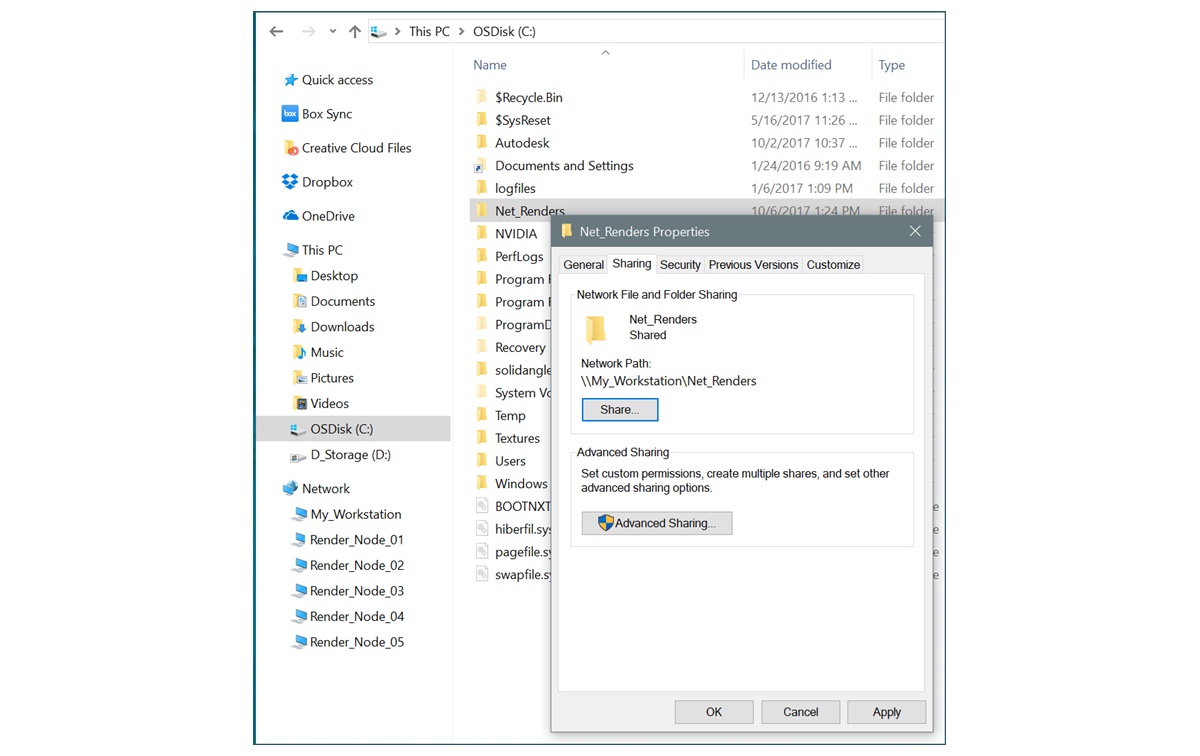
What is the Universal Naming Convention (UNC Path)?
The Universal Naming Convention (UNC Path) is a format used to identify and access resources on a network. It provides a standardized way to reference files, folders, and printers by their network location rather than relying on specific drive letters or IP addresses. UNC Paths are primarily used in Windows environments and are supported by most networking protocols, including Server Message Block (SMB) and Common Internet File System (CIFS).
A UNC Path consists of two components: the server name and the share name. The server name identifies the computer or device hosting the resource, while the share name specifies the specific resource being accessed. The UNC Path follows the format \\server\share, with the backslashes acting as separators between the server and share names.
For example, let’s say we have a network file server named “FileServer” and a shared folder named “Documents”. The UNC Path to access this shared folder would be \\FileServer\Documents. This allows users on the network to access the shared folder regardless of their individual drive mappings or network configurations.
UNC Paths also support accessing specific files within a shared folder. By appending the file name to the UNC Path, users can directly access that file. For example, \\FileServer\Documents\report.docx would directly access the “report.docx” file within the “Documents” shared folder.
