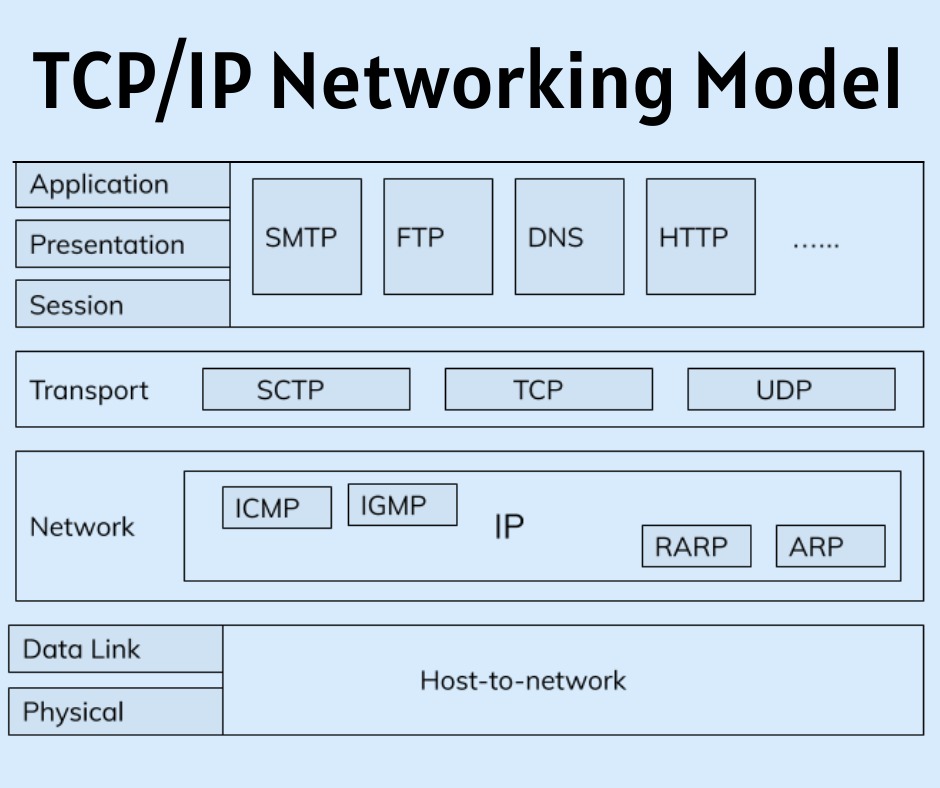
Overview of TCP/IP
TCP/IP (Transmission Control Protocol/Internet Protocol) is a set of protocols that allows computers to communicate with each other over a network. It is the foundation of the internet and is widely used in local area networks (LANs) and wide area networks (WANs).
The TCP/IP protocol suite consists of several layers that handle different aspects of network communication. At the lowest level is the Network Interface Layer, which defines the methods for transmitting data over a physical medium, such as Ethernet or Wi-Fi. The Internet Layer is responsible for addressing and routing packets across different networks. The Transport Layer ensures reliable delivery of data between applications running on different devices.
One of the key components of TCP/IP is the IP address, which uniquely identifies each device on a network. IP addresses are divided into two parts: the network portion and the host portion. Subnets allow for further division of IP addresses to efficiently manage network resources.
The TCP and UDP protocols operate on the Transport Layer of TCP/IP. TCP provides reliable, connection-oriented communication, making it suitable for applications that require data integrity, such as web browsing and email. UDP, on the other hand, is connectionless and best suited for applications that prioritize speed over reliability, such as streaming media and online gaming.
TCP/IP uses ports to enable communication between specific applications or services. Each application or service is assigned a unique port number, allowing packets to be directed to the appropriate destination. Sockets are used to establish and manage network connections between devices.
In addition to the core protocols, TCP/IP includes various auxiliary protocols such as Domain Name System (DNS), which translates domain names into IP addresses, and Dynamic Host Configuration Protocol (DHCP), which dynamically assigns IP addresses to devices on a network. Other protocols, like Address Resolution Protocol (ARP), Reverse Address Resolution Protocol (RARP), and Internet Control Message Protocol (ICMP), handle tasks such as address resolution, error reporting, and network diagnostics.
