to complete the update.
- Mozilla Firefox: Click on the three-line menu in the top-right corner, go to Help, and select “About Firefox.” Firefox will check for updates and download them if necessary. Once the update is downloaded, click on the Restart to Update Firefox button to complete the process.
- Microsoft Edge: Edge updates are typically included as part of Windows updates. Make sure to install the latest Windows updates to keep Edge up to date. You can check for updates by going to Settings > Update & Security > Windows Update.
- Apple Safari: On macOS, Safari updates are distributed through Software Update. Go to the Apple menu, select “System Preferences,” and click on Software Update to check for available updates. On iOS, updates for Safari are included with iOS updates. Go to Settings > General > Software Update to check for updates.
Regularly updating your browser is an essential step in maintaining a secure and hassle-free browsing experience. By ensuring that you have the latest version, you can avoid certificate errors and enjoy improved performance and new features offered by the browser developers.
Disabling Antivirus or Firewall Temporarily
Antivirus software and firewalls are essential security measures that help protect your device from malware and unauthorized access. However, in some cases, they can interfere with the proper functioning of internet security certificates and cause errors. Temporarily disabling your antivirus software or firewall can help determine if they are the cause of the certificate errors. Here’s how you can do it:
Disabling antivirus software:
- Windows: Locate the icon for your antivirus software in the system tray, right-click on it, and look for options like “Real-time protection” or “Disable.” Alternatively, open the antivirus program from the Start menu and navigate to settings or preferences where you can find an option to temporarily disable it. Remember to re-enable the antivirus software after troubleshooting.
- Mac: Open the antivirus software from the Applications folder or by clicking on its icon in the menu bar. Look for an option to disable or turn off real-time protection. Make sure to enable the antivirus software again once you have finished troubleshooting.
Disabling the firewall:
- Windows: Go to the Control Panel and click on “System and Security” or “Windows Security.” From there, select “Windows Firewall.” In the left sidebar, click on “Turn Windows Defender Firewall on or off.” Choose the option to turn off the firewall and click on Apply. Remember to turn the firewall back on once you’ve completed the troubleshooting.
- Mac: Open System Preferences from the Apple menu and click on “Security & Privacy.” Select the “Firewall” tab and click on the lock icon to make changes. Enter your password, then click on the “Turn Off Firewall” button. Once you have finished troubleshooting, click on the lock icon again to re-enable the firewall.
Temporarily disabling your antivirus software or firewall can help determine if they are causing internet security certificate errors. If the errors no longer occur after disabling these security measures, it may indicate a configuration issue or compatibility problem. In such cases, you can explore the settings of your antivirus software or firewall to modify the configuration and allow proper functioning of the certificates.
Remember, when you disable your antivirus software or firewall, you are temporarily compromising your device’s security. Therefore, it is crucial to enable them again as soon as you have completed the troubleshooting process or determine that they are not the cause of the certificate errors. If you continue to experience certificate errors after disabling your security measures, it is recommended to seek further assistance or consider alternative troubleshooting solutions.
Modifying Browser Security Settings
Modifying your browser’s security settings can help resolve internet security certificate errors by adjusting how your browser handles and verifies SSL/TLS certificates. Here are some steps to modify the security settings in popular web browsers:
Google Chrome:
- Open Google Chrome and click on the three-dot menu in the top-right corner.
- Go to Settings and scroll down to the “Privacy and security” section.
- Click on “Security” and then select the “Advanced” section.
- Under the “Privacy and security” section, click on “Manage certificates.”
- In the “Certificates” dialog box, you can modify various settings, such as managing trusted root certificates and clearing SSL state.
Mozilla Firefox:
- Open Mozilla Firefox and click on the three-line menu in the top-right corner.
- Go to Options and select “Privacy & Security.”
- Scroll down to the “Certificates” section and click on “View Certificates.”
- In the “Certificate Manager” dialog box, you can manage various certificate-related settings, such as importing and deleting certificates, as well as modifying trust settings.
