The OSI Model: Overview
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a communication system into seven distinct layers. Each layer has a specific role in the transmission of data between devices in a network. It provides a structured approach for understanding how different networking protocols interact and enables the seamless exchange of information across different systems.
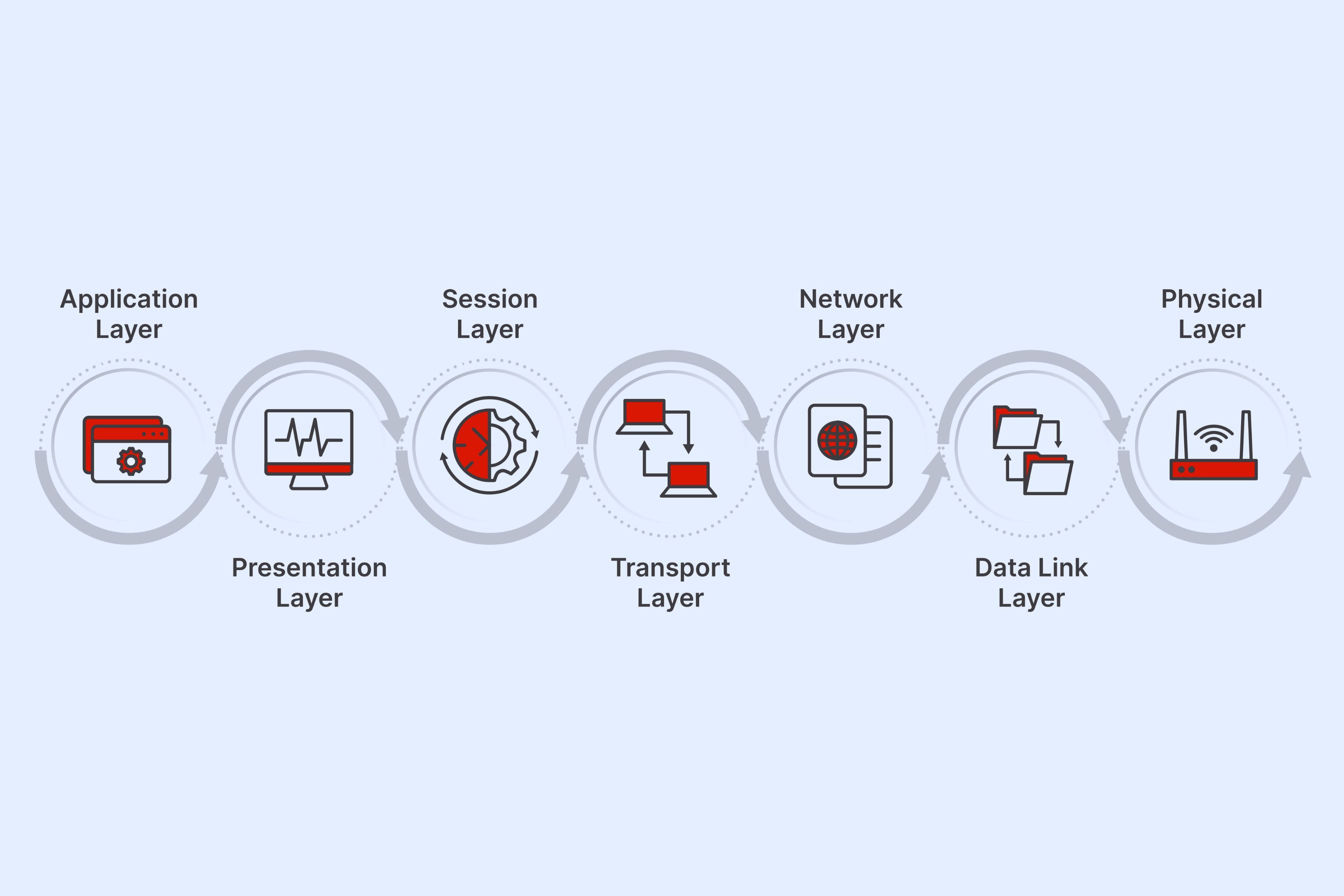
The seven layers of the OSI model, from bottom to top, are the Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, and Application Layer. Each layer builds upon the one below it, providing specific services and protocols to support network communication.
