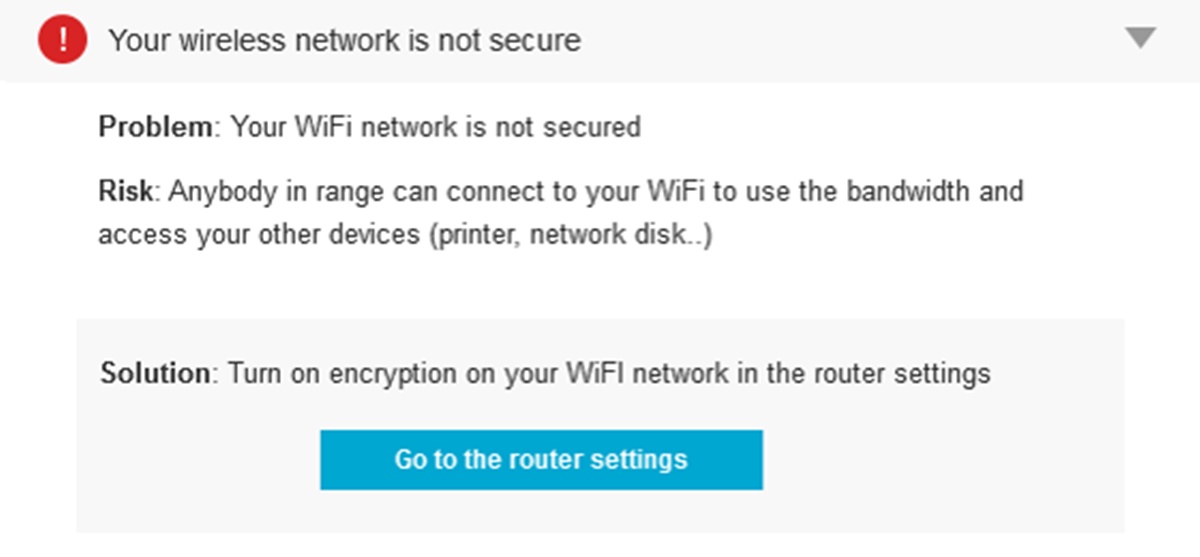
Importance of Wi-Fi Security
Your wireless network is the gateway to the digital world, providing you with the convenience of connecting to the internet without relying on cumbersome cables. However, it can also be vulnerable to various security threats if not properly secured. Maintaining a secure Wi-Fi network is crucial to protect your data, privacy, and prevent unauthorized access to your network.
One of the primary reasons to prioritize Wi-Fi security is to prevent potential hackers from gaining access to your personal information. When you connect to a public Wi-Fi network or leave your home network unsecured, you expose your sensitive data to interception. Hackers can intercept your internet traffic and potentially steal your usernames, passwords, financial information, and other confidential data.
Moreover, an unsecured Wi-Fi network can become an open invitation for unauthorized users to connect and exploit your network resources. This can result in slower network speeds, increased data usage, and potential damage to your network devices. Additionally, unauthorized users could potentially launch malicious attacks or engage in illegal activities using your network, leaving you liable for any legal consequences.
By implementing proper Wi-Fi security measures, you can safeguard your network and ensure that only authorized devices and users can access it. This not only protects your personal information but also helps maintain a stable and reliable network connection. With a secure Wi-Fi network, you can browse the internet, conduct online transactions, and communicate online with peace of mind.
Furthermore, securing your Wi-Fi network also helps to protect your devices from security vulnerabilities. Many internet-connected devices, such as smartphones, tablets, and smart home devices, are susceptible to attacks if they are connected to an unsecured Wi-Fi network. By encrypting your wireless network and implementing other security measures, you can minimize the risk of these devices becoming compromised.
In today’s digital age, where an increasing amount of personal and confidential information is exchanged online, ensuring the security of your wireless network is paramount. By taking the necessary steps to secure your Wi-Fi network, you can protect your data, maintain privacy, and create a safe online environment for yourself and your family.