Routing and forwarding are essential aspects of TCP/IP networking. Routers use routing tables to determine the best path for forwarding packets between networks. Network Address Translation (NAT) is a technique that allows multiple devices to share a single public IP address.
Security is a critical concern in network communication, and TCP/IP provides mechanisms for securing data transmission. IPsec (IP Security) provides encryption and authentication to protect data at the network layer. Virtual Private Networks (VPNs) use IPsec to create secure connections between remote networks or devices over the internet.
When troubleshooting TCP/IP networking issues, it is essential to understand the various tools and techniques available, such as using network diagnostic utilities like ping and traceroute, analyzing network traffic with packet sniffers, and checking device configurations.
The future of TCP/IP is promising, as it continues to evolve to meet the growing needs of network communication. New technologies like IPv6, which offers a larger address space and improved security features, are being gradually implemented to ensure the continued growth and efficiency of the internet.
The TCP/IP Protocol Stack
The TCP/IP protocol stack is a layered approach that defines the communication protocols used in TCP/IP networking. It provides a structured framework for organizing and implementing the various protocols involved in transmitting data over a network.
At the lowest layer of the TCP/IP protocol stack is the Network Interface Layer. This layer defines the physical connection methods and standards for transmitting data over a physical medium, such as Ethernet cables or wireless signals. It specifies how the data is encoded and decoded, and it handles tasks like framing and error detection.
Above the Network Interface Layer is the Internet Layer, which is responsible for addressing and routing packets across different networks. The Internet Protocol (IP) is the primary protocol of this layer. It provides logical addressing through IP addresses and handles packet routing based on network topology. IP is connectionless and operates independently of the specific network technology being used.
The Transport Layer sits above the Internet Layer and is responsible for ensuring reliable delivery of data between applications running on different devices. It offers two main protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). TCP provides a reliable, connection-oriented service that ensures data integrity and ordered delivery. UDP, on the other hand, is connectionless and provides a faster, but less reliable, service.
Above the Transport Layer is the Application Layer, which includes various protocols that enable specific services or applications to communicate over a network. Some common protocols found in this layer include HTTP (Hypertext Transfer Protocol) for web browsing, SMTP (Simple Mail Transfer Protocol) for email transmission, and FTP (File Transfer Protocol) for file transfers.
The TCP/IP protocol stack is often represented as a vertical arrangement of these layers, with each layer building upon the services provided by the layer below it. This organization allows for modular design and easy modification or replacement of individual protocols without affecting the others. It also promotes interoperability between various hardware and software implementations.
By using a layered approach, the TCP/IP protocol stack allows for flexibility and scalability in network communications. It also simplifies the process of adding new protocols and services as technology evolves.
Overall, the TCP/IP protocol stack provides a comprehensive framework for network communication by dividing the complex task into manageable layers. Each layer performs specific functions, ensuring the reliable transmission of data across networks. This layered architecture has been instrumental in the success and widespread adoption of TCP/IP as the underlying protocol suite for the internet and modern networking.
Understanding IP Addresses and Subnets
In TCP/IP networking, IP addresses are used to uniquely identify devices on a network. An IP address consists of a series of numbers separated by periods, such as 192.168.0.1. This addressing scheme allows data to be directed to the correct destination in a network.
IP addresses are divided into two parts: the network portion and the host portion. The network portion identifies the specific network to which a device belongs, while the host portion identifies the individual device on that network.
IP addresses can be classified into different classes based on the range of possible values in the network portion. Classes A, B, and C are the most commonly used. Class A addresses have a large range of network addresses, allowing for a significant number of hosts on each network. Class B addresses have a more limited network range but can still accommodate a substantial number of hosts. Class C addresses are used for smaller networks.
Subnetting is a technique used to divide large IP address ranges into smaller, more manageable subnetworks. It allows for efficient utilization of IP addresses and facilitates network management. By using subnet masks, devices on a network can determine which portion of an IP address represents the network and which portion represents the host.
A subnet mask is a numerical value that is used in conjunction with an IP address to determine the network and host portions. It consists of a series of 1’s followed by a series of 0’s. The 1’s in the subnet mask indicate the network portion, while the 0’s represent the host portion.
