What is a VPN and Why Do You Need It?
In today's digital age, online security is a paramount concern for individuals and businesses alike. With the increasing prevalence of cyber threats and privacy breaches, the need for robust protective measures has never been more critical. This is where a Virtual Private Network (VPN) comes into play.
A VPN serves as a secure tunnel between your device and the internet, encrypting the data transmitted and shielding it from prying eyes. By rerouting your internet connection through a remote server, a VPN effectively masks your IP address and location, thereby enhancing your online anonymity and privacy.
Why Do You Need It?
-
Enhanced Security: When you connect to public Wi-Fi networks, such as those in cafes, airports, or hotels, your data becomes vulnerable to interception by malicious actors. A VPN encrypts your internet traffic, safeguarding it from potential eavesdropping and cyber attacks.
-
Privacy Protection: Internet service providers (ISPs) and other entities may track and log your online activities. With a VPN, your browsing history and online behavior are shielded from prying eyes, preserving your privacy and anonymity.
-
Access to Restricted Content: Certain websites and online services may be geo-blocked or restricted based on your location. By using a VPN, you can bypass these restrictions and access region-locked content, such as streaming services and websites, from anywhere in the world.
-
Secure Remote Access: For professionals working remotely, a VPN provides a secure means of accessing corporate networks and sensitive data, mitigating the risks associated with unsecured connections.
-
Protection Against Surveillance: In regions where internet censorship and surveillance are prevalent, a VPN empowers users to circumvent such restrictions and communicate freely without the fear of monitoring or censorship.
In essence, a VPN is a versatile tool that not only fortifies your online security and privacy but also grants you the freedom to access the internet without constraints. Whether you're concerned about safeguarding sensitive data, evading geo-restrictions, or preserving your digital anonymity, integrating a VPN into your online repertoire is a prudent and proactive step towards a safer and more liberated online experience.
How to Activate VPN on iPhone 13
Activating a VPN on your iPhone 13 is a straightforward process that empowers you to fortify your online security and privacy. Follow these simple steps to enable a VPN on your device:
-
Accessing VPN Settings: Begin by navigating to the "Settings" app on your iPhone 13. This can be easily located on your home screen and is represented by a gear icon. Tap on the "Settings" icon to proceed.
-
Selecting VPN: Within the "Settings" menu, scroll down and tap on the "VPN" option. This will lead you to the VPN configuration page, where you can manage and set up your VPN connections.
