What is TrueCrypt?
TrueCrypt is a powerful and widely-used open-source disk encryption software that allows you to protect your sensitive files and folders by encrypting them. With TrueCrypt, you can create virtual encrypted volumes that act as regular files and can be easily accessed when mounted. The software uses a combination of strong encryption algorithms to ensure the security and confidentiality of your data.
One of the key features of TrueCrypt is its ability to create hidden volumes within other volumes. This means that you can have a hidden volume within an outer volume, providing an additional layer of security. This makes TrueCrypt an ideal choice for protecting sensitive information, such as financial data, personal documents, or confidential business files.
TrueCrypt is compatible with multiple operating systems, including Windows, macOS, and Linux, making it accessible to a wide range of users. It supports various encryption algorithms, including AES, Serpent, and Twofish, allowing you to choose the level of security that best suits your needs. It also integrates seamlessly with the operating system, providing a user-friendly interface that makes it easy to create, mount, and manage encrypted volumes.
Furthermore, TrueCrypt offers plausible deniability through hidden volumes. If you are ever compelled to disclose your password, you can provide the password for the outer volume, which will reveal only innocent and non-sensitive data, while the hidden volume remains completely secure and concealed.
It is important to note that TrueCrypt has been discontinued, but its source code is available for review and auditing. As a result, various forks and alternative implementations of TrueCrypt are available, ensuring that you can still benefit from its encryption capabilities.
Downloading and Installing TrueCrypt
To get started with TrueCrypt, you’ll need to download and install the software on your computer. Follow the steps below to ensure a smooth installation process:
- Visit the official website of a trusted TrueCrypt alternative, such as VeraCrypt or CipherShed, as TrueCrypt is no longer maintained. Download the installation file compatible with your operating system.
- Once the download is complete, locate the installation file on your computer and run it. You may be prompted with a security warning; if so, click “Run” to proceed.
- The installation wizard will guide you through the process. Read and accept the license agreement, then choose the destination folder where you want TrueCrypt to be installed. Leave the default settings unchanged unless you have specific requirements.
- On the next screen, you’ll be presented with the option to create a Start Menu entry. Decide whether you want TrueCrypt to be easily accessible from your Start Menu and make the appropriate selection.
- Next, choose whether you want to create a desktop shortcut. Again, this is a matter of personal preference.
- Before proceeding with the installation, you’ll be asked to install the TrueCrypt driver. This driver is essential for TrueCrypt to function properly. Click “Install” to continue.
- The installation process will now commence. Wait for it to complete, which should only take a few moments.
