The Basics of Networks
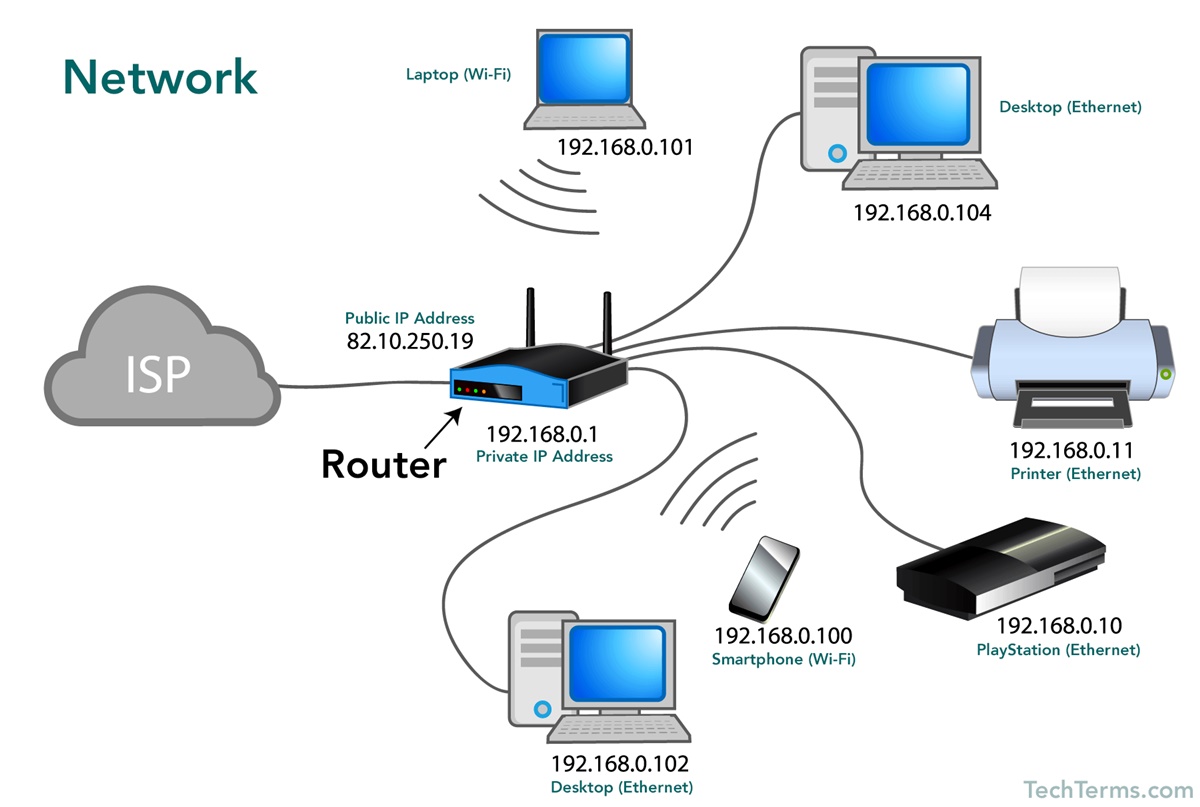
A network is a collection of interconnected devices, such as computers, servers, routers, and switches, that are designed to communicate with each other and share resources. It allows for the efficient transfer of data, information, and applications between devices, enabling users to collaborate, access information, and communicate effectively.
At its core, a network functions by establishing a connection between devices through various communication channels, such as wired or wireless connections. These connections can be physical, such as Ethernet cables, or virtual, such as Wi-Fi or cellular networks.
The fundamental purpose of a network is to facilitate the sharing of data and resources. This includes sharing files, printers, databases, and internet connectivity. By connecting devices together, networks enable users to access and utilize shared resources, promoting productivity and efficiency.
Networks can be classified based on their geographical scope:
- Local Area Networks (LANs): LANs cover a relatively small area, such as a home, office building, or campus. They are typically used by a single organization to connect their internal devices and resources.
- Wide Area Networks (WANs): WANs span large areas, such as cities, states, or even continents. They connect multiple LANs and are often used to connect multiple branches of a company or to provide internet connectivity to a larger area.
