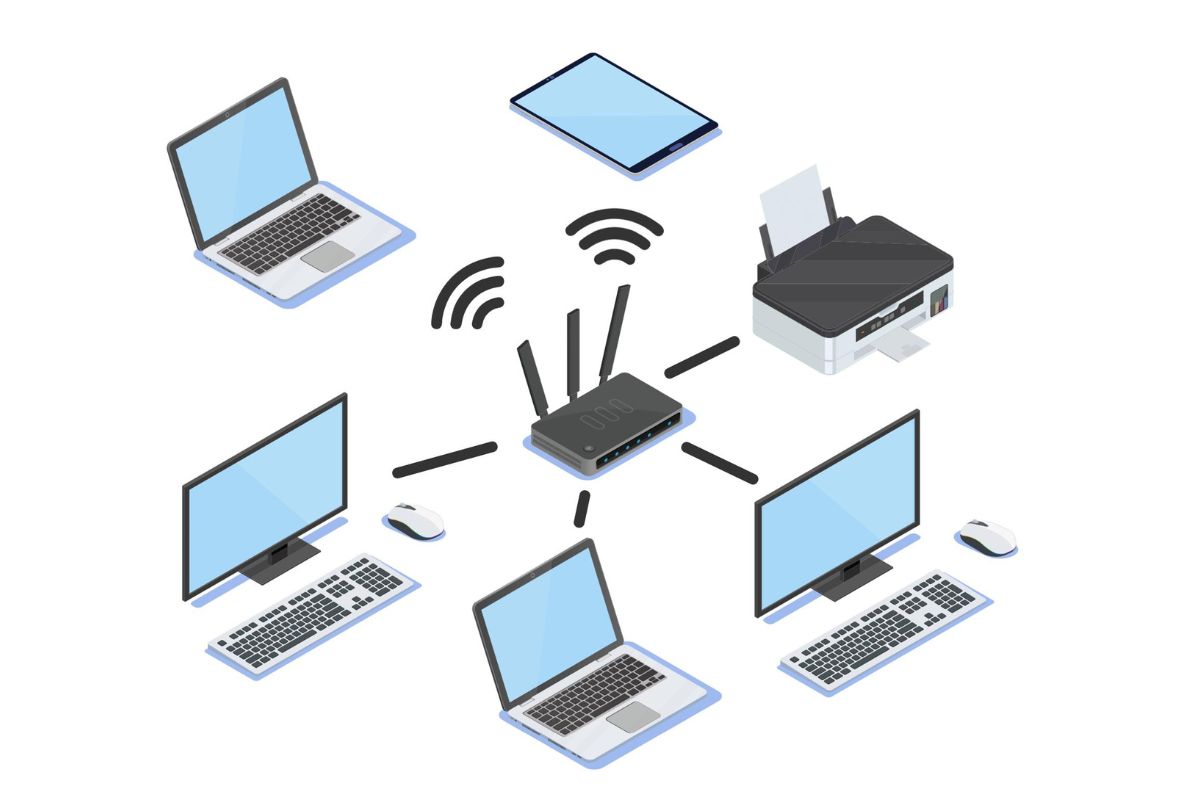
Definition of a Node
In computer networking, a node refers to any device or component that is connected within a computer network. It can be a computer, a server, a printer, a modem, a switch, a router, or any other device that has the ability to send, receive or transmit data over the network.
At its core, a node is essentially a connection point in a network. It acts as a communication endpoint that allows for the exchange of information between devices and users within the network. Each node has its own unique address, known as the Network Layer address or IP address, which helps in identifying and routing data packets to and from the respective device.
A node can vary in size, ranging from a simple handheld device to a complex server that hosts multiple services and applications. Regardless of its size or functionality, each node plays a crucial role in facilitating the flow of data across the network.