Microsoft Edge:
- Open Microsoft Edge and click on the three-dot menu in the top-right corner.
- Go to Settings and click on “Privacy, search, and services.”
- Scroll down to the “Security” section and click on “Security settings.”
- In the “Security” settings, you can adjust various security-related options, such as managing trusted certificates and configuring SSL/TLS settings.
By modifying browser security settings, you can customize how your browser handles SSL/TLS certificates and ensure a more secure browsing experience. However, it is essential to exercise caution and make informed decisions when changing these settings, as improper modifications may lead to security vulnerabilities or cause issues with other websites. If you are unsure about a particular setting, it is advisable to seek guidance or consult the browser’s documentation or support resources.
Keep in mind that modifying browser security settings is an advanced troubleshooting step and may not always resolve internet security certificate errors. If certificate errors persist or appear on multiple websites, it is recommended to explore other troubleshooting steps or seek further assistance.
Ensuring the Certificates are Not Revoked
Internet security certificates can be revoked if they are compromised or if the certificate holder’s authorization is revoked. Browsers regularly check for certificate revocations to ensure that users are protected against potentially unsafe websites. If you are experiencing certificate errors, it is crucial to verify that the certificates in question are not revoked. Here are some steps to ensure the certificates are not revoked:
Checking certificate revocation status:
- Open the website certificate: Click on the padlock icon in the browser’s address bar to view the website certificate details. Look for a “View Certificate” or similar option to access the certificate information. This may vary depending on your browser.
- Check the certificate details: Once you have accessed the certificate details, look for information about the issuer, validity period, and certificate revocation status. Check if there are any warnings or indications that the certificate has been revoked.
- Verify the issuer: Ensure that the certificate is issued by a trusted certificate authority (CA). If the issuer is not recognized or appears suspicious, it could indicate a potential issue or a revoked certificate.
- Additional verification: You can also manually check the revocation status of a certificate by searching for the issuing CA’s revocation services on their website. They typically provide a method to search for revoked certificates using the certificate’s serial number or other identifier.
If you find that the certificates in question are indeed revoked, it is advisable to refrain from accessing the website, as it may pose a security risk. Revoked certificates are invalidated to protect users from potential attacks or unauthorized access to sensitive information.
In some cases, certificate revocation errors may occur due to issues with the browser’s certificate revocation checking process. If you encounter persistent certificate errors, even for valid certificates, you can try disabling the certificate revocation checking temporarily to see if it resolves the issue. However, it is essential to re-enable this feature after troubleshooting to maintain robust security measures.
Checking the revocation status of certificates is an important step in troubleshooting certificate errors. By ensuring that certificates are not revoked, you can have confidence that the websites you visit are secure and trustworthy.
Bypassing Certificate Warnings (Not Recommended)
When encountering internet security certificate errors, it may be tempting to bypass these warnings and proceed to access the website. However, bypassing certificate warnings is not recommended and can potentially compromise your online security. Here’s why bypassing certificate warnings should be avoided:
Risk of compromise: Certificate warnings are designed to alert users when there is a potential security risk, such as an invalid or expired certificate. Bypassing these warnings means disregarding these important indicators, leaving you vulnerable to potential attacks or fraudulent websites.
Loss of trust: Internet security certificates play a vital role in establishing trust between a user’s browser and a website. Bypassing certificate warnings erodes this trust and undermines the purpose of SSL/TLS certificates. It is important to rely on proper certificate validation to ensure the authenticity and security of the websites you visit.
Increased exposure to phishing attacks: By bypassing certificate warnings, you may unknowingly expose yourself to phishing attacks. Attackers can use fake or compromised certificates to create convincing replicas of legitimate websites, luring users into sharing sensitive information. Trusting valid certificates and avoiding websites with certificate errors reduces the risk of falling victim to phishing attempts.
It is crucial to note that certificate errors are often indicators of potential security risks or misconfigurations. Instead of bypassing these warnings, it is recommended to address the root cause of the certificate errors or seek assistance from the website administrator or your IT support team.