- Wireless Networks: Wireless networks utilize radio waves or infrared signals to connect devices without the need for physical cables. Wi-Fi networks, for example, allow devices to connect to a network wirelessly, providing flexibility and mobility.
In addition to geographical scope, networks can also be categorized based on their purpose or network architecture. Some common types include client-server networks, peer-to-peer networks, and hybrid networks that combine elements of both.
Understanding the basics of networks is essential for individuals and organizations alike. It allows us to harness the power of connectivity, enabling seamless communication and information sharing. Whether it’s a small LAN in a home or a complex WAN connecting offices around the world, networks play a crucial role in our modern digital world.
Types of Networks
There are various types of networks, each designed to serve different purposes and meet specific connectivity needs. Understanding the different types of networks can help in determining the most suitable network architecture for a particular situation or organization. Here are some common types:
- Local Area Networks (LANs): LANs are commonly used within homes, offices, or educational institutions. They connect devices within a relatively small area, enabling users to share resources such as files, printers, and internet connections. LANs typically use Ethernet cables or Wi-Fi for connectivity.
- Wide Area Networks (WANs): WANs cover larger geographical areas, spanning cities, states, or even continents. They connect multiple LANs and are commonly used by organizations with multiple branches. WANs utilize routers and leased lines or technologies like MPLS, VPNs, or the internet for connectivity.
- Wireless Networks: Wireless networks enable devices to connect to a network without the need for physical cables. Wi-Fi, Bluetooth, and cellular networks are examples of wireless networks. They provide flexibility and mobility, allowing users to access the network from different locations within the network’s coverage area.
- Client-Server Networks: In a client-server network, there are dedicated servers that provide services and resources to client devices. Clients request and consume resources from the servers. This architecture is common in organizations where centralized control and resource management are important.
- Peer-to-Peer Networks: In a peer-to-peer network, devices are equals and communicate directly with each other without the need for dedicated servers. Each device can act as both a client and a server, sharing resources and services with other devices. Peer-to-peer networks are commonly used for file sharing and collaboration.
- Hybrid Networks: Hybrid networks combine elements of both client-server and peer-to-peer architectures. They leverage the benefits of centralized control from client-server networks and the distributed nature of peer-to-peer networks. This type of network is often used in larger organizations with diverse connectivity requirements.
These are just a few examples of network types, and each type can be further customized to meet specific needs by selecting appropriate technologies and network components. It’s important to carefully consider the requirements and objectives before choosing the right network type.
Local Area Networks (LANs)
A Local Area Network (LAN) is a type of network that covers a relatively small area, such as a home, office building, or campus. LANs are designed to connect devices within the same geographical location, enabling efficient communication and resource sharing.
LANs are commonly used in various settings, including homes, small businesses, educational institutions, and government organizations. They provide numerous benefits, such as improved collaboration, resource sharing, and centralized management of devices and services.
Components of a LAN:
A LAN typically consists of the following components:
- Devices: These include computers, laptops, printers, servers, switches, and routers. Each device is connected to the LAN and has a unique IP address to facilitate communication.
- Network Interface Cards (NICs): NICs are hardware components that enable devices to connect to the LAN. They provide the necessary communication capabilities and allow devices to send and receive data over the network.
- Cables and Connectivity: LANs use Ethernet cables, such as Cat5e or Cat6, to establish physical connections between devices. These cables connect devices to switches or routers, creating a network infrastructure.
- Switches: Switches are used to connect multiple devices within a LAN. They provide a way for devices to communicate with each other by forwarding data packets to the intended recipient.
- Routers: Routers are essential for LANs that require connections to other networks, such as the internet or other LANs. They provide the necessary routing capabilities to direct network traffic between different networks.
- Network Protocols: LANs use various network protocols, such as Ethernet, TCP/IP, and IPv4 or IPv6, to ensure reliable data transmission and efficient network operations.
Advantages of LANs:
LANs offer several advantages:
- Resource Sharing: LANs allow for the sharing of resources such as files, printers, and internet connections. This enhances collaboration and productivity within the LAN.
- Centralized Management: With LANs, administrators have centralized control over network configuration, security, and access. This simplifies network management and improves security.
- High-Speed Data Transfer: LANs provide high-speed data transfer, allowing for fast and efficient communication between devices.
- Cost-Effectiveness: Setting up a LAN is generally more cost-effective than implementing a wide area network (WAN) for local connectivity needs.
