Overview
Trivial File Transfer Protocol (TFTP) is a simple and lightweight file transfer protocol that allows for the seamless transfer of files over a network. It is typically used in scenarios where simplicity and efficiency are prioritized over security and advanced features.
TFTP was first developed in the 1970s as a means of transferring files between different computer systems within a Local Area Network (LAN). Unlike other file transfer protocols, such as FTP, TFTP is minimalistic in nature, making it easy to implement and use.
One of the core concepts behind TFTP is its simplicity. The protocol primarily relies on User Datagram Protocol (UDP) as its underlying transport protocol, which allows for rapid and lightweight data transfers. However, due to its reliance on UDP, TFTP lacks many of the advanced features found in other file transfer protocols, such as reliable data delivery and encryption.
Another defining characteristic of TFTP is its lack of authentication and access control mechanisms. Unlike FTP, which requires a username and password for authentication, TFTP does not provide any built-in mechanisms for verifying the identity of the users or restricting access to certain files. This simplicity is one of the reasons why TFTP is commonly used for tasks such as booting diskless workstations or transferring firmware updates to network devices.
Despite its limitations, TFTP continues to be widely used in various industries. It is commonly found in network devices, such as routers and switches, where it is used to transfer operational data, configuration files, or firmware updates. TFTP is also utilized in the field of embedded systems, where it is employed to upload firmware or software updates to devices with limited resources.
How Does TFTP Work?
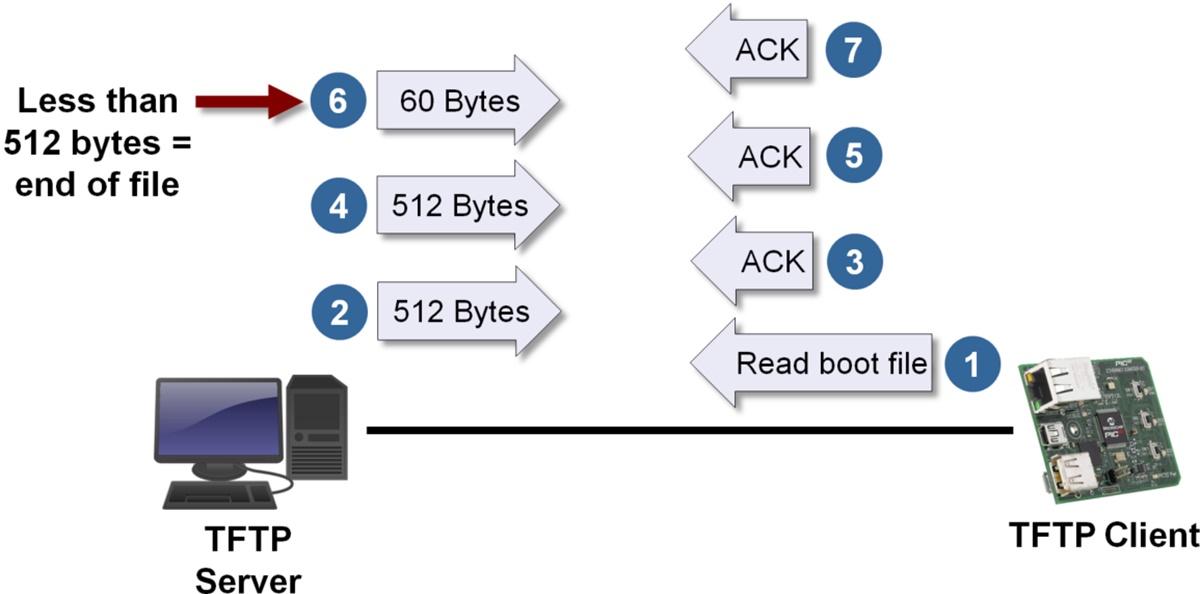
TFTP operates on a client-server architecture, where the client initiates the file transfer request and the server responds by sending the requested file. The communication between the client and server occurs over UDP, which makes it fast but less reliable than TCP.
The TFTP protocol defines a set of packet types that are used to facilitate the file transfer process. These packet types include read request (RRQ), write request (WRQ), data, acknowledgment (ACK), and error. The client and server exchange these packets to communicate and transfer the file.
