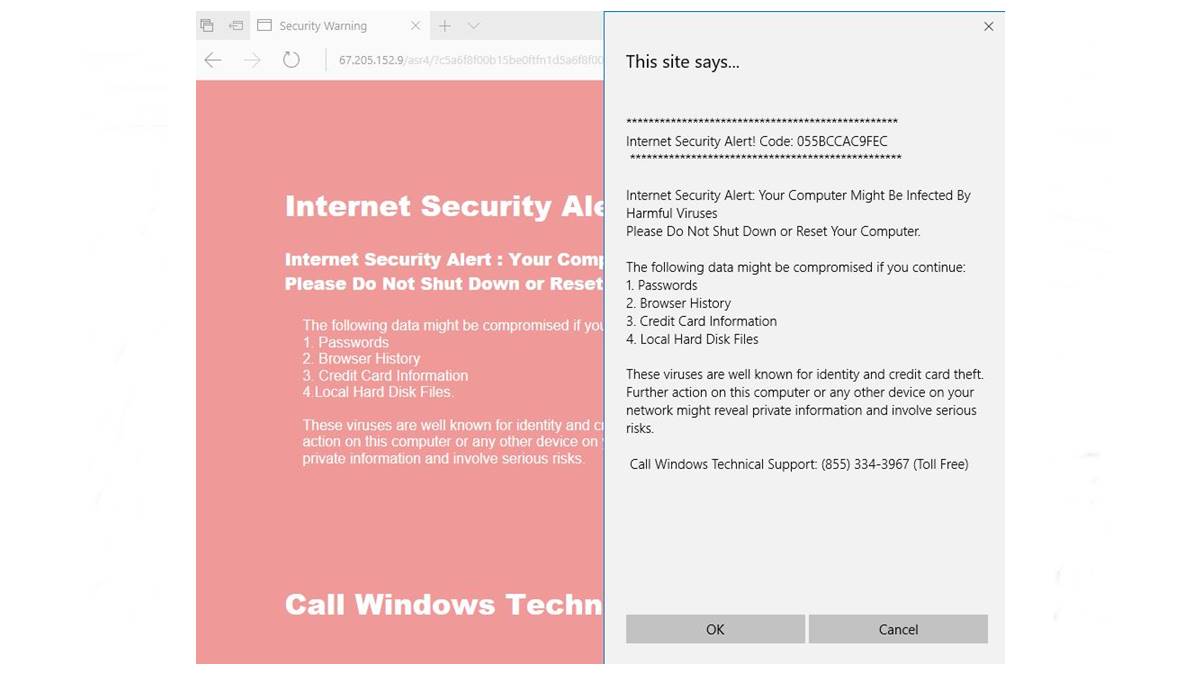
Common Internet Security Alerts
As technology advances, so do the risks associated with using the internet. Cybercriminals are constantly finding new ways to exploit vulnerabilities and gain unauthorized access to sensitive information. This has led to an increase in internet security alerts, which aim to warn users about potential threats and breaches. Understanding and responding to these alerts is crucial in maintaining a secure online presence. Here are some of the most common internet security alerts you may encounter:
- Malware Detection: This alert indicates that malicious software, such as viruses, spyware, or adware, has been detected on your device. It’s important to take immediate action to remove or quarantine the malware and prevent any further damage to your system.
- Phishing Attempts: Phishing is a deceptive technique used by cybercriminals to trick individuals into revealing sensitive information, such as passwords or credit card details. Phishing alerts warn you about suspicious emails, websites, or messages that could be attempting to steal your personal data. Be cautious and avoid clicking on any suspicious links or providing sensitive information.
- Unauthorized Access: This alert notifies you when someone attempts to gain unauthorized access to your accounts or devices. It could indicate a brute-force attack on your passwords or a suspicious login from an unfamiliar location. Change your passwords immediately and enable two-factor authentication for added security.
