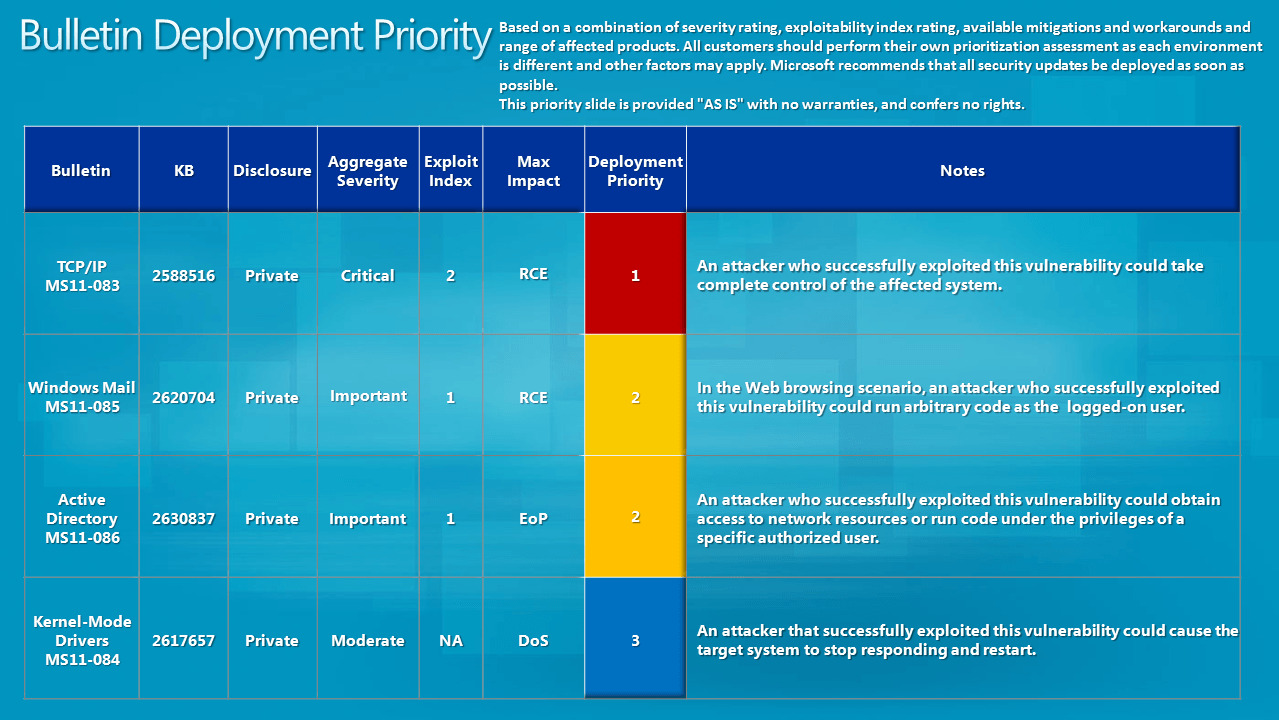
Overview of Microsoft Security Bulletin Severity Rating System
The Microsoft Security Bulletin Severity Rating System is a critical component of Microsoft’s approach to addressing security vulnerabilities in its software and systems. It provides a standardized severity rating for each vulnerability, allowing users and system administrators to understand the level of risk associated with a particular issue.
The purpose of this rating system is to help prioritize and allocate resources for addressing security vulnerabilities. By assigning a severity rating to each vulnerability, Microsoft can provide guidance on the urgency and importance of applying security updates and patches.
With this rating system, Microsoft categorizes vulnerabilities into four different levels: Critical, Important, Moderate, and Low. Each severity level represents a different level of risk and potential impact to systems and users.
The severity ratings are designed to provide a clear indication of the potential damage that could occur if a vulnerability is exploited. They help users and system administrators prioritize their response efforts and apply the necessary security updates in a timely manner.
The severity rating for each vulnerability is determined through a comprehensive assessment of various factors, such as the potential for remote code execution, the level of user interaction required for exploitation, and the potential impact on the confidentiality, integrity, and availability of data and systems.