Local Area Networks (LANs) play a crucial role in facilitating communication and resource sharing within small-scale environments. By connecting devices and enabling efficient data transfer, LANs enhance productivity and collaboration.
Wide Area Networks (WANs)
Wide Area Networks (WANs) are networks that span large geographical areas, connecting multiple Local Area Networks (LANs) together. They are designed to facilitate data transfer and communication between devices that are located far apart, such as different branch offices of a company or across different cities or countries.
WANs utilize various technologies and network infrastructure to establish connectivity between geographically dispersed locations. These networks are essential for organizations that require efficient and secure communication across multiple sites.
Components of a WAN:
Implementing a WAN involves several key components:
- Routers: Routers are crucial for WANs as they direct network traffic between different networks. They analyze and forward data packets to the appropriate destination across the WAN.
- Leased Lines: Leased lines are dedicated communication lines rented from a service provider, providing a direct and private connection between two or more locations. They offer consistent and reliable bandwidth but can be expensive.
- Virtual Private Networks (VPNs): VPNs create secure connections over public networks, such as the internet, by encrypting data and creating a virtual tunnel. This allows for secure communication between different locations over the WAN.
- Multiprotocol Label Switching (MPLS): MPLS is a routing technique used in WANs to efficiently manage data transmission. It assigns labels to packets, making it faster and more reliable for transmitting data.
- Cloud-based Services: Many WANs leverage cloud-based services to enhance connectivity and enable efficient data transfer across different locations. Cloud networking allows for flexibility and scalability in WAN deployments.
Advantages of WANs:
Wide Area Networks offer several benefits:
- Connectivity: WANs connect geographically dispersed locations, allowing organizations to share resources, data, and applications across multiple sites.
- Centralized Resource Management: WANs provide the ability to centrally manage resources and services, ensuring consistency and control across all connected sites.
- Secure Communication: Implementing VPNs in a WAN establishes secure connections for transmitting sensitive data, keeping it safe from unauthorized access.
- Improved Collaboration: WANs enable seamless communication and collaboration between employees, regardless of their physical location, leading to increased productivity and efficiency.
- Access to Centralized Services: WANs provide access to centralized services, such as centralized data storage, applications, and databases, ensuring data consistency and reducing duplication.
Wide Area Networks (WANs) are vital for organizations with a geographically distributed presence. By facilitating communication, resource sharing, and centralized management, WANs enable seamless collaboration and enhance connectivity across different sites.
Wireless Networks
Wireless networks, as the name suggests, enable devices to connect to a network without the need for physical cables. These networks utilize radio waves or infrared signals to transmit data, providing flexibility and mobility for users. Wireless networks have become increasingly prevalent, facilitating connectivity in various environments, such as homes, offices, public spaces, and even entire cities.
Types of Wireless Networks:
There are several types of wireless networks:
- Wi-Fi Networks: Wi-Fi (Wireless Fidelity) is the most common type of wireless network. It allows devices to connect to a local network or the internet wirelessly. Wi-Fi networks are widely available and commonly used in homes, offices, cafes, airports, and other public spaces.
- Bluetooth Networks: Bluetooth networks enable devices to connect and communicate with each other over short distances. It is commonly used for connecting peripherals, such as keyboards, mice, speakers, and other devices, to computers and smartphones.
- Cellular Networks: Cellular networks provide wireless connectivity over a wide area using cell towers. They allow devices such as smartphones, tablets, and IoT devices to connect to the internet through cellular data networks, enabling communication and data access on the go.
- Satellite Networks: Satellite networks use orbiting satellites to provide wireless communication over large areas, often in remote or rural locations where other forms of connectivity are limited. They are commonly used for internet access, telecommunication, and broadcasting.
Advantages of Wireless Networks:
Wireless networks offer several benefits:
- Flexibility and Mobility: Wireless networks allow users to connect and access the network without being constrained by physical cables. This provides the freedom to access information and resources from anywhere within the network’s coverage area.
- Convenience: Wireless networks eliminate the need for manually connecting devices with cables, making it convenient to connect and disconnect devices as needed.
- Scalability: Wireless networks can easily accommodate a growing number of devices without the need for extensive cabling infrastructure, providing scalability in terms of device connections.
- Simplified Installation: Setting up a wireless network is typically easier and less complex compared to wired networks, reducing installation time and costs.