The Physical Layer, the lowest layer of the OSI model, is responsible for the transmission and reception of raw bit streams over a physical medium. It deals with the electrical, mechanical, and physical characteristics of the network, such as cables, connectors, and network devices. Ethernet, Wi-Fi, and USB are examples of technologies that operate at this layer.
The Data Link Layer, layer 2 of the OSI model, defines how data is formatted for transmission and provides error detection and correction mechanisms. It ensures the reliable transmission of data across a physical connection. Ethernet and Wi-Fi protocols, as well as switches and bridges, operate at this layer.
The Network Layer, layer 3 of the OSI model, handles the routing and forwarding of data packets across different networks. It defines protocols for logical addressing, subnetting, and routing. The Internet Protocol (IP) is a key protocol at this layer, and routers are the primary devices that operate in this layer.
The Transport Layer, layer 4 of the OSI model, provides end-to-end communication between hosts. It ensures the reliable delivery of data by handling segmentation, flow control, and error recovery. The Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are common protocols at this layer.
The Session Layer, layer 5 of the OSI model, establishes, maintains, and terminates sessions between applications. It manages the communication channels, synchronization, and session checkpoints. This layer allows multiple applications to share the same network connection.
The Presentation Layer, layer 6 of the OSI model, is responsible for data representation and encryption. It translates data into a format that the application layer can interpret and provides services like data compression and encryption. This layer ensures that data is presented in a consistent and meaningful manner.
The Application Layer, the top layer of the OSI model, is where user applications and services interact with the network. It includes protocols like Hypertext Transfer Protocol (HTTP) and File Transfer Protocol (FTP) that enable communication between users and network services.
By understanding the OSI model and its layers, network administrators and engineers can troubleshoot network issues, design efficient networks, and ensure interoperability between different systems. Each layer plays a crucial role in the transmission of data, and a deep understanding of these layers is fundamental in building and maintaining reliable networks.
What is a Firewall?
A firewall is a network security device that acts as a barrier between an internal network and the external internet. It implements security policies to control and monitor incoming and outgoing network traffic, based on a set of predefined rules or criteria. The primary function of a firewall is to protect the network from unauthorized access, malicious activities, and potential security threats.
A firewall can be either a hardware device or a software program that runs on a computer or network device. It operates by examining the data packets flowing through it and making decisions about whether to allow or block the packets based on the defined rules. These rules can be configured to restrict certain types of traffic, such as specific ports, protocols, or IP addresses, thereby preventing unauthorized access to the network.
Firewalls work at different layers of the OSI model, depending on their type and functionality. For instance, network firewalls operate at the Network Layer (Layer 3) or Transport Layer (Layer 4), while application-level firewalls operate at the Application Layer (Layer 7).
There are several types of firewalls, including packet-filtering firewalls, stateful inspection firewalls, proxy firewalls, and next-generation firewalls. Packet-filtering firewalls examine individual packets of data and filter them based on predefined rules. Stateful inspection firewalls, on the other hand, maintain information about the state of network connections, allowing them to make more informed decisions about packet filtering.
Proxy firewalls act as intermediaries between the internal network and the external internet. They process and filter network traffic on behalf of the internal devices, adding an extra layer of security by hiding the internal network’s IP addresses and potentially blocking access to certain websites or content.
Next-generation firewalls (NGFWs) combine the features of traditional firewalls with advanced security functionalities, such as intrusion prevention, deep packet inspection, and application awareness. NGFWs provide enhanced protection against modern threats, including malware, ransomware, and advanced persistent threats.
In addition to protecting the network from external threats, firewalls also help in enforcing internal security policies. They can restrict access to specific resources within the network, preventing unauthorized users from accessing sensitive data or resources. Firewalls also log network traffic, allowing administrators to monitor and investigate any potential security breaches or suspicious activities.
