Overview of IPSec
IPSec, which stands for Internet Protocol Security, is a framework used to secure communication over IP networks. It is a widely adopted standard that provides a robust and reliable way to protect data integrity, confidentiality, and authenticity over the internet. IPSec operates at the network layer of the OSI model and can be used to secure various protocols, including IP, TCP, and UDP.
The primary goal of IPSec is to establish a secure connection between two or more endpoints, ensuring that data transmitted between them remains secure and private. This is particularly important in today’s interconnected world, where sensitive information is constantly being exchanged over public networks.
IPSec achieves its security objectives through two main mechanisms: authentication and encryption. Authentication ensures that the communicating parties are who they claim to be, while encryption ensures that data is protected from unauthorized access or modification.
IPSec provides a flexible framework that can be utilized in various scenarios, such as site-to-site VPNs (Virtual Private Networks), remote access VPNs, and secure remote management. It can be implemented in both IPv4 and IPv6 networks, making it compatible with a wide range of devices and network setups.
One of the key advantages of IPSec is its transparency to applications and protocols running on top of it. This means that applications do not need to be modified or aware of IPSec to benefit from its security features. IPSec operates at the network layer, providing a secure and transparent tunnel for the higher layer protocols, such as HTTP, FTP, or VoIP.
Overall, IPSec is a crucial component of network security, enabling organizations to protect their valuable data and ensure the privacy and integrity of their communications. By establishing secure connections between endpoints and encrypting data in transit, IPSec provides a vital layer of protection in today’s interconnected world.
How IPSec Works
IPSec works by establishing a secure channel, known as a VPN tunnel, between two or more endpoints. This tunnel encrypts all data passing through it, ensuring its confidentiality and integrity.
The process of establishing an IPSec connection involves several steps:
- Key Exchange: Before data can be encrypted and transmitted securely, the communicating parties need to establish a shared secret key. This is accomplished through a key exchange protocol, such as Internet Key Exchange (IKE), which ensures that both sides have a common key that cannot be easily guessed or intercepted.
- Authentication: Once the key exchange is complete, the next step is to authenticate the communicating parties. This is done to ensure that each endpoint is legitimate and authorized to establish a secure connection. Authentication can be achieved using various methods, such as digital certificates, pre-shared keys, or username/password combinations.
- Encryption: After successfully authenticating each other, the endpoints can start encrypting the data they exchange. IPSec supports multiple encryption algorithms, such as AES (Advanced Encryption Standard), 3DES (Triple Data Encryption Standard), and Blowfish, to ensure data confidentiality. The encryption process converts plain text data into an unreadable format, which can only be decrypted with the appropriate encryption key.
- Integrity: To ensure that the data has not been tampered with during transmission, IPSec uses message integrity checks. These checks, known as hash functions, generate a unique code (hash) for each packet of data. The receiving endpoint can use this code to verify the integrity of the received data and detect any unauthorized modifications or tampering.
Once the IPSec connection is established, all traffic between the endpoints is encapsulated within IPSec packets. These packets are protected using the established encryption and integrity mechanisms, ensuring that the data remains secure and confidential throughout its journey across the network.
It’s important to note that IPSec can operate in two modes: transport mode and tunnel mode. Transport mode encrypts only the payload of the IP packet, while tunnel mode encrypts the entire IP packet, including the original IP header. The mode used depends on the specific requirements and configuration of the IPSec implementation.
Overall, IPSec provides a robust and reliable method for securing communication over IP networks. By implementing encryption, authentication, and integrity checks, IPSec ensures that data is protected from unauthorized access and tampering, establishing a secure and private channel for communication.
Key Elements of IPSec
IPSec comprises several key elements that work together to provide secure communication over IP networks. Understanding these elements is crucial for implementing and configuring IPSec effectively. The main elements of IPSec are:
- Security Association (SA): SA is a logical connection between two IPSec endpoints. It defines the security parameters, such as encryption and authentication algorithms, keys, and other parameters necessary for secure communication. Each direction of communication (inbound and outbound) requires a separate SA.