Nodes are interconnected through the use of cables, wireless connections, or a combination of both. These connections create a network infrastructure that enables communication and data transmission between the nodes. The network infrastructure can be local, such as a Local Area Network (LAN), or it can span over larger distances, like a Wide Area Network (WAN).
Nodes can be categorized into two main types: client nodes and server nodes. Client nodes are the devices that initiate requests and consume services provided by server nodes. They include personal computers, laptops, smartphones, and tablets. On the other hand, server nodes are the devices that provide services and respond to requests from client nodes. These can include web servers, email servers, file servers, and database servers.
Overall, nodes are the building blocks of a computer network, ensuring the efficient exchange of information and the seamless functioning of various network services. Understanding the concept of nodes is essential for anyone working with computer networks or anyone looking to optimize their network infrastructure.
Types of Nodes
In a computer network, there are various types of nodes that serve different functions and play distinct roles in the overall network infrastructure. Understanding these types of nodes can provide insights into how devices are connected and how information is transmitted within the network.
1. End-user Nodes: These nodes are also known as client nodes and are the devices used by individuals to access and consume network resources. Examples of end-user nodes include personal computers, laptops, smartphones, and tablets. These devices are the primary interface for users to interact with the network and access services provided by server nodes.
2. Server Nodes: Server nodes are responsible for providing services and responding to requests from client nodes. They are designed to handle specific tasks such as hosting websites, managing databases, or providing email services. Server nodes are typically more powerful than client nodes and are equipped with specialized hardware and software to handle the increased workload.
3. Network Infrastructure Nodes: These nodes are responsible for facilitating the transmission of data over the network. They include devices such as switches, routers, and modems. Switches enable the connection between multiple devices within a local network, allowing for the exchange of data packets. Routers, on the other hand, connect different networks and route the data packets between them. Modems are used to connect a network to the internet through a service provider.
4. Peripheral Nodes: Peripheral nodes are devices connected to the network that provide additional functionality or services. This includes printers, scanners, storage devices, and cameras. These nodes are often accessed and controlled by client nodes, allowing users to print documents, access files, or retrieve data from external devices.
5. Bridge Nodes: Bridge nodes function as a bridge or a connector between two different network segments. They assist in extending the network by connecting two or more networks that use different network protocols or technologies. This enables seamless communication and data exchange between otherwise separate network entities.
6. Gateway Nodes: Gateway nodes act as an entry point or exit point to another network. They serve as a portal between two networks with different protocols, enabling communication and data transfer between them. Gateways are commonly used to connect a local network to the internet or to link networks with different security protocols.
Each type of node plays a crucial role in the overall network infrastructure. By understanding the different types of nodes and their functions, network administrators can effectively design, configure, and maintain a robust and efficient computer network.
Functions of Nodes
Nodes in a computer network perform various functions to facilitate the communication and transmission of data within the network. These functions are essential for the smooth operation of the network infrastructure and the efficient exchange of information between devices. Here are some of the key functions of nodes:
1. Data Processing: Nodes, particularly server nodes, are responsible for processing and managing data within the network. They can perform tasks such as data storage, retrieval, manipulation, and analysis. Server nodes often host applications and services that allow users to access and process data stored on the network.
2. Data Routing: One of the primary functions of network infrastructure nodes, such as routers and switches, is to route data packets to their intended destinations. These nodes analyze the destination IP address of the data packet and determine the optimal path for its delivery. They ensure that the data is efficiently and accurately transmitted across the network.
3. Resource Sharing: Nodes enable the sharing of network resources among different devices. For example, printers, storage devices, and scanners connected to the network can be accessed and used by multiple client nodes. Server nodes also provide services like file sharing, email, and application hosting, which enable resource sharing among users within the network.
4. Security and Access Control: Nodes play a crucial role in network security by implementing security measures and access control mechanisms. They enforce user authentication and authorization, ensuring that only authorized individuals can access sensitive data or network resources. Nodes also monitor and protect the network against cyber threats, such as malware, viruses, and unauthorized access attempts.