Wireless Network Encryption
Wireless network encryption plays a vital role in securing your Wi-Fi network from unauthorized access and data interception. Encryption involves encoding your network traffic with a unique key, making it unreadable to anyone without the correct credentials. There are different encryption methods available, each offering varying levels of security. Let’s explore the three most commonly used encryption protocols: WEP, WPA, and WPA2.
WEP (Wired Equivalent Privacy): WEP was the first encryption method introduced for wireless networks. Unfortunately, it is relatively weak compared to more modern encryption protocols. WEP uses a shared key authentication system, and its encryption algorithm can be easily cracked by experienced hackers. Therefore, it is highly recommended to avoid using WEP encryption for your Wi-Fi network.
WPA (Wi-Fi Protected Access): WPA is an improvement over WEP and provides better security for your Wi-Fi network. It introduces stronger encryption algorithms, such as TKIP (Temporal Key Integrity Protocol), which dynamically generates unique encryption keys for each data transmission. WPA also supports passphrase-based authentication, making it easier for users to set up and manage their network security. While WPA is more secure than WEP, it still has some vulnerabilities.
WPA2 (Wi-Fi Protected Access 2): WPA2 is currently the most secure encryption protocol for wireless networks. It utilizes the Advanced Encryption Standard (AES) algorithm, which is highly resistant to hacking attempts. WPA2 has replaced WPA as the standard security protocol for Wi-Fi networks worldwide. It provides robust encryption and allows for more secure authentication methods, such as using digital certificates or RADIUS authentication servers.
When setting up your wireless network, it is essential to select the appropriate encryption method. If your devices support it, always choose WPA2 encryption for the highest level of security. If you have older devices that do not support WPA2, opt for WPA as a second-best option. Avoid using WEP encryption, as it provides minimal security and is susceptible to hacking.
Remember that encryption alone is not sufficient to secure your Wi-Fi network. It should be used in conjunction with other security measures, such as strong passwords and regular firmware updates. Additionally, it is crucial to keep up with advancements in wireless security and periodically review and update your encryption settings to stay ahead of potential vulnerabilities.
WEP (Wired Equivalent Privacy)
WEP (Wired Equivalent Privacy) is an encryption protocol that was introduced as the first security standard for wireless networks. Initially, it aimed to provide a level of security equivalent to that of wired networks. However, over time, it has been found to be vulnerable to various security exploits, making it an outdated and insecure encryption method.
WEP uses a shared key authentication system, where a predetermined password or key is shared between the wireless access point and the devices connecting to it. This key is used to encrypt and decrypt data transmitted over the network. However, the encryption algorithm used in WEP, known as RC4 (Rivest Cipher 4), has several weaknesses that have been exposed over the years.
One of the main vulnerabilities of WEP is the easily crackable encryption key. WEP keys are typically either 64 bits or 128 bits long. However, due to flaws in the encryption algorithm, it is relatively easy for attackers to retrieve the encryption key by capturing a sufficient amount of encrypted data packets. Once an attacker obtains the key, they can decrypt all the data transmitted over the network.
Another weakness of WEP is the reuse of initialization vectors (IVs). Each data packet transmitted in a WEP-encrypted network is assigned a unique IV. However, the pool of available IVs in WEP is limited, and once an IV is reused, it becomes easier for attackers to crack the encryption key.
Additionally, WEP does not provide a robust mechanism for authentication. It only verifies that the entered key matches the key programmed into the access point. There is no way to verify the authenticity of the device connecting to the network, leaving the network vulnerable to impersonation attacks.
Due to these vulnerabilities, it is highly recommended to avoid using WEP encryption for your Wi-Fi network. Its weaknesses can be exploited by even amateur attackers using readily available tools and techniques. Instead, opt for stronger encryption methods like WPA or WPA2, which provide better security and are more resistant to hacking attempts.
If you are currently using WEP encryption on your wireless network, it is crucial to upgrade to a more secure encryption method as soon as possible. Most modern routers and devices support WPA2 encryption, which offers significantly improved security. By making this switch, you can protect your network and data from potential breaches and ensure a safer and more secure Wi-Fi experience for all connected devices.