For example, a subnet mask of 255.255.255.0 means that the first three octets of the IP address are part of the network portion, while the last octet is used to identify individual hosts. This allows for up to 254 hosts on the network.
Subnetting also enables network administrators to implement security measures and control network traffic more effectively. By dividing a network into smaller subnets, it becomes easier to manage and isolate specific groups of devices.
Understanding IP addresses and subnets is crucial for network administrators and IT professionals. It allows them to design and configure networks efficiently, allocate IP addresses effectively, and troubleshoot network issues.
The Internet Layer: IP Protocol
The Internet Protocol (IP) is a key protocol in the TCP/IP networking suite. It operates at the Internet Layer and is responsible for addressing and routing packets across different networks.
The primary function of IP is to provide logical addressing for devices on a network. An IP address is a unique numerical identifier assigned to each device connected to a network. It consists of a series of numbers separated by periods, such as 192.168.0.1. IP addresses are divided into two parts: the network portion and the host portion.
When a device wants to send data to another device on a different network, IP is responsible for routing the data packets to the appropriate destination. IP accomplishes this by using routing tables and protocols to determine the best path for packet delivery across interconnected networks. It takes into consideration factors such as network congestion, link availability, and network distance to ensure efficient and reliable packet transmission.
IP operates in a connectionless manner, meaning it does not establish a direct connection before transmitting data. Instead, each packet is addressed individually and can travel different routes to reach its destination. This approach allows for flexibility and scalability in network communication.
One of the notable features of IP is its ability to handle fragmentation and reassembly of data packets. When a packet is too large to be transmitted over a network without being fragmented, IP divides it into smaller packets. At the receiving end, IP reassembles the fragments into the original packet before delivering it to the higher-layer protocols.
There are two main versions of IP in use today: IPv4 and IPv6. IPv4 is the older version and uses a 32-bit address format, allowing for approximately 4.3 billion unique addresses. With the rapid growth of the internet and the depletion of available IPv4 addresses, IPv6 was introduced. IPv6 utilizes a 128-bit address format, providing an abundance of unique addresses to accommodate the expanding number of connected devices.
IP is a fundamental protocol in TCP/IP networking and plays a crucial role in enabling the communication of devices across different networks. It ensures the effective addressing, routing, and delivery of data packets, allowing for seamless connectivity and the global reach of the internet.
The Transport Layer: TCP and UDP
The Transport Layer in the TCP/IP protocol suite is responsible for ensuring reliable delivery of data between applications running on different devices. It offers two main protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
TCP is a connection-oriented protocol that provides reliable, ordered delivery of data packets. It establishes a connection between the sender and the receiver before transmitting data, ensuring that packets arrive in the correct order and without errors. TCP achieves this reliability through mechanisms such as error detection, acknowledgement of received packets, and retransmission of lost packets. It is commonly used for applications that require data integrity, such as web browsing, email, and file transfers.
UDP, on the other hand, is a connectionless protocol. It does not establish a connection before transmitting data, and it does not provide guaranteed delivery or ordered packets. UDP is faster and more lightweight than TCP since it lacks the overhead associated with reliability mechanisms. It is best suited for applications that prioritize speed over reliability, such as streaming media, online gaming, and real-time communication.
One of the key features of TCP is its ability to handle flow control. Flow control ensures that a sender does not overwhelm a receiver with data by regulating the rate of data transmission. TCP uses a windowing mechanism where the receiver informs the sender about its available buffer space, allowing for efficient data transfer without packet loss or congestion.
Another important aspect of TCP is its congestion control mechanism. It aims to prevent congestion in the network by adjusting the transmission rate based on the perceived network congestion. TCP monitors network conditions and dynamically adjusts the sending rate to avoid overwhelming the network and ensure fair sharing of available bandwidth among all connections.
Unlike TCP, UDP does not implement flow control or congestion control mechanisms. It simply sends packets as quickly as possible, without any guarantees of delivery or maintaining a specific order. While this lack of reliability makes UDP less suitable for certain applications, it offers lower latency and overhead, making it ideal for real-time or time-sensitive applications where speed is crucial.