- Network Intrusion: If you receive an alert about a network intrusion or an attempted breach, it means that someone is trying to break into your network or compromise your Wi-Fi security. Take steps to strengthen your network security, such as updating your router firmware and enabling encryption.
- Data Breach Notifications: Companies or online services may send breach notifications if they have experienced a security breach that could have exposed your personal data. Take these alerts seriously and follow any recommended actions, such as changing passwords or monitoring your accounts for suspicious activity.
Other common internet security alerts include reports of suspicious or malicious websites, firewall violations, and malware-infected downloads. It is essential to be aware of these alerts and respond promptly to mitigate potential risks. Remember, prevention is always better than cure when it comes to internet security.
Stay Calm and Assess the Situation
Receiving an internet security alert can be alarming, but it’s important to stay calm and assess the situation objectively. Panicking or acting impulsively can lead to further complications. Here are some steps to follow when you receive an internet security alert:
- Pause and Take a Deep Breath: Take a moment to collect yourself and avoid making hasty decisions. Panic can cloud your judgment and result in taking unnecessary risks or falling for scams.
- Read the Alert Carefully: Carefully read through the entire alert message and ensure you understand its contents. Pay close attention to any specific instructions or recommended actions provided.
- Confirm the Source of the Alert: Verify that the alert is legitimate and not a phishing attempt or a false alarm. Cross-reference the details in the alert with information from reputable sources or security software installed on your device.
- Evaluate the Severity of the Threat: Assess the potential impact and severity of the threat mentioned in the alert. Determine if it’s a minor issue that can be easily resolved or a more serious security concern that requires immediate action.
- Gather Additional Information: Conduct further research to gather more information about the specific threat or vulnerability mentioned in the alert. Visit trusted sources, such as security forums or official websites of the software or service involved.
- Consider the Source’s Reputation: Take into account the reputation and credibility of the source that issued the alert. Only trust alerts from reputable security organizations, software vendors, or your trusted internet service provider (ISP).
- Assess the Potential Impact: Evaluate the potential impact of the threat on your personal information, financial data, or online accounts. Consider the sensitivity of the data that could be compromised and the potential consequences if it falls into the wrong hands.
- Consult with Experts: If you’re unsure about how to interpret or handle the security alert, seek advice from cybersecurity experts or IT professionals. They can provide guidance and help you make informed decisions.
By staying calm and assessing the situation, you can better understand the nature of the internet security alert and take appropriate actions to protect yourself and your online presence.
Verify the Source of the Alert
When you receive an internet security alert, it’s crucial to verify the source to ensure its legitimacy. Unfortunately, cybercriminals often use deceptive tactics to trick users into falling for scams or disclosing sensitive information. Here are steps to help you verify the source of the alert:
- Check for Official Communication: If the alert claims to be from a specific company or organization, visit their official website or contact their customer support directly to confirm the authenticity of the alert. Avoid clicking on any links provided in the alert itself.
- Verify Sender Information: Carefully examine the email address, domain, or phone number associated with the alert. Cybercriminals often use spoofed or slightly altered addresses to make their messages appear legitimate. Look for any unusual or suspicious elements.
- Research the Sender: Conduct a quick online search to gather information about the sender or the organization mentioned in the alert. Look for reviews, news articles, or user experiences that can provide insights into their reputation and credibility.
- Compare with Known Contacts: If the alert claims to be from someone you know or a service you use, compare the information and tone of the alert with previous communication from that source. Look for inconsistencies or signs of a phishing attempt.
- Trust Reputable Sources: Rely on reputable security software, internet service providers (ISPs), or cybersecurity organizations for alerts. These sources have established credibility and employ robust methods to detect and notify users of potential threats.
- Examine URL and Webpage: If the alert directs you to a website, inspect the URL carefully. Look for secure connections (https://) and ensure that the website has a professional design and legitimate branding. Be cautious if the website requests confidential information.