Understanding the Layers of the OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that defines the functions and interactions of a communication system. It divides the communication process into seven layers, each serving a specific purpose in the transmission of data over a network.
Let’s take a closer look at each layer of the OSI model:
1. Physical Layer: This layer is responsible for the physical transmission of data bits over a network medium. It deals with the electrical, mechanical, and physical aspects of communication, such as cables, connectors, and network interfaces. The Physical Layer defines the specifications for transmitting raw data between devices.
2. Data Link Layer: The Data Link Layer manages the flow of data between adjacent devices on a local network. It provides error detection and correction capabilities to ensure the reliable transmission of data. This layer is responsible for organizing data bits into frames and handling access to the physical medium.
3. Network Layer: The Network Layer facilitates the end-to-end delivery of data across multiple networks. It handles logical addressing, routing, and packet forwarding. This layer uses unique IP addresses to identify devices in a network and determines the best path for data transmission.
4. Transport Layer: The Transport Layer ensures reliable data delivery between end systems. It breaks the data into smaller segments, manages the flow control, and provides error recovery mechanisms. The Transport Layer establishes virtual connections between applications and ensures the successful transmission of data.
5. Session Layer: The Session Layer establishes, manages, and terminates communication sessions between applications. It allows different applications on the network to exchange data and synchronizes their communication. This layer manages session checkpoints and ensures the continuity of data exchange.
6. Presentation Layer: The Presentation Layer handles the data representation and transformation aspects of communication. It is responsible for data encryption, compression, and formatting to ensure compatibility between different systems. This layer helps in the interpretation of data received by the Application Layer.
7. Application Layer: The Application Layer interacts directly with user applications. It provides services and protocols that enable user access to network resources. This layer includes protocols like HTTP, FTP, and SMTP, which are used by applications to exchange data over the network.
The OSI model’s layering approach allows for modular design, easy troubleshooting, and interoperability between different systems. Each layer performs specific functions and relies on the layers beneath it to provide services. This model provides a standardized framework for designing, implementing, and managing complex network architectures.
Layer 1: Physical Layer
The Physical Layer is the first layer of the OSI model, responsible for the physical transmission of data bits over a network. It deals with the electrical, mechanical, and physical characteristics of the communication medium, such as cables, connectors, and network devices.
The primary function of the Physical Layer is to establish and maintain a physical connection between network devices. It defines the physical characteristics of the transmission medium, including the type of cable used, the voltage levels for signal transmission, and the data encoding scheme.
At this layer, data is transmitted in the form of raw bit streams. It ensures that the bit streams are properly encoded and transmitted across the network without errors. The Physical Layer handles tasks such as data encoding, signaling, and transmission synchronization.
The Physical Layer defines various physical characteristics and specifications that govern the transmission of data. These specifications include the type of cable, such as twisted-pair, coaxial, or fiber optic, and the connectors used to connect devices. It also determines the transmission speed or bandwidth of the network, measured in bits per second (bps).
Furthermore, the Physical Layer specifies the type of signaling used to transmit data over the network. Common signaling methods include amplitude modulation (AM), frequency modulation (FM), and phase modulation (PM). These methods help in conveying the data by modulating the physical signals that travel across the transmission medium.
In addition to the physical transmission aspects, the Physical Layer also deals with network devices such as repeaters and hubs. Repeaters regenerate and amplify signals to extend the distance over which data can be transmitted without degradation. Hubs, on the other hand, act as central connection points for devices within a network, allowing multiple devices to be connected together.
Examples of technologies and protocols that operate at the Physical Layer include Ethernet, Wi-Fi, USB, and HDMI. Ethernet, for instance, uses multiple twisted-pair cables or fiber optic cables to establish a physical connection between network devices. Wi-Fi, on the other hand, relies on radio waves for wireless communication.
Layer 2: Data Link Layer
The Data Link Layer is the second layer of the OSI model, responsible for the reliable transfer of data frames between adjacent devices on a local network. It provides the necessary protocols and services to ensure error-free and efficient data transmission.