If you regularly encounter certificate errors on a trusted website, it indicates a potential configuration issue that should be resolved by the website owner. Contacting the website’s support or technical team and providing details about the error can help expedite the resolution.
Remember, your online security is of utmost importance, and bypassing certificate warnings compromises that security. It is always better to err on the side of caution and trust the certificate validation process to ensure a safe and trustworthy browsing experience.
Invalid Certificates: HTTPS vs. HTTP
Internet security certificates are primarily associated with websites that use the HTTPS protocol. Websites secured with HTTPS encrypt the data exchanged between your browser and the web server, providing a secure and private connection. However, it is important to understand the implications of invalid certificates when it comes to distinguishing between HTTPS and HTTP websites. Here’s what you need to know:
HTTPS (Hypertext Transfer Protocol Secure):
Websites that use HTTPS are secured with an SSL/TLS certificate, which ensures the authenticity and integrity of the connection. When you access an HTTPS website, your browser confirms that the website’s SSL/TLS certificate is valid and issued by a trusted certificate authority (CA). If the certificate is invalid or expired, your browser will display a warning that the website’s connection may not be secure.
It is crucial to pay attention to these warnings as they indicate potential security risks. An invalid or expired certificate may suggest that the website is not properly secured or that it could be an imposter site attempting to deceive users. In such cases, it is advisable to avoid accessing the website until the certificate issue is resolved.
HTTP (Hypertext Transfer Protocol):
HTTP websites, without the “S” in HTTPS, do not have an SSL/TLS certificate and therefore do not provide a secure connection. These websites transfer data in plain text, which means that any information exchanged between your browser and the web server is susceptible to interception or tampering. While accessing HTTP websites, you will not encounter certificate warnings but should be aware that the lack of encryption poses potential security risks.
It is worth noting that many website owners are switching from HTTP to HTTPS to enhance security and ensure the privacy of their users’ data. It is encouraged to favor HTTPS websites when possible, especially for sensitive transactions and information exchange. Most modern web browsers also prioritize HTTPS websites in search results to encourage a safer browsing experience.
When it comes to internet security certificates, invalid certificates pose a significant risk regardless of whether a website uses HTTP or HTTPS. While HTTPS websites provide encryption and validation through SSL/TLS certificates, it is important to exercise caution and avoid accessing websites with invalid or expired certificates, regardless of the protocol used.
Staying vigilant and being mindful of certificate warnings is essential in maintaining a secure online experience. Verify the validity of certificates and prioritize HTTPS websites to ensure the highest level of security while browsing the internet.
Configuring Trusted Sites List
Configuring your browser’s trusted sites list can help manage internet security certificate errors and ensure a seamless browsing experience on trusted websites. By adding websites to the trusted sites list, you instruct your browser to automatically trust the SSL/TLS certificates associated with those websites. Here’s how to configure the trusted sites list in popular web browsers:
Google Chrome:
- Open Google Chrome and click on the three-dot menu in the top-right corner.
- Go to Settings and scroll down to the “Privacy and security” section.
- Click on “Security” and then select “Manage certificates.”
- In the “Certificates” dialog box, go to the “Trusted Root Certification Authorities” tab.
- Click on the “Import” button and follow the prompts to add the websites’ SSL/TLS certificates to the trusted list.
Mozilla Firefox:
- Open Mozilla Firefox and click on the three-line menu in the top-right corner.
- Go to Options and select “Privacy & Security.”
- Scroll down to the “Certificates” section and click on “View Certificates.”
- In the “Certificate Manager” dialog box, go to the “Authorities” tab.
- Click on the “Import” button and follow the prompts to add the websites’ SSL/TLS certificates to the trusted list.
Microsoft Edge:
- Open Microsoft Edge and click on the three-dot menu in the top-right corner.
- Go to Settings and click on “Privacy, search, and services.”
- Scroll down to the “Security” section and click on “Manage certificates.”
- In the “Certificates” dialog box, go to the “Trusted Root Certification Authorities” tab.
- Click on the “Import” button and follow the prompts to add the websites’ SSL/TLS certificates to the trusted list.