WPA (Wi-Fi Protected Access)
Wi-Fi Protected Access (WPA) is an improved encryption protocol introduced as a replacement for the vulnerable WEP (Wired Equivalent Privacy) encryption. WPA was designed to provide enhanced security for wireless networks and overcome the weaknesses of its predecessor.
The primary security improvement in WPA is the use of the Temporal Key Integrity Protocol (TKIP). TKIP dynamically generates a unique encryption key for each data transmission, making it significantly more resistant to encryption key attacks compared to WEP.
WPA also introduces an improved authentication mechanism to verify the integrity of devices connecting to the network. It includes support for Pre-Shared Key (PSK) authentication, where users can set up a passphrase that serves as a shared secret between the access point and the connecting devices. This makes it easier to authenticate devices without the need for additional authentication servers.
Another vital improvement in WPA is the use of integrity checks, which prevent tampering with the data packets during transmission. This ensures that the data received by the devices is intact and has not been modified by an unauthorized party.
Although WPA addressed several security vulnerabilities present in WEP, it still has some weaknesses. WPA is susceptible to offline dictionary attacks, where an attacker intercepts a WPA-encrypted handshake and attempts to crack the passphrase by trying various precomputed combinations. Additionally, some older devices may not fully support WPA, limiting compatibility with certain devices.
It is important to note that WPA is a deprecated encryption protocol and has been superseded by WPA2 (Wi-Fi Protected Access 2). WPA2 offers even stronger security measures, rendering WPA less desirable for securing wireless networks. It is recommended to use WPA2 encryption whenever possible to ensure the highest level of security for your Wi-Fi network.
If your network devices do not support WPA2 encryption, using WPA is still a better choice than relying on the outdated and vulnerable WEP encryption. To enhance the security of your WPA-encrypted network, it is crucial to select a strong and unique passphrase. Avoid using common dictionary words or easily guessable combinations. Instead, combine uppercase and lowercase letters, numbers, and special characters to create a complex and secure passphrase.
Regularly updating your Wi-Fi network hardware and firmware is also crucial to maintain a secure Wi-Fi environment. By keeping your devices up to date, you ensure that any security vulnerabilities discovered in the encryption protocols or the hardware itself are patched and addressed.
Overall, WPA is a significant improvement over WEP and offers better security for wireless networks. However, it is recommended to transition to the more advanced and secure WPA2 encryption for optimal protection against potential security breaches.
WPA2 (Wi-Fi Protected Access 2)
WPA2 (Wi-Fi Protected Access 2) is the current industry standard encryption protocol for securing wireless networks. It encompasses significant improvements over its predecessors, WEP and WPA, providing the highest level of security for Wi-Fi networks today.
One of the key advancements in WPA2 is the use of the Advanced Encryption Standard (AES) algorithm. AES is a robust encryption algorithm that is highly resistant to attacks and provides secure encryption of data packets transmitted over the network. Unlike the outdated encryption algorithms used in WEP and WPA, AES ensures the confidentiality and integrity of your network data.
WPA2 supports two authentication methods: Personal (PSK) and Enterprise. The Personal mode, also known as Pre-Shared Key (PSK) authentication, is suitable for home networks and small businesses. It uses a passphrase to generate a unique encryption key for each device that connects to the network. The Enterprise mode, on the other hand, employs a RADIUS (Remote Authentication Dial-In User Service) server for centralized authentication, making it ideal for larger organizations with more complex authentication requirements.
One of the notable features of WPA2 is the inclusion of Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) as the default encryption method. CCMP provides both data confidentiality and integrity, ensuring that the encrypted data remains secure during transmission. Compared to the Temporal Key Integrity Protocol (TKIP) used in WPA, CCMP offers stronger encryption and is less susceptible to cryptographic vulnerabilities.
Another essential aspect of WPA2 security is the concept of pairwise transient keys. With WPA2, each device on the network generates a unique encryption key for every session or communication link established. This increases security by minimizing the potential impact of compromised keys or intercepted data.