- Security Policy Database (SPD): The SPD is a database that stores a set of rules used by IPSec to determine how packets should be processed. These rules define which traffic should be protected, what security services should be applied, and which SA to use. The SPD provides the necessary information for IPSec to determine if packets match a specific security policy.
- Internet Key Exchange (IKE): IKE is a key management protocol used by IPSec to establish and update SA parameters between two endpoints. It performs key exchange, authentication, and negotiation of the IPSec security parameters. IKE ensures that the communication parties share a common secret key and mutually agree on the encryption and authentication algorithms to be used.
- Encryption Algorithms: IPSec supports a variety of encryption algorithms, including AES, 3DES, and Blowfish. These algorithms determine how the data is encrypted and decrypted, ensuring its confidentiality. The choice of encryption algorithm depends on factors such as security requirements, performance considerations, and compatibility with the endpoints.
- Authentication Algorithms: IPSec uses authentication algorithms, such as HMAC (Hashed Message Authentication Code), to ensure the integrity and authenticity of the data. Authentication algorithms generate hash codes that are used to verify that the data has not been tampered with during transmission. Commonly used authentication algorithms include HMAC-MD5 and HMAC-SHA1.
- Security Protocols: IPSec can be implemented using different security protocols, such as Encapsulating Security Payload (ESP) and Authentication Header (AH). ESP provides confidentiality, integrity, and authentication of the data, while AH provides integrity and authentication but does not encrypt the data. The choice of security protocol depends on the specific requirements and configuration of the IPSec implementation.
These key elements form the foundation of IPSec and allow for the secure and reliable transmission of data over IP networks. By understanding how these elements work together, network administrators can configure IPSec to meet their organization’s specific security needs.
Authentication in IPSec
Authentication plays a vital role in IPSec by ensuring the identity and legitimacy of communicating parties. It verifies that the endpoints attempting to establish a secure connection are who they claim to be, preventing unauthorized access and ensuring the integrity of the communication. IPSec offers several authentication methods, including:
- Digital Certificates: Digital certificates are issued by trusted certification authorities and are used to verify the identity of communicating parties. Each endpoint possesses a unique certificate that contains a public key. During the IPSec handshake process, the endpoints exchange their certificates and validate them against the trusted certification authority. This ensures that only authorized entities can establish a secure connection.
- Pre-Shared Keys: Pre-shared keys are manually configured secret keys shared between the endpoints. During the IPSec handshake, the endpoints authenticate each other by exchanging these keys. Both endpoints must possess the same pre-shared key for the authentication to be successful. While pre-shared keys are relatively simpler to implement, care must be taken to ensure their confidentiality, as a compromised key could lead to unauthorized access.
- Challenge-Response: In a challenge-response authentication method, one endpoint (the challenger) sends a randomly generated challenge to the other endpoint (the responder). The responder uses a secret key or password to calculate a response, which is then sent back to the challenger. If the response matches the expected value, authentication is successful. Challenge-response authentication adds an extra layer of security by verifying that the endpoints possess the correct secret information.
- Username/Password: Username and password authentication is a common method used in remote access VPNs. The user provides a username and password combination during the authentication process, which is then validated by the authentication server. This authentication method is widely used due to its simplicity, but it may be less secure compared to other methods if strong passwords are not enforced.
Authentication in IPSec establishes trust between the communicating parties and ensures that only authorized entities can access the protected network. It prevents unauthorized access and protects against impersonation or man-in-the-middle attacks. By accurately verifying the identity of the endpoints, authentication contributes to the overall security and integrity of the IPSec connection.
It is worth noting that authentication in IPSec is not only limited to verifying the endpoint’s identity but can also extend to the integrity and authenticity of the transmitted data. Authentication algorithms, such as HMAC, are used to generate hash codes that are used to verify the integrity of the data. This ensures that the data has not been tampered with during transmission and that it can be trusted.
By employing robust authentication methods within IPSec, organizations can enhance the security of their networks, protect sensitive data, and ensure that communication takes place only between trusted and authorized entities.