It’s important to note that the severity rating represents the potential impact of a vulnerability and is not a reflection of its exploitability or the likelihood of it being actively exploited in the wild. Microsoft continually monitors and investigates new vulnerabilities and provides security updates accordingly.
Understanding and staying informed about the Microsoft Security Bulletin Severity Rating System can help users and system administrators make informed decisions when it comes to applying security updates and patches. By prioritizing and addressing vulnerabilities based on their severity, users can minimize the risk of their systems being compromised by malicious actors.
Background and Purpose
The Microsoft Security Bulletin Severity Rating System was introduced by Microsoft to provide a standardized way of assessing and communicating the severity of security vulnerabilities in its products. Prior to the implementation of this rating system, the severity of vulnerabilities was communicated in a less structured and inconsistent manner.
The purpose of the rating system is to help users and system administrators understand the potential impact and severity of a vulnerability and prioritize their response efforts accordingly. By assigning a severity rating, Microsoft aims to provide clarity and guidance on the urgency and importance of applying security updates.
The need for a standardized severity rating system arose from the growing complexity and diversity of software vulnerabilities. With a wide range of products and technologies, each with its own set of vulnerabilities, it became crucial to establish a consistent framework for evaluating and communicating their severity.
By implementing this rating system, Microsoft sought to address the following objectives:
- Consistency: The rating system ensures that vulnerabilities are assessed and communicated in a consistent and standardized manner across all Microsoft products. This helps users and system administrators understand the severity of a vulnerability, regardless of the specific product or technology it affects.
- Transparency: Microsoft aims to be transparent in its communication regarding security vulnerabilities. The severity rating system provides a clear and transparent way of indicating the potential impact and risk associated with a vulnerability, enabling users to make informed decisions about the urgency of applying security updates.
- Prioritization: With the wide range of vulnerabilities that exist, it’s important for users and system administrators to prioritize their response efforts. The severity rating system helps in prioritizing vulnerabilities based on their potential impact, allowing for effective allocation of resources and timely application of security updates.
Overall, the background and purpose of the Microsoft Security Bulletin Severity Rating System is to ensure consistent assessment and communication of the severity of vulnerabilities in Microsoft products. By providing a standardized rating, Microsoft enables users and system administrators to prioritize their actions and apply security updates effectively, minimizing the risk of exploitation and maintaining the security of their systems.
Different Severity Levels
The Microsoft Security Bulletin Severity Rating System assigns vulnerabilities to different severity levels based on the potential impact and risk they pose to systems and users. There are four severity levels: Critical, Important, Moderate, and Low. Each level represents a different level of risk and importance in terms of potential exploitation.
1. Critical Severity Level: Vulnerabilities categorized as Critical are deemed to have a high potential for exploitation and can lead to severe consequences if left unpatched. These vulnerabilities could allow remote code execution, result in data loss or compromise, or enable attackers to gain full control of the system without user interaction. It is crucial to address critical vulnerabilities immediately to prevent widespread security breaches and protect sensitive data.
2. Important Severity Level: Vulnerabilities classified as Important have a lower potential for exploitation compared to critical vulnerabilities. While they may not allow remote code execution without user interaction, they can still have significant consequences if exploited. Important vulnerabilities may compromise the confidentiality, integrity, or availability of data or systems. It is recommended to address important vulnerabilities as soon as possible to prevent potential harm.
3. Moderate Severity Level: Vulnerabilities rated as Moderate have a limited potential for exploitation and usually require significant user interaction or specific conditions to be met. They might pose a threat to the system’s confidentiality, integrity, or availability, but the impact is generally less severe than critical or important vulnerabilities. It is recommended to address moderate vulnerabilities within a reasonable timeframe to minimize the risk of exploitation and maintain system security.
4. Low Severity Level: Vulnerabilities designated as Low have a minimal potential for exploitation and pose a low risk to systems and users. They typically require a high level of user interaction or specific conditions to be met. While the impact of low severity vulnerabilities is generally minimal, it is still advisable to address them during regular maintenance cycles to maintain overall system security.
It is important to note that the severity rating system provides a guideline for prioritizing vulnerabilities based on their potential impact. However, the actual risk and importance may vary depending on the specific environment and factors unique to each system. System administrators should evaluate the severity rating in conjunction with other factors, such as the specific products and technologies in use and the potential impact on critical operations.