- Improved Collaboration: Wireless networks enable seamless collaboration by allowing multiple users to connect and share resources and information simultaneously.
Wireless networks have revolutionized how we connect and access information in both personal and professional settings. With the increasing demand for mobility, wireless networks continue to evolve, providing faster speeds, broader coverage, and enhanced security to meet the needs of a connected world.
Network Components
A network is made up of various components that work together to enable communication and data transfer between devices. Understanding these network components is essential for managing, troubleshooting, and optimizing network performance. Here are some key components:
- Devices: The devices in a network include computers, servers, routers, switches, modems, and other hardware components. These devices are responsible for sending, receiving, and processing data within the network.
- Network Interface Cards (NICs): A Network Interface Card, also known as a network adapter, is a hardware component that enables devices to connect to a network. It provides the necessary interface and protocols for devices to transmit and receive data over the network.
- Cables and Connectors: Cables, such as Ethernet cables, fiber optic cables, or coaxial cables, are used to establish physical connections between devices in a network. Connectors, such as RJ45 or SC connectors, help to ensure a secure and proper connection between devices and cables.
- Switches: Switches are networking devices that facilitate the connection and communication between devices within a network. They direct network traffic by receiving data packets and forwarding them to the appropriate devices. Switches come in various sizes and configurations, including unmanaged switches for basic connectivity and managed switches with advanced features for more control and security.
- Routers: Routers are critical components that connect multiple networks together, such as connecting a LAN to the internet or linking different LANs within a Wide Area Network (WAN). They analyze network traffic and determine the most efficient path for data transmission. Routers use IP addresses to identify and route data packets.
- Firewalls: Firewalls are security devices that protect networks from unauthorized access and malicious activities. They monitor and filter network traffic, enforcing security policies to safeguard the network and its resources.
- Wireless Access Points (WAPs): Wireless Access Points are devices that enable wireless connectivity in a network. They transmit and receive wireless signals, allowing devices to connect to the network without the need for physical cables. WAPs are commonly used in wireless LANs (WLANs).
- Network Protocols: Network protocols define the rules and procedures for communication within a network. Common protocols include TCP/IP, Ethernet, Wi-Fi, DNS, HTTP, and HTTPS. These protocols ensure that data is transmitted accurately and efficiently across the network.
These are just some of the key components that make up a network infrastructure. Each component plays a vital role in ensuring reliable and efficient data transfer, connectivity, and security within the network. Understanding these components is essential for building, maintaining, and troubleshooting networks of all sizes and complexities.
Network Protocols
Network protocols are sets of rules and standards that govern the communication and data exchange between devices in a network. These protocols define how devices connect, transmit, receive, and interpret data, ensuring reliable and efficient communication across networks. Understanding network protocols is crucial for building and maintaining functional and interoperable networks. Here are some common network protocols:
- TCP/IP: Transmission Control Protocol/Internet Protocol (TCP/IP) is the foundation of modern internet communication. It provides a suite of protocols that enable data transmission between devices over the internet. TCP establishes connections and ensures reliable delivery of data, while IP handles the addressing and routing of data packets.
- Ethernet: Ethernet is a widely-used protocol for local area networks (LANs) and provides a standard for wired network connections. It defines the rules for data transmission over Ethernet cables, specifying how devices communicate, detect collisions, and handle data transfer.
- Wi-Fi: Wi-Fi protocols, such as 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac, govern wireless network connections. These protocols define the communication standards for wireless transmission, including data rates, frequencies, and security measures.
- DNS: The Domain Name System (DNS) protocol translates domain names into IP addresses, enabling users to access websites using user-friendly domain names instead of numeric IP addresses. DNS servers store and provide the information needed to map domains to their respective IP addresses.
- HTTP and HTTPS: The Hypertext Transfer Protocol (HTTP) is used for transmitting web pages and other resources over the internet. HTTPS is a secure version of HTTP that adds encryption and ensures secure data transmission between the web server and the client.
- POP and IMAP: Post Office Protocol (POP) and Internet Message Access Protocol (IMAP) are protocols used for email retrieval. POP retrieves emails from a mail server and stores them on the client device, while IMAP allows for remote access and management of emails stored on the mail server.