Encryption in IPSec
Encryption is a vital component of IPSec, as it ensures the confidentiality and privacy of data transmitted over IP networks. By encrypting the data, IPSec protects it from unauthorized access and ensures that only the intended recipient can decipher and read the information. IPSec utilizes various encryption algorithms to provide strong and secure encryption, including:
- AES (Advanced Encryption Standard): AES is widely regarded as one of the most secure and efficient encryption algorithms currently available. It supports key sizes of 128, 192, or 256 bits, providing strong encryption and resistance against brute-force attacks. AES has become the preferred encryption algorithm in many IPSec implementations due to its strength and performance.
- 3DES (Triple Data Encryption Standard): 3DES is a symmetric encryption algorithm that applies the Data Encryption Standard (DES) algorithm three times to each data block. It provides a higher level of security compared to the original DES algorithm and is still used in some legacy IPSec deployments. However, due to its relatively slower processing speed, 3DES has been largely replaced by AES.
- Blowfish: Blowfish is a fast and flexible encryption algorithm that uses variable key sizes between 32 and 448 bits. It provides a good balance between security and performance, making it suitable for a wide range of applications. While Blowfish is not as widely adopted as AES, it is still considered a reliable encryption option in some IPSec deployments.
When data is sent over an IPSec connection, it is encapsulated within IPSec packets. The data is encrypted at the sending endpoint and decrypted at the receiving endpoint, ensuring that only the intended recipient can access the original information. This process of encryption and decryption ensures that the data remains confidential and secure from eavesdroppers and unauthorized individuals.
IPSec operates at the network layer, allowing it to encrypt and protect all types of IP traffic, including TCP, UDP, and ICMP packets. This means that applications and protocols running on top of IPSec do not need to be aware of the encryption process; the encryption and decryption occur transparently at the IPSec layer.
It’s important to note that IPSec supports two modes of operation for encryption: transport mode and tunnel mode. In transport mode, only the payload (data) of the IP packet is encrypted, leaving the original IP header intact. Tunnel mode, on the other hand, encrypts the entire IP packet, including the original IP header. The mode used depends on the network setup and security requirements of the IPSec implementation.
By utilizing strong encryption algorithms, IPSec ensures that data confidentiality is maintained and that sensitive information remains protected during transmission. The encryption capabilities of IPSec are a crucial aspect of its overall security framework, providing organizations with a reliable way to secure their communications over IP networks.
IPSec Protocols
IPSec relies on various protocols to establish secure communication channels and provide the necessary security services. The primary protocols used in IPSec are:
- Internet Key Exchange (IKE): IKE is a key management protocol that is used to negotiate the security parameters and establish secure connections in IPSec. It provides a secure and automated way for endpoints to exchange keys, authenticate each other, and establish a secure channel. IKE ensures that both sides agree on the encryption, authentication, and other security parameters before data transmission begins.
- Authentication Header (AH): AH is an IPSec protocol that provides integrity and authentication for IP packets. It adds an additional header to the IP packet, which contains a cryptographic hash code (hash) that ensures the integrity of the packet. AH does not provide encryption, but it can be used in combination with other protocols, such as encapsulating security payload (ESP), to provide a comprehensive security solution.
- Encapsulating Security Payload (ESP): ESP is an IPSec protocol that provides both encryption and authentication for IP packets. It encapsulates the payload of the IP packet and adds additional headers to provide confidentiality, integrity, and authentication. ESP encrypts the IP payload, ensuring that the data remains confidential, and provides authentication to verify the integrity of the packet. ESP is commonly used in combination with IKE for more comprehensive IPSec security.
IKE, AH, and ESP work together to establish secure connections and ensure the secure transmission of data over IP networks. They provide a strong and reliable security framework that protects against unauthorized access, eavesdropping, and tampering of data.