- Beware of Urgency or Threats: Cybercriminals often use urgency or threats to manipulate users into taking immediate action without proper verification. Be skeptical of alerts that create a sense of urgency or pressure you to provide personal information quickly.
- Consult with Experts: If you are still unsure about the legitimacy of the alert, consult with cybersecurity experts or IT professionals. They can review the alert and provide valuable insights to help you make an informed decision.
Verifying the source of the alert is crucial to avoid falling victim to scams or divulging sensitive information to malicious actors. Take the time to conduct thorough checks and rely on trusted sources before taking any further action based on the alert.
Understand the Type of Threat
When you receive an internet security alert, it’s essential to understand the type of threat you’re dealing with. Different types of threats require different responses and precautions. Here are some key steps to help you understand the nature of the threat:
- Read the Alert Details: Carefully read the alert to identify the specific type of threat mentioned. Common threats include malware infections, phishing attempts, brute-force attacks, network intrusions, or data breaches. Understanding the specific threat will help you determine the appropriate actions.
- Research the Threat: Conduct additional research on the identified threat to gather more information. Study the methods and techniques used by cybercriminals for that particular threat. This knowledge will help you better prepare yourself and take necessary precautions.
- Identify Potential Risks: Assess the potential risks associated with the identified threat. Determine the impact it could have on your personal information, financial data, or online accounts. Understanding the risks will emphasize the importance of taking prompt action.
- Consider Severity and Reach: Evaluate the severity and reach of the threat. Determine if it’s a widespread issue affecting many users or a targeted attack specifically aimed at you. This information will help you gauge the level of urgency in responding to the threat.
- Consult with Experts: If you’re unsure about the nature of the threat or need guidance, consult with cybersecurity experts or IT professionals. They can provide insights into the specific threat, its potential consequences, and the recommended steps to mitigate the risks.
- Educate Yourself: Take the initiative to educate yourself about common internet security threats and their characteristics. Stay updated with evolving trends in cybersecurity to better recognize and understand the threats you may encounter in the future.
- Follow Trusted Sources for Information: Rely on reputable sources, such as cybersecurity blogs, official software vendors, or security forums, to stay informed about the latest threats and vulnerabilities. Avoid relying solely on the information provided in the alert itself.
- Stay Updated: Security threats evolve rapidly, with new techniques and vulnerabilities emerging regularly. Stay updated with security patches and updates for your operating system, antivirus software, and other applications to protect yourself against the latest threats.
Understanding the type of threat you’re facing is crucial in formulating an effective response. By familiarizing yourself with the nature of the threat and its potential risks, you can take the necessary steps to safeguard your online presence and mitigate potential damages.
Take Immediate Action
When you receive an internet security alert, taking immediate action is critical to mitigate the potential risks and protect your online presence. Delaying or ignoring the alert can lead to further security breaches and compromises. Here are the essential actions to take when faced with an internet security alert:
- Isolate Infected Devices: If the alert indicates a malware infection or unauthorized access, disconnect the affected device from the internet or your network. This prevents the spread of malware and limits further damage to your system and data.
- Follow Alert Instructions: Carefully follow any instructions provided in the alert regarding actions to take to address the security threat. This may include downloading specific security patches, running antivirus scans, or changing passwords.
- Update Security Software: Ensure that your antivirus software, firewall, and other security tools are up to date. Regularly check for updates and install them promptly to incorporate the latest security patches and maintain the highest level of protection.
- Scan for Malware: Run a full system scan using your antivirus software to detect and remove any malware or malicious files. Quarantine or delete any identified threats to prevent further damage to your system and data.
- Change Compromised Passwords: If the alert notifies you of compromised passwords or accounts, change those passwords immediately. Create strong, unique passwords using a combination of letters, numbers, and special characters to enhance security.
- Enable Two-Factor Authentication: Strengthen the security of your accounts by enabling two-factor authentication (2FA). This adds an extra layer of protection by requiring a verification code in addition to your password when logging in.