5. Communication and Collaboration: Nodes facilitate communication and collaboration among users within the network. Client nodes can send messages, emails, or participate in voice or video calls with other users. Server nodes host applications and services that enable real-time collaboration, such as document sharing, conferencing, and project management tools.
6. Network Management: Nodes are crucial for network configuration, monitoring, and management. Network administrators use specialized software and tools to monitor the performance and health of nodes, identify potential issues, and troubleshoot network problems. They configure and update nodes with the necessary settings to ensure efficient network operation and optimize performance.
By performing these functions, nodes contribute to the overall operation and efficiency of the computer network. Each node type has its own set of functions that collectively enable devices to communicate, share resources, and access services within the network.
Physical vs. Logical Nodes
In the realm of computer networking, nodes can be classified into two distinct categories: physical nodes and logical nodes. Understanding the difference between these two types is crucial for effectively managing and maintaining a network. Let’s explore each category in detail:
Physical Nodes: Physical nodes refer to the actual physical devices or components that make up the network infrastructure. These are tangible entities that can be physically touched and interacted with. Examples of physical nodes include computers, servers, routers, switches, printers, and other network devices. Physical nodes have their own individual physical addresses and are connected via cables, wires, or wireless connections.
Physical nodes are responsible for executing tasks related to data processing, storage, and transmission within the network. They have specific hardware configurations, processing power, memory capacity, and input/output capabilities. Physical nodes can be located within a single location, such as an office or data center, or they can be distributed across different geographical locations.
Logical Nodes: Logical nodes, on the other hand, are virtual representations or abstractions of physical nodes within a network. These nodes do not correspond to any specific physical device but are created for the purpose of organizing and managing network resources. Logical nodes are defined by their functions, roles, or services they provide within the network.
Examples of logical nodes include IP addresses, network interfaces, virtual LANs (VLANs), virtual machines (VMs), subnets, and network protocols. These nodes are created and configured through software and network settings. By defining logical nodes, network administrators can efficiently allocate resources, manage access control, and optimize network performance.
Logical nodes can also be used to represent groupings or collections of physical nodes. For instance, a logical node may represent a group of servers that collectively provide a specific service like email hosting or web hosting. This abstraction simplifies network administration by treating a group of physical nodes as a single logical entity.
The relationship between physical and logical nodes is interdependent. Logical nodes rely on physical nodes to execute their functions and utilize the underlying hardware resources. At the same time, physical nodes can be configured and grouped together to create logical nodes that serve specific purposes.
Understanding the distinction between physical and logical nodes is crucial for network design, management, and troubleshooting. By effectively leveraging both types of nodes, network administrators can create a robust and efficient network infrastructure that meets the organization’s needs.
Examples of Nodes in a Computer Network
A computer network consists of a diverse range of devices and components, each serving as a node to facilitate communication and data exchange. These nodes play vital roles in the network infrastructure, ensuring seamless connectivity and efficient transmission of information. Let’s explore some common examples of nodes found in a computer network:
1. Desktop and Laptop Computers: Personal computers, including both desktop and laptop computers, are common nodes in a network. These devices serve as end-user nodes, allowing individuals to access and utilize network resources, browse the internet, send/receive emails, and run various applications.
2. Servers: Server nodes are powerful computers designed to provide specialized services within the network. Examples include web servers that host websites, file servers that store and distribute files, database servers that handle data storage and retrieval, and mail servers that facilitate email communication.
3. Switches: Switches are network infrastructure nodes used to connect multiple devices within a local network. They enable the exchange of data packets between devices, ensuring efficient communication. Switches operate at the data link layer of the network and can be either managed or unmanaged.
4. Routers: Routers are critical nodes that connect different networks together. They transmit data packets across networks and determine the most efficient path for data transmission. Routers operate at the network layer of the network protocol stack and use routing tables to determine the next hop for data packets.
