Choose a Secure Username
Your username is the first impression others have of you on social media platforms like Twitter. To prevent strangers from following you, it’s important to choose a secure and non-identifiable username. Here are some tips to consider:
Avoid using your real name: Using your real name as your username can make it easier for strangers to find and track you. Instead, go for a username that doesn’t reveal your identity.
Don’t include personal information: Stay away from including any personal information in your username. This includes your birthdate, address, phone number, or any other identifiable details.
Use a combination of letters, numbers, and symbols: A strong username contains a combination of different characters, making it harder for someone to guess. Mixing uppercase and lowercase letters, along with numbers and symbols, adds an extra layer of security.
Avoid common or predictable usernames: Using generic and easily guessable usernames increases the risk of attracting unwanted attention. Stay away from common names, common words, or any other predictable combinations.
Regularly change your username: Consider changing your username periodically to ensure a higher level of security. This can help avoid being easily recognized or targeted by strangers who might have previously known your username.
Remember, choosing a secure username is just one of the steps in keeping your Twitter account safe. Combine this strategy with other security measures to ensure a robust and protected online presence.
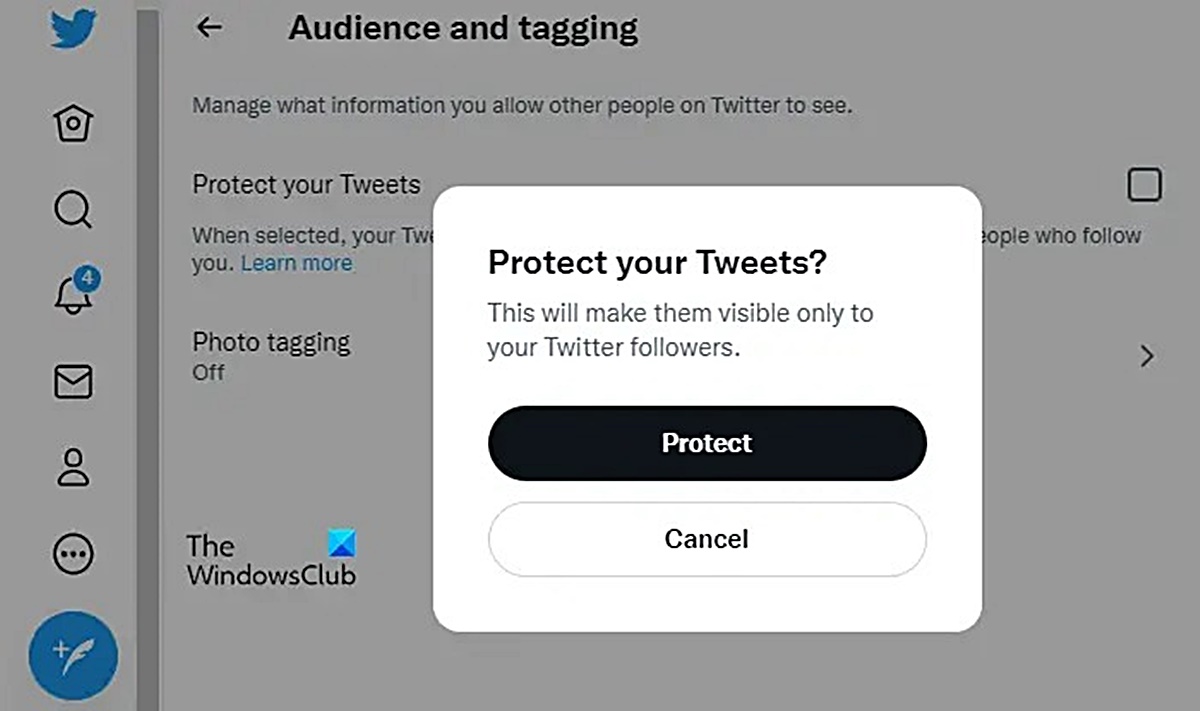
Protect Your Tweets
One effective way to prevent strangers from following you on Twitter is by protecting your tweets. By making your tweets private, you have control over who can see and interact with your content. Here’s how to protect your tweets:
Enable the privacy setting: In your Twitter account settings, you can find an option to enable “Protect your Tweets.” Once activated, only approved followers will be able to see your tweets.
Approve followers manually: With protected tweets, you have the power to approve or deny follower requests. This means that you can carefully screen and choose who has access to your content.
Exclude specific accounts: If there are specific accounts you want to prevent from following you, you have the ability to block them from your Twitter settings. This adds an extra level of control over your followers.
Be mindful of follower requests: Before approving follower requests, assess the profiles of potential followers. Look for any red flags or suspicious activity that may indicate their intentions. Only approve those you trust.