Here is a step-by-step breakdown of how a TFTP file transfer works:
- The client sends a read request (RRQ) packet to the server, specifying the file it wants to retrieve.
- The server receives the RRQ packet and checks if the requested file is available. If the file is found, the server prepares to send the file.
- The server sends a data packet containing a block of the file’s data to the client.
- The client receives the data packet and sends an acknowledgment (ACK) packet back to the server, confirming the successful receipt of the data.
- If the file is not completely transferred, the process repeats from step 3, with the client and server sequentially numbering the data packets and acknowledgments.
- Once the file transfer is complete, the server sends a final data packet with zero data length to signal the end of the file.
- The client acknowledges the final data packet with an ACK packet, and the file transfer is considered successful.
TFTP is a connectionless protocol, meaning that there is no ongoing connection established between the client and server during the file transfer process. Each packet is individually sent and acknowledged, without any guarantee of delivery. This simplicity allows for fast transfers, but it also means that TFTP is more susceptible to packet loss and errors.
In addition, TFTP does not provide any form of authentication or encryption. It is crucial to ensure that TFTP is used in secure and trusted environments to prevent unauthorized access to sensitive files.
TFTP vs. FTP
TFTP and FTP (File Transfer Protocol) are both file transfer protocols, but they have distinct differences in terms of functionality, features, and use cases.
TFTP is a simpler and more lightweight protocol compared to FTP. It is primarily used for transferring files over a network and is often employed in scenarios where simplicity and efficiency are prioritized over advanced features and security.
FTP, on the other hand, is a more feature-rich protocol that offers a wide range of functionalities, including file uploads, downloads, directory listings, and file management operations. It provides more control and flexibility but comes with added complexity.
Here are some key differences between TFTP and FTP:
- Transport Protocol: TFTP uses UDP (User Datagram Protocol), while FTP uses TCP (Transmission Control Protocol). UDP provides faster data transfer with minimal overhead, but it does not guarantee reliable delivery or error checking, unlike TCP which ensures reliable and ordered delivery of packets.
- Authentication and Security: TFTP lacks built-in authentication mechanisms and does not support encryption, making it less secure compared to FTP, which supports various authentication methods, such as username and password, and can use Secure FTP (SFTP) or FTP over TLS/SSL for secure transfers.
- Port Usage: TFTP typically uses UDP port 69, while FTP uses TCP ports 20 and 21 for data transfer and control commands, respectively.
- Transfer Modes: FTP supports both ASCII and binary transfer modes, allowing for the transfer of files in different formats. TFTP, on the other hand, only supports binary mode, which is suitable for transferring binary files but not for text files with special character conversions.
- File Size Limitation: TFTP has a maximum file size limit of 32 MB, which may be a constraint in certain scenarios. FTP does not have a specific file size limitation, allowing for the transfer of larger files.
When choosing between TFTP and FTP, it is essential to consider the specific requirements of your file transfer needs. If simplicity, speed, and small file transfers are the main focus, TFTP may be a suitable choice. However, if you require advanced features, secure transfers, and support for larger files, FTP is the more appropriate option.
Advantages of TFTP
TFTP (Trivial File Transfer Protocol) offers several advantages that make it a popular choice for specific use cases.
- Simplicity: TFTP is a straightforward and minimalistic protocol, making it easy to implement, use, and troubleshoot. Its simplicity allows for faster transfers and reduces the overhead associated with more complex file transfer protocols.
- Efficiency: TFTP uses the User Datagram Protocol (UDP) as its underlying transport protocol, which enables fast and lightweight data transfers. Unlike protocols like FTP, TFTP does not require establishing and maintaining a connection, resulting in faster transfers. This efficiency is particularly advantageous in scenarios where speed is critical, such as in booting diskless workstations or transferring firmware updates to network devices.
- Low Resource Consumption: TFTP requires fewer system resources compared to more robust file transfer protocols like FTP. It is suitable for systems with limited memory and processing capabilities, making it widely utilized in embedded systems and network devices.
- Wide Device Support: TFTP is supported by a vast range of network devices, including routers, switches, and other networking equipment. It is commonly used for tasks such as transferring operational data, configuration files, and firmware updates in these devices.