- Monitor Financial Activity: If the alert involves potential financial fraud or credit card breaches, monitor your financial accounts and transactions closely. Contact your financial institutions to report any suspicious activity and take appropriate actions to protect your finances.
- Backup Important Data: Regularly backup your important files and data to an external hard drive, cloud storage, or another secure location. In case of a security breach or system failure, you can restore your data and minimize the impact on your productivity and personal information.
- Report Phishing Attempts: If the alert involves a phishing attempt or suspicious communication, report it to the appropriate authorities, such as your email provider or the Anti-Phishing Working Group (APWG). This helps protect others from falling victim to similar scams.
- Update Privacy Settings: Review and update the privacy settings on your online accounts, social media profiles, and other platforms. Restricting the amount of personal information visible to the public reduces the risk of identity theft and targeted attacks.
Taking immediate action when faced with an internet security alert is crucial in minimizing the impact of potential threats. By following the recommended steps and promptly addressing the security issues raised in the alert, you can enhance your online security and protect your sensitive information.
Update All Software and Operating Systems
Keeping your software and operating systems up to date is crucial for maintaining a secure online presence and protecting yourself from potential security vulnerabilities. When you receive an internet security alert, one important action you should take is to update all relevant software and operating systems. Here’s why:
- Patch Security Vulnerabilities: Software updates often include security patches that address known vulnerabilities. These vulnerabilities could potentially be exploited by cybercriminals to gain unauthorized access to your system or compromise your data. By regularly updating your software, you ensure that these vulnerabilities are patched, strengthening your overall security.
- Fix Software Bugs: Updates not only address security vulnerabilities but also fix software bugs and glitches. These bugs can sometimes be exploited by attackers to gain control over your system or cause it to malfunction. By keeping your software up to date, you minimize the risk of encountering such issues.
- Enhance Performance and Functionality: Software updates often introduce new features, improve performance, and enhance the overall functionality of the applications you use. By staying updated, you can take advantage of these improvements, ensuring a smoother and more secure experience when using your software.
- Address Compatibility Issues: Updating your software and operating systems helps ensure compatibility with the latest technologies and standards. This is especially important as new security measures and encryption protocols are introduced. By having the latest updates, you can maintain compatibility and ensure a seamless and secure online experience.
- Protect Against Exploits: Cybercriminals often target outdated software and operating systems that have known vulnerabilities. These vulnerabilities can be easily exploited to gain unauthorized access or launch attacks. By regularly updating your software, you decrease the chances of falling victim to such exploits.
- Automate Updates: Many software applications and operating systems provide the option to automate updates. By enabling this feature, you ensure that your software is always up to date without having to manually check for updates. This reduces the likelihood of missing crucial security patches.
- Enable Automatic Security Updates: Some operating systems offer automatic security updates as a built-in feature. Enabling this feature ensures that security patches are applied as soon as they become available, providing continuous protection against emerging threats.
- Regularly Check for Updates: Even if automatic updates are enabled, it’s still a good practice to manually check for updates regularly, especially for software that may not have an automatic update feature. This ensures that you don’t miss any critical updates that could address security vulnerabilities.
- Consider End-of-Life Software: If your software or operating system has reached its end-of-life (EOL) and is no longer supported by the vendor, it’s crucial to replace it with a supported version or alternative. Unsupported software becomes more vulnerable to security threats as it no longer receives updates or patches.
Regularly updating your software and operating systems is a fundamental step in maintaining a secure online environment. By staying up to date, you ensure that your software is equipped with the latest security measures, bug fixes, and performance enhancements, reducing the risk of security breaches and keeping your data safe.
Run a Full System Scan
When you receive an internet security alert, it’s important to run a full system scan on your devices. This thorough scan helps to identify any potential malware infections or security vulnerabilities that may be present on your system. Here’s why running a full system scan is crucial:
- Detect Malware and Suspicious Files: A full system scan thoroughly examines all files and programs on your device, searching for any signs of malware or suspicious activities. It helps to identify and remove any existing infections that could compromise your security and privacy.