Regularly review and remove followers: Periodically review your follower list and remove any accounts that appear suspicious or no longer align with your interests or goals. This ensures that your followers remain trustworthy and relevant.
Think before you tweet: Even with protected tweets, it’s important to be mindful of what you post. Avoid sharing revealing or sensitive information that could potentially be harmful in the hands of strangers.
By protecting your tweets, you create a secure environment for sharing your thoughts and updates with a selected group of followers. This can give you peace of mind and control over the content you share on Twitter.
Set Your Account to Private
Setting your Twitter account to private is another effective way to prevent strangers from following you. When your account is private, only approved followers can see your tweets and interact with your content. Here’s how to set your account to private:
Access your account settings: Log in to your Twitter account and navigate to the settings menu.
Privacy and safety settings: Look for the “Privacy and safety” section in your account settings.
Enable privacy: Within the privacy settings, you’ll find an option to toggle your account between public and private. Choose the “Private” option to restrict access to your tweets.
Approve follower requests: Once your account is set to private, you can manually approve or deny follower requests. This gives you control over who can view your tweets and engage with your content.
Secure your tweets: By setting your account to private, you’re adding an additional layer of security to your Twitter presence. This prevents strangers from accessing your tweets and helps preserve your privacy.
Be selective with follower approvals: When approving follower requests, carefully consider the profiles and intentions of potential followers. Only approve requests from individuals you trust and feel comfortable sharing your tweets with.
Regularly review follower list: It’s important to periodically review your follower list and remove any accounts that may no longer align with your interests or goals. This helps maintain a safe and trusted circle of followers.
By setting your Twitter account to private, you have greater control over who can view and engage with your tweets. This ensures that your content remains within a trusted and secure circle of followers.
Customize Your Privacy Settings
Customizing your privacy settings on Twitter allows you to have more control over your account and protects you from unwanted followers. By adjusting these settings to fit your preferences, you can enhance your privacy and security. Here are some privacy settings to consider customizing:
Manage who can tag you in photos: Adjust your settings to control who can tag you in photos. You can choose to allow only people you follow to tag you, or disable this feature altogether.
Control who can see your connections: Decide whether you want your followers to see the accounts you follow or the accounts that follow you. Adjust these settings based on your preferences and comfort level.
Review and control your tagged tweets: Enable the setting that allows you to review and approve any tweets you are mentioned in before they appear in your timeline. This gives you greater control over the content associated with your account.
Manage your tweet location: If you prefer not to share your location, disable the option that allows Twitter to collect and use your precise location information.
Avoid search engine indexing: Prevent your tweets from appearing in search engine results by enabling the “Protect your tweets from search engines” option. This adds an extra layer of privacy to your account.
Limit data sharing with third-party apps: Review and adjust the settings related to third-party apps to control what information they can access and share. Be cautious about granting unnecessary permissions.
Manage your personalization and data settings: Take the time to review and customize the personalization and data settings in your account. This allows you to control the types of information Twitter uses to personalize your experience.
Regularly review and update your settings: Privacy settings can change over time, so it’s important to review and update them periodically. Stay informed about any new features or options that may impact your privacy.
By customizing your privacy settings, you can tailor your Twitter experience to meet your specific privacy needs and preferences. Take advantage of these options to ensure your account remains secure and protected from unwanted followers.
Block and Report Suspicious Accounts
To maintain a safe and secure Twitter environment, it’s important to be proactive in blocking and reporting suspicious accounts. Blocking and reporting can help prevent strangers from following you and protect you from potential malicious activity. Here’s how to block and report suspicious accounts:
Identify suspicious accounts: Be vigilant and look out for accounts that exhibit suspicious behavior or show signs of being fake or spam. Look for red flags such as profiles with no profile picture, generic usernames, or a history of spammy tweets.
Block suspicious accounts: When you encounter a suspicious account, block it immediately. Blocking prevents the account from following you, viewing your tweets, and interacting with your content.
Report suspicious accounts: After blocking the account, report it to Twitter. Reporting helps identify and flag suspicious accounts to protect other users from potential harm or harassment.
Provide detailed information: When reporting an account, be sure to provide as much detail as possible. Describe the suspicious behavior, include any relevant links or screenshots, and explain why you believe the account is malicious or harmful.
Take advantage of advanced reporting: Twitter offers advanced reporting options for more serious issues such as harassment, impersonation, or graphic content. Use these options when appropriate to ensure the proper handling of the situation.
Stay on top of blocked accounts: Regularly review your blocked account list to verify that the accounts you have blocked are still inactive or suspicious. This helps keep your block list up to date and ensures continued protection.
Seek support from Twitter’s Help Center: If you encounter persistent issues or need further assistance, reach out to Twitter’s Help Center for guidance and support. They can provide specific advice and address any concerns you may have.