- Compatibility: TFTP clients and servers are available for various operating systems, making it a versatile choice for cross-platform file transfers. It allows for seamless communication and file sharing between different devices and operating systems.
Despite these advantages, it is important to note that TFTP does have limitations, particularly in terms of security and advanced features. The lack of built-in authentication mechanisms and encryption makes TFTP less secure compared to other protocols like FTP or SFTP. Additionally, TFTP operates on UDP, which does not guarantee reliable data delivery, making it more susceptible to packet loss or errors.
Considering these advantages and limitations, it is crucial to assess your requirements and the specific context in which you plan to use TFTP. If simplicity, speed, and efficient file transfers are the primary considerations, TFTP may be an ideal choice. However, if security, authentication, and advanced features are critical factors, alternative protocols such as FTP or SFTP may be more suitable.
Disadvantages of TFTP
While Trivial File Transfer Protocol (TFTP) offers simplicity and efficiency, it also comes with several limitations and disadvantages that may impact its suitability for certain use cases.
- Lack of Security: One of the major disadvantages of TFTP is its lack of built-in security features. Unlike protocols such as FTP or SFTP, TFTP does not provide authentication mechanisms or encryption. This makes TFTP vulnerable to unauthorized access, data interception, and tampering. It is crucial to ensure that TFTP is used in secure and trusted environments to prevent security breaches.
- No Error Checking or Correction: TFTP operates on the User Datagram Protocol (UDP), which does not include error checking or correction mechanisms. This means that TFTP cannot guarantee the reliable delivery of data packets. In the event of packet loss or errors, TFTP does not automatically recover and retransmit the lost packets, potentially leading to incomplete or corrupted file transfers.
- Limited File Size: TFTP imposes a maximum file size limit of 32 megabytes. This restriction can be a significant limitation in scenarios requiring the transfer of larger files. If you need to transfer files larger than the specified limit, alternative protocols like FTP or HTTP may be more suitable.
- No Directory Listing Support: Unlike FTP, TFTP does not support directory listing functionality. This means that clients can only access specific files if they know the exact file name and location on the server. This limitation can make it more challenging to navigate and manage files in a TFTP environment.
- Limited Functionality: TFTP is designed for simplicity and efficiency, sacrificing advanced features that are available in other protocols like FTP. Functions such as resuming interrupted transfers, file deletion, and renaming are not supported in TFTP. It may be necessary to consider alternative protocols if comprehensive file management capabilities are required.
When considering the use of TFTP, it is essential to weigh these disadvantages against your specific requirements and the level of security and functionality needed for your file transfer operations. In many cases, TFTP is a suitable choice for simple file transfers in trusted environments. However, for more complex transfers that require advanced features and enhanced security, alternative protocols such as FTP or SFTP may be more appropriate.
Use Cases for TFTP
Trivial File Transfer Protocol (TFTP) has a range of practical use cases where its simplicity and efficiency make it a suitable choice.
- Network Device Configuration: TFTP is commonly used to transfer configuration files to network devices such as routers, switches, and firewalls. It allows for easy and quick configuration updates, minimizing downtime and simplifying device management.
- Firmware Updates: TFTP is frequently employed for transferring firmware updates to various devices, including network equipment, embedded systems, and IoT devices. Its lightweight nature and fast transfer speeds make it ideal for distributing firmware updates efficiently.
- Booting Diskless Systems: TFTP is often used in diskless environments, where client systems boot from a network instead of a local storage device. TFTP enables clients to retrieve the necessary boot files (such as operating system images or configuration files) from a TFTP server, facilitating centralized management and reducing the need for local storage.
- Embedded Systems: TFTP plays a significant role in the field of embedded systems. It is frequently used for updating firmware, transferring configuration settings, and exchanging data between embedded devices and external systems. The lightweight nature of TFTP makes it well-suited for devices with limited resources.
- Diagnostic and Troubleshooting: TFTP is a valuable tool for diagnostic and troubleshooting purposes. It allows technicians to transfer log files, configuration files, and diagnostic tools to and from network devices and troubleshoot issues remotely.