Device compatibility is a crucial consideration when implementing WPA2 encryption. Most modern Wi-Fi devices, including routers, smartphones, tablets, and computers, support WPA2. However, it is essential to ensure that both your wireless router (access point) and client devices are capable of using WPA2 encryption to establish a secure connection.
It is important to regularly update your network devices’ firmware to ensure they are equipped with the latest security patches and enhancements provided by the manufacturer. The Wi-Fi Alliance, the organization that oversees wireless standards, continues to refine and update the WPA2 standard to address emerging security threats, and keeping your devices up-to-date helps maintain the highest level of security for your network.
Overall, WPA2 is the current gold standard for network encryption, providing robust security for Wi-Fi networks. By utilizing WPA2 encryption, you can protect your data, maintain network integrity, and ensure a high level of privacy for all the devices connected to your network.
Selecting the Right Encryption Method
When it comes to securing your wireless network, selecting the right encryption method is crucial. The encryption method you choose will determine the level of security your network provides and the compatibility of devices connecting to it. Here are some factors to consider when selecting the appropriate encryption method:
Network and Device Compatibility: Ensure that both your wireless router (access point) and the devices that will connect to the network support the encryption method you choose. The most widely supported and recommended encryption method is WPA2. However, if you have older devices that do not support WPA2, you may need to opt for WPA as a fallback, as it provides better security than the outdated WEP encryption.
Security Level: Consider the desired level of security for your network. If you prioritize the highest level of security, WPA2 is the best choice. It employs the advanced AES encryption algorithm, which is highly resistant to attacks. WPA2 ensures that your data remains confidential and secure during transmission. However, if WPA2 is not an option due to device compatibility, WPA is a suitable alternative, providing improved security over WEP.
Authentication Method: Consider whether you want to use Pre-Shared Key (PSK) authentication or the more advanced Enterprise mode requiring a RADIUS server. PSK authentication is suitable for home networks and small businesses, making it easy to set up and manage. Enterprise mode, on the other hand, is ideal for larger organizations that require centralized authentication and additional security measures.
Futureproofing: Take into account the longevity of the encryption method you choose. WEP is highly outdated and vulnerable to attacks, so it is essential to avoid using it. WPA has been phased out in favor of WPA2, which is the current industry standard. By selecting WPA2, you ensure that your network remains secure and compatible with future devices and security advancements.
Ease of Use: Consider the ease of use and management of the encryption method. WPA2, with its stronger security, may require a more complex setup, particularly in the Enterprise mode. However, modern routers often have user-friendly interfaces that simplify the configuration process, making it easier for both novice and experienced users to set up and manage their network security.
Taking these factors into account, the recommended encryption method for most users is WPA2. It provides the highest level of security, compatibility with modern devices, and an effective balance between ease of use and advanced security features. However, if device compatibility is a concern, WPA can be used as an alternative. Whatever encryption method you choose, remember to also implement other security measures such as strong passwords, regular firmware updates, and network monitoring to ensure the overall security of your wireless network.
Password Selection
Choosing a strong and secure password for your wireless network is essential to prevent unauthorized access and protect your data. A weak password can be easily guessed or cracked, leaving your network vulnerable to intrusion. Here are some guidelines to consider when selecting a password:
Length and Complexity: Aim for a password that is at least 12 characters long. The longer the password, the harder it is for attackers to crack. Include a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using common dictionary words or simple patterns that can be easily guessed.
Avoid Personal Information: Do not use personal information such as your name, birthdate, or address as part of your password. This information can often be easily obtained or guessed by attackers. Instead, choose a password that is unrelated to your personal life.
Unique Passwords: Do not reuse passwords for multiple accounts or services. If one account is compromised, reusing the same password makes it easier for attackers to gain access to other accounts. Use a unique password for your wireless network that is not used for any other purposes.
Avoid Common Passwords or Patterns: Stay away from commonly used passwords or patterns such as “password,” “123456,” or sequential patterns like “abcd” or “qwerty.” These are the first passwords attackers will attempt when trying to crack into a network.
Regular Password Updates: Change your password regularly to maintain security. Set a reminder to update your password every few months or whenever there is a significant security incident. Regularly changing your password mitigates the risk of a compromised password being used to gain unauthorized access.