Critical Severity Level
The Critical severity level within the Microsoft Security Bulletin Severity Rating System denotes vulnerabilities that have the highest potential for exploitation and pose the most significant risk to systems and users. These vulnerabilities are deemed critical due to the severe consequences they can have if left unaddressed.
When a vulnerability is classified as Critical, it means that it has the potential to allow remote code execution without any user interaction. Attackers can exploit these vulnerabilities to execute malicious code on targeted systems, gain unauthorized access, or compromise sensitive data. Critical vulnerabilities can also lead to system crashes, data loss, or complete takeover of the affected system.
Due to the high potential for exploitation and severe consequences, it is crucial to address Critical vulnerabilities as a matter of utmost urgency. Microsoft typically releases security updates and patches for Critical vulnerabilities as soon as possible to prevent widespread security breaches and minimize the risk of significant data breaches.
System administrators and users should promptly apply the necessary security updates to protect their systems from known vulnerabilities categorized as Critical. It is essential to regularly check for security updates and patches released by Microsoft and ensure they are applied promptly to minimize the risk of attack.
Safeguarding systems against Critical vulnerabilities requires a proactive approach to security. Organizations and individuals are encouraged to adopt standard security practices, such as implementing strong access controls, regularly monitoring for unusual activities, and employing advanced threat protection mechanisms.
Additionally, staying informed about emerging threats and vulnerabilities is crucial. Microsoft provides detailed security bulletins that contain information about Critical vulnerabilities, their potential impact, and the recommended actions to mitigate the risk. It is important to regularly review these bulletins and implement the necessary security measures accordingly.
By addressing Critical vulnerabilities promptly and taking proactive security measures, users and system administrators can significantly reduce the risk of exploitation and protect their systems from malicious actors aiming to exploit these high-risk vulnerabilities.
Important Severity Level
The Important severity level within the Microsoft Security Bulletin Severity Rating System classifies vulnerabilities that have a lower potential for exploitation compared to Critical vulnerabilities. While they may not pose an immediate and severe threat, Important vulnerabilities still hold significant importance and should not be overlooked.
Important vulnerabilities may not allow for remote code execution without user interaction, but they can still have serious implications if left unpatched. They have the potential to compromise the confidentiality, integrity, or availability of data and systems. Exploiting Important vulnerabilities can enable attackers to gain unauthorized access, bypass security controls, or steal sensitive information.
Although the risk associated with Important vulnerabilities may be relatively lower than that of Critical vulnerabilities, it is still crucial to address them in a timely manner. Microsoft regularly releases security updates and patches to address Important vulnerabilities and minimize the potential risk they pose.
System administrators and users should pay attention to Important vulnerabilities and apply the recommended security updates as soon as possible. Failure to address Important vulnerabilities can leave systems exposed to potential attacks, leading to data breaches, system disruption, or unauthorized access.
It is important to note that the impact of Important vulnerabilities may vary depending on the specific environment and the sensitivity of the data at risk. System administrators should consider the nature of their systems, the potential impact of exploitation, and the specific requirements of their organization when prioritizing the patching of Important vulnerabilities.
Staying proactive in terms of security is essential when dealing with vulnerabilities categorized as Important. Regularly monitoring for security updates and patches released by Microsoft, and promptly applying them, can help mitigate the risk associated with these vulnerabilities. Implementing robust security measures, such as strong authentication controls and intrusion detection systems, can also help protect against potential exploitation.
By actively addressing vulnerabilities classified as Important and adopting proactive security measures, organizations and individuals can strengthen the overall security posture of their systems and minimize the risk of exploitation by malicious actors.
Moderate Severity Level
The Moderate severity level within the Microsoft Security Bulletin Severity Rating System reflects vulnerabilities that have a limited potential for exploitation. While they may not pose an immediate and critical risk, it is still important to address them in order to maintain the overall security of systems and prevent potential exploitation.
Moderate vulnerabilities typically require a significant level of user interaction or specific conditions to be met for exploitation. They may allow attackers to gain unauthorized access, compromise data integrity, or disrupt system availability to some extent. Although the impact of moderate vulnerabilities is generally less severe than Critical or Important vulnerabilities, they still warrant attention and action.