- Ensure Comprehensive Protection: While real-time antivirus software can provide ongoing protection, running a full system scan offers a comprehensive analysis of your entire device. This ensures that no traces of malware or potential threats are left undetected.
- Identify Hidden Threats: Some malware can hide and evade detection by traditional security measures. Running a full system scan increases the chances of identifying these hidden threats and allows you to take appropriate actions to remove or quarantine them.
- Prevent System Performance Issues: Malware infections can cause system slowdowns, crashes, and other performance issues. By running a full system scan, you can identify and remove any malware or unwanted programs that may be impacting your device’s performance.
- Scan for Potentially Unwanted Programs: Full system scans also help identify potentially unwanted programs (PUPs) or adware that may have been inadvertently installed on your device. These programs can compromise your privacy and provide avenues for further malware infections.
- Discover Hidden Security Vulnerabilities: In addition to malware detection, a full system scan can uncover security vulnerabilities in your operating system, applications, or network configurations. Identifying these vulnerabilities allows you to address and patch them, reducing the risk of future security breaches.
- Perform Regular Maintenance: Running a full system scan is a form of routine maintenance that helps ensure your device is in optimal condition. It allows you to clean up unnecessary files, remove temporary data, and detect any potential issues that may impact your device’s performance and security.
- Assess Overall Security Health: By running a full system scan, you can assess the overall security health of your device. It provides valuable insights into the current state of your security measures, allowing you to make necessary adjustments and strengthen your defenses if needed.
Running a full system scan should be a regular part of your cybersecurity routine. It helps detect and remove any existing threats, guarantees comprehensive protection, and safeguards your device and data from potential security risks.
Change Your Passwords
When you receive an internet security alert, one crucial action you should take is to change your passwords. Strong and unique passwords are a fundamental defense against unauthorized access to your accounts and sensitive information. Here’s why changing your passwords is vital:
- Mitigate Potential Compromise: Changing your passwords helps mitigate the risk of unauthorized access to your accounts or personal information. If you receive an alert indicating a security breach or potential password compromise, changing your password immediately is essential to protect yourself.
- Prevent Credential Exploitation: Cybercriminals often acquire credentials through data breaches or phishing attempts. By changing your passwords regularly, even if you haven’t received a specific alert, you reduce the likelihood of unauthorized individuals exploiting stolen credentials to gain access to your accounts.
- Enable Stronger Protection: Changing your passwords presents an opportunity to create stronger, more secure passwords. Incorporate a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information, such as birthdays or common words.
- Avoid Password Reuse: Reusing passwords across multiple accounts poses a significant security risk. If one account is compromised, it puts all your other accounts at risk. Changing passwords regularly helps break the pattern of password reuse and strengthens your overall security posture.
- Implement Two-Factor Authentication (2FA): Changing passwords is a good time to enable two-factor authentication (2FA) whenever possible. 2FA requires an additional verification step, such as a temporary code sent to your mobile device, which adds an extra layer of security to your accounts.
- Protect Financial and Personal Information: Your passwords provide a line of defense for your financial and personal information. Regularly changing them helps ensure that your accounts remain secure, making it more difficult for cybercriminals to gain access to sensitive data or make unauthorized transactions.
- Stay Ahead of Potential Threats: Cyber threats are constantly evolving. Changing your passwords regularly helps stay ahead of potential threats, making it harder for attackers to exploit passwords that may have become easier to crack due to technological advancements in hacking tools.
- Enhance Overall Security: Changing passwords should be part of your overall security hygiene. It’s a proactive measure that contributes to your overall security posture and helps reduce the risk of becoming a victim of cybercrime.
Remember, changing passwords regularly is an important step in protecting your accounts and personal information. Ensure you create strong, unique passwords for each account and consider implementing additional security measures, such as 2FA, to enhance your online security.