- Once the installation is finished, you’ll see a confirmation message. You can now launch TrueCrypt by clicking on the appropriate shortcut or by searching for it in your Start Menu.
Congratulations! You have successfully downloaded and installed TrueCrypt or its alternative on your computer. It is now time to create a new volume and start securing your sensitive files and folders.
Creating a New Volume
After installing TrueCrypt or its alternative, the next step is to create a new volume where you can store and encrypt your files. Follow the steps below to create a new volume using TrueCrypt:
- Launch TrueCrypt by clicking on the shortcut or searching for it in your Start Menu.
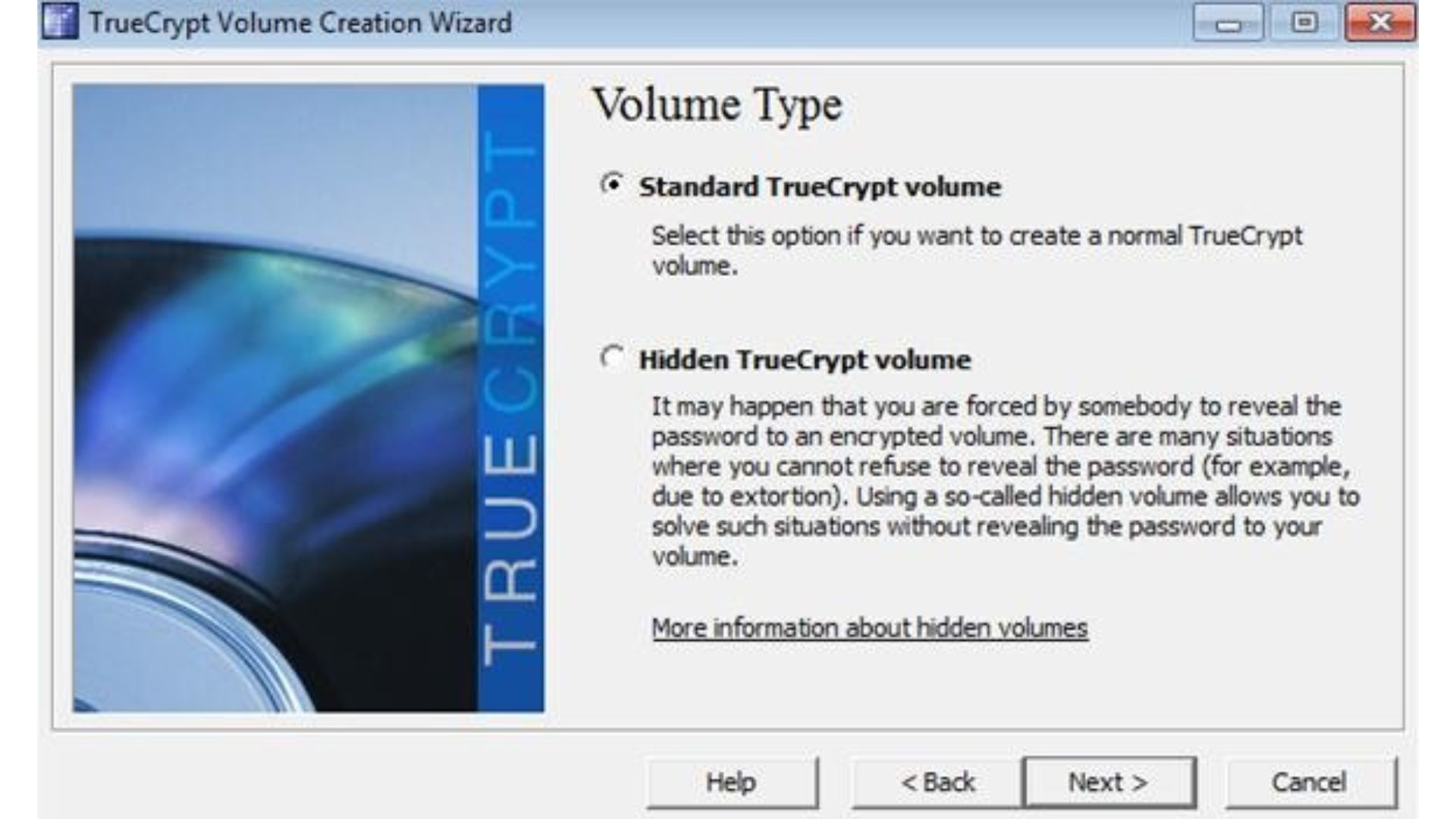
- In the TrueCrypt main window, click on the “Create Volume” button to start the volume creation wizard.
- Choose the option “Create an encrypted file container” and click “Next” to continue.
- Select the volume type. “Standard TrueCrypt volume” is the most common choice, so leave it selected and click “Next”.
- Choose a location and name for your new volume file. This file will act as a virtual disk that contains your encrypted data. Make sure to choose a secure location and a strong, memorable name.
- Specify the size of your volume. You can enter a specific size or choose to create a dynamic volume that grows as you add files to it.
- Select the encryption algorithm and hash algorithm you want to use. TrueCrypt offers multiple options, but it is generally recommended to use AES as the encryption algorithm for its strong security.
- Set the password for your volume. Make sure to use a strong, unique password that includes a combination of uppercase and lowercase letters, numbers, and symbols.
- Click “Next” to proceed to the Format Options screen. Here, you can choose to either create a file system within the volume or leave it unformatted. Select the appropriate option based on your needs.
- Review the summary of the settings you have chosen and click “Format” to begin creating the volume.
- Wait for the formatting process to complete. This may take some time depending on the size of the volume.
- Once the formatting is finished, you will see a confirmation message. Click “Exit” to close the volume creation wizard.
Congratulations! You have successfully created a new encrypted volume using TrueCrypt. You can now start using this volume to store and protect your sensitive files and folders. Remember to keep your password in a secure place and regularly back up your encrypted volume to prevent data loss.
Choosing Encryption Algorithms
When using TrueCrypt or its alternative, one of the most important considerations is the choice of encryption algorithms. TrueCrypt offers various encryption algorithms, each with its own strengths and characteristics. Understanding these algorithms can help you make an informed decision for securing your data. Here are some common encryption algorithms available in TrueCrypt:
- AES (Advanced Encryption Standard): AES is widely regarded as one of the most secure encryption algorithms available. It offers a high level of protection and is used by governments and organizations worldwide. AES is available in different key sizes, such as 128-bit, 192-bit, and 256-bit, with larger key sizes providing stronger encryption.