While the risk associated with moderate vulnerabilities may be relatively lower, it is still recommended to address them within a reasonable timeframe. Microsoft includes security updates and patches for moderate vulnerabilities in its regular release cycle, aiming to minimize the risk of potential exploitation.
System administrators and users should regularly review the security bulletins provided by Microsoft and take the necessary actions to address moderate vulnerabilities. Applying the recommended security updates and patches can help mitigate the risk of these vulnerabilities being exploited.
It is important to note that the impact of moderate vulnerabilities may vary depending on the specific environment and the criticality of the systems or data involved. System administrators should consider the potential impact of exploitation, the nature of their systems, and any specific compliance requirements when prioritizing the addressing of moderate vulnerabilities.
In addition to applying the necessary security updates and patches, it is recommended to maintain proactive security practices. This includes implementing strong access controls, network monitoring, and intrusion detection systems. Regularly monitoring for potential security threats can help identify any signs of exploitation or unusual activities associated with moderate vulnerabilities.
By promptly addressing moderate vulnerabilities and implementing proactive security measures, organizations and individuals can enhance the overall security of their systems and minimize the risk of potential exploitation by malicious actors.
Low Severity Level
The Low severity level within the Microsoft Security Bulletin Severity Rating System signifies vulnerabilities that have a minimal potential for exploitation and pose a low risk to systems and users. While they may not pose an immediate and significant threat, it is still important to address them as part of regular maintenance and security practices.
Low vulnerabilities typically require a high level of user interaction or specific conditions to be met for exploitation. They may have limited impact on system security, data confidentiality, integrity, or availability. While the risk associated with low vulnerabilities is generally minimal, it is still advisable to address them during regular system maintenance.
Microsoft includes security updates and patches for low vulnerabilities as part of its regular release cycle to ensure overall system security and mitigate potential risk. Even though the impact of low vulnerabilities may be minimal, neglecting them can leave systems open to potential exploitation.
System administrators and users should regularly review the security bulletins provided by Microsoft and consider applying the recommended security updates and patches for low vulnerabilities. While the urgency may be lower compared to higher severity vulnerabilities, maintaining up-to-date software and addressing low vulnerabilities can contribute to a comprehensive security approach.
It is important to note that the impact of low vulnerabilities may vary depending on the specific environment and the criticality of the systems or data involved. System administrators should evaluate the potential impact, along with other factors specific to their organization, when prioritizing the addressing of low vulnerabilities.
In addition to addressing low vulnerabilities through security updates, maintaining proactive security practices is essential to overall system security. This includes measures such as regularly changing passwords, monitoring for suspicious activities, and implementing appropriate access controls.
By addressing low vulnerabilities as part of regular maintenance cycles and implementing proactive security measures, organizations and individuals can ensure a strong security posture and minimize the risk of potential exploitation of low-risk vulnerabilities.
How Severity Ratings are Determined
The determination of severity ratings within the Microsoft Security Bulletin Severity Rating System involves a comprehensive assessment of various factors to evaluate the potential impact and risk associated with a vulnerability. The severity rating reflects the seriousness of the vulnerability and helps users and system administrators prioritize their response efforts.
Microsoft performs in-depth analysis and testing to determine the severity ratings. The process involves evaluating the technical details and understanding the potential consequences if the vulnerability is successfully exploited. Several key factors are taken into consideration when assigning a severity rating:
- Potential for Exploitation: Microsoft assesses the vulnerability’s potential to be exploited by attackers. This includes analyzing whether remote code execution can be achieved and the level of user interaction required for exploitation.
- Impact on Confidentiality, Integrity, and Availability: The potential impact on the confidentiality, integrity, and availability of data and systems is evaluated. This includes considering the potential loss, compromise, or unauthorized access to sensitive information, as well as possible disruption to system operations.
- Scope of Affected Systems: The number and types of systems that are affected by the vulnerability are examined. Vulnerabilities that have a broader impact across various products or technologies are likely to receive a higher severity rating.
- Exploitability in the Wild: Microsoft evaluates whether the vulnerability has been exploited in real-world scenarios. If active exploitation is detected or if there are known public exploits, the severity rating may be elevated to reflect the immediate risk.