Enable Two-Factor Authentication
Two-Factor Authentication (2FA) is a powerful security measure that provides an additional layer of protection to your online accounts. When you receive an internet security alert, enabling 2FA is an important step you should take to enhance your account security. Here’s why enabling 2FA is crucial:
- Added Layer of Verification: 2FA requires users to provide an additional piece of information to verify their identity when logging into an account. This can be a temporary code sent via SMS, a biometric scan, or a hardware token. It adds an extra layer of protection, making it harder for attackers to gain unauthorized access to your accounts.
- Protects Against Stolen Credentials: Even if your username and password are compromised due to a security breach or a phishing attempt, 2FA provides an extra level of security. Attackers would still need the second factor of authentication (such as a unique code on your mobile device) to gain access to your account.
- Effective Against Brute-Force Attacks: Brute-force attacks involve automated tools that systematically guess passwords. Enabling 2FA mitigates the risk of such attacks, as even if the attacker manages to guess your password, they would still need the second factor of authentication to gain access to your account.
- Increases Account Security: By enabling 2FA, you significantly enhance the security of your online accounts. This security measure adds an extra barrier that must be overcome to gain access to your sensitive information, reducing the risk of unauthorized access and potential data breaches.
- Protects Against Phishing Attacks: 2FA renders phishing attacks less effective. Even if you unintentionally provide your username and password to a phishing site, the attackers would still be unable to access your account without the second factor of authentication, preventing them from compromising your account.
- Offers Flexibility in Authentication Methods: 2FA supports a variety of authentication methods, such as SMS codes, email verification, authenticator apps, or hardware tokens. This allows you to choose a method that is convenient for you, ensuring a seamless and secure authentication process.
- Compatible with Multiple Online Services: Many popular online services, such as email providers, social media platforms, and financial institutions, offer 2FA as an option. Enabling 2FA across multiple accounts provides a blanket of protection for your online presence, safeguarding your valuable information across various platforms.
- Easy to Set Up: Setting up 2FA is generally a straightforward process. Most online services provide step-by-step instructions to guide you through the setup, including linking your account with a mobile device or authenticator app. Once enabled, the additional step during login becomes a routine part of accessing your accounts.
Enabling Two-Factor Authentication is an effective way to fortify your account security and protect your sensitive information. By implementing this additional layer of verification, you significantly reduce the risk of unauthorized access and enhance your overall online security.
Contact Your Internet Service Provider (ISP)
When you receive an internet security alert, reaching out to your Internet Service Provider (ISP) is an important step to take. Your ISP can provide valuable assistance and guidance in addressing the security issue at hand. Here’s why contacting your ISP is crucial:
- Reporting Potential Network Issues: If you receive an alert indicating a network intrusion or suspicious activity on your network, your ISP needs to be informed. They can investigate the issue from their end and take appropriate action to safeguard your network and connection.
- Verifying Legitimacy of the Alert: Contacting your ISP allows you to verify the legitimacy of the security alert you received. They can confirm if the alert is genuine and provide additional information about any known security issues or ongoing threats in your area.
- Seeking Technical Assistance: ISPs often have dedicated technical support teams that can assist you in addressing the security issue. They can guide you through the necessary steps to secure your connection, troubleshoot any network-related problems, or provide recommendations for additional security measures.
- Receiving Updates and Alerts: Your ISP may send out updates, alerts, or advisories regarding security threats or network maintenance. By staying in touch with your ISP, you can stay informed about potential risks and take preventive measures to protect yourself.
- Investigating Connectivity Issues: If you encounter repeated security alerts or experience connectivity issues, your ISP can help investigate the cause. They can check for any unusual network activity or troubleshoot any technical problems that may be impacting your internet security.
- Addressing Unauthorized Access or Account Compromises: If the security alert relates to unauthorized access to your ISP account or compromised credentials, contacting your ISP is vital. They can help you regain control of your account, reset passwords, and implement additional security measures.