UNC Paths are incredibly useful in networked environments as they provide a consistent and reliable way to access resources. They eliminate the need to remember and maintain specific drive letters or IP addresses. Additionally, UNC Paths enable simplified sharing and collaboration by allowing multiple users to access and modify resources on the network.
In subsequent sections, we will explore how to format a UNC Path, access files and folders using a UNC Path, common UNC Path issues and solutions, mapping a network drive to a UNC Path, the benefits of using UNC Paths, and best practices for working with UNC Paths.
How to Format a UNC Path
Formatting a UNC Path correctly is crucial to ensure proper access to network resources. The UNC Path follows a specific structure and must be formatted correctly to function effectively.
To format a UNC Path, follow these guidelines:
- Start with two backslashes (\\) to indicate the beginning of the UNC Path.
- Next, specify the server name. The server name can be an IP address or the hostname of the server.
- After the server name, use another backslash to separate the server name from the share name.
- Finally, specify the share name, which represents the specific resource being accessed.
Here is an example of a properly formatted UNC Path: \\ServerName\ShareName
It’s important to note that the server name and share name are case-insensitive, meaning they can be written in uppercase or lowercase letters without affecting the UNC Path’s functionality. However, it is recommended to use consistent casing for clarity and ease of use.
When using a UNC Path to access a specific file within a shared folder, append the filename to the end of the UNC Path, separated by another backslash. For example: \\ServerName\ShareName\FileName
Having a clear understanding of the UNC Path format ensures that you can accurately reference and access network resources. By following these formatting guidelines, you can ensure seamless network connectivity and efficient collaboration.
In the next section, we will learn how to access files and folders using a UNC Path.
Accessing Files and Folders Using a UNC Path
Accessing files and folders using a UNC Path provides a convenient and reliable way to navigate network resources. With a properly formatted UNC Path, users can easily access shared folders and files regardless of their individual network configurations or drive mappings.
To access files and folders using a UNC Path, follow these steps:
- Open the file explorer on your computer. This can typically be done by clicking on the “File Explorer” or “This PC” icon in the taskbar.
- In the file explorer, click on the address bar at the top. Alternatively, you can press “Ctrl + L” to directly access the address bar.
- Type the UNC Path of the shared folder or file you want to access. The UNC Path should follow the format \\ServerName\ShareName for accessing folders and \\ServerName\ShareName\FileName for accessing specific files within a shared folder.
- Press “Enter” or click on the “Go” button to navigate to the specified UNC Path.
Once you have accessed a shared folder or file using the UNC Path, you can perform various operations, such as opening, editing, copying, or deleting files. These actions are carried out in the same way as you would interact with local files and folders.
It’s important to note that to successfully access files and folders using a UNC Path, you must have the necessary permissions and network connectivity. Ensure that you have the appropriate access rights and are connected to the network before attempting to access resources via UNC Paths.
By utilizing UNC Paths, individuals and teams can easily collaborate on shared files and folders. It eliminates the need for complex drive mappings and simplifies the process of accessing network resources from any computer on the network.
In the next section, we will explore common UNC Path issues and their solutions.
Common UNC Path Issues and Solutions
While UNC Paths provide a convenient way to access network resources, there can be instances where issues arise. Understanding and troubleshooting these common UNC Path issues can help ensure smooth access and collaboration on networked files and folders.
Here are some common UNC Path issues and their solutions:
- Invalid UNC Path: If you encounter an “Invalid UNC Path” error, double-check the syntax and ensure that the UNC Path is correctly formatted. Verify that the server name and share name are accurate and that there are no typos or missing characters.
- Network Connectivity Problems: If you’re unable to access a UNC Path, check your network connectivity. Ensure that you are connected to the network and have proper internet access. Try accessing other network resources to determine if the issue is specific to the UNC Path or a broader network problem.
- Permission Issues: If you receive an “Access Denied” error when trying to access a UNC Path, check your permissions. Confirm that you have the necessary rights to access the shared resource. Contact the server administrator or owner of the resource to request appropriate permissions.