By adding websites to the trusted sites list, you instruct your browser to trust the certificates associated with those sites, reducing the likelihood of encountering certificate errors. However, it is important to exercise caution and only add websites that you trust and believe to have valid SSL/TLS certificates. Adding untrusted or malicious websites to the trusted list could expose you to security risks.
Configuring the trusted sites list provides a convenient way to manage certificate errors on websites you frequently visit and trust. It effectively streamlines the validation process, allowing your browser to establish a secure connection with trusted websites without generating certificate warnings. Regularly reviewing and updating the trusted sites list can help ensure an optimal and secure browsing experience.
Dealing with Self-Signed Certificates
Self-signed certificates are SSL/TLS certificates that are signed by the entity that issued them, rather than a trusted third-party certificate authority (CA). These certificates are often used by individuals or organizations for internal purposes, testing environments, or local network applications. However, self-signed certificates can cause certificate errors in web browsers due to their lack of endorsement from a trusted CA. Here are some considerations for dealing with self-signed certificates:
Understanding the risks:
Self-signed certificates do not undergo the same level of rigorous validation as those issued by trusted CAs. As a result, your web browser will not automatically trust these certificates, and you may encounter certificate errors when accessing websites or applications secured with self-signed certificates. It is important to understand that using self-signed certificates introduces certain security risks, as they are not backed by the same level of trust and verification as certificates issued by trusted CAs.
Bypassing certificate errors (not recommended):
In some situations, you may be presented with the option to bypass certificate errors and proceed to access a website or application secured with a self-signed certificate. While this may allow you to continue, it is not recommended due to the inherent security risks involved. Bypassing certificate errors means that you are disregarding the warning signs that indicate a potential security compromise. It is crucial to exercise caution and refrain from accessing websites or applications secured with self-signed certificates unless you fully trust the source and understand the associated risks.
Importing self-signed certificates:
If you need to access a website or application secured with a self-signed certificate regularly, you may choose to import the certificate into your browser’s trusted certificates or keychain. By manually adding the self-signed certificate, you instruct your browser to trust it, reducing the likelihood of encountering certificate errors. However, importing self-signed certificates should only be done for trusted sources, as importing certificates from unknown or untrusted entities may expose you to security risks.
Using alternative browsers or configurations:
Some browsers or configurations may be more lenient with self-signed certificates or offer specific settings to bypass or ignore certificate errors. While this may provide temporary relief from certificate errors, it is important to understand that these configurations may lower your level of protection against potentially harmful websites. If you choose to utilize such browsers or configurations, exercise caution and ensure that other security measures are in place to mitigate the associated risks.
In summary, self-signed certificates can be a useful tool for internal or specific purposes, but they come with inherent security risks. It is important to assess the trustworthiness of the source before bypassing or importing self-signed certificates. Understanding the implications of using self-signed certificates and adopting other security measures will help you navigate the complexities associated with these types of certificates safely.
Checking SSL/TLS Protocols and Cipher Suites
SSL/TLS protocols and cipher suites are cryptographic protocols and algorithms used to establish secure connections between a web browser and a web server. Checking and configuring these protocols and cipher suites can help resolve internet security certificate errors and ensure a strong and secure connection. Here’s how you can check and modify these settings:
Checking SSL/TLS protocols:
- Open your web browser: Launch your preferred web browser and access the browser settings or preferences.
- Find the security settings: Look for the security or privacy section within the browser’s settings. The location may vary depending on the browser you are using.
- Check the SSL/TLS protocols: Within the security settings, locate the section related to SSL/TLS protocols. Common protocols include TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3. Ensure that the appropriate protocols are enabled or selected, depending on your security requirements.
- Disable outdated or insecure protocols: Disable any outdated or insecure protocols, such as SSL 2.0 and SSL 3.0, to enhance security. These older protocols are susceptible to security vulnerabilities and should not be used.
Checking cipher suites:
- Locate the cipher suite settings: In the same security or privacy section of your browser’s settings, look for the cipher suite settings.