- SMTP: Simple Mail Transfer Protocol (SMTP) is a protocol used for sending email messages between servers. SMTP defines how email servers communicate and transfer messages over the internet.
- SNMP: The Simple Network Management Protocol (SNMP) is used for network management and monitoring devices within a network. It allows network administrators to collect information, monitor network performance, and manage devices remotely.
These are just a few examples of network protocols that play critical roles in enabling communication and data transfer across networks. Each protocol serves specific functions in different layers of the network architecture, ensuring compatibility, reliability, and security in network communication.
Network Topologies
Network topologies define the physical or logical layout of a network, determining how devices are connected and communicate with each other. Understanding network topologies is essential for designing, implementing, and managing networks effectively. Here are some common network topologies:
- Bus Topology: In a bus topology, devices are connected to a single central cable, known as a bus. Each device taps into the bus, and data is transmitted along the bus to all connected devices. This topology is simple and cost-effective but can be limited in terms of scalability and fault tolerance.
- Star Topology: In a star topology, devices are connected to a central hub or switch using separate cables. All data traffic passes through the central hub, which facilitates communication between devices. The star topology allows for easy scalability and fault isolation, but a failure of the central hub can disrupt the entire network.
- Ring Topology: In a ring topology, devices are connected in a closed loop or ring. Each device is connected to its adjacent devices, forming a unidirectional data path. Data circulates around the ring until it reaches the intended recipient. The ring topology provides equal access to all devices but can be susceptible to network disruptions if a single device or cable fails.
- Mesh Topology: In a mesh topology, devices are connected to each other in a network where every device has a point-to-point connection with every other device. Mesh topologies can be full mesh, where every device is directly connected to every other device, or partial mesh, where only some devices have direct connections. Mesh topologies provide high redundancy and fault tolerance but require more cabling and configuration.
- Tree Topology: A tree topology, also known as a hierarchical topology, consists of multiple networks connected in a hierarchical structure. It uses a root node connected to multiple child nodes, forming a tree-like structure. This topology is commonly used in larger networks, such as organizational networks, as it allows for easy scalability and management.
- Hybrid Topology: A hybrid topology combines multiple topologies to create a customized network design that suits specific requirements. For example, a network may use a combination of star and mesh topologies to achieve scalability, fault tolerance, and efficient communication in different parts of the network.
Each network topology offers advantages and limitations in terms of scalability, fault tolerance, cost, and ease of management. The choice of network topology depends on factors such as the size of the network, the intended use, budget, and the specific needs of the organization or environment in which it is implemented.
Network Security
Network security is essential for protecting data, devices, and communication from unauthorized access, threats, and vulnerabilities. It encompasses various measures and technologies that ensure the confidentiality, integrity, and availability of network resources. Implementing robust network security measures is critical for maintaining the privacy and security of sensitive information. Here are some key aspects of network security:
- Firewalls: Firewalls form the first line of defense in network security. They monitor and control incoming and outgoing network traffic based on predetermined security policies, protecting the network from unauthorized access and malicious attacks.
- NAT: Network Address Translation (NAT) adds an extra layer of security by hiding internal IP addresses from external networks. It allows multiple devices within a network to share a single public IP address, reducing the exposure of internal devices to potential threats.
- Encryption: Encryption technology, such as Secure Socket Layer/Transport Layer Security (SSL/TLS), encrypts data to ensure secure transmission over the network. Encryption scrambles data, making it unreadable to unauthorized individuals, and can be used for securing sensitive information like passwords and financial transactions.
- Access Control: Implementing strong access controls is vital in network security. This includes user authentication mechanisms like passwords, two-factor authentication (2FA), and access control lists (ACLs) that define who can access specific network resources.
- Intrusion Detection System (IDS)/Intrusion Prevention System (IPS): IDS and IPS monitor network traffic, detecting and responding to suspicious or malicious activity. IDS detects potential threats, while IPS actively blocks and mitigates such threats to protect the network.
- Vulnerability Management: Regularly scanning and assessing the network for vulnerabilities is crucial in network security. Vulnerability management includes identifying, patching, and updating systems to protect against known vulnerabilities and emerging threats.
- Network Segmentation: Network segmentation is the practice of dividing a network into smaller subnetworks to enhance security. By separating sensitive resources or departments from the rest of the network, potential security breaches can be contained, reducing the impact on the entire network.