5. Wireless Access Points: Wireless access points (WAPs) enable wireless connectivity, allowing devices to connect to a network without the need for physical cables. WAPs act as nodes that provide wireless access to devices such as laptops, smartphones, and tablets.
6. Printers and Scanners: Peripheral nodes, such as printers and scanners, are commonly found in a network. These devices offer shared printing and scanning capabilities, allowing multiple devices to utilize the printing and scanning functionalities provided by the nodes.
7. Modems: Modems are nodes responsible for connecting a network to the internet through an Internet Service Provider (ISP). They convert digital signals from devices into analog signals that can be transmitted over telephone lines, cable lines, or fiber optic cables, allowing network communication with the broader internet.
8. Firewalls: Firewalls act as network security nodes that protect the network from unauthorized access and malicious activity. They monitor and control network traffic based on predefined security rules, ensuring that only legitimate and safe communication is allowed.
9. Virtual Machines (VMs): VMs are software-based nodes that run on physical computers. They enable the creation and operation of multiple virtual instances within a single physical device, allowing for efficient resource utilization and better scalability.
10. Network Attached Storage (NAS): NAS devices are specialized nodes that provide centralized storage and file sharing capabilities within a network. They are dedicated file servers designed to store and manage large volumes of data, serving as a central repository accessible to all authorized network users.
These are just a few examples of nodes that can be found in a computer network. Understanding the different types of nodes and their functions is essential for building and managing a reliable and efficient network infrastructure.
Importance of Nodes in a Computer Network
Nodes are the fundamental building blocks of a computer network, and their importance cannot be overstated. They play a crucial role in ensuring the connectivity, functionality, and efficiency of the network infrastructure. Here are some key reasons why nodes are essential in a computer network:
1. Communication and Data Exchange: Nodes facilitate communication and data exchange between devices within the network. They enable the seamless transfer of information, such as files, messages, and multimedia content, among users and applications. Without nodes, devices would be isolated and unable to share resources or collaborate effectively.
2. Resource Sharing: Nodes allow for the sharing of network resources, ensuring efficient utilization of hardware and services. Printers, storage devices, and other shared resources can be accessed and utilized by multiple nodes in the network. This promotes cost-effectiveness and improves productivity by eliminating the need for individual devices for every user.
3. Scalability and Flexibility: Nodes enable the network to scale and adapt to changing needs. Adding or removing nodes allows for the expansion or reconfiguration of the network infrastructure. This flexibility ensures that the network can accommodate new devices, services, and users as the organization grows or requirements change.
4. Centralized Management: Nodes provide a centralized point for network management. Network administrators can monitor, configure, and manage nodes to ensure optimal performance and security. Centralized management simplifies tasks such as software updates, user access control, and troubleshooting, making network administration more efficient.
5. Redundancy and Fault Tolerance: Nodes can be configured to provide redundancy and fault tolerance within the network. If one node fails, another node can take over to ensure uninterrupted service. Redundancy minimizes network downtime and enhances reliability, crucial for critical applications and services.
6. Security and Access Control: Nodes play a vital role in network security. They enforce authentication, authorization, and encryption mechanisms to protect sensitive data and resources. Firewalls, IDS/IPS systems, and access control systems implemented at nodes help safeguard the network from unauthorized access, data breaches, and cyber threats.
7. Performance Optimization: Nodes enable network administrators to optimize network performance. Through monitoring and analysis of node performance metrics, administrators can identify and address bottlenecks, optimize bandwidth allocation, and ensure efficient data transmission. This results in improved network speed, reduced latency, and enhanced overall performance.
8. Supporting Advanced Network Services: Nodes are crucial for the provision of advanced network services. Mail servers, web servers, DNS servers, and other specialized nodes enable functions like email communication, website hosting, domain name resolution, and virtual private networking. These services enhance collaboration, productivity, and user experience within the network.