In addition to these primary protocols, IPSec can also utilize other ancillary protocols and technologies to enhance its functionality and security. These include:
- Internet Security Association and Key Management Protocol (ISAKMP): ISAKMP is a protocol framework used in conjunction with IKE to establish, negotiate, and manage the security associations. It defines the format and management of security payloads used in IKE-based protocols.
- Public Key Infrastructure (PKI): PKI is a system that provides mechanisms for managing and verifying digital certificates used for authentication in IPSec. It relies on a trusted certification authority to issue and sign digital certificates, ensuring the authenticity and integrity of the certificates used in the IPSec communication.
- Diffie-Hellman (DH) Key Exchange: DH is a key exchange algorithm used as part of the IKE protocol to securely establish a shared secret key between the communicating endpoints. It allows the endpoints to agree on a shared key without exchanging it directly over the network, thereby protecting it from eavesdroppers.
By utilizing these protocols and technologies, IPSec provides a comprehensive and robust framework for securing IP communication. It ensures the confidentiality, integrity, and authenticity of data transmitted over IP networks, protecting organizations and individuals from potential threats and vulnerabilities.
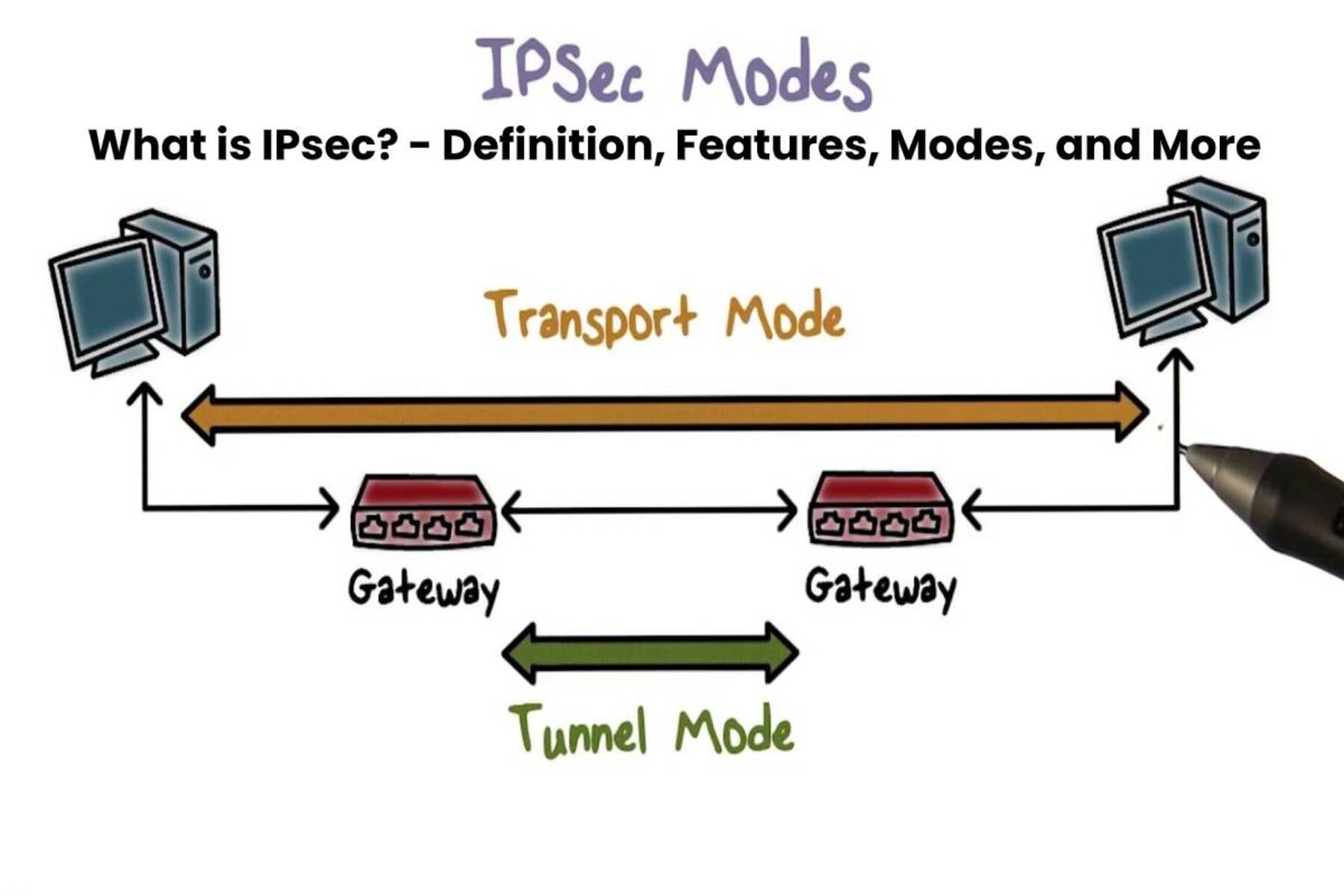
IPSec Modes of Operation
IPSec offers two modes of operation: transport mode and tunnel mode. These modes determine how IPSec is applied to the IP packets and provide flexibility in configuring IPSec based on specific network requirements.