- View the available cipher suites: Your browser will list the available cipher suites that it supports. These suites are combinations of cryptographic algorithms used to encrypt and decrypt data during the SSL/TLS session.
- Ensure strong cipher suites are enabled: Check that strong cipher suites, such as those using AES (Advanced Encryption Standard) or SHA (Secure Hash Algorithm), are enabled. Disable any weak or deprecated cipher suites to maintain a high level of security.
Checking SSL/TLS protocols and cipher suites is an important step in troubleshooting certificate errors and ensuring a secure connection. It is recommended to enable the latest and most secure protocols, such as TLS 1.2 or TLS 1.3, as well as strong cipher suites, to prioritize security while browsing the web.
However, it’s worth noting that modifying SSL/TLS protocols and cipher suites should be done with caution, as some websites or applications may have specific protocol and cipher suite requirements. It is always a good idea to keep your browser up to date to ensure you have the latest security enhancements and algorithm support.
By regularly checking and configuring SSL/TLS protocols and cipher suites, you can enhance the security of your browsing experience and reduce the likelihood of encountering internet security certificate errors.
Resolving Certificate Chain Issues
Certificate chain issues can occur when the SSL/TLS certificate presented by a website does not have a proper or complete chain of trust back to a trusted root certificate authority (CA). These issues can result in certificate errors and warnings in web browsers. Resolving certificate chain issues is crucial to ensure secure and trusted connections to websites. Here’s how you can address certificate chain issues:
Identify the certificate chain:
- View the certificate details: Click on the padlock icon in the browser’s address bar and select “Certificate” or “View Certificate” to access the details of the certificate.
- Inspect the certificate chain: Look for the certificate chain information, which usually includes the website’s SSL/TLS certificate and one or more intermediate certificates. The chain should ultimately lead to a trusted root certificate.
- Check for missing or incorrect certificates: Verify that all the certificates in the chain are present and correctly linked. If any intermediate certificate is missing or improperly configured, it can lead to certificate chain issues.
Addressing certificate chain issues:
- Contact the website administrator: If you encounter certificate chain issues on a website, contact the website administrator or technical support team. They can investigate and resolve the issue from their end. Make sure to provide them with the specific details of the certificate chain error for effective troubleshooting.
- Verify the intermediate certificates: If you have access to the intermediate certificates associated with the website’s SSL/TLS certificate, verify their validity and ensure they are correctly installed on the web server. The website administrator can guide you on how to obtain and verify the necessary intermediate certificates.
- Update the root certificate store: Occasionally, certificate chain issues occur due to outdated or missing root certificates on your device. Updating the root certificate store on your operating system or browser can resolve such issues. Consult the documentation or support resources for your specific operating system or browser to learn how to update the root certificates.
- Intermediate certificate bundle: Some websites may provide an intermediate certificate bundle that includes all the necessary intermediate certificates. Follow the website’s instructions to download and install the intermediate certificate bundle, which can help establish a proper certificate chain.
Resolving certificate chain issues requires collaboration between website administrators and users. Promptly informing the website administrator about any certificate chain issues is crucial for them to address the problem effectively. Remember, ensuring a valid and complete certificate chain is important for establishing trust and maintaining a secure browsing experience.
If you continue to encounter certificate chain issues on multiple websites or find it challenging to resolve them, it may be best to consult an IT professional or seek assistance from your organization’s technical support team. They can provide advanced troubleshooting steps and guidance tailored to your specific environment.
Using Third-Party Tools for Certificate Troubleshooting
When troubleshooting certificate-related issues, utilizing third-party tools can provide valuable insights and assistance. These tools are specifically designed to diagnose, analyze, and resolve various certificate problems. Here’s how you can leverage third-party tools for certificate troubleshooting:
Certificate Validation Tools:
Certificate validation tools are designed to check the validity and integrity of SSL/TLS certificates. They can confirm if a certificate is properly signed, has a valid chain of trust, and complies with industry standards. These tools can help identify issues such as expired certificates, incorrect chain configurations, or revoked certificates. Some popular certificate validation tools include SSL Labs (Qualys), SSL Checker (SSL Shopper), and Keyhub (Axur).