- Firewall Blocking UNC Path: If you have a firewall enabled, it may be blocking access to UNC Paths. Configure the firewall settings to allow network access to the specific server and share. Consult your organization’s IT department or network administrator for assistance.
- Server Unavailable: In case the server hosting the shared resource is offline or unavailable, you won’t be able to access the UNC Path. Verify if the server is online and functioning properly. Contact the server administrator if necessary.
By addressing these common UNC Path issues, you can resolve connectivity and access problems, ensuring uninterrupted access to network resources.
In the next section, we will discuss how to map a network drive to a UNC Path for easier access.
Mapping a Network Drive to a UNC Path
Mapping a network drive to a UNC Path allows you to assign a drive letter to a shared folder, making it easily accessible and convenient to navigate. By mapping a network drive, you can access network resources as if they were local drives on your computer.
Follow these steps to map a network drive to a UNC Path:
- Open File Explorer on your computer by clicking on the “File Explorer” or “This PC” icon in the taskbar.
- Click on the “This PC” option on the left-hand side of the File Explorer window.
- From the top menu, click on the “Map network drive” option. This will open the “Map Network Drive” dialog box.
- In the “Map Network Drive” dialog box, choose a drive letter from the drop-down menu. You can select any available letter that you prefer.
- In the “Folder” field, enter the UNC Path of the shared folder you want to map. You can either enter the UNC Path directly (e.g., \\ServerName\ShareName) or browse the network to locate and select the shared folder.
- Optional: Check the “Reconnect at sign-in” box if you want the network drive to be automatically mapped every time you log into your computer.
- Click on the “Finish” button to complete the mapping process.
Once the network drive is mapped, you can open it through File Explorer or any file management utility, and access the shared resources just like you would with local drives. The mapped network drive will retain the assigned drive letter and provide seamless access to the shared folder or files.
Mapped network drives offer the convenience of quick access to frequently used network resources. You can create shortcuts, save files, and perform various operations on the shared files and folders directly through the mapped drive.
If you no longer need to access the mapped network drive, you can right-click on it in File Explorer and select “Disconnect” to remove the mapping.
In the next section, we will discuss the benefits of using UNC Paths for accessing network resources.
Benefits of Using UNC Paths
Using UNC Paths for accessing network resources offers several advantages that contribute to a more efficient and user-friendly network environment. Let’s explore some of the key benefits of using UNC Paths:
- Consistent Accessibility: UNC Paths provide a consistent way to access shared resources on a network. Regardless of individual drive mappings or network configurations, UNC Paths ensure that users can reliably access files and folders by specifying their network location. This promotes seamless collaboration and eliminates the need for users to remember specific drive letters or IP addresses.
- Reduction in Dependency on Drive Letters: When accessing network resources using drive letters, conflicts can arise when multiple users have different mappings for the same drive letter. UNC Paths eliminate these conflicts by allowing users to access resources directly through their network location, bypassing the need for specific drive letters. This improves compatibility and eliminates confusion caused by conflicting drive letter assignments.
- Flexibility in Resource Sharing: With UNC Paths, file sharing and collaboration become easier. Users can share resources by providing the UNC Path to others, who can then access the shared files or folders directly. This simplifies remote access and enables efficient collaboration, particularly in distributed or remote work environments.
- Centralized Administration: UNC Paths facilitate centralized administration of network resources. By using UNC Paths, network administrators can easily manage and control access to shared files and folders. They can assign appropriate permissions to users and groups, ensuring secure and efficient resource management.
- Improved System Stability: UNC Paths offer a more stable solution compared to relying on specific drive mappings. Drive mappings can sometimes be lost or disconnected due to various reasons, such as system updates or network changes. UNC Paths provide a reliable way to access resources and reduce the chances of disruptions caused by lost drive mappings.