Both TCP and UDP use ports to enable communication between specific applications or services. Each application or service is assigned a unique port number, allowing packets to be directed to the appropriate destination. Sockets, which are a combination of IP address and port number, are used to establish and manage network connections between devices.
TCP/IP Ports and Sockets
In TCP/IP networking, ports and sockets are used to enable communication between specific applications or services running on different devices. They play a crucial role in the transmission and reception of data packets within the TCP/IP protocol suite.
Ports are numerical identifiers that allow network devices to differentiate between different services or applications. They act as endpoints for communication, allowing data to be directed to the appropriate application or service running on a device.
There are two types of ports in TCP/IP: well-known ports and dynamic ports. Well-known ports range from 0 to 1023 and are assigned to specific services or protocols. For example, port 80 is commonly used for HTTP (Hypertext Transfer Protocol) web browsing, while port 25 is reserved for SMTP (Simple Mail Transfer Protocol) email transmission. Well-known port numbers are standardized and ensure that different devices can recognize and communicate with each other using the same port numbers.
Dynamic ports, also known as ephemeral or private ports, range from 1024 to 65535. These ports are used for temporary connections and are dynamically assigned by the operating system or application when needed. When a client device initiates a communication with a server device, it selects a random or available dynamic port for the connection.
Sockets, on the other hand, are a combination of an IP address and port number. They allow for the establishment and management of network connections between devices. When a client device wants to communicate with a server device, it creates a socket that includes the IP address of the server and the port number associated with the desired service or application.
A socket acts as a communication endpoint, enabling the client and server devices to send and receive data packets. The client’s socket initiates the connection by sending a request to the server’s socket, and if the server accepts the connection, a communication channel is established.
Data is exchanged between the client and server through the established socket connection. The client’s socket sends data packets to the server’s socket, and the server responds by sending its own data packets back to the client. This bidirectional communication enables the exchange of information between applications running on different devices.
Ports and sockets are vital in TCP/IP networking, facilitating the communication between applications and services. They allow for the identification and differentiation of data streams, ensuring that data is directed to the intended destination. By utilizing the combination of IP addresses and port numbers, TCP/IP enables efficient and reliable communication across networks.
DNS in TCP/IP Networking
The Domain Name System (DNS) is a critical component of TCP/IP networking that enables the translation of domain names into IP addresses. Instead of relying solely on numerical IP addresses, DNS allows users to access websites or services using easy-to-remember domain names, such as example.com, rather than complex IP addresses like 192.168.0.1.
When a user enters a domain name into a web browser or attempts to access a network resource, the DNS system is responsible for resolving the domain name to its corresponding IP address. This process involves several steps:
1. DNS Query: The client device sends a query to a DNS server, typically provided by the Internet Service Provider (ISP) or configured within the network. The query specifies the desired domain name.
2. DNS Recursive Resolution: If the DNS server does not have the IP address corresponding to the domain name in its cache, it initiates a recursive resolution process. It begins by contacting the root DNS servers, which provide information on the Top-Level Domains (.com, .org, .net, etc.).
3. DNS Hierarchy: The DNS server then queries the Top-Level Domain (TLD) servers to obtain the authoritative DNS server for the specific domain, such as the DNS server for example.com.
4. Authoritative Resolution: The authoritative DNS server is contacted to retrieve the IP address associated with the requested domain name. This server holds the authoritative information for the specific domain and provides the IP address back to the client.
5. DNS Response: The DNS server responds to the client’s original query with the resolved IP address, allowing the client to establish a connection to the desired domain or network resource.
DNS not only translates domain names to IP addresses but also plays a crucial role in managing various other record types, such as mail exchange (MX) records for email routing, canonical name (CNAME) records for aliasing domain names, and others, providing a flexible and comprehensive system for managing and resolving names within the TCP/IP networking infrastructure.
By using DNS, users can access websites, send emails, or connect to network resources using easy-to-remember domain names, without the need to remember complex IP addresses. DNS greatly simplifies the process of locating and connecting to resources on the internet, enhancing the usability and accessibility of TCP/IP networks.
DHCP in TCP/IP Networking
The Dynamic Host Configuration Protocol (DHCP) is a fundamental component of TCP/IP networking that simplifies the assignment of IP addresses to devices on a network. It provides a dynamic and automated process for configuring network settings, eliminating the need for manual configuration of IP addresses.