The Data Link Layer’s primary function is to establish and maintain a link or connection between two directly connected devices. It handles the physical addressing of devices on the network and provides mechanisms for accessing the shared network medium. Additionally, it detects and corrects errors that may occur during data transmission.
At this layer, data is organized into frames, which are units of data that can be transmitted over the network. These frames contain information such as source and destination MAC addresses, control information, and error-checking codes.
The Data Link Layer employs two main types of protocols: Media Access Control (MAC) and Logical Link Control (LLC). The MAC sublayer is responsible for controlling access to the physical medium and handling issues such as collision detection and prevention in shared media environments. The LLC sublayer is responsible for providing error control, flow control, and synchronization, ensuring the reliable transmission of data.
Another important task of the Data Link Layer is to provide error detection and correction mechanisms. Through the use of techniques like cyclic redundancy check (CRC), the Data Link Layer can detect errors in the received data frames. If errors are detected, the receiving device can request the sender to retransmit the corrupted frames.
Furthermore, the Data Link Layer also manages the flow of data between devices. It implements flow control mechanisms to ensure that the receiving device can handle data at its own pace without overwhelming its buffer. This helps prevent data loss or congestion on the network.
The Data Link Layer operates at both the local and physical link levels. At the local level, it establishes communication between devices within the same local area network (LAN). At the physical link level, it provides connectivity between adjacent devices, allowing them to exchange data frames.
Ethernet and Wi-Fi are common examples of technologies that operate at the Data Link Layer. Ethernet protocols, such as Ethernet II and IEEE 802.3, define the standards for framing, addressing, and flow control mechanisms. Wi-Fi protocols, such as IEEE 802.11, provide wireless connectivity and the necessary data link controls for wireless network communication.
Layer 3: Network Layer
The Network Layer is the third layer of the OSI model, responsible for the routing and forwarding of data packets across different networks. It handles logical addressing, routing, and packet delivery to ensure that data reaches its intended destination efficiently and reliably.
The primary function of the Network Layer is to provide end-to-end communication between hosts on different networks. It establishes logical connections, known as paths, between devices and determines the best path for data transmission.
One of the key tasks of the Network Layer is logical addressing. Each device connected to a network has a unique identifier called an IP (Internet Protocol) address. The Network Layer uses IP addressing to identify the source and destination devices in a network, allowing for proper routing and delivery of data packets.
The Network Layer is responsible for routing, which involves determining the optimal path for data to travel from the source device to the destination device. Routing protocols, such as OSPF (Open Shortest Path First) and BGP (Border Gateway Protocol), are used to exchange routing information between routers and to calculate the best path based on factors such as network congestion, link reliability, and cost.
Packet forwarding is another crucial function of the Network Layer. Once the best path is identified by the routing process, the Network Layer ensures that data packets are correctly encapsulated and forwarded to the next hop along the route. Routers, which operate at the Network Layer, examine the destination IP address of each packet and determine the next hop based on their routing tables.
In addition to routing and forwarding, the Network Layer can also handle fragmentation and reassembly of data packets. If a packet is too large to be transmitted over a network, the Network Layer can break it into smaller fragments for transmission. At the receiving end, the Network Layer reassembles the fragments into the original packet.
The Internet Protocol (IP) is the primary protocol used at the Network Layer. It defines the addressing scheme and provides the necessary protocols for data routing and delivery. Other protocols, such as Internet Control Message Protocol (ICMP) for error reporting and Internet Group Management Protocol (IGMP) for multicast group management, operate at this layer as well.
By functioning at the Network Layer, routers play a crucial role in forwarding data between different networks. They receive data packets, examine the destination IP addresses, and determine the best path for forwarding the packets to their next destination, ensuring that data can flow seamlessly across interconnected networks.
Layer 4: Transport Layer
The Transport Layer is the fourth layer of the OSI model, responsible for providing reliable, end-to-end communication between applications running on different hosts. It ensures the efficient and error-free transmission of data by handling segmentation, flow control, and error recovery.