- Network Monitoring: Continuous monitoring of network traffic and system logs helps in detecting and responding to security incidents. Monitoring tools track network activity, identify anomalies, and provide real-time alerts to potential security breaches.
- Employee Education and Awareness: Educating employees about best security practices, such as strong password management, identifying phishing attempts, and exercising caution while accessing network resources, is vital in maintaining network security.
Implementing a comprehensive network security strategy involves a layered approach that combines multiple security measures and technologies. By prioritizing network security, organizations can safeguard their sensitive data, prevent unauthorized access, and mitigate potential risks and vulnerabilities.
Network Administration
Network administration involves the management, operation, and maintenance of computer networks to ensure their optimal performance, security, and reliability. Network administrators play a crucial role in designing, implementing, and troubleshooting networks, as well as overseeing network infrastructure and user support. Here are some key aspects of network administration:
- Network Planning and Design: Network administrators are responsible for planning and designing network architectures that meet the organization’s requirements. This includes determining the network topology, selecting appropriate network components, and addressing scalability and future growth needs.
- Network Configuration and Implementation: Network administrators configure network devices such as routers, switches, and firewalls to establish connectivity and ensure proper data transmission. They also deploy and configure network services, such as DHCP, DNS, and VPNs, to provide essential network functionality.
- Network Monitoring and Performance Optimization: Network administrators monitor network performance, traffic patterns, and resource utilization to identify and resolve bottlenecks or issues. They use monitoring tools to track network health, analyze network traffic, and optimize network performance for better efficiency.
- Network Security Management: Network administrators implement and manage security measures to protect network infrastructure and data from unauthorized access and threats. This includes configuring firewalls, implementing encryption, enforcing access controls, and conducting security audits to ensure compliance with industry standards and best practices.
- Network Troubleshooting and Issue Resolution: When network issues arise, network administrators analyze and diagnose the problems, employing troubleshooting techniques and tools to identify the root cause and implement solutions. They are responsible for resolving issues quickly to minimize downtime and restore network functionality.
- User Support and Training: Network administrators provide user support, assisting with network-related issues, troubleshooting connectivity problems, and addressing user inquiries. They may also conduct training sessions to educate users on network usage, security protocols, and best practices.
- Configuration Management: Network administrators maintain an inventory of network devices, firmware versions, and configurations to ensure consistency and control. They manage network device configurations, implement changes, and maintain documentation to facilitate efficient network administration and troubleshooting.
- Backup and Disaster Recovery: Network administrators perform regular backups of network data and develop disaster recovery plans to mitigate the potential impact of network outages or data loss. They test and execute recovery strategies to ensure business continuity in the event of a network failure or disaster.
Network administration requires technical expertise in networking technologies, protocols, and tools. It also demands strong problem-solving skills, attention to detail, and the ability to adapt and keep up with evolving network trends and security threats. Efficient network administration ensures the smooth and secure operation of computer networks, enabling organizations to leverage the full potential of their network infrastructure.
Cloud Networking
Cloud networking refers to the practice of establishing and managing network connections and services in a cloud computing environment. With cloud networking, organizations can leverage the scalability, flexibility, and cost-effectiveness of cloud infrastructure to enhance their network capabilities. It offers numerous benefits compared to traditional on-premises networking. Here are some key aspects of cloud networking:
- Virtualized Network Infrastructure: Cloud networking allows organizations to virtualize and abstract their network infrastructure. Virtual networking components, such as virtual routers, switches, and firewalls, can be provisioned and managed dynamically, providing on-demand network resources based on business needs.
- Elasticity and Scalability: Cloud networking enables organizations to easily scale their network resources up or down based on fluctuating demands. With cloud services, network bandwidth, storage, and computing capacity can be adjusted dynamically to accommodate changing workloads and user requirements.
- Global Network Accessibility: Cloud networking eliminates the limitations of traditional on-premises networks by providing global accessibility. Organizations can establish network connections and services across geographically dispersed locations, enabling users to access resources and data from anywhere in the world.
- Software-Defined Networking (SDN): SDN is a key component of cloud networking that separates the network control plane from the underlying physical infrastructure. It allows for centralized network management, policy enforcement, and automation, making network configuration and provisioning more efficient and agile.