-
Adding a VPN Configuration: To add a new VPN configuration, tap on the "Add VPN Configuration" option. Here, you will be prompted to enter the relevant details provided by your VPN service provider, including the type of VPN (e.g., IKEv2, IPSec, or L2TP), server information, and authentication credentials.
-
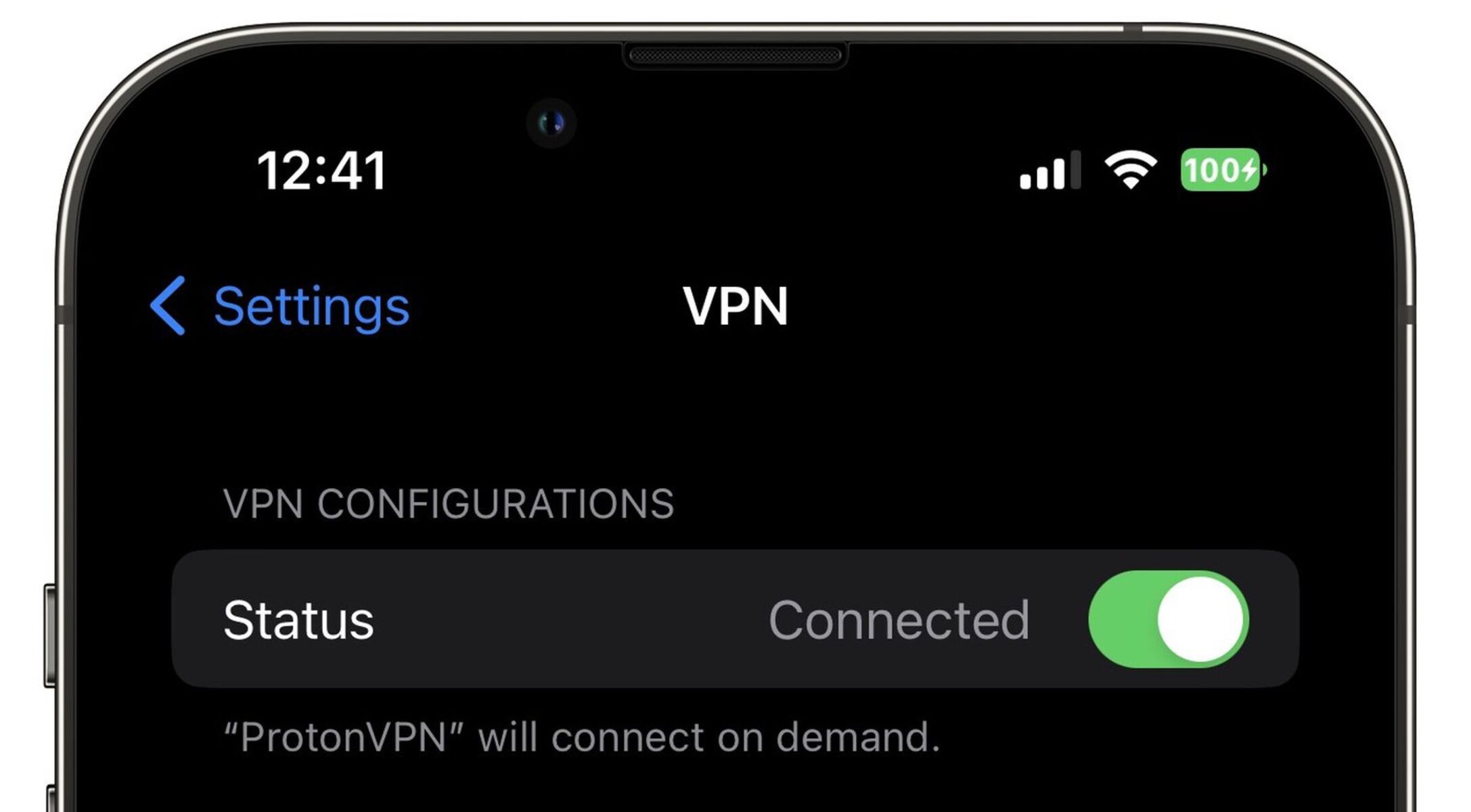
Configuring VPN Settings: After entering the necessary details, tap on the "Done" button to save the VPN configuration. You can then toggle the VPN switch to activate the connection. Once enabled, the VPN icon will appear in the status bar at the top of your iPhone screen, indicating that the VPN is active and your internet traffic is being securely routed through the VPN server.
-
Verifying VPN Connection: To ensure that the VPN is functioning as intended, you can visit a website or use an online tool to verify your IP address and location. With the VPN active, your IP address should reflect the location of the VPN server rather than your actual location.
-
Managing VPN Connections: Additionally, the "Settings" app allows you to manage multiple VPN configurations if you have subscriptions to multiple VPN services. You can easily switch between different VPN connections or modify the settings of existing configurations as needed.
By following these steps, you can seamlessly activate a VPN on your iPhone 13, bolstering your online security and privacy with encrypted internet traffic and enhanced anonymity. Whether you're connecting to public Wi-Fi networks, accessing geo-restricted content, or safeguarding sensitive data, leveraging a VPN on your iPhone 13 is a proactive measure towards a more secure and liberated online experience.
Choosing the Right VPN Provider
Selecting the right VPN provider is a pivotal decision that significantly impacts the efficacy of your online security and privacy measures. With a myriad of options available in the market, it's essential to discern the key factors that distinguish a reliable VPN provider. Here's a comprehensive guide to help you navigate the process of choosing the right VPN provider for your specific needs:
1. Security and Encryption Protocols
A reputable VPN provider prioritizes robust security measures, including advanced encryption protocols such as AES-256, OpenVPN, or IKEv2, to safeguard your data from unauthorized access. Look for providers that employ secure tunneling protocols and have a strict no-logs policy, ensuring that your online activities remain private and protected.
2. Server Network and Locations
The extent and diversity of a VPN provider's server network play a crucial role in determining the accessibility and performance of the service. Opt for a provider with a broad global server coverage, encompassing diverse geographic locations. This not only facilitates bypassing geo-restrictions but also ensures optimal connection speeds and reliability.