With DHCP, a dedicated server or router, known as a DHCP server, is responsible for leasing IP addresses to devices on the network. When a device connects to the network, it sends a DHCP request message, requesting an IP address assignment from the DHCP server.
The DHCP server manages a pool of available IP addresses and assigns one of these addresses to the requesting device. Along with the IP address, the DHCP server can also provide additional configuration information, such as the subnet mask, default gateway, DNS server addresses, and other network settings.
The DHCP client, which is the device requesting an IP address, will accept the assigned IP address and configuration parameters provided by the DHCP server. It configures its network interface using the assigned information, allowing it to communicate on the network and access network resources.
DHCP operates on a lease-based system, meaning that IP address assignments are temporary and have an expiration time. The DHCP client must periodically renew its IP address lease by contacting the DHCP server. If the lease expires without renewal, the IP address is returned to the available pool and can be reassigned to other devices.
DHCP offers several advantages in TCP/IP networking:
1. Simplified Network Configuration: DHCP eliminates the need for manual IP address configuration, making it easier and more efficient to set up and manage large networks with multiple devices. It reduces the likelihood of address conflicts and configuration errors.
2. Centralized IP Address Management: With DHCP, IP address assignment is centralized and controlled by the DHCP server. This allows for better management and allocation of IP addresses, ensuring efficient utilization of available addresses.
3. Dynamic Resource Allocation: DHCP allows for dynamic allocation of IP addresses. Devices that are not connected or in use can release their IP addresses back to the DHCP server, making them available for other devices as needed.
4. Configuration Flexibility: In addition to IP address assignment, DHCP can provide other network configuration parameters, such as subnet masks, default gateways, and DNS server addresses, ensuring devices are properly configured with all necessary networking information.
DHCP is widely used in TCP/IP networking, especially in larger networks where manual IP address assignment would be impractical. It streamlines the process of IP address configuration, reduces administrative overhead, and promotes efficient network operations.
ARP and RARP in TCP/IP Networking
Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP) are essential protocols in TCP/IP networking that help devices resolve and map IP addresses to MAC addresses and vice versa.
ARP is used when a device wants to discover the MAC address associated with a specific IP address on the same network. When a device needs to send data to another device, it first checks if it has the MAC address of the destination device in its ARP cache. If not, it will send an ARP request broadcast message to the network, asking for the MAC address corresponding to the IP address it wants to communicate with.
The devices on the network receive the ARP request and compare it to their own IP addresses. When a matching IP address is found, the device responds with an ARP reply, providing its MAC address. The requesting device can then update its ARP cache with the MAC address and use it to encapsulate the data and send it to the correct destination on the network.
RARP, on the other hand, is used when a device wants to discover its IP address by using its MAC address. In certain scenarios, such as diskless workstations or machines without any preconfigured network settings, a device with only the MAC address needs to request its IP address from a server.
The device sends a RARP request broadcast message on the local network, including its MAC address. The RARP server, which maintains a mapping of MAC addresses to IP addresses, receives the request and responds by sending a RARP reply, providing the IP address associated with the requesting MAC address. The device can then configure itself with the received IP address, allowing it to participate in network communication.
ARP and RARP are vital in TCP/IP networking as they enable devices to communicate and establish connections at the data link layer using MAC addresses, regardless of the underlying IP addressing scheme. These protocols facilitate the efficient resolution of addresses, which is crucial for proper packet forwarding and delivery in a network.
Today, ARP and RARP are widely supported and used in Ethernet-based TCP/IP networks. They provide the necessary mechanisms for devices to determine the correct MAC and IP addresses, allowing for seamless communication and efficient data transmission.
ICMP in TCP/IP Networking
The Internet Control Message Protocol (ICMP) is an integral part of the TCP/IP networking suite. It is a network layer protocol that allows devices to communicate and exchange control messages concerning network connectivity and communication issues.
ICMP is primarily used for diagnostic and error reporting purposes. It provides a means for devices to send error messages back to the sender, notifying them of various network-related issues. These messages help to identify and troubleshoot problems in TCP/IP networking.