- Multi-Cloud Networking: Cloud networking enables organizations to connect and integrate multiple cloud environments, public or private, into a cohesive network infrastructure. This provides the ability to leverage different cloud services and resources from various providers while maintaining connectivity and data consistency.
- Network Security and Compliance: Cloud networking includes built-in security features and allows organizations to implement comprehensive security measures. Cloud service providers offer robust security controls, encryption, and compliance certifications to protect network traffic, data, and user access.
- Cost Optimization: Cloud networking offers cost optimization benefits by reducing the need for upfront investment in physical networking hardware and the associated maintenance costs. Organizations can pay for the network resources they consume on a flexible, pay-as-you-go basis, aligning expenses with actual usage.
- Integration with Cloud Services: Cloud networking seamlessly integrates with other cloud services, such as cloud storage, compute instances, and serverless computing. This allows for efficient data transfers, application deployments, and the creation of hybrid architectures that combine on-premises and cloud resources.
Implementing cloud networking requires organizations to assess their networking needs, adopt appropriate cloud networking technologies, and work with cloud service providers or network service partners to configure, deploy, and manage their cloud network infrastructure. With cloud networking, organizations can achieve greater agility, scalability, and cost-efficiency while leveraging the vast computing and networking resources offered by cloud providers.
Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) are secure and encrypted connections established over public networks, such as the internet, to enable secure communication and data transfer. VPNs provide a private and protected pathway for transmitting data, allowing organizations and individuals to access network resources remotely with enhanced security. Here are some key aspects of VPNs:
- Secure Data Transmission: VPNs encrypt data, encapsulating it within a secure tunnel, which helps protect sensitive information from interception and unauthorized access. Encryption ensures that data remains confidential and secure during transmission.
- Remote Access: VPNs allow authorized users to securely access a private network from remote locations. This enables employees, partners, or clients to connect to internal resources, such as files, applications, and databases, as if they were directly connected to the private network.
- Identity and Authentication: VPNs authenticate users before granting them access to the private network. This ensures that only authorized individuals can establish a VPN connection and access network resources, enhancing network security and preventing unauthorized access.
- Privacy and Anonymity: By masking the user’s IP address and encrypting network traffic, VPNs provide privacy and anonymity. This is especially important when accessing the internet from public Wi-Fi networks or when dealing with sensitive data and information.
- Geo-spoofing and Bypassing Restrictions: VPNs allow users to mask their location by connecting to servers located in different regions. This can help bypass geographically-based restrictions and access content or services that may be blocked or limited in their actual location.
- Business and Enterprise Use: VPNs are commonly used by organizations to establish secure connections between remote offices, employees working from home, or traveling employees. VPNs enable secure data transfer, facilitate remote collaboration, and ensure encrypted communication within the organization’s private network.
- Types of VPNs: There are several types of VPNs, including site-to-site VPNs, which connect multiple networks together, and client-to-site VPNs, which allow individual devices or users to access a network remotely. VPNs can be implemented using different protocols such as IPsec, SSL/TLS, or OpenVPN.
- Trustworthiness of VPN Services: When using VPN services provided by external providers, it is crucial to choose trusted providers. A reputable VPN service should have strong encryption, a “no-logs” policy, transparent privacy practices, and robust security measures to ensure the confidentiality and integrity of data transmission.
VPNs are essential tools for ensuring secure and private communication over public networks. Whether for personal use or business needs, VPNs provide a secure and encrypted connection that allows users to access network resources remotely while maintaining data confidentiality and privacy.
Internet of Things (IoT) Networks
Internet of Things (IoT) networks are a collection of interconnected devices, sensors, and objects that communicate and exchange data with each other over the internet. IoT networks enable smart automation, remote monitoring, and control of various physical objects and environments. The proliferation of IoT devices has brought about new opportunities and challenges in network connectivity and management. Here are some key aspects of IoT networks:
- Device Connectivity: IoT networks consist of a wide variety of devices, including sensors, actuators, wearables, and smart appliances. These devices connect to the network using various wireless communication protocols, such as Wi-Fi, Bluetooth, Zigbee, or cellular networks.
- Data Collection and Analysis: IoT devices continuously collect and transmit vast amounts of data, often in real-time. This data is then analyzed to derive insights, make informed decisions, and automate processes. Cloud computing and edge computing technologies are often utilized to handle the massive scale and processing requirements of IoT data.