The Transport Layer’s primary function is to break down the data received from the upper layers into smaller, manageable units called segments. These segments are then transmitted over the network and reassembled at the receiving end. Segmenting the data helps in efficient transmission and allows for error recovery in case a segment is lost or corrupted.
The Transport Layer establishes and manages virtual connections, also known as transport connections, between applications. The two most common transport protocols at this layer are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP).
TCP is a connection-oriented protocol that provides reliable, error-checked, and ordered delivery of data. It ensures that all segments are received in their correct order and can detect and recover from packet loss or errors. TCP also handles flow control, ensuring that data is transmitted at an appropriate rate to prevent data overflow or congestion.
UDP, on the other hand, is a connectionless protocol that offers minimal error checking and no guarantee of ordered delivery. It is suitable for applications that require fast and lightweight data transmission, such as real-time streaming or online gaming. While UDP sacrifices reliability for speed, it still provides a basic level of error detection using checksums.
At the Transport Layer, both TCP and UDP use port numbers to direct the data to the appropriate application running on the receiving host. Port numbers help in distinguishing between different services or applications and allow multiple applications to communicate simultaneously.
In addition to segmentation and connection management, the Transport Layer also provides error detection and recovery mechanisms. By using techniques such as checksums, the Transport Layer can detect errors in received segments. If errors are detected, the receiving end can request retransmission of the corrupted segments.
An example of an application that operates at the Transport Layer is HTTP, the protocol used for transmitting web page data over the internet. HTTP relies on TCP to ensure the reliable delivery of web page resources, such as HTML, images, and other media, from a web server to a web browser.
The Transport Layer bridges the gap between the network and the application layer, ensuring that data is transmitted and delivered reliably. It plays a crucial role in supporting various applications and services that depend on efficient and error-free data transmission.
Layer 5: Session Layer
The Session Layer is the fifth layer of the OSI model, responsible for establishing, managing, and terminating communication sessions between applications running on different hosts. It provides synchronization and control mechanisms that allow multiple applications to exchange data and maintain ongoing sessions.
The Session Layer is responsible for establishing a dialogue or session between two communicating applications. It creates a logical connection, known as a session, and ensures that both ends of the session are aware of each other’s status and can synchronize their communication.
This layer manages session checkpoints, which are points within a session that allow for easy recovery in case of failure or interruption. Session checkpoints enable applications to restart sessions from a known state, ensuring the continuity of communication and preventing data loss.
Another important function of the Session Layer is managing session control. It enables the initiation, maintenance, and termination of sessions between applications. It handles tasks such as session establishment, authentication, and authorization. This layer also manages session parameters, such as time-outs and synchronization points, to ensure smooth and reliable communication.
The Session Layer provides services that allow applications on different hosts to establish and control their communication sessions. These services may include establishing checkpoints, managing session tokens or handles, and implementing session encryption and security mechanisms.
Furthermore, the Session Layer also handles session termination, ensuring that sessions are properly closed when the communication between applications is complete. It releases any resources associated with the session and ensures that both ends of the session are notified of its termination.
Despite the Session Layer’s importance in the OSI model, it is worth noting that it is often combined with the Presentation Layer (Layer 6) or integrated into the Application Layer (Layer 7) in many networking implementations.
An example of a protocol that operates at the Session Layer is the Remote Procedure Call (RPC), which allows a program running on one host to execute procedures on a remote host over a network. RPC relies on the Session Layer to establish a session between the client and server applications, enabling them to communicate and exchange data.
The Session Layer plays a vital role in managing the communication sessions between applications. It ensures the synchronization, control, and termination of sessions, enhancing the reliability and performance of communication between hosts.
Layer 6: Presentation Layer
The Presentation Layer is the sixth layer of the OSI model. It is responsible for data representation and encryption, ensuring that data exchanged between applications is compatible, secure, and meaningful.
The Presentation Layer’s main function is to translate data received from the Application Layer into a format that can be understood by the receiving application. It handles data formatting, compression, and encryption, as well as code conversion between different character sets or data formats.