Consider Using a Passphrase: Instead of a single complex password, consider using a passphrase. A passphrase is a sequence of words or sentences that are easy for you to remember but difficult for others to guess. For example, “CorrectHorseBatteryStaple” is a strong passphrase that is highly resistant to cracking attempts.
Securely Store and Share Passwords: Avoid writing down passwords and leaving them in easily accessible places. If you need to store passwords, use a reputable password manager that encrypts your passwords and provides secure access. When sharing passwords with trusted individuals, do so in person or using a secure form of communication.
By following these guidelines, you can significantly enhance the security of your wireless network by selecting a strong and unique password. A secure password serves as a crucial barrier against unauthorized access, reducing the risk of data breaches and maintaining the integrity of your network.
Changing the Default SSID
The SSID (Service Set Identifier) is the name of your wireless network that devices use to identify and connect to it. When you set up a new wireless router, it typically comes with a default SSID assigned by the manufacturer. It is important to change this default SSID to enhance the security and privacy of your network. Here are several reasons why changing the default SSID is advisable:
Eliminating Easy Identification: When attackers attempt to gain unauthorized access to wireless networks, they often target networks with default SSIDs first. By changing the default SSID, you remove the easily identifiable characteristic of your network, making it less likely to be targeted.
Preventing Identification of Router Model: Manufacturers commonly include the router model or brand name in the default SSID. This information can provide attackers with insights into the potential vulnerabilities associated with specific router models. Changing the SSID removes this identifying information, making it harder for attackers to exploit known vulnerabilities.
Enhancing Network Privacy: Using the default SSID may allow others to identify the brand and model of your router, which could potentially expose your network to various security risks. Changing the SSID helps protect your network’s privacy and adds an additional layer of security.
Reducing Confusion and Interference: In densely populated areas or apartment buildings, multiple Wi-Fi networks with default SSIDs can cause confusion and interference. By changing your SSID to something unique and memorable, you can easily identify your network and reduce potential interference from neighboring networks.
Customizing Network Identification: Changing the SSID allows you to personalize your wireless network and give it a unique identity. You can use a name that reflects your personality or a name that is easily recognizable to you and your family members.
To change the default SSID, access your router’s administration settings through a web browser. Log in to the router’s interface using the administrator credentials provided by the manufacturer or your internet service provider. Look for the wireless settings or SSID option and enter your desired network name. Remember to save the changes to apply the new SSID.
When choosing a new SSID, avoid using personal information or anything that could easily identify you, such as your address or name. It is best to select a unique and creative name that is easily recognizable to you and those who need to connect to your network.
By changing the default SSID, you enhance the security, privacy, and personalization of your wireless network. It adds a layer of protection against potential attacks and allows you to stand out among other nearby networks. Take the time to change your SSID, and enjoy greater control and peace of mind over your wireless network.
MAC Address Filtering
MAC address filtering is an additional security measure you can implement on your wireless network to control which devices are allowed to connect. MAC (Media Access Control) addresses are unique identifiers assigned to network interfaces, including those of computers, smartphones, and other devices. By enabling MAC address filtering, you create a whitelist of approved MAC addresses and only allow devices with those addresses to connect to your network. Here are the benefits and considerations of using MAC address filtering:
Increased Network Security: MAC address filtering adds an extra layer of security to your wireless network by allowing only authorized devices to connect. Even if an attacker knows your Wi-Fi password, they won’t be able to access your network without their device’s MAC address being on the approved list.
Protection against Unauthorized Access: MAC address filtering prevents unauthorized devices from connecting to your network, reducing the risk of intrusions, data breaches, and misuse of network resources. It also prevents neighboring devices from accidentally connecting to your network.
Device Control: MAC address filtering allows you to have fine-grained control over which devices can connect to your network. You can specify individual devices by their MAC addresses or define groups of devices, such as laptops, smartphones, or smart home devices.
Limitations: While MAC address filtering is a useful security measure, it is not foolproof. Skilled attackers can spoof MAC addresses, making it possible for unauthorized devices to connect. Additionally, maintaining the MAC address whitelist can be time-consuming, especially if you frequently add or remove devices from your network.