- Interoperability: IoT networks involve devices and sensors from different manufacturers, each utilizing their own protocols and standards. Interoperability becomes crucial to ensure seamless communication and integration among devices. Standardization efforts, such as IoT protocols like MQTT and CoAP, aim to address this challenge.
- Scalability and Network Infrastructure: As the number of connected IoT devices continues to grow, IoT networks require scalable and resilient network infrastructure to accommodate the increasing demand. This includes robust Wi-Fi and cellular networks, as well as the adoption of technologies like IPv6 to support the vast number of devices.
- Security and Privacy: IoT networks introduce new security and privacy concerns due to the vast amount of sensitive data being transmitted and the potential vulnerabilities of IoT devices. Network administrators must implement strong security measures, including encryption, authentication, and access controls, to protect IoT networks from cyber threats.
- Analytics and Automation: IoT networks leverage data analytics and automation to enable intelligent decision-making and automate processes. Real-time analytics, machine learning, and AI algorithms are applied to IoT data to derive valuable insights and trigger automated actions or alerts.
- Industry Applications: IoT networks have extensive applications across industries. Examples include smart homes, industrial automation, healthcare monitoring, agriculture, transportation, and smart cities. IoT networks enable increased efficiency, improved productivity, and enhanced decision-making capabilities in these domains.
- Challenges: Deploying and managing IoT networks presents several challenges, including network complexity, device compatibility, data security, privacy concerns, and the need for skilled administrators. Addressing these challenges requires a comprehensive approach that considers the unique characteristics and requirements of IoT networks.
Internet of Things (IoT) networks are transforming industries and revolutionizing the way objects and devices interact and communicate. With continued advancements in connectivity, data analytics, and network infrastructure, IoT networks have the potential to deliver significant value and innovation in various domains.
The Future of Networks
The field of networking is constantly evolving, driven by advancements in technology and the increasing demands of our digital world. The future of networks holds numerous exciting possibilities and trends that will shape the way we connect and communicate. Here are some key aspects to consider:
- 5G and Beyond: The rollout of 5G technology is set to revolutionize network connectivity with faster speeds, lower latency, and increased bandwidth. 5G networks will enable a wide range of applications, including immersive virtual reality, autonomous vehicles, and smart cities. Beyond 5G, technologies like 6G are already being explored and hold the potential to take network speeds and capabilities even further.
- Edge Computing: Traditional cloud computing relies on centralized data centers, but edge computing brings computing power closer to the source of data generation. With edge computing, data processing and analysis happen at the network edge, reducing latency and enabling real-time decision-making. This will be particularly important for applications requiring low latency, such as autonomous vehicles and augmented reality.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML will play a significant role in enhancing network management and optimization. AI-powered algorithms can automate network operations, detect anomalies, and predict and mitigate network issues. ML algorithms can also analyze network data to optimize network performance and improve security.
- Software-Defined Networks (SDN): SDN will continue to gain traction, offering centralized control and programmability of network infrastructures. SDN technology will simplify network management and enable agile network provisioning, reducing the reliance on manual configurations and enhancing network flexibility.
- Internet of Things (IoT) Expansion: The IoT will continue to expand, connecting billions of devices and creating vast amounts of data. Networks will need to be optimized to handle the influx of IoT devices and the associated data, resulting in increased demand for scalable and secure IoT networking solutions.
- Network Security Enhancements: As cyber threats evolve, network security will remain a top priority. Network security measures will become more sophisticated, incorporating advanced threat detection, enhanced encryption protocols, and automated response systems to proactively defend against emerging threats.
- Virtualization and Network Function Virtualization (NFV): Virtualization will become even more prevalent, allowing for the creation of virtual networks and the dynamic allocation of network resources. NFV will play a key role in optimizing network performance and reducing hardware dependence by virtualizing network functions, such as firewalls and routers.
- Quantum Networking: Quantum networking is an emerging field that leverages the principles of quantum physics to enhance network security and communication. Quantum encryption can provide unhackable communication channels, while quantum teleportation may enable instantaneous data transfer across vast distances.
The future of networks holds immense potential for innovation and advancements that will shape our digital world. From faster and more reliable connectivity to intelligent network management and secured communication, ongoing developments in networking technologies will unlock new possibilities and transform how we connect, collaborate, and experience the digital realm.