Data compression is a key aspect of the Presentation Layer. It reduces the size of data to optimize transmission efficiency and reduce bandwidth usage. Compression techniques like run-length encoding, Huffman coding, and Lempel-Ziv-Welch (LZW) are commonly used to compress data at this layer.
The Presentation Layer also handles data encryption and decryption, ensuring the confidentiality and integrity of data exchanged between applications. It can encrypt data to protect it from unauthorized access during transmission or storage. Common encryption algorithms like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are utilized at this layer.
In addition to data formatting, compression, and encryption, the Presentation Layer also handles the translation of data between different character sets or data formats. It ensures that the data received by the receiving application is in a format that it can interpret and process correctly. Examples include converting text between ASCII, Unicode, and UTF-8 encoding schemes.
The Presentation Layer also provides services for data integrity checks, ensuring that data received from the network is not corrupted or tampered with. It can use techniques like checksums or cyclic redundancy checks (CRC) to detect errors in the received data and request retransmission if necessary.
Although the Presentation Layer is specified in the OSI model, its functionalities are often combined with other layers, particularly with the Application Layer (Layer 7). In many network implementations, the Presentation Layer functionality is embedded within the application or handled by the operating system.
Examples of protocols and formats that relate to the Presentation Layer include JPEG (Joint Photographic Experts Group) for image compression, HTML (Hypertext Markup Language) for web page formatting, and SSL/TLS (Secure Sockets Layer/Transport Layer Security) for secure data encryption.
The Presentation Layer ensures that data exchanged between applications is properly translated, formatted, compressed, and encrypted. It plays a significant role in guaranteeing the compatibility, security, and overall integrity of data during communication.
Layer 7: Application Layer
Layer 7, the Application Layer, is the topmost layer of the OSI model. It is the layer that interacts directly with the end-user applications and provides services and protocols for accessing network resources and services.
The Application Layer enables user applications to communicate with the network and other applications across different hosts. It includes a wide range of protocols and services that support various functions required by applications, such as file transfer, email services, web browsing, remote access, and more.
Applications at this layer interact with the underlying layers to establish communication sessions, exchange data, and perform actions over the network. They rely on the lower layers to handle the transmission and delivery of data packets.
The protocols operating at the Application Layer define the syntax and semantics of the data exchanged by applications. They determine how the data should be packaged, addressed, and processed. Some commonly used protocols at this layer include HTTP (Hypertext Transfer Protocol) for web browsing, FTP (File Transfer Protocol) for file transfer, SMTP (Simple Mail Transfer Protocol) for email communication, and DNS (Domain Name System) for domain name resolution.
Applications at the Application Layer may have user interfaces that allow users to interact with the network. This can include graphical user interfaces (GUIs), command-line interfaces (CLIs), or even APIs (Application Programming Interfaces) for programmatic access.
The Application Layer also provides services for security and authentication, allowing applications to authenticate users, encrypt data, and establish secure connections over the network. SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a widely used protocol for secure data transmission over the internet at this layer.
Furthermore, the Application Layer is responsible for handling requests and providing responses to the lower-layer protocols, ensuring the smooth operation of the network. It interacts with the Presentation Layer (Layer 6) to format and present data received from the lower layers.
Examples of application layer software include web browsers, email clients, instant messaging applications, and video conferencing applications. These applications use specific protocols to communicate with servers or other client applications, allowing users to access various network services and resources.
Overall, the Application Layer serves as the interface between the user applications and the underlying layers of the OSI model. It provides the necessary protocols, services, and functionalities to enable efficient and secure communication between applications over the network.
Firewall Placement in the OSI Model
A firewall is a network security device that safeguards a network by monitoring and controlling incoming and outgoing network traffic. It acts as a barrier between an internal network and the external internet, preventing unauthorized access and protecting against potential security threats. The placement of a firewall within the OSI model depends on the function and capabilities of the firewall itself.