Overall, nodes are the backbone of a computer network, enabling communication, resource sharing, scalability, security, and efficient utilization of network resources. Understanding the importance of nodes is essential for designing, managing, and optimizing a reliable and robust network infrastructure.
How Nodes Communicate in a Computer Network
Communication between nodes in a computer network is essential for the exchange of data and the functioning of various network services. Nodes employ specific protocols and techniques to transmit and receive information, ensuring efficient and reliable communication across the network. Here is an overview of how nodes communicate in a computer network:
1. Data Packets: Communication between nodes is organized into small units called data packets. These packets encapsulate data, along with control information such as source and destination addresses. Each packet contains a portion of the data being transmitted and is assigned a sequence number to ensure correct ordering during transmission.
2. Addressing: Each node in a network has a unique identifier known as an IP address. This address allows nodes to send and receive data to and from specific destinations. IP addresses can be either IPv4 or IPv6, and they play a vital role in routing data packets, ensuring they reach the correct destination.
3. Transmission Methods: Nodes in a network communicate through wired or wireless connections. Wired connections use cables, such as Ethernet cables, to transmit data. Wireless connections utilize wireless signals, typically using Wi-Fi or cellular networks. Both transmission methods follow specific protocols and standards to enable data transmission between nodes.
4. Data Link Layer: Nodes communicate at the data link layer of the network protocol stack. This layer is responsible for establishing a reliable connection between nodes and ensuring error-free data transmission. It also manages access to the shared network media, such as Ethernet or wireless channels, by using protocols like Ethernet or Wi-Fi protocols.
5. Network Layer: The network layer is responsible for routing data packets from the source to the destination node. Routers play a crucial role in this layer by examining the destination IP address of the data packet and determining the best path for forwarding the packet toward the destination. They use routing tables and algorithms to make these routing decisions.
6. Transport Layer: The transport layer manages the reliable and ordered delivery of data packets between nodes. It determines which protocol, such as TCP (Transmission Control Protocol) or UDP (User Datagram Protocol), is used for transmitting the data packets. TCP provides error checking, flow control, and congestion control, while UDP provides a connectionless and less reliable transmission.
7. Application Layer: Communication between nodes occurs through various network applications and services at the application layer. Nodes utilize application-layer protocols such as HTTP (Hypertext Transfer Protocol), SMTP (Simple Mail Transfer Protocol), FTP (File Transfer Protocol), and DNS (Domain Name System) to exchange data and interact with network services.
8. Protocols and Standards: Nodes follow specific protocols and standards for communication. The most widely used protocol suite is the TCP/IP (Transmission Control Protocol/Internet Protocol), which provides a set of guidelines and rules for data transmission and network communication. Other protocols, such as Ethernet, Wi-Fi, and DNS, also play important roles in facilitating communication between nodes.
By adhering to these communication mechanisms, nodes in a computer network can establish reliable connections, transmit data packets, and ensure efficient communication between devices. Understanding the different layers and protocols involved in network communication is crucial for designing, configuring, and troubleshooting computer networks.
Node Addressing in a Computer Network
In a computer network, node addressing is the process of assigning unique identifiers to individual nodes to facilitate communication and data transmission. These addresses enable nodes to send and receive data packets, ensuring that information reaches the correct destination within the network. Let’s explore the key aspects of node addressing in a computer network:
1. IP Addresses: The most common form of node addressing is through IP (Internet Protocol) addresses. An IP address is a unique numeric identifier assigned to each device connected to a network. It allows nodes to be identified and located within the network infrastructure. IP addresses can be either IPv4 (32-bit address) or IPv6 (128-bit address) formats, with each addressing a different number of devices.
2. IP Address Classes: IPv4 addresses are divided into different classes, denoted by the first octet of the address. Classes include A, B, C, D, and E, with each class providing a different range of IP addresses for allocation. The class determines the number of network and host bits in the IP address, influencing the maximum number of nodes that can be addressed within a network.