- Understanding Security Measures: Your ISP can provide information and resources to help you understand the security measures they have in place to protect your connection. This knowledge can empower you to take proactive steps and make informed decisions to enhance your online security.
- Receiving Compliance or Policy Updates: ISPs may periodically update their security policies or compliance requirements. Contacting your ISP allows you to stay informed about any changes and ensure that you are in compliance with their security guidelines.
Contacting your Internet Service Provider is an important step in addressing internet security issues. They can provide technical assistance, verify the legitimacy of security alerts, and offer guidance on securing your connection. By establishing a line of communication with your ISP, you can better protect yourself and stay informed about potential risks.
Report the Incident to the Authorities
When you receive an internet security alert, reporting the incident to the appropriate authorities is a crucial step to ensure that the incident is properly documented and investigated. Reporting internet security incidents helps protect not only yourself but also other potential victims. Here’s why reporting the incident to the authorities is essential:
- Support Law Enforcement Efforts: Reporting the incident to the authorities provides valuable information that can aid law enforcement agencies in their efforts to combat cybercrime. By reporting the details of the incident, you help contribute to a broader picture of criminal activities and assist authorities in tracking down and apprehending offenders.
- Document the Incident: Reporting the incident creates an official record and documentation of what has transpired. This record may be useful for future reference, especially if you encounter related incidents or need to provide evidence for legal proceedings or insurance claims.
- Identify Widespread Threats: Authorities rely on public reporting to identify widespread threats and patterns of cybercriminal activities. Reporting your incident can contribute to the collective knowledge and help authorities identify trends, modus operandi, and potential links to other cases.
- Receive Assistance and Guidance: Authorities can provide you with guidance and assistance in understanding the nature of the incident and the steps you should take to protect yourself. They may also provide recommendations on additional security measures or resources that can help you prevent future incidents.
- Protect Other Potential Victims: Reporting the incident allows authorities to take appropriate action to mitigate the threat and protect other potential victims. By sharing your experience, you help raise awareness and provide valuable information that can prevent others from falling victim to similar attacks.
- Contribute to Cybersecurity Research: Incident reports contribute to cybersecurity research and the development of preventive measures. Researchers and cybersecurity professionals analyze reported incidents to better understand emerging threats, identify vulnerabilities, and develop effective countermeasures to enhance overall cybersecurity.
- Support Legal Action: Reporting the incident helps support potential legal action against the perpetrators. Law enforcement agencies rely on reported incidents to gather evidence, build cases against cybercriminals, and bring them to justice.
- Stay Informed about Updates: Reporting the incident may entitle you to updates and notifications from the authorities regarding the progress of the investigation or any developments related to the incident. This enables you to stay informed about the actions being taken and any measures you should take to protect yourself further.
Reporting the incident to the authorities plays a critical role in combating cybercrime, protecting yourself and other potential victims, and contributing to the overall improvement of cybersecurity. By promptly reporting incidents, you can make a meaningful impact in preventing future attacks and ensuring a safer online environment.
Educate Yourself and Stay Informed
In the ever-evolving landscape of internet security, educating yourself and staying informed about the latest threats and best practices is essential to protect yourself effectively. When you receive an internet security alert, it’s important to realize that ongoing education is a crucial step in maintaining your online security. Here’s why educating yourself and staying informed is vital:
- Recognize and Understand Emerging Threats: By staying informed, you can recognize new and emerging threats in the digital landscape. Understanding the latest attack techniques, malware strains, and phishing tactics empowers you to take proactive measures to prevent falling victim to these threats.
- Identify Warning Signs and Red Flags: Education helps you identify warning signs and red flags that indicate a potential security threat. This includes suspicious email attachments, requests for personal information, or unusual website behavior. Knowing what to look for can prevent you from inadvertently exposing yourself to security risks.