Configuration: To enable MAC address filtering, you need to access your router’s administration settings through a web browser. Look for the MAC address filtering or Access Control List (ACL) option in the wireless settings. There, you can manually enter the MAC addresses of devices you wish to allow or disallow from connecting to your network. Make sure to save the changes to apply the MAC address filtering rules.
Adding Devices: When adding a new device to your network, you will need to retrieve its MAC address. This can usually be found in the device’s network settings or on the device itself. Once you have the MAC address, you can add it to the allowed list in your router’s MAC address filtering settings.
Managing Approved Devices: It is important to regularly review and update the approved MAC address list to ensure it remains accurate and up-to-date. Remove any devices that are no longer in use, and add new devices as needed. This will help maintain network security and prevent unauthorized access.
MAC address filtering can be a useful tool in securing your wireless network and controlling device access. While it is not a comprehensive security solution, it adds another layer of protection against unauthorized connections. Combine MAC address filtering with other security measures, such as strong encryption and a secure password, to create a robust and secure wireless network.
Disabling Guest Networks
Many modern routers provide the option to enable guest networks, which allow visitors to connect to the internet without accessing your main network. While guest networks can be convenient for guests and provide an extra layer of separation between your devices and their devices, they can also pose security risks if not properly configured. In some cases, it may be advisable to disable guest networks altogether. Here’s what you need to consider:
Reducing Potential Security Risks: By disabling guest networks, you eliminate the potential security risks associated with allowing unknown devices to connect to your network. Guests may inadvertently introduce malware, viruses, or engage in unauthorized activities that could compromise the security of your network and connected devices.
Protecting Bandwidth and Performance: Guest networks can consume valuable bandwidth and impact the overall performance of your network. Disabling guest networks ensures that your available bandwidth is prioritized for your own devices, providing better speeds and overall network performance.
Preventing Unauthorized Access: If not set up properly, guest networks may provide an entry point for unauthorized users to gain access to your main network. By disabling the guest network functionality, you minimize the risk of unauthorized individuals attempting to connect and exploit your network resources.
Strengthening Device Isolation: Disabling guest networks ensures that your devices are isolated from any potentially compromised devices connected to the guest network. This separation helps prevent unauthorized access, data breaches, and other security threats from spreading to your main network.
Increased Control and Management: Disabling guest networks gives you more control over who can access your network. Instead of relying on a separate network for guests, you can provide guest access through individual Wi-Fi passwords, giving you the ability to grant temporary access and easily revoke it when necessary.
Considerations: Before disabling the guest network, it is important to evaluate your specific requirements. If you frequently have visitors who require Wi-Fi access, it may be more convenient to keep the guest network enabled. In such cases, ensure that the guest network is properly secured with strong encryption and a unique password. Set limitations on the bandwidth and monitor guest network usage to mitigate potential security risks.
Disabling Guest Networks: To disable the guest network functionality, access your router’s administration settings through a web browser. Look for the guest network settings and disable or turn off the feature. Save the changes to apply the configuration. Consult your router’s user manual or the manufacturer’s website for specific instructions on disabling the guest network.
By disabling guest networks, you eliminate unnecessary security risks and maintain better control over your network. However, it is important to strike a balance between security and convenience based on your specific needs and circumstances. Regularly review and update your network settings to ensure the highest level of security and performance for your wireless network.
Updating Router Firmware
Updating the firmware of your router is an essential step in maintaining the security and functionality of your wireless network. Firmware is the software that runs on your router, controlling its operations and features. Manufacturers often release firmware updates to address security vulnerabilities, fix bugs, improve stability, and introduce new features. Here’s why updating router firmware is important:
Enhanced Security: Firmware updates often include security patches that address vulnerabilities discovered in previous versions. By keeping your router firmware up to date, you ensure that any known security loopholes are closed, reducing the risk of unauthorized access and potential attacks on your network.