3. Private IP Addresses: To accommodate the increasing number of devices connected to networks, private IP addresses are used within local networks. These addresses are not directly accessible over the internet and include ranges specified by the Internet Assigned Numbers Authority (IANA), such as 192.168.x.x and 10.x.x.x. Private IP addresses allow for the reuse of address space within local network environments.
4. Subnetting: Subnetting involves dividing an IP address range into smaller subnetworks, known as subnets. This allows for efficient allocation of IP addresses and enables logical segmentation of a network into smaller manageable units. Subnetting improves network performance, security, and management by providing control over the flow of data within the network.
5. DNS (Domain Name System): While IP addresses are essential for network communication, they can be difficult to remember for humans. The DNS system translates human-friendly domain names, such as www.example.com, into their corresponding IP addresses. DNS provides a hierarchical naming structure that resolves domain names to the IP addresses of the nodes hosting the requested resources.
6. MAC Addresses: In addition to IP addresses, nodes also have unique MAC (Media Access Control) addresses at the data link layer. MAC addresses are assigned to network interface cards (NICs) and are used to identify devices within a local network. They are represented as a sequence of hexadecimal numbers and are globally unique, providing a hardware-based identification for nodes.
7. DHCP (Dynamic Host Configuration Protocol): DHCP is a network protocol that dynamically assigns IP addresses to nodes within a network. Instead of manually configuring IP addresses for each node, DHCP servers automate the assignment process. This simplifies network management and ensures efficient use of available IP address space.
Node addressing is crucial for network communication and data transmission. IP addresses, subnetting, DNS, MAC addresses, and DHCP are key components that enable nodes to establish connections, route data, and interact within the network. Understanding and properly configuring node addressing is essential for the smooth operation and scalability of a computer network.
Node Configuration and Management
Effective configuration and management of nodes in a computer network are crucial for ensuring optimal performance, security, and functionality. Properly configuring and managing nodes allows network administrators to control and monitor settings, troubleshoot issues, and maintain a stable and reliable network infrastructure. Here are the key aspects of node configuration and management:
1. Initial Configuration: When adding a new node to the network, initial configuration is required to set up the device for network connectivity. This involves configuring basic settings such as IP address assignment, subnet mask, default gateway, DNS servers, and other network-specific parameters. Initial configuration may also include setting up user accounts, passwords, and security settings.
2. Network Monitoring and Management: Network monitoring tools are used to oversee the health, performance, and security of nodes within the network. These tools provide real-time monitoring of node status, network traffic, bandwidth utilization, and other key parameters. Network management systems allow administrators to centrally manage and control node configurations, detect and resolve issues, and optimize network performance.
3. Security and Access Control: Nodes must be properly configured to ensure network security. Security measures such as firewall configurations, access control lists (ACLs), and user authentication mechanisms need to be implemented to protect nodes from unauthorized access and cyber threats. Regular updates, patches, and security policies must be enforced to mitigate vulnerabilities and ensure the integrity of the network.
4. Firmware and Software Updates: Nodes often require firmware and software updates to stay up-to-date with the latest features, bug fixes, and security patches. Regular updates ensure the stability, compatibility, and functionality of nodes within the network. Patch management systems can automate the process of updating nodes, ensuring that critical updates are applied promptly.
5. Backup and Disaster Recovery: Node configuration and management should include regular backup of critical configurations, settings, and data. This ensures that in case of node failure, data loss, or system crash, configurations can be easily restored. Backup solutions and disaster recovery plans should be implemented to mitigate the risk of data loss and ensure business continuity.
6. Documentation and Inventory: A comprehensive and up-to-date record of node configurations, settings, and network inventory is essential for efficient node management. Documentation should include details such as node IP addresses, MAC addresses, hardware specifications, software versions, and any relevant network configurations. This information aids in troubleshooting, monitoring, and planning future network upgrades.