Transport Mode:
In transport mode, IPSec provides security for the payload (data) of the IP packets while leaving the original IP header intact. The main purpose of transport mode is to secure end-to-end communication between two hosts. Only the data portion of the IP packet is encrypted, ensuring confidentiality and integrity during transmission.
In transport mode, the IP header of the packet is not encrypted, which means that the source and destination IP addresses remain visible. This mode is typically used when both endpoints are within the same secure network or trust boundary, and there is no need to hide the IP addresses of the communicating hosts.
Transport mode is commonly used for securing protocols that require end-to-end security, such as voice over IP (VoIP) or video conferencing. It provides a lightweight and efficient way to secure communication while maintaining the original IP addressing scheme.
Tunnel Mode:
Tunnel mode, on the other hand, provides a more comprehensive level of security by encrypting the entire IP packet, including the original IP header. In tunnel mode, a new IP header is added, encapsulating the original IP packet, which is then encrypted and authenticated.
The primary purpose of tunnel mode is to create secure connections between networks or across the internet. It allows for the creation of a virtual private network (VPN) where all traffic sent between the networks is encrypted and protected. Tunnel mode essentially creates a secure “tunnel” for the entire IP packet through potentially untrusted networks.
Tunnel mode is commonly used in scenarios where the communicating endpoints are located in different networks, and there is a need to protect the IP addresses of the communicating hosts. It is also often used for site-to-site VPN connections or remote access VPNs, where users need to securely access resources within a private network over public networks.
By offering both transport and tunnel modes, IPSec enables organizations to implement the appropriate level of security based on their specific requirements. Transport mode provides end-to-end security for host-to-host communication, while tunnel mode offers network-to-network or remote access security, ensuring the confidentiality, integrity, and privacy of the transmitted data.
Advantages of Using IPSec
IPSec offers several advantages that make it a widely adopted and trusted solution for securing communication over IP networks. The benefits of using IPSec include:
- Security: IPSec provides a strong and reliable security framework for protecting data transmitted over IP networks. By encrypting the data and ensuring the integrity and authenticity of the communication, IPSec safeguards sensitive information, preventing unauthorized access and eavesdropping.
- Transparent Operation: IPSec operates at the network layer of the OSI model, which means that it is transparent to higher layer protocols and applications. Applications do not need to be modified or aware of IPSec to benefit from its security features. This transparency allows for seamless integration with existing network infrastructure and applications.
- Flexibility: IPSec provides flexibility in terms of implementation and configuration options. It supports various encryption and authentication algorithms, allowing organizations to choose the level of security that best suits their needs. IPSec is also compatible with both IPv4 and IPv6 networks, ensuring compatibility with a wide range of devices and network setups.
- Scalability: IPSec can be easily scaled to accommodate a growing network or increased traffic demands. It can be deployed to secure communication between individual hosts, as well as large networks and subnets. This scalability makes IPSec suitable for organizations of all sizes, from small businesses to large enterprises.