One of the main functions of ICMP is to handle error reporting. When a network problem occurs, such as an unreachable host or a time-to-live (TTL) exceeded error, ICMP sends informative error messages back to the originating device. These messages help identify the issue and assist in the resolution of network connectivity problems.
ICMP also supports a range of messages used for network diagnostics, such as echo requests and echo replies. The most common example of this is the “ping” utility, which uses ICMP echo request messages to test the reachability and response time of a network host. The host that receives the echo request responds with an echo reply message.
In addition to error reporting and diagnostics, ICMP is also responsible for handling network congestion notifications using ICMP congestion control messages. These messages alert devices to network congestion and assist in adjusting transmission rates to avoid further congestion issues, improving overall network performance.
ICMP works closely with other protocols in the TCP/IP suite. For example, when a router receives an ICMP message indicating an unreachable destination, it may generate an Internet Control Message Protocol Redirect message, informing the sender of a better route to the destination. This allows for efficient routing and better utilization of network resources.
Overall, ICMP plays a crucial role in TCP/IP networking by providing essential messaging and reporting capabilities. It aids in network troubleshooting, error detection and reporting, network diagnostics, and congestion control. ICMP messages allow devices to communicate critical information about network issues, ensuring efficient and reliable transmission of data across TCP/IP networks.
Routing and Forwarding in TCP/IP Networking
Routing and forwarding are vital processes in TCP/IP networking that enable the transfer of data packets across networks. These processes ensure that packets are correctly routed and delivered to their intended destinations, allowing for efficient communication between devices.
Routing involves determining the optimal path for packet transmission between networks. Routers are the network devices responsible for making routing decisions based on the destination IP addresses of packets. They use routing tables, which contain information about network topologies and available routes, to determine the best path to forward packets. Routing protocols, such as OSPF (Open Shortest Path First) and BGP (Border Gateway Protocol), help routers exchange routing information and update their routing tables dynamically.
Each packet that travels across a network is examined by routers, which analyze the destination IP address and consult their routing tables. Based on this information, routers determine the next hop or interface through which the packet should be forwarded. This process is repeated at each router along the path until the packet reaches its final destination network.
For the actual transmission of packets, routers use a process called forwarding. Forwarding involves the physical movement of packets from one network interface to another, according to the routing decisions made. Routers maintain tables known as forwarding tables, which map destination IP addresses to corresponding network interfaces.
When a packet arrives at a router, the router consults its forwarding table to determine the appropriate outgoing interface for the packet. The packet is then encapsulated in a new frame and forwarded to the next hop router along the determined path. This process continues until the packet reaches its destination network.
Efficient routing and forwarding are critical for optimal network performance. Routing algorithms and protocols ensure that packets take the most efficient paths, avoiding congestion and minimizing delays. The forwarding process ensures that packets are efficiently transmitted through network interfaces and delivered to the intended destinations, enabling successful communication between devices.
In addition to traditional routing, there is also the concept of default routing. When a router does not have a specific route to a destination in its routing table, it can use a default route, also known as the gateway of last resort. The default route specifies the next-hop router to which packets should be sent if no other specific routes match the destination IP address. Default routing is commonly used to handle traffic directed to destinations outside of a particular network or subnet.
Overall, routing and forwarding are essential mechanisms in TCP/IP networking that enable efficient and reliable packet delivery. They ensure that data packets are correctly routed between networks and accurately forwarded to their intended destinations, facilitating seamless communication and interaction within the TCP/IP network infrastructure.
Network Address Translation (NAT) in TCP/IP Networking
Network Address Translation (NAT) is a technique used in TCP/IP networking to enable devices on a private network to communicate with devices on the public internet using a shared public IP address. NAT plays a crucial role in addressing limitations and optimizing the use of IP addresses.
In a private network, such as a home or office network, devices are assigned private IP addresses that are not accessible from the internet. These private IP addresses are unique within the local network but cannot be used for direct communication outside of the network. To establish communication with devices on the internet, NAT is used to map private IP addresses to a single or a pool of public IP addresses.