7. Remote Management: Remote management capabilities allow administrators to configure, monitor, and troubleshoot nodes from a centralized location. Remote management tools enable tasks such as configuration updates, software installations, and troubleshooting without the need for physical access to the nodes. This simplifies network administration, increases efficiency, and minimizes downtime.
8. Performance Optimization: Node configuration can greatly impact network performance. Optimization techniques such as Quality of Service (QoS) settings, bandwidth management, and traffic shaping can be applied to prioritize critical traffic, ensure optimal network performance, and provide a better user experience. Regular assessment and fine-tuning of node configurations are essential to maintain optimal performance levels.
Proper node configuration and management are critical for the smooth operation of a computer network. From initial configuration to ongoing monitoring, security measures, and optimization, effective management ensures the stability, security, and performance of the network infrastructure.
Common Issues and Troubleshooting with Nodes in a Computer Network
Nodes in a computer network can encounter various issues that impact their performance, connectivity, and functionality. Troubleshooting these issues promptly is vital to minimize network downtime, ensure smooth operation, and maintain optimal network performance. Here are some common issues faced with nodes in a computer network and troubleshooting methods to address them:
1. Connectivity Issues: One common issue is when a node is unable to connect to the network or experiences intermittent connectivity. This can be caused by network cable faults, incorrect IP configuration, router or switch issues, or wireless signal interference. Troubleshooting may involve checking cable connections, resetting network devices, verifying IP configurations, or adjusting wireless channels and antennas.
2. Slow Network Performance: Nodes experiencing slow network performance can affect overall productivity. This issue can be caused by bandwidth congestion, network congestion, outdated hardware or software, or misconfigured QoS settings. Troubleshooting involves assessing network utilization, identifying bottlenecks, optimizing network configurations, and upgrading hardware or software as necessary.
3. IP Address Conflict: IP address conflicts occur when two nodes in the network have the same IP address assigned. This leads to communication issues and can result in network disruptions. Troubleshooting involves identifying the conflicting IP addresses, ensuring a unique IP address assignment, and updating DHCP configurations to prevent future conflicts.
4. DNS Resolution Issues: Nodes may encounter challenges resolving domain names or accessing internet resources due to DNS (Domain Name System) issues. This can be caused by misconfigured DNS settings, DNS server failures, or network connectivity problems. Troubleshooting involves checking DNS configurations, verifying DNS server availability, and performing DNS cache flushing or DNS server reconfiguration if necessary.
5. Hardware Malfunctions: Nodes may experience hardware malfunctions, leading to unexpected system failures or communication issues. Faulty network interface cards (NICs), defective cables, or malfunctioning switches can cause these problems. Troubleshooting involves isolating and replacing faulty hardware components, ensuring proper cable connections, or resetting switches to resolve the issue.
6. Security Breaches: Nodes can become vulnerable to security breaches, including malware infections, unauthorized access attempts, or data breaches. This can be due to weak passwords, outdated security software, or unpatched vulnerabilities. Troubleshooting includes updating security software, applying patches, strengthening access controls, and educating users on best security practices.
7. Software Compatibility Issues: Nodes may encounter compatibility issues with software applications, leading to errors or malfunctions. These issues can arise due to outdated software versions, incompatible software updates, or conflicts between different applications. Troubleshooting involves updating software to the latest versions, checking system requirements, and resolving any conflicting software installations.
8. Power and Connectivity Outages: Power outages or network connectivity failures can impact node functionality. These issues can be caused by electrical faults, network equipment failures, or external disruptions. Troubleshooting may involve checking power connections, resetting network devices, or contacting service providers to resolve outages or disruptions.
It is crucial to document and track these issues, including their resolution, to guide future troubleshooting efforts and identify recurring problems. Additionally, regular network maintenance, software updates, monitoring, and user education can help prevent many of these common issues from occurring in the first place.