- Serpent: Serpent is another strong encryption algorithm supported by TrueCrypt. It is known for its robustness and resistance against various cryptographic attacks. Serpent has a fixed key size of 256 bits and is considered highly secure.
- Twofish: Twofish is a symmetric encryption algorithm that offers a good balance between security and performance. It has a variable key size, ranging from 128 bits to 256 bits, and is renowned for its efficiency and resistance to cryptanalysis.
When choosing encryption algorithms, it is important to balance security requirements with system performance. Stronger encryption algorithms tend to require more computational resources, which can impact system performance during encryption and decryption processes. Assess your needs and consider factors such as the sensitivity of your data, the intended usage, and the capabilities of your hardware.
TrueCrypt also supports cascading encryption, where multiple encryption algorithms are used in combination for added security. This means that the data is encrypted using one algorithm and then encrypted again using another algorithm. While cascading encryption can enhance security, it does come with an increased computational overhead.
Ultimately, the choice of encryption algorithms depends on your specific security requirements and preferences. Consider the level of risk, the need for compatibility with different systems, and the available computational resources when making your decision. It is also recommended to stay up to date with the latest advancements in encryption technology and periodically review and update your encryption settings to ensure the highest level of security for your data.
Setting the Volume Size
When creating a new volume using TrueCrypt or its alternative, one important consideration is determining the size of the volume. The volume size refers to the amount of space allocated for storing your encrypted files and folders. Properly setting the volume size is crucial to ensure that you have enough storage capacity while also considering factors such as security and future expansion needs.
Here are some important points to consider when setting the volume size:
- Storage requirements: Take into account the amount of data you need to store in the volume. Consider the size of the files and folders you want to encrypt and estimate the total space needed.
- Future expansion: Plan for future growth and ensure that the chosen volume size allows for additional files and folders to be added without running out of space. It is recommended to allocate some extra space to accommodate future needs.
- Available disk space: Consider the amount of free space available on your disk drive. Make sure that the chosen volume size does not exceed the available disk space to avoid any issues during the volume creation process.
- Security considerations: Larger volume sizes can offer a higher level of security as they make it more difficult for attackers to analyze patterns within the encrypted data. However, keep in mind that larger volumes require more time to create, mount, and perform operations on.
When setting the volume size, it is essential to strike a balance between the above factors. Allocating too much space can lead to wasted disk space, while allocating too little space may result in insufficient storage capacity.
It is also worth mentioning that TrueCrypt allows you to create dynamic volumes that grow as you add files to them. This can be a useful feature if you are unsure about the exact size requirements or if you anticipate frequent additions to the volume. Dynamic volumes automatically expand as needed, up to the maximum size specified during the volume creation process.
By carefully considering your storage needs, anticipating future growth, and evaluating available disk space, you can determine the optimal volume size for your encrypted files and folders. Remember to regularly assess your storage requirements and adjust the volume size accordingly to ensure a seamless and secure encryption experience.
Setting a Password
Setting a strong and secure password is a critical step when using TrueCrypt or its alternative to encrypt your files and folders. The password acts as the key to unlock and access your encrypted volume, so it is essential to choose a password that is not easily guessable and provides a high level of security. Here are some important tips for setting a strong password:
- Length: Use a password that is at least 12 characters long. Longer passwords are generally more secure as they offer a greater combination of characters.
- Complexity: Include a mix of uppercase and lowercase letters, numbers, and special characters in your password. This makes it more difficult for attackers to crack the password using brute-force methods.
- Avoid common words and patterns: Avoid using common words, phrases, or patterns in your password. Hackers often use dictionaries and common password lists to guess passwords, so it is important to choose something unique and unpredictable.
- Avoid personal information: Do not include any personal information, such as your name, birthdate, or address, in your password. This information is easily accessible and can be used to guess your password.
- Change regularly: It is good practice to change your password regularly, even if you believe it is secure. This further reduces the risk of your password being compromised.
- Memorable but not obvious: Choose a password that you can remember without writing it down, but also avoid using easily guessable information, such as birthdays or family names. Consider using a passphrase that combines several words or a combination of memorable elements.
Remember, the strength of your password directly impacts the security of your encrypted volume. A weak password can be easily guessed, increasing the risk of unauthorized access to your sensitive data. Conversely, a strong password significantly improves the security of your encrypted volume.
In addition to setting a strong password, it is crucial to keep your password confidential and not share it with anyone. If you need to store your password somewhere, consider using a reliable password manager that encrypts your passwords and securely stores them.
By following these guidelines and setting a strong, unique, and memorable password, you can enhance the security of your encrypted volume and protect your sensitive files and folders from unauthorized access.