When a device from a private network initiates a connection to the internet, NAT modifies the source IP address in the outgoing packets to the public IP address associated with the NAT device. This process is known as source NAT or masquerading. When the response packets from the internet arrive, the NAT device identifies the internal private IP address that the packet is intended for and modifies the destination IP address accordingly before forwarding the packet to the appropriate device on the private network. This process is known as destination NAT or port forwarding.
NAT provides several benefits:
1. IP Address Conservation: NAT allows multiple devices on a private network to share a single public IP address, effectively conserving valuable public IP addresses.
2. Enhanced Security: By utilizing NAT, devices on a private network are not directly exposed to the public internet. This adds a layer of security by concealing the private IP addresses and making them inaccessible from outside the network.
3. Seamless Integration: NAT enables devices with private IP addresses to communicate with devices on the public internet, providing seamless integration between the private network and the broader internet.
4. Load Balancing: NAT can distribute incoming internet traffic across a pool of public IP addresses, allowing for load balancing and improved performance for connected devices.
There are different types of NAT, including static NAT, dynamic NAT, and Port Address Translation (PAT). Static NAT involves manually mapping specific private IP addresses to corresponding public IP addresses. Dynamic NAT dynamically assigns public IP addresses from a pool to private IP addresses. PAT is a specific type of dynamic NAT where multiple private IP addresses are mapped to a single public IP address using different ports.
NAT is widely used in many network environments, including home networks, small office networks, and large corporate networks. It enables efficient utilization of public IP addresses and provides a level of security by obscuring private IP addresses from external networks while allowing for seamless communication between devices on the private network and the internet.
IPsec and VPNs in TCP/IP Networking
IPsec (IP Security) and Virtual Private Networks (VPNs) are integral components of TCP/IP networking that provide secure and private communication over public networks such as the internet. They play a crucial role in ensuring the confidentiality, integrity, and authenticity of transmitted data.
IPsec is a set of protocols and security measures that operate at the network layer of the TCP/IP protocol stack. It provides encryption, data integrity, and authentication mechanisms to protect the privacy and security of IP communications. IPsec can be used to secure both individual communications between two devices (host-to-host), as well as entire networks (network-to-network).
IPsec operates in two main modes: tunnel mode and transport mode. In tunnel mode, the entire IP packet is encapsulated within a new IP packet, adding a layer of encryption and authentication. This mode is commonly used in VPNs to establish secure connections between remote networks. In transport mode, IPsec protects the data payload of IP packets while leaving the original IP headers intact, typically used for securing end-to-end communications between individual devices.
VPNs are virtual private networks that leverage IPsec (among other protocols) to create secure, private connections over public networks. A VPN extends a private network across a public network, such as the internet, allowing remote users or branch offices to securely access resources on the private network as if they were directly connected to it.
When a device establishes a VPN connection, it creates a secure tunnel using IPsec. This tunnel encrypts all data transmitted between the device and the VPN gateway or server, ensuring that it remains confidential and protected from eavesdropping or unauthorized access. VPNs also use authentication mechanisms to verify the identity of devices before allowing access to the private network.
VPNs provide numerous benefits:
1. Secure Remote Access: VPNs allow remote users to securely access resources on a private network from anywhere, providing a secure extension of the corporate network to remote employees or traveling employees.
2. Site-to-Site Connectivity: VPNs establish secure connections between multiple networks, enabling seamless connectivity and secure communication between different offices or branches of an organization.
3. Cost Savings: VPNs allow organizations to utilize public networks, such as the internet, instead of expensive dedicated private networks, resulting in cost savings without compromising security.
4. Enhanced Data Security: By encrypting data transmitted over the VPN, VPNs ensure the confidentiality and integrity of sensitive information, protecting it from unauthorized access or interception.
IPsec and VPNs are widely used in various industries to establish secure and private communication channels. They provide the necessary security mechanisms to protect sensitive data and facilitate remote access to resources, making them essential components of TCP/IP networking in today’s interconnected and globalized world.
Troubleshooting TCP/IP Networking Issues
TCP/IP networking is robust and reliable, but issues can arise that disrupt connectivity and communication. When faced with TCP/IP networking problems, troubleshooting techniques can help identify and resolve the root cause of the issues.