These factors, among others, are thoroughly assessed to determine the appropriate severity rating for a vulnerability. The severity rating aligns with the potential impact and risk associated with the vulnerability, allowing users and system administrators to prioritize their actions based on the severity level.
It is important to note that severity ratings are not static and can change based on new information or the evolution of a vulnerability. As new details emerge or as Microsoft gains more understanding of the potential impact, the severity rating may be adjusted accordingly.
Microsoft maintains a continuous process of monitoring, analyzing, and classifying vulnerabilities to enhance the accuracy of the severity ratings. The goal is to ensure that users and system administrators have the most reliable and relevant information to make informed decisions regarding security updates and the protection of their systems.
Factors Considered in Severity Rating
When determining the severity rating within the Microsoft Security Bulletin Severity Rating System, various factors are taken into consideration. These factors help assess the potential impact and risk associated with a vulnerability and contribute to assigning an appropriate severity level. The severity rating aims to provide users and system administrators with a clear indication of the seriousness of the vulnerability. Here are some key factors considered:
- Exploitability: The ease with which an attacker can exploit the vulnerability is an important factor. Vulnerabilities that are easily exploitable, especially remotely, are generally rated higher in terms of severity. The level of complexity required to successfully exploit the vulnerability is assessed, including factors such as user interaction, network proximity, and the need for specific conditions to be met.
- Impact: The potential impact on systems, data, and users is a critical aspect of determining severity. Factors such as the potential loss, disclosure, or unauthorized modification of sensitive information are assessed. Additionally, the impact on system availability, integrity, or functionality is considered. The severity rating reflects the expected consequences if the vulnerability is successfully exploited.
- Scope: The scope of the vulnerability, including the number and types of affected products or services, is taken into account. Vulnerabilities that have a wider reach, affecting a broader range of systems or technologies, may be assigned a higher severity rating due to their potential for widespread impact.
- Known Attacks: The presence of active attacks or known public exploits targeting the vulnerability is a significant factor in assessing severity. If a vulnerability is actively being exploited in the wild or if there are publicly available tools or techniques for exploitation, the severity rating may be increased to reflect the immediate risk.
- Mitigation Measures: The availability of effective mitigation measures, such as workarounds or temporary fixes, can impact the severity rating. If there are readily available measures that significantly reduce the risk or consequences of exploitation, the severity rating may be lowered.
- Industry Impact: Vulnerabilities that have a potential impact on critical infrastructure, key industries, or widespread user base may be given an increased severity rating. Considerations are made to ensure that vulnerabilities with significant implications for national security, public safety, or economic stability are appropriately addressed and prioritized.
These factors, along with others specific to each vulnerability, are carefully evaluated to determine the severity rating. Microsoft employs a thorough assessment process that combines technical analysis, real-world data, and expert judgment to ensure the accuracy and reliability of the severity ratings.
By considering these factors, the severity rating system provides users and system administrators with a standardized framework to prioritize their response efforts, allocate resources effectively, and address vulnerabilities that pose the highest potential risk to systems and users.
Impact on Users and Systems
Vulnerabilities categorized within the Microsoft Security Bulletin Severity Rating System can have varying degrees of impact on users and systems. The severity rating assigned to a vulnerability provides an indication of the potential consequences if the vulnerability is successfully exploited. Understanding the impact is crucial for users and system administrators to gauge the urgency and importance of addressing the vulnerability. Here are some key aspects of the impact vulnerabilities can have:
- Data Breach: Exploiting a vulnerability can lead to unauthorized access, disclosure, or compromise of sensitive data. This can result in a significant impact on user privacy, corporate secrets, or other confidential information. Data breaches can have far-reaching consequences, including financial losses, regulatory penalties, damage to reputation, and loss of customer trust.
- System Compromise: Vulnerabilities that allow remote code execution or unauthorized access can lead to complete system compromise. Attackers may gain control of affected systems, enabling them to install malicious software, steal information, or carry out further attacks. System compromise can result in disruption of operations, loss of productivity, and potential damage to critical infrastructure.
- Service Disruption: Some vulnerabilities can cause service disruptions, leading to downtime and impacting the availability of systems and services. Exploitation can result in system crashes, application failures, or denial-of-service attacks. Service disruptions can lead to financial losses, customer frustration, and reputational damage.