Bug Fixes and Stability: Firmware updates also resolve any bugs or stability issues that may impact the performance of your router. These issues may manifest as dropped connections, slow speeds, or intermittent network problems. Updating the firmware helps to improve the overall stability and reliability of your wireless network.
New Features and Improvements: Manufacturers often introduce new features or enhancements through firmware updates. These updates can enhance the functionality and performance of your router, providing you with additional capabilities or improved performance that were not available in the previous firmware version.
Compatibility with New Devices and Standards: Firmware updates can ensure that your router remains compatible with the latest devices and network standards. As new devices and technologies are released, firmware updates often include the necessary configurations and protocols to ensure optimal compatibility and performance.
Preparation for Future Technologies: Updating your router firmware can also prepare your network for upcoming technologies and advancements in wireless networking. It allows your router to adopt new standards and protocols that will be necessary for future network requirements, ensuring that your network remains up to date and capable of supporting emerging technologies.
Checking for Firmware Updates: To check for firmware updates, access your router’s administration settings through a web browser and locate the firmware update section. Some routers have an automatic check for updates feature, while others may require manual downloading and installation of the latest firmware. Refer to your router’s user manual or the manufacturer’s website for specific instructions on updating the firmware.
Backup and Precautions: Before performing a firmware update, it is crucial to back up your router’s current settings. This allows you to restore your preferred settings in case any issues arise during the update process. It is also recommended to perform the firmware update over a wired connection rather than a wireless connection to ensure a stable and uninterrupted update process.
Regularly updating your router firmware is a vital step in maintaining a secure and reliable wireless network. By staying up to date with firmware updates, you can benefit from improved security, enhanced performance, and compatibility with new devices and technologies. Make it a habit to check for firmware updates periodically to ensure that your network remains protected and optimized.
Regularly Changing Wi-Fi Passwords
Regularly changing your Wi-Fi password is a fundamental aspect of maintaining a secure wireless network. Your Wi-Fi password serves as a crucial line of defense against unauthorized access and helps protect your sensitive information. Here’s why regularly changing your Wi-Fi password is important:
Enhanced Security: Changing your Wi-Fi password on a regular basis helps minimize the risk of unauthorized individuals gaining access to your network. Even if someone has previously obtained your Wi-Fi password, changing it regularly ensures that they can no longer use it to connect to your network.
Protection against Brute-Force Attacks: Brute force attacks involve systematically attempting various password combinations until the correct one is found. By regularly changing your Wi-Fi password, you reduce the likelihood of falling victim to such attacks as the password becomes outdated.
Preventing Unauthorized Device Access: When you change your Wi-Fi password, all devices currently connected to your network will be disconnected. This helps prevent unauthorized devices from remaining connected to your network after compromising your Wi-Fi password, allowing you to maintain better control over who accesses your network.
Limiting Exposure: Tangible risks such as accidental password sharing, forgetting to revoke access for guests, or unauthorized individuals gaining access to your network can be mitigated by changing your Wi-Fi password regularly. By limiting the exposure of your Wi-Fi password, you reduce the likelihood of such incidents occurring.
Creating a Strong Password: Regularly changing your Wi-Fi password can encourage you to create a strong and unique password each time. A strong password includes a combination of uppercase and lowercase letters, numbers, and special characters. By regularly updating your password, you can ensure a higher level of security.
Procedure for Changing Wi-Fi Password: To change your Wi-Fi password, access your router’s administration settings through a web browser. Log in using the administrator credentials provided by the manufacturer or your internet service provider. Look for the wireless settings or security settings section, where you can change the Wi-Fi password. Make sure to save the changes to apply the new password.
Informing Authorized Users: After changing your Wi-Fi password, it is important to inform any authorized users who may require access to the network. This can include family members, friends, or other individuals who regularly connect to your network. Provide them with the new password to ensure uninterrupted network access.
Regularly changing your Wi-Fi password is an essential practice in maintaining a secure wireless network. By staying proactive and updating your password at regular intervals, you can enhance the security of your network, protect your data, and maintain better control over who accesses your network. Remember to select strong passwords and inform authorized users of any password changes to ensure a seamless Wi-Fi experience for all.