Here are some common troubleshooting steps to address TCP/IP networking issues:
1. Check Physical Connections: Ensure that all physical network connections, such as Ethernet cables or wireless connections, are properly connected and functional. Physical damage or loose connections can result in network connectivity problems.
2. Verify IP Configuration: Check the IP configuration of the devices involved. Ensure that each device has a valid IP address, subnet mask, default gateway, and DNS server addresses configured correctly. Incorrect or mismatched IP configurations can lead to connectivity issues.
3. Ping and Traceroute: Use network diagnostic utilities like ping and traceroute to test connectivity and identify potential network bottlenecks or failures. Ping can verify if a device is reachable, while traceroute provides information about the route packets take to reach a destination, helping identify any problematic hops.
4. Analyze Network Traffic: Use packet sniffers or network analyzer tools to capture and analyze network traffic. These tools can help identify anomalies, errors, or excessive network traffic that may be causing communication issues.
5. Verify DNS Resolution: Check the DNS resolution by using the nslookup or dig commands to ensure that domain names are being correctly resolved to IP addresses. DNS misconfigurations can result in inability to access websites or services.
6. Firewall and Security Settings: Review firewall and security settings on devices and network infrastructure. Incorrectly configured firewalls or security policies can block or restrict network communication, causing connectivity problems.
7. Review Routing Tables: Check the routing tables on devices, particularly routers, to ensure that routes are properly configured and packets are being routed correctly. Incorrect routing configurations can lead to traffic being directed to the wrong destinations.
8. Firmware and Software Updates: Ensure that devices have the latest firmware and software updates installed. Outdated or buggy software can cause compatibility issues or security vulnerabilities that impact network connectivity.
9. Verify Hardware Compatibility: Check the compatibility of network hardware, such as network interface cards (NICs) or routers, to ensure they are compatible with the TCP/IP protocol suite. Incompatibilities can cause communication problems.
10. Consult Documentation and Support: Refer to device documentation, user manuals, or online support resources specific to the devices or networking equipment being used. Manufacturers often provide troubleshooting guides or support forums that can offer insights and solutions to common networking issues.
By following these troubleshooting steps, network administrators and IT professionals can identify and resolve TCP/IP networking issues effectively, ensuring stable and reliable network communication.
The Future of TCP/IP
TCP/IP has been the backbone of internet communication for decades, but as technology advances and networking requirements evolve, the future of TCP/IP is constantly being reimagined and enhanced to meet the changing needs of the digital world.
One notable development is the transition from IPv4 to IPv6. IPv4, with its limited address space, is becoming increasingly inadequate to support the growing number of connected devices. IPv6 provides a much larger address space, ensuring that there are enough unique IP addresses to accommodate the exponential growth of internet-connected devices. The transition to IPv6 is an ongoing process, and as it becomes more widely adopted, it will play a significant role in the future of TCP/IP networking.
Another area of innovation is in the field of network security. With the rise of cyber threats and the need for secure communication, enhancements in protocols like IPsec and VPN technologies will continue to evolve. There will be a greater focus on encryption, authentication, and confidentiality to ensure the security of data transmitted over TCP/IP networks.
As the demand for real-time and multimedia applications continues to grow, Quality of Service (QoS) mechanisms within TCP/IP will become more important. Efforts will be made to optimize network traffic management, prioritize certain types of communication, and minimize latency to provide a seamless user experience for applications such as streaming media, video conferencing, and online gaming.
The future of TCP/IP also lies in the continuous improvement of network performance and efficiency. Researchers are exploring technologies like Software-Defined Networking (SDN) and Network Function Virtualization (NFV), which aim to increase flexibility, scalability, and automation in network infrastructure management. These advancements will provide greater control and agility in configuring and managing TCP/IP networks.
IoT (Internet of Things) is another area where TCP/IP networking is expected to play a significant role. As more devices become connected, TCP/IP protocols will continue to enable seamless communication and interoperability among various IoT devices. IPv6’s larger address space will be crucial in supporting the massive number of IoT devices and enabling them to communicate efficiently.
Additionally, innovations in artificial intelligence and machine learning will likely impact TCP/IP networking. These technologies can be utilized to optimize routing protocols, predict network performance, and dynamically adjust network configurations to enhance efficiency and reliability.