- Interoperability: IPSec is a widely adopted and standardized protocol, ensuring interoperability between different vendors’ implementations. This allows organizations to leverage IPSec across their network infrastructure, regardless of the specific hardware or software solutions being used.
- Cost-Effectiveness: As a built-in feature of many operating systems and network devices, IPSec provides a cost-effective solution for securing communication. There is no need for additional hardware or software investments, reducing the overall cost of implementing and maintaining network security.
- Compliance: IPSec is often required to meet regulatory and industry compliance standards, such as HIPAA (Health Insurance Portability and Accountability Act) or PCI DSS (Payment Card Industry Data Security Standard). By implementing IPSec, organizations can ensure that they meet the necessary security requirements and protect sensitive data.
Overall, IPSec offers a comprehensive and reliable solution for securing communication over IP networks. Its strong security features, flexibility, transparency, and interoperability make it an attractive choice for organizations seeking to protect their data and maintain the privacy and integrity of their communication.
Common Use Cases for IPSec
IPSec is widely utilized in various scenarios to ensure secure and private communication over IP networks. Some common use cases for IPSec include:
- Virtual Private Networks (VPNs): IPSec is commonly used in VPNs to create secure connections between remote sites or for remote access to a private network. By implementing IPSec, organizations can establish encrypted tunnels over public networks, ensuring that data transmitted between sites or remote users remains confidential and secure.
- Site-to-Site Communication: IPSec is often deployed to secure communication between different branch offices or data centers within an organization. By establishing secure tunnels between sites, IPSec ensures that data transmitted over these connections remains secure and protected from unauthorized access, ensuring the confidentiality and integrity of sensitive information.
- Remote Access: IPSec is utilized for remote access scenarios, allowing remote employees or mobile users to securely connect to a private network over the internet. Whether through VPN clients or built-in IPSec functionality on mobile devices, IPSec ensures that remote access connections are encrypted and authenticated, protecting sensitive data from potential threats.
- Wireless Networks: IPSec is used to secure wireless networks, particularly in enterprise or public Wi-Fi environments. By implementing IPSec on wireless access points and devices, organizations can ensure that data transmitted over these networks remains protected, preventing unauthorized access or eavesdropping.
- Voice and Video Communication: IPSec provides secure encryption for real-time voice and video communication, such as VoIP (Voice over IP) or video conference calls. By securing the traffic with IPSec, organizations can ensure the privacy and integrity of these communication channels, protecting sensitive conversations from interception or tampering.
- Cloud Computing: IPSec is commonly utilized in cloud computing environments to establish secure communication between on-premises networks and cloud services. By implementing IPSec tunnels, organizations can ensure that data transmitted to and from the cloud remains encrypted and protected, maintaining the security and privacy of sensitive information.
- Internet of Things (IoT): With the rise of IoT devices, IPSec is increasingly used to secure communication between these devices and central systems. By implementing IPSec, organizations can ensure that data transmitted between IoT devices and cloud platforms remains confidential and protected from potential security threats.
These are just a few common use cases for IPSec, highlighting its versatility and wide-ranging applications. IPSec provides a robust and reliable solution for securing communication in various scenarios, allowing organizations to protect their data and maintain the privacy and integrity of their communication over IP networks.
Limitations of IPSec
While IPSec offers numerous advantages, it also has some limitations that organizations should be aware of when considering its implementation. These limitations include:
- Complexity: Implementing IPSec can be complex, especially for organizations with limited IT resources or expertise. Configuration and management of IPSec require careful planning and understanding of the network infrastructure, security policies, and compatibility with different devices and platforms.
- NAT (Network Address Translation) Traversal: IPSec can encounter difficulties when traversing network address translation (NAT) devices or firewalls. NAT modifies the IP addresses and ports of packets, which can interfere with the IPSec headers and cause connectivity issues. Although techniques like NAT traversal have been developed to address this limitation, it may require additional setup and configuration.