The benefits of using UNC Paths make them a preferred choice for accessing network resources in Windows environments. By utilizing UNC Paths, organizations can enhance collaboration, simplify resource management, and improve the overall functionality and stability of their network.
In the next section, we will discuss some limitations and best practices for working with UNC Paths.
Limitations of UNC Paths
While UNC Paths offer numerous benefits for accessing network resources, they also come with some limitations that users should be aware of. Understanding these limitations allows for better planning and mitigating potential issues when working with UNC Paths:
- Network Dependency: UNC Paths rely on network connectivity for accessing shared resources. If there are network issues or the server hosting the shared resource is unavailable, accessing the resource through the UNC Path may not be possible. It is important to ensure stable and reliable network connectivity to avoid disruptions in accessing network resources.
- Permissions and Security: UNC Paths adhere to the same permission and security settings as the shared resource they are accessing. If a user does not have appropriate permissions to access a shared folder or file, they will encounter access denied errors when trying to access the resource through the UNC Path. It is crucial to manage permissions correctly to ensure secure and authorized access to network resources.
- Length Limitations: UNC Paths have a limitation on the total length of the path. In Windows, the maximum length for a UNC Path is typically 260 characters. If the path exceeds this limit, users may encounter errors when trying to access the resource through the UNC Path. It is essential to keep the length of file and folder names within this limit to ensure accessibility.
- Case Sensitivity: Although UNC Paths are not case-sensitive, inconsistencies in case can lead to confusion and difficulties in accessing resources. It is recommended to use consistent casing for server names, share names, file names, and folder names when working with UNC Paths.
- Reliance on Server Name: UNC Paths depend on the server name to access shared resources. If the server name changes or if the server is decommissioned, accessing the shared resources through the UNC Path may no longer be possible. It is crucial to update and maintain UNC Paths when there are changes in the network infrastructure.
By understanding the limitations of UNC Paths, users can effectively plan and troubleshoot issues associated with accessing network resources. Proper network configuration, permissions management, and adherence to naming conventions help overcome these limitations and maximize the benefits of UNC Paths.
In the next section, we will discuss best practices for working with UNC Paths in order to optimize their usage and effectiveness.
Best Practices for Working with UNC Paths
To ensure optimal usage and effectiveness when working with UNC Paths, it is important to follow certain best practices. These practices help maintain consistency, enhance accessibility, and minimize potential issues when accessing network resources through UNC Paths:
- Consistent Naming Conventions: Use consistent and descriptive naming conventions for servers, shares, files, and folders. This promotes clarity and ease of use when referencing network resources through UNC Paths.
- Proper Permissions Management: Ensure that permissions are properly configured for shared resources. Assign appropriate permissions to users and groups to control access and maintain security. Regularly review and update permissions to align with changing requirements.
- Clear Documentation: Maintain clear and up-to-date documentation of UNC Paths used in your network. This documentation should include server names, share names, and any other relevant details to facilitate easy reference and accessibility for users.
- Regular Testing and Monitoring: Regularly test UNC Paths to ensure their accessibility and functionality. Monitor network connectivity and address any issues promptly to prevent disruptions in accessing shared resources.
- Avoid Long Paths: Keep file and folder names within the maximum path length limit of 260 characters to avoid issues with accessing resources through UNC Paths. Consider shorter and more concise names to maintain compatibility and accessibility.
- Network Mapping: Consider mapping frequently accessed UNC Paths to network drives. This provides users with a more convenient and familiar method of accessing shared resources, similar to local drives.
- Regular Backup and Recovery: Implement regular backup and recovery practices for shared resources accessed through UNC Paths. This ensures data protection and minimizes the risk of losing critical information.
By adhering to these best practices, organizations can maximize the benefits of UNC Paths and ensure a seamless experience when accessing network resources. Following standardized naming conventions, managing permissions effectively, documenting UNC Paths, and proactively testing and monitoring network connectivity contributes to a more efficient and user-friendly network environment.
Implementing these best practices enhances collaboration, accessibility, and security when working with UNC Paths.