- Financial Loss: Exploitation of vulnerabilities may lead to financial losses through various means, such as financial fraud, theft of sensitive information, or unauthorized access to financial systems. Additionally, the cost of remediation, incident response, and legal consequences can significantly impact an organization’s finances.
- Regulatory Compliance: Vulnerabilities that expose sensitive data can result in non-compliance with industry regulations or legal requirements. This can lead to legal penalties, reputational damage, and loss of business opportunities. Compliance obligations should be considered when assessing the impact of vulnerabilities.
- User Safety and Privacy: Vulnerabilities affecting user-facing systems can jeopardize user safety, privacy, and trust. For example, vulnerabilities in internet-connected devices or software may allow unauthorized access, surveillance, or manipulation of personal information. User safety and privacy are critical considerations when evaluating the impact of vulnerabilities.
It is important to recognize that the impact of a vulnerability may vary depending on the specific environment, industry, and the value of the assets being protected. System administrators must consider these factors when evaluating the potential consequences and prioritizing the addressing of vulnerabilities.
Understanding the potential impact on users and systems assists in making informed decisions when it comes to applying security updates, implementing protective measures, and allocating resources effectively. By prioritizing vulnerabilities based on their severity and impact, organizations and individuals can minimize the risk of exploitation and maintain the security and integrity of their systems.
Vulnerabilities Addressed by Each Severity Level
The Microsoft Security Bulletin Severity Rating System categorizes vulnerabilities into different severity levels: Critical, Important, Moderate, and Low. Each severity level encompasses vulnerabilities with varying degrees of potential risk and impact. Understanding the vulnerabilities addressed by each severity level helps users and system administrators prioritize their response efforts effectively. Here is an overview of the vulnerabilities addressed by each severity level:
- Critical Severity Level: Critical vulnerabilities are the most severe and potentially impactful. They often allow remote code execution without user interaction and can lead to system compromise, data loss, or unauthorized access. Exploiting critical vulnerabilities can result in significant damage to systems, sensitive information, and user privacy. It is crucial to promptly address critical vulnerabilities to minimize the risk of widespread security breaches.
- Important Severity Level: Important vulnerabilities, while not as severe as Critical ones, still have the potential to cause significant harm. They may pose a threat to the confidentiality, integrity, or availability of data and systems. Exploiting important vulnerabilities can lead to unauthorized access, compromise sensitive information, or disrupt system operations. It is vital to address important vulnerabilities in a timely manner to mitigate the risk they pose to systems and users.
- Moderate Severity Level: Moderate vulnerabilities have a limited potential for exploitation and typically require significant user interaction or specific conditions to be met. While the impact is less severe compared to Critical or Important vulnerabilities, they may still affect the confidentiality, integrity, or availability of data and systems. Addressing moderate vulnerabilities in a reasonable timeframe helps maintain system security and reduces the risk of exploitation.
- Low Severity Level: Low vulnerabilities have a minimal potential for exploitation and pose a low risk to systems and users. They require a high level of user interaction or specific conditions to be met for exploitation. Although the impact is generally minimal, it is still important to address low vulnerabilities during routine maintenance to maintain overall system security and minimize potential risks.
By categorizing vulnerabilities into different severity levels, the Microsoft Security Bulletin Severity Rating System provides a framework for prioritizing response efforts. It allows users and system administrators to allocate resources effectively based on the potential risk and impact of vulnerabilities. Regularly monitoring security bulletins from Microsoft and promptly addressing vulnerabilities based on their severity level is crucial to maintaining the security and integrity of systems and protecting against potential exploits.
Understanding Security Bulletins
Security bulletins play a vital role in keeping users and system administrators informed about vulnerabilities and the corresponding security updates provided by Microsoft. Understanding security bulletins is crucial for effectively managing and mitigating potential risks to systems and data. Here are key aspects of understanding security bulletins:
Content and Format: Security bulletins typically provide detailed information about specific vulnerabilities, including their impact, severity rating, and affected products or technologies. They outline the necessary steps to address the vulnerabilities, such as applying security updates, patches, or workarounds. Bulletins are presented in a standardized format, making it easier to navigate and understand the information provided.