It is important to note that while TFTP is well-suited for these use cases, its minimalistic nature does come with certain limitations. Due to the lack of authentication and encryption, TFTP should only be used in trusted, secure environments. Additionally, the absence of error checking and correction mechanisms may necessitate additional precautions to ensure data integrity during transfers.
When considering TFTP for your specific use case, carefully evaluate the security and reliability requirements of your file transfers. If simplicity, speed, and efficiency are key considerations, and the limited feature set of TFTP aligns with your needs, it can be an effective solution for several practical scenarios.
TFTP Clients and Servers
In order to implement and utilize Trivial File Transfer Protocol (TFTP), you will need TFTP clients and servers. A TFTP client is a software application that initiates file transfer requests, while a TFTP server is responsible for responding to these requests and facilitating the file transfer process.
Several TFTP client and server implementations exist, available for various operating systems and platforms. These software tools allow for seamless interaction with TFTP, enabling easy and efficient file transfers.
Here are some notable TFTP client and server options:
- PumpKIN TFTP: PumpKIN TFTP is a free and open-source TFTP client and server available for Windows. It provides a user-friendly interface and supports features such as file transfers, directory transfers, and IP address filtering.
- Tftpd32: Tftpd32 is another popular TFTP client and server for Windows. It offers a comprehensive feature set, including support for TFTP, DHCP, SNTP, and Syslog. Tftpd32 is widely used for network management, firmware updates, and network booting.
- tftp-hpa: tftp-hpa is a TFTP client and server package commonly used in Linux environments. It is known for its high-performance capabilities and compatibility with various hardware platforms.
- TFTP Server by SolarWinds: SolarWinds offers a TFTP server solution that is highly regarded for its reliability and ease of use. It provides a secure and scalable platform for both Windows and Linux environments, making it suitable for diverse applications.
- Windows TFTP Utility: Windows includes a built-in TFTP client utility called “tftp,” which can be accessed via the command line interface (CLI). Although it is a basic client, it supports necessary TFTP operations, making it a convenient option for simple file transfers.
When selecting a TFTP client or server, consider factors such as platform compatibility, ease of use, supported features, and security. Additionally, make sure the chosen solution aligns with your specific operating system and networking requirements.
It is important to remember that TFTP lacks built-in security features. Therefore, it is essential to ensure that you implement appropriate security measures, such as network segmentation, access controls, and firewall configurations, to protect your TFTP transfers from unauthorized access or data breaches.
Common TFTP Commands
TFTP (Trivial File Transfer Protocol) utilizes several commands to facilitate file transfers between clients and servers. These commands are simple and straightforward, designed to align with the minimalistic nature of the protocol. Understanding these commands is essential for effectively using TFTP for file transfers.
Here are some common TFTP commands:
- RRQ (Read Request): The RRQ command is initiated by the client to request a file from the server. It specifies the filename and transfer mode. The server responds by sending the requested file.
- WRQ (Write Request): The WRQ command is used by the client to request the server to accept a file for writing. It includes the filename and transfer mode. Once the server confirms readiness, the client proceeds to send the file data.
- DATA: The DATA command is used to send a block of data from the server to the client. It contains a sequence number identifying the block of data being sent.
- ACK (Acknowledgment): The ACK command is sent by the client to acknowledge the receipt of a data block. It includes the sequence number of the successfully received block, indicating that the client is ready for the next data block.
- ERROR: The ERROR command is used to indicate an error condition during the file transfer process. It includes an error code and an error message to provide information about the encountered error.
These commands are typically exchanged between the client and server to initiate and manage the file transfer process. The request and response cycle allows for the transfer of file data in blocks, ensuring that the entire file is successfully transmitted.
It is worth noting that different TFTP client and server implementations may have variations in command syntax or additional commands specific to their functionalities. Therefore, it is recommended to refer to the documentation or user guide of the TFTP software you are using to ensure accurate usage of commands.
Understanding and utilizing these TFTP commands enables efficient and effective file transfers, allowing users to retrieve or upload files to TFTP servers seamlessly.
Securing TFTP
Trivial File Transfer Protocol (TFTP) lacks built-in security mechanisms, making it vulnerable to unauthorized access and data interception. However, there are steps you can take to enhance the security of your TFTP transfers.