3. User-Friendly Interface and Cross-Platform Compatibility
A user-friendly VPN interface and seamless compatibility across various devices and operating systems enhance the overall user experience. Look for VPN providers that offer intuitive applications for iOS, Android, Windows, macOS, and other platforms, enabling effortless integration and usage across your devices.
4. Privacy and Logging Policies
Prioritize VPN providers with transparent privacy policies and a commitment to maintaining minimal to no user logs. A trustworthy provider should uphold a strict no-logs policy, refraining from storing any identifiable user information or browsing history, thereby preserving your digital privacy and anonymity.
5. Speed and Performance
While encryption and security are paramount, a VPN should also deliver commendable connection speeds and minimal latency. Opt for providers that offer high-speed servers and employ technologies to mitigate performance degradation, ensuring a seamless and responsive browsing and streaming experience.
6. Customer Support and Reliability
Reliable customer support is indispensable when evaluating VPN providers. Look for providers offering responsive customer service, including live chat support, comprehensive knowledge bases, and troubleshooting resources. Additionally, consider the provider's uptime and reliability to ensure consistent and uninterrupted VPN connectivity.
7. Pricing and Subscription Plans
Evaluate the pricing structure and subscription plans offered by VPN providers, considering factors such as the number of simultaneous connections, additional features, and the availability of trial periods or money-back guarantees. Seek a balance between affordability and the comprehensive feature set offered by the provider.
By meticulously assessing these key considerations, you can make an informed decision when selecting a VPN provider that aligns with your specific security, privacy, and accessibility requirements. Prioritizing a reputable and trustworthy VPN provider empowers you to fortify your online defenses and enjoy a secure, unrestricted, and private internet experience.
Additional Security Measures for Online Protection
In addition to leveraging a VPN for bolstering online security and privacy, implementing supplementary security measures further fortifies your digital defenses and mitigates potential risks. These additional measures serve as proactive safeguards against a spectrum of cyber threats, encompassing data breaches, malware infections, and identity theft. By integrating the following security practices into your online routine, you can enhance your resilience against evolving cyber threats and safeguard your digital assets effectively.
1. Multi-Factor Authentication (MFA)
Enabling multi-factor authentication across your online accounts adds an extra layer of security by requiring multiple forms of verification to access your accounts. This typically involves a combination of passwords, biometric authentication, or one-time codes, significantly reducing the likelihood of unauthorized access, even if your credentials are compromised.
2. Regular Software Updates and Patch Management
Consistently updating your device's operating system, applications, and security software is imperative for addressing known vulnerabilities and mitigating the risk of exploitation by cybercriminals. Timely installation of security patches and updates bolsters the resilience of your devices against emerging threats and potential security loopholes.
3. Strong and Unique Passwords
Employing strong, complex, and unique passwords for each of your online accounts is fundamental in thwarting unauthorized access. Consider utilizing reputable password managers to generate and store intricate passwords, minimizing the susceptibility to credential-based attacks and unauthorized account infiltration.
4. Phishing Awareness and Email Security
Educating yourself and your peers about phishing tactics and exercising caution when interacting with unsolicited emails and links is pivotal. Vigilance against phishing attempts and email scams mitigates the risk of falling victim to fraudulent schemes and malicious content, thereby fortifying your digital resilience.
5. Endpoint Security and Antivirus Protection
Deploying robust endpoint security solutions and reputable antivirus software across your devices safeguards against malware, ransomware, and other malicious threats. Regular scans and real-time protection mechanisms fortify your devices against potential infections and unauthorized access attempts.
6. Encrypted Communication Channels
Utilizing encrypted communication channels, such as secure messaging applications and email encryption tools, enhances the confidentiality and integrity of your digital communications. Encryption mitigates the risk of unauthorized interception and eavesdropping, preserving the privacy of your sensitive exchanges.
7. Secure Backup and Data Protection
Implementing regular data backups to secure, offsite locations shields your critical information from data loss incidents, ransomware attacks, and hardware failures. By maintaining redundant copies of your data, you can swiftly recover from unforeseen incidents and minimize the impact of potential data compromises.
By integrating these additional security measures into your online practices, you fortify your digital resilience and establish a robust defense against a myriad of cyber threats. Embracing a proactive and comprehensive approach to online security empowers you to navigate the digital landscape with confidence, safeguarding your digital assets and privacy effectively.