- Performance Overhead: Implementing encryption and authentication processes in IPSec can introduce performance overhead. The computational resources required to encrypt and decrypt the data packets can impact network throughput, potentially leading to slower connection speeds. However, advancements in hardware and software have significantly mitigated this limitation, and modern systems can handle IPSec processing efficiently.
- Key Management: Effective key management is crucial for the secure operation of IPSec. Generating and distributing keys securely, ensuring their integrity, and managing their lifecycle can be challenging. Organizations need to establish proper processes and protocols for key management to ensure the confidentiality and security of the keys used in IPSec deployments.
- Compatibility: Although IPSec is a widely adopted standard, compatibility issues can arise with different implementations or network devices. While efforts have been made to ensure interoperability, organizations should verify compatibility and conduct thorough testing when deploying IPSec across different platforms, vendors, and operating systems.
- Public Key Infrastructure (PKI) Dependencies: Implementing digital certificates for authentication in IPSec often requires a robust and well-managed Public Key Infrastructure (PKI). Setting up and managing a PKI infrastructure can introduce additional complexity and overhead. Organizations need to consider the overhead and maintenance associated with PKI deployments when planning for IPSec implementation.
Despite these limitations, IPSec remains a powerful and widely adopted security framework for protecting communication over IP networks. By understanding and addressing these limitations, organizations can leverage IPSec effectively to secure their networks and protect sensitive information.
Alternatives to IPSec
While IPSec is a widely used and trusted protocol for securing communication over IP networks, there are alternative approaches and technologies available that organizations can consider based on their specific needs and requirements. Some alternatives to IPSec include:
- Transport Layer Security (TLS): TLS is a cryptographic protocol primarily used to secure web communication, such as HTTP and HTTPS. It operates at the application layer and provides encryption, integrity, and authentication for the transmitted data. While IPSec secures communication at the network layer, TLS focuses on securing application layer protocols. TLS is commonly used for securing web-based applications and is widely supported by web browsers.
- Secure Shell (SSH): SSH is a network protocol that provides secure remote login and file transfer. It allows for encrypted communication between the client and the server, ensuring the confidentiality and integrity of the transmitted data. SSH is commonly used for remote administration, secure file transfer, and secure tunneling.
- WireGuard: WireGuard is a relatively new and lightweight VPN protocol that aims to provide simplicity, security, and speed. It operates at the kernel level and uses modern encryption techniques, such as the Noise protocol framework. WireGuard is known for its simplicity of configuration and ease of use while providing robust security for VPN connections.
- Virtual Private LAN Service (VPLS): VPLS is a technology that allows for the creation of a virtual LAN (Local Area Network) over a wide area network (WAN). It can provide secure, transparent, and multipoint connectivity between different sites. VPLS is commonly used in scenarios where organizations require the appearance of a single LAN across multiple locations.
- Software-Defined WAN (SD-WAN): SD-WAN is a technology that enables organizations to dynamically and intelligently route traffic across multiple network connections, such as MPLS, broadband, or cellular. While SD-WAN is primarily used for network optimization and cost efficiency, it can also incorporate security features, such as encryption and firewall capabilities, to secure the network traffic.
- Application Layer Gateways (ALG): ALGs are software components that operate at the application layer of the network stack. They can be used to add security features, such as protocol-specific parsing and inspection, to help secure application layer protocols. ALGs are commonly used in firewalls and network devices to provide additional security for specific applications or protocols.
These alternative solutions provide organizations with different options for securing their communication and data transmission. The choice of alternative depends on factors such as the specific use case, the level of security required, the compatibility with existing infrastructure, and the ease of implementation and management.
It’s worth noting that some of these alternatives, such as TLS and SSH, can also be used in conjunction with IPSec to provide additional layers of security for specific applications or requirements. Organizations may choose to implement a combination of these technologies to create a comprehensive and tailored security solution.
Ultimately, the selection of an alternative to IPSec should be based on a thorough evaluation of the organization’s needs, infrastructure, and security requirements, ensuring that the chosen solution aligns with the organization’s goals and provides the necessary protection for its communication and data.