Severity Ratings: Security bulletins include the severity rating assigned to each vulnerability. This rating helps users and system administrators assess the potential impact and prioritize their response efforts accordingly. It serves as a guide to understand the seriousness of the vulnerability and the urgency of applying the recommended security updates.
Affected Products: Security bulletins specify the products or technologies that are affected by the vulnerabilities. This information is crucial for identifying the systems that require immediate attention and applying the necessary security updates. It is important to note that different products may have different severity ratings for the same vulnerability, reflecting variations in potential impact and risk.
Recommended Actions: Security bulletins provide clear instructions on the recommended actions to address the vulnerabilities. This may involve downloading and installing security updates or patches, applying workarounds, or implementing additional security measures to mitigate the risk. Following the recommended actions promptly and accurately is crucial to maintaining system security.
Additional Information: Security bulletins often include additional information, such as known issues, FAQs, and resources for further assistance. This additional information can help users and system administrators navigate the remediation process and address any challenges or complexities that may arise.
Timeliness: Staying up to date with the latest security bulletins is critical. Microsoft regularly releases security bulletins as vulnerabilities are discovered and security updates become available. Promptly reviewing and acting upon security bulletins ensures that systems are protected against known vulnerabilities and potential exploits.
Understanding security bulletins enables users and system administrators to make informed decisions regarding the application of security updates, patches, and other necessary actions. By regularly monitoring and following the guidance provided in security bulletins, organizations and individuals can effectively mitigate potential risks, protect systems and data, and stay ahead of emerging security threats.
Importance of Staying Updated with Security Bulletins
Staying updated with security bulletins is of paramount importance in maintaining the security and integrity of systems and data. Security bulletins provide critical information about vulnerabilities, their potential impact, and recommended actions to mitigate the associated risks. Here are key reasons illustrating the importance of staying updated with security bulletins:
Timely Vulnerability Mitigation: Security bulletins inform users and system administrators about the latest vulnerabilities and the corresponding security updates or patches released by Microsoft. By staying updated, organizations can promptly identify and address vulnerabilities before they are exploited by attackers. Applying security updates in a timely manner helps minimize the window of opportunity for potential attacks.
Effective Risk Management: Security bulletins provide insight into the severity ratings assigned to vulnerabilities, allowing users and system administrators to assess the potential impact and prioritize their response efforts. Staying updated with security bulletins enables organizations to allocate resources effectively and efficiently manage and mitigate potential risks to their systems and data.
Protection Against Exploits: Attackers continually search for vulnerabilities to exploit. By staying updated with security bulletins, organizations gain valuable information about vulnerabilities and the steps required to protect against them. Applying recommended security updates promptly helps prevent successful exploitation and safeguards systems and data from compromise or unauthorized access.
Compliance Requirements: Staying informed about security bulletins is essential for meeting compliance requirements. Many industries and regulatory bodies mandate timely application of security updates to ensure the protection of sensitive information. Organizations that fail to stay updated with security bulletins may face penalties or loss of compliance status, leading to financial and reputational consequences.
Minimizing System Downtime: Exploited vulnerabilities can lead to system crashes, service disruptions, or data loss, resulting in significant downtime for organizations. Staying updated with security bulletins helps identify vulnerabilities that could potentially cause system failures or disruptions. By promptly applying security updates, organizations can minimize the risk of downtime and maintain continuous operations.
Proactive Security Posture: Staying updated with security bulletins demonstrates a proactive approach to system security. It allows organizations to stay ahead of emerging threats and vulnerabilities, protecting their systems and networks from potential attacks. Regularly reviewing security bulletins and implementing the recommended security measures reinforces a strong security posture.
Vendor Communication and Support: Security bulletins facilitate communication between Microsoft and its users, providing a platform for disseminating crucial security information. Staying updated allows organizations to avail themselves of vendor support and guidance in addressing vulnerabilities. The information in security bulletins assists the effective implementation of security measures and reinforces collaboration with Microsoft’s security experts.
Overall, staying updated with security bulletins is essential for protecting systems, data, and networks from potential exploits, ensuring compliance, and maintaining a proactive security posture. By monitoring security bulletins regularly and promptly applying recommended security updates, organizations can secure their infrastructure and mitigate risks associated with emerging security threats.