By blocking and reporting suspicious accounts, you contribute to a safer Twitter community for yourself and others. Stay vigilant, act promptly, and report any accounts that pose a threat to your security or the well-being of the Twitter community.
Be Careful with Third-Party Apps
When it comes to protecting yourself from unwanted followers on Twitter, it’s crucial to be cautious with third-party apps. While these apps can offer additional features and functionality, they may also pose risks to your privacy and security. Here are some tips to be careful with third-party apps:
Only use reputable apps: Stick to well-known and reputable third-party apps when integrating them with your Twitter account. Research the app and read reviews to ensure its credibility and reliability.
Review permissions: Before authorizing any third-party app to access your Twitter account, carefully review the permissions it requires. Make sure it only has access to the necessary information and features.
Avoid granting unnecessary permissions: Be cautious about granting excessive permissions to apps. Make sure you understand why the app needs access to certain information and only provide the permissions that are absolutely necessary.
Regularly review connected apps: Periodically review the list of connected apps in your Twitter account settings. Remove any apps you no longer use or feel uncomfortable granting access to.
Check app reviews and ratings: Before installing a third-party app, check its reviews and ratings in the app store. This can provide insights into other users’ experiences and help you decide whether it’s trustworthy.
Be wary of app solicitations: Exercise caution when receiving unsolicited messages or emails promoting third-party apps. Avoid clicking on suspicious links and don’t provide your Twitter login credentials to unknown sources.
Stay informed about app privacy policies: Familiarize yourself with the privacy policies of the third-party apps you use. Make sure they have transparent data handling practices and prioritize user privacy.
Report suspicious or malicious apps: If you come across a third-party app that appears suspicious or violates Twitter’s terms of service, report it to Twitter immediately. This helps protect other users from potential harm.
Being careful with third-party apps is essential for safeguarding your Twitter account and preventing unwanted followers. By exercising caution, reviewing permissions, and staying informed, you can enjoy the benefits of these apps while minimizing the risks to your privacy and security.
Review Your Follower List Regularly
Regularly reviewing your follower list is an important step in maintaining a safe and secure Twitter presence. By taking the time to review your followers, you can identify and remove any suspicious or unwanted accounts. Here are some tips for reviewing your follower list:
Identify suspicious accounts: Look for accounts that exhibit suspicious behavior or have no activity on their profile. Pay attention to accounts with generic usernames, scant information, or a low follower-to-following ratio.
Assess follower engagement: Take note of accounts that have never engaged with your tweets or have very minimal interaction. These accounts could be inactive or potentially bots.
Investigate unfamiliar accounts: If you come across accounts that you don’t recognize, dig deeper into their profile and tweets. Verify if these accounts are relevant to your interests or if they pose a potential risk.
Remove unwanted followers: Once you’ve identified suspicious or unwanted accounts, remove them from your follower list. This helps ensure that your followers remain genuine and aligned with your preferences.
Consider blocking or reporting: If you encounter accounts that exhibit harmful or malicious behavior, consider blocking or reporting them to Twitter. This helps protect yourself and other users from potential harm.
Review followers from third-party apps: If you’ve granted access to your Twitter account via third-party apps, review the followers acquired through these apps. Ensure that they align with your interests and are genuine followers.
Regularly repeat the process: Follower lists can change over time, so it’s crucial to make reviewing a regular practice. Aim to review your follower list at least once every few months to maintain a healthy and secure follower base.
Stay aware of new followers: Keep an eye on your new followers and take note of any suspicious accounts that follow you. Promptly review their profiles to determine their authenticity and relevance.
Reviewing your follower list regularly helps keep your Twitter account secure and prevents unwanted followers from accessing your content. By actively managing your followers, you can maintain a trusted and engaged Twitter community.
Limit the Personal Information You Share
Protecting your privacy on Twitter involves being mindful of the personal information you share. Limiting the amount of personal information you disclose can help prevent strangers from following you and safeguard your online identity. Here are some tips to limit the personal information you share on Twitter:
Avoid sharing your full name: Instead of using your full name, consider using a username or handle that doesn’t reveal your identity completely.
Be cautious with your location: Think twice before sharing your exact location on Twitter. It is best to be general in revealing your whereabouts rather than specific.
Protect your contact information: Avoid sharing your email address or phone number publicly on your Twitter profile or in your tweets. This can help prevent unwanted communication or potential harassment.
Think before sharing personal photos: Be mindful when sharing personal photos on Twitter. Consider limiting the visibility of your photos to a select group of trusted followers or use the option to protect your tweets.
Guard sensitive personal details: Refrain from sharing sensitive personal details such as your home address, social security number, or financial information. These details should be kept strictly confidential.
Consider a separate email address: It might be worth creating a separate email address dedicated solely to your Twitter account. This provides an added layer of security and helps keep your personal and professional communication separate.