Traditionally, firewalls have been positioned at the network layer (Layer 3) of the OSI model. Network-layer firewalls examine packet headers, IP addresses, and port numbers to make decisions about allowing or blocking traffic. They enforce security policies based on network-specific rules and can control traffic based on source and destination IP addresses, specific protocols, or port numbers.
Firewalls at the network layer can effectively filter and secure traffic, but they may lack visibility into the content of packets beyond the network and transport layer headers. This limitation can make it challenging to detect certain types of attacks or to filter based on application-specific characteristics or content.
Modern firewalls, often referred to as next-generation firewalls (NGFWs), have advanced capabilities that enable them to operate at higher layers of the OSI model. NGFWs have the ability to filter traffic based on application-layer data, inspecting packet payloads and performing deep packet inspection (DPI).
By residing at the application layer (Layer 7), NGFWs can identify and control traffic based on specific applications or protocols. This enables more granular and context-aware filtering, allowing organizations to set policies based on the specific needs of their applications and better protect against application-layer attacks and vulnerabilities.
NGFWs can also offer additional security features such as intrusion prevention system (IPS) functionality, antivirus scanning, web filtering, and URL filtering. These capabilities further strengthen the security posture of the network by providing multiple layers of protection against various types of threats.
It is important to note that the placement of a firewall within the OSI model may vary based on the specific implementation and deployment scenario. Some firewalls may focus solely on network-layer protection, while others may include application-layer inspection and filtering capabilities.
In addition to their placement within the OSI model, firewalls can also be positioned within the TCP/IP model layers. The TCP/IP model’s network layer aligns with the OSI model’s network and data link layers, while the transport layer aligns with the OSI model’s transport layer. Firewalls can be placed in these respective layers to provide network and transport layer security.
Ultimately, the placement of a firewall within the OSI model or the TCP/IP model depends on the organization’s security requirements, the desired level of filtering granularity, and the specific capabilities of the firewall solution being deployed.
Comparison: Firewall Placement in TCP/IP Model vs OSI Model
Firewalls play a crucial role in network security by monitoring and controlling network traffic. While the OSI (Open Systems Interconnection) model and the TCP/IP model serve as frameworks for understanding network protocols, they have different levels of granularity in terms of where firewalls can be placed within their respective layers.
In the OSI model, firewalls are typically placed at the network layer (Layer 3). They examine packet headers, IP addresses, and port numbers to make decisions about allowing or blocking traffic. By operating at the network layer, firewalls can enforce security policies based on network-specific rules and control traffic based on source and destination IP addresses, protocols, or port numbers.
On the other hand, the TCP/IP model, which is often considered a simplified version of the OSI model, does not have a separate layer dedicated to network-layer functionality. Instead, the TCP/IP model combines the functions of the OSI model’s network layer and data link layer into one layer called the internet layer. Firewalls can be placed within this combined layer, allowing them to filter and secure traffic using IP addresses, protocols, and port numbers.
While both models provide a layer for firewall placement, the OSI model offers a more granular approach. It includes distinct layers for the physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and application layer. Firewalls in the OSI model can be positioned at any layer depending on the specific functionality and capabilities required, providing more flexibility in terms of where and how they operate within the network stack.
The TCP/IP model, in contrast, is more streamlined, with fewer layers. This simplicity can make firewall deployment and configuration easier, as there are fewer layers to consider. However, it also means that firewalls may have less granularity in terms of the types of filtering and security controls they can provide.
Furthermore, the OSI model allows for the placement of firewalls at the application layer (Layer 7). This enables next-generation firewalls (NGFWs) to perform deep packet inspection, filtering based on application-level data, and protection against application-layer vulnerabilities and attacks. NGFWs are able to provide more context-aware and granular filtering, enhancing network security at a higher layer of the OSI model.
In comparison, the TCP/IP model does not explicitly define a dedicated layer for application-level functionality. Therefore, firewalls in the TCP/IP model are generally limited to operating at the lower layers, such as the internet layer or transport layer, focusing primarily on network and transport layer security.