Certificate Revocation Checking Tools:
Certificate revocation checking tools are used to verify if a certificate has been revoked by the issuing certificate authority (CA). These tools check certificate revocation status against certificate revocation lists (CRLs) or online certificate status protocol (OCSP) responders. They help determine if a certificate is still considered trustworthy. Notable tools in this category include CRLDP (Certificate Revocation List Distribution Points) checkers and OCSP responders.
SSL/TLS Scanner Tools:
SSL/TLS scanner tools perform comprehensive security scans on websites to identify vulnerabilities, misconfigurations, and certificate-related issues. These tools assess the certificate’s strength, encryption protocols, cipher suites, and other security parameters. They provide detailed reports and recommendations to address any identified issues. Popular SSL/TLS scanner tools include Qualys SSL Labs Server Test, SSL/TLS Server Test (High-Tech Bridge), and ImmuniWeb SSLScan.
Certificate Management Platforms:
If you are managing certificates for multiple websites or a complex environment, certificate management platforms can streamline the management process. These platforms provide centralized visibility, automated certificate deployments, renewal reminders, and comprehensive monitoring of certificate usage. They help ensure proper configuration and timely renewal of certificates. Examples of certificate management platforms include CertCentral (DigiCert), Keyfactor Command, and GlobalSign Certificate Manager.
Using third-party tools can greatly assist in diagnosing and resolving certificate-related issues. However, it is important to choose reputable and trusted tools to ensure the accuracy and security of the results. Additionally, while these tools provide valuable insights, it is advisable to consult with cybersecurity professionals or website administrators to interpret and address the issues identified.
Remember that using third-party tools is part of a holistic approach to certificate troubleshooting. In complex scenarios or persistent problems, seeking professional assistance or engaging with the certificate authority (CA) that issued the certificate can provide in-depth guidance and support for resolving critical certificate-related issues.
Seeking Professional Help and Support
In some cases, resolving internet security certificate issues may require expertise and assistance from professionals with in-depth knowledge of certificate management and troubleshooting. Seeking professional help and support can ensure efficient and accurate resolution of complex certificate-related problems. Here’s how professionals can offer valuable assistance:
Certificate Authorities (CAs):
CAs are responsible for issuing and managing SSL/TLS certificates. If you encounter persistent certificate errors or require expert guidance, reaching out to the CA that issued the certificate can be beneficial. They can provide insights into certificate configuration, troubleshoot potential issues related to their certificates, and offer recommendations for resolving the errors.
IT Support Teams:
Your organization’s IT support team or security professionals can be useful resources for certificate troubleshooting. They can provide guidance specific to your environment, assist in diagnosing certificate-related issues, and offer solutions tailored to your network infrastructure. They may also help with the installation, management, and renewal of certificates for internal systems and applications.
Certificate Management Providers:
If you are using a certificate management platform or service, the provider’s support team can offer expertise in managing and troubleshooting certificate-related issues. They can guide you through the configuration process, provide best practices for certificate management, and help resolve any technical problems that may arise.
Security Consultants:
Engaging security consultants with expertise in certificate management and internet security can be beneficial, especially for complex environments or critical systems. They can perform comprehensive audits, review your certificate infrastructure, identify vulnerabilities or misconfigurations, and develop a tailored plan to enhance your overall security posture.
When seeking professional help, it is important to provide detailed information about the certificate errors and the specific environment in which they occur. This will assist the professionals in accurately diagnosing and addressing the issues. Collaborating with professionals ensures that the certificate-related problems are resolved effectively and helps maintain a secure online presence.
Remember to follow any recommended best practices provided by the professionals and to stay proactive in keeping your certificates up to date, regularly monitoring their validity, and promptly addressing any errors or warnings that occur.
In complex scenarios or if you lack internal expertise, seeking professional help and support is a prudent step to ensure the secure and proper operation of your certificate infrastructure.