1. Use a Virtual Private Network (VPN): Implementing a VPN adds an extra layer of security by encrypting the data transmitted between the client and server. This prevents eavesdropping and ensures the confidentiality of your TFTP transfers.
2. Limit Access: Restrict access to your TFTP server by allowing only authorized users and trusted hosts to connect. Implement measures such as firewall rules, access control lists, or IP address filtering to limit access to the TFTP service and prevent unauthorized users from accessing your files.
3. Implement User Authentication: Consider utilizing additional security measures, such as implementing user authentication mechanisms alongside TFTP. This can involve creating user accounts with strong passwords and granting appropriate access privileges to ensure that only authorized users can access the TFTP server.
4. Encrypt Data at the Transport Layer: Since TFTP operates over UDP, it does not inherently encrypt data. To add encryption to your TFTP transfers, consider using an additional encryption mechanism, such as SSH (Secure Shell) or SSL/TLS (Secure Sockets Layer/Transport Layer Security), to protect the data as it is transmitted over the network.
5. Implement TFTP Security Extensions: TFTP has several security extensions available that can enhance its security capabilities. One such extension is TFTP over SSH, which combines the security features of SSH with the simplicity of TFTP. Implementing these extensions can provide an additional layer of encryption and authentication for your TFTP transfers.
6. Regularly Update and Patch: Keep your TFTP software up to date with the latest patches and updates. Regularly check for security updates or patches provided by the TFTP software vendor. Updating your software ensures that any known vulnerabilities are addressed and enhances the overall security of your TFTP transfers.
By implementing these security measures, you can significantly enhance the security of your TFTP transfers. However, it is important to remember that TFTP is not intended for secure file transfers, and for more sensitive or critical data, it is recommended to use alternative protocols like SFTP (SSH File Transfer Protocol) or FTPS (FTP Secure) that offer built-in encryption and authentication mechanisms.
Alternatives to TFTP
While Trivial File Transfer Protocol (TFTP) is a lightweight and simple file transfer protocol, there are alternative protocols available that offer additional features and improved security. These alternatives provide enhanced functionality and are better suited for specific use cases.
1. FTP (File Transfer Protocol): FTP is a widely used file transfer protocol that supports various features such as directory listing, renaming files, and resuming interrupted transfers. It offers more control and functionality compared to TFTP, making it suitable for scenarios that require advanced file management capabilities. FTP also provides built-in authentication mechanisms and supports secure transfers using FTPS (FTP Secure) or SFTP (SSH File Transfer Protocol).
2. SFTP (SSH File Transfer Protocol): SFTP is a protocol that uses Secure Shell (SSH) to provide secure file transfer capabilities. It combines the security features of SSH, such as encryption and authentication, with the file transfer functionality. SFTP is widely supported and commonly used for secure file transfers, particularly in situations where data confidentiality and integrity are crucial.
3. SCP (Secure Copy Protocol): SCP is a protocol that uses SSH for secure file transfers. It provides a simple command-line interface for copying files between hosts securely. SCP is built on top of SSH, ensuring encrypted connections and secure transfers, making it a popular choice for secure file transfers in both local and remote environments.
4. HTTP/S (Hypertext Transfer Protocol/Secure): HTTP and its secure counterpart, HTTPS, are widely used protocols for transferring files over the web. They offer a range of features, including support for larger file sizes, resumeable transfers, and authentication mechanisms. HTTP/S can be utilized for file transfers in situations where HTTP servers are already in place, or when web-based file sharing and distribution are required.
5. FASP (Fast And Secure Protocol): FASP is a highly secure and high-speed file transfer protocol developed by Aspera. It utilizes advanced encryption algorithms and adaptive rate control to ensure fast and reliable transfers over long distances and challenging network conditions. FASP is commonly used in industries such as media and entertainment, research, and data-intensive environments.
These alternatives offer a broader range of features, better security, and improved scalability compared to TFTP. When selecting an alternative protocol, consider the specific requirements of your file transfer scenario, including security, functionality, and the environment in which the transfers will take place.
While TFTP remains a suitable choice for simple and efficient transfers in trusted environments, these alternatives provide more robust options for scenarios that demand extended functionality, advanced security, and enhanced reliability.