- Implement Best Security Practices: Staying informed allows you to implement best security practices across your digital activities. This includes using strong and unique passwords, enabling two-factor authentication, regularly updating software, and backing up data. These practices form the foundation of a robust security posture.
- Understand Privacy and Data Protection: Educating yourself about privacy and data protection enables you to make informed decisions about the information you share online. This knowledge helps you understand the risks associated with data collection, how to protect your personal data, and how to navigate privacy settings on different platforms.
- Stay Up to Date with Security News and Updates: Following security news and updates keeps you informed about the latest breaches, vulnerabilities, and security patches. This knowledge enables you to take immediate action in response to emerging threats and apply necessary security updates to protect yourself.
- Benefit from Expert Advice and Resources: Educating yourself provides access to expert advice and resources from cybersecurity professionals. Online publications, blogs, forums, and webinars are valuable sources of information that can enhance your understanding of security practices and keep you updated on the ever-changing threat landscape.
- Protect Yourself and Those Around You: Education not only benefits you but also allows you to help others stay safe. By imparting your knowledge and raising awareness among friends, family, and colleagues, you contribute to a safer digital environment for everyone.
- Empower Yourself to Make Informed Decisions: Education empowers you to make informed decisions regarding your online activities. It enables you to assess risks, evaluate the security of different platforms or services, and make choices that align with your privacy and security preferences.
Educating yourself and staying informed about internet security is an ongoing process. By being proactive in expanding your knowledge and keeping up with the latest developments, you strengthen your ability to protect yourself, adapt to emerging threats, and maintain a secure online presence.
Take Preventive Measures to Avoid Future Alerts
Receiving internet security alerts can be stressful and disruptive. To minimize the frequency of such alerts and maintain a secure online presence, it’s important to take preventive measures. By proactively implementing security practices and adopting preventive measures, you can reduce the risk of future security incidents. Here are some preventive measures to consider:
- Use Strong and Unique Passwords: Create strong and unique passwords for each of your accounts. Avoid using easily guessable information and consider using a password manager to securely store and generate complex passwords.
- Enable Two-Factor Authentication (2FA): Enable 2FA whenever it is available. This provides an additional layer of security by requiring a second form of verification, such as a temporary code sent to your mobile device, in addition to your password.
- Keep Software and Operating Systems Up to Date: Regularly update your software, apps, and operating systems to ensure you have the latest security patches and bug fixes. Enable automatic updates to streamline this process.
- Be Cautious with Email and Online Communications: Exercise caution when opening email attachments or clicking on links. Avoid responding to unsolicited emails or providing personal information via email. Verify the legitimacy of the sender before taking any action.
- Use Antivirus and Anti-Malware Software: Install reputable antivirus and anti-malware software and keep it up to date. Regularly run scans to detect and remove any potential threats.
- Secure Your Wi-Fi Network: Protect your home Wi-Fi network with a strong password and enable encryption (WPA2 or higher). Regularly update your router firmware to patch any security vulnerabilities.
- Be Mindful of Social Media Privacy Settings: Review and adjust your privacy settings on social media platforms to limit the amount of personal information that is publicly accessible. Be aware of what you share and with whom.
- Stay Informed about the Latest Threats: Keep up to date with the latest security news, trends, and best practices. Follow reputable sources and cybersecurity blogs to stay informed about potential threats and ways to protect yourself.
- Be Wary of Suspicious Websites: Exercise caution when visiting unfamiliar websites or downloading files from untrusted sources. Stick to reputable websites and be mindful of any warnings or security indicators provided by your browser.
- Regularly Back Up Your Data: Regularly back up your important files and data to an external hard drive, cloud storage, or another secure location. This ensures that even if you experience a security incident, you can restore your data without significant losses.
Taking preventive measures is key to reducing the likelihood of future security alerts and protecting yourself from potential threats. By implementing these measures, you can enhance your online security and minimize the risk of falling victim to cybercriminals and malicious activities.