Be cautious with direct messages: When engaging in direct messages (DMs) with other users, be cautious about sharing personal information or engaging in conversations that may compromise your privacy.
Secure your linked accounts: If you have linked other accounts, such as Instagram or Facebook, to your Twitter profile, review the privacy settings of those accounts as well. Limit the information that can be accessed or shared through those connections.
Regularly audit your tweets: Take the time to review your past tweets and delete any that reveal personal information or opinions you no longer feel comfortable sharing. This helps maintain your privacy moving forward.
By being cautious about the personal information you share on Twitter, you can enhance your privacy and protect yourself from potential risks. Always think twice before disclosing any sensitive information and remember that your online safety should be a priority.
Don’t Engage with Unwanted Followers
One effective way to prevent unwanted followers from causing further issues on your Twitter account is to avoid engaging with them. By not interacting with suspicious or unwanted followers, you can maintain a safe and controlled online environment. Here are some tips for handling unwanted followers:
Ignore their messages and mentions: By choosing not to engage with unwanted followers, you minimize the risk of escalating any potential issues. Ignore their messages, mentions, or any attempts at engaging you in conversation.
Avoid responding to provocative content: Some unwanted followers may try to provoke a response from you by posting controversial or offensive content. It’s important to avoid engaging and giving them the attention they seek.
Do not retweet or share their content: By refraining from retweeting or sharing the content of unwanted followers, you avoid amplifying their presence and minimize the chances of their content reaching a wider audience.
Consider using the mute or block function: If an unwanted follower continues to be persistent or becomes a source of harassment, you can utilize Twitter’s mute or block functions. Muting allows you to stop seeing their content without them knowing, while blocking completely cuts off their access to your profile.
Report any harassment or abusive behavior: If an unwanted follower starts harassing you or displaying abusive behavior, it is crucial to report the account to Twitter. This helps ensure the safety of not only yourself but other users as well.
Don’t let them deter you: It’s important not to let unwanted followers discourage you from being active on Twitter. Focus on engaging with positive interactions and building connections with followers who share your interests and goals.
Set your boundaries and enforce them: Establish clear boundaries for yourself on how you want to be treated on Twitter. Be firm in enforcing those boundaries and remember that you have the right to maintain a respectful and safe online environment.
Monitor and adjust your privacy settings: Regularly review and update your privacy settings to ensure they align with your comfort level. This allows you to have greater control over who can interact with you and view your content.
Engage with trusted followers: Focus your attention and energy on engaging with your trusted followers who genuinely support and contribute positively to your Twitter experiences. Build meaningful connections and foster a supportive community.
By not engaging with unwanted followers, you maintain control over your Twitter experience and minimize the risk of encountering further issues. Prioritize your own well-being and focus on fostering a positive and engaging environment with your trusted followers.
Use Strong and Unique Passwords
One of the fundamental steps to protect your Twitter account from unauthorized access is to use strong and unique passwords. A strong password is essential to ensure the security of your account and prevent strangers from gaining unauthorized access. Here are some tips to create and manage strong and unique passwords:
Avoid common or predictable passwords: Stay away from using common or easily guessable passwords such as “123456” or “password.” These passwords are weak and can be easily cracked by hackers.
Use a mix of characters: Create a password that includes a combination of uppercase and lowercase letters, numbers, and symbols. The more complex and varied your password is, the harder it is for hackers to crack it.
Make it lengthy: Create a password that is at least 12 characters long. Longer passwords provide an extra layer of security and make it more difficult for brute force attacks.
Unique password for each account: Avoid reusing passwords across different accounts. If one account gets compromised, having a unique password for each account will prevent unauthorized access to all your other accounts.
Consider using a passphrase: Instead of a single word, consider using a passphrase composed of multiple words. Passphrases are easier to remember and harder to crack than individual words.
Utilize a password manager: Consider using a password manager app or software to store and generate strong and unique passwords for each of your accounts. This ensures that you can access your passwords securely and easily.
Enable two-factor authentication: Take advantage of Twitter’s two-factor authentication feature. It adds an extra layer of security by requiring a verification code in addition to your password for logging in.
Regularly update your passwords: Set a reminder to regularly update your passwords, ideally every few months. Regularly changing your passwords helps protect against any potential breaches and keeps your accounts secure.
Never share your password: It’s crucial to never share your password with anyone, including friends, family, or coworkers. Your password should be kept confidential to maintain the integrity of your account.
Be cautious of phishing attempts: Be wary of emails, links, or messages that request your password or login credentials. Always verify the legitimacy of such requests before providing any information.
By using strong and unique passwords, you significantly reduce the risk of unauthorized access to your Twitter account. Protect yourself from potential security breaches and safeguard your online presence by taking the necessary steps to create and manage strong passwords.