Generating a Keyfile
In addition to setting a strong password, TrueCrypt or its alternative offers an additional layer of security through the use of keyfiles. A keyfile is an external file that acts as a second factor of authentication, enhancing the security of your encrypted volumes. Generating a keyfile involves creating a unique file that is used in conjunction with your password to unlock and access your encrypted data. Follow the steps below to generate a keyfile:
- Launch TrueCrypt and make sure you have a volume created or mounted.
- In the TrueCrypt main window, click on the “Settings” button.
- In the Settings window, select the “Keyfiles” tab.
- Click on the “Add Files” or “Add Security Token” button to select the file or device that you want to use as your keyfile.
- Browse your computer and choose an appropriate file. It can be any file you have access to, such as an image, document, or even a music file. Alternatively, you can use a device like a USB drive as your keyfile.
- After selecting the file or device, click on the “OK” button to add it as a keyfile.
- You can add multiple keyfiles by repeating the process.
Once you have generated a keyfile, it is important to keep it secure and in a safe location separate from your encrypted volume. Store it in a location that is physically separate from your computer, such as an external drive or a cloud storage service.
During the volume mounting process, you will be prompted to enter your password and select your keyfile(s). Both the correct password and the authorized keyfile(s) are required to successfully unlock and access the encrypted volume. This provides an additional layer of security as an attacker would need both your password and access to the specific keyfile(s) to gain unauthorized access to your data.
It is recommended to periodically review and update your keyfiles to ensure their integrity and security. If you suspect that a keyfile has been compromised or lost, remove it from the list of keyfiles in the TrueCrypt settings and generate a new one to maintain the security of your encrypted volumes.
By generating and using a keyfile in combination with a strong password, you significantly enhance the security of your encrypted volumes, safeguarding your sensitive data from unauthorized access.
Mounting and Unmounting Volumes
Once you have created an encrypted volume using TrueCrypt or its alternative, you need to know how to mount and unmount the volume to access and secure your files. Mounting a volume means making it accessible and ready for use, while unmounting ensures that the volume is safely closed and encrypted. Here’s a step-by-step guide on how to mount and unmount volumes:
- Launch TrueCrypt and ensure that the software is running.
- In the TrueCrypt main window, click on the “Select File” button and browse to locate your encrypted volume file.
- Once selected, click on the “Mount” button to initiate the mounting process.
- Enter your password in the provided field. If you have also set up keyfiles, you will be prompted to select the appropriate keyfile(s).
- Click on the “OK” button to start the mounting process.
- After successfully mounting the volume, it will be assigned a unique drive letter or mount point, depending on your operating system.
- You can now access the mounted volume and work with your files and folders as you would with any regular drive or directory.
- When you are finished working with the volume, it is essential to unmount it to ensure the security of your data.
- In the TrueCrypt main window, locate the mounted volume in the drive list.
- Select the mounted volume and click on the “Unmount” button.
- The unmounting process will close the volume, encrypt it, and remove the assigned drive letter or mount point.
- Wait for the unmounting process to complete, and you will receive a confirmation message.
It is important to note that unmounting the volume ensures that your data remains encrypted and inaccessible to unauthorized users. Always make sure to unmount your volumes properly before shutting down your computer or disconnecting any external storage devices.
Additionally, TrueCrypt allows you to set up hotkeys for mounting and unmounting volumes, providing a convenient way to access and secure your data with a simple keyboard shortcut.
By mastering the process of mounting and unmounting volumes, you can seamlessly access your encrypted data when needed and ensure that it remains protected when not in use.
Using TrueCrypt to Encrypt Files and Folders
TrueCrypt or its alternative provides a straightforward way to encrypt individual files and folders, allowing you to protect specific data while leaving the rest of your system untouched. Encrypting your files and folders adds an extra layer of security, ensuring that sensitive information remains confidential even if it falls into the wrong hands. Here’s how to use TrueCrypt to encrypt files and folders:
- Launch TrueCrypt and ensure the software is running.
- In the TrueCrypt main window, click on the “Select File” or “Select Folder” button, depending on whether you want to encrypt a file or a folder.
- Browse to locate the file or folder you want to encrypt.
- Click on the “Encrypt” button to initiate the encryption process.
- Choose the location where you want to save the encrypted file or folder.
- Enter a name for the encrypted file or folder. This name can be different from the original file or folder name.
- Set your preferred encryption algorithm, key size, and other encryption settings.
- Choose a strong password and, if desired, select any keyfile(s) to enhance the security of the encrypted file or folder.
- Click on the “OK” button to start the encryption process.
- Wait for the encryption process to complete. The time it takes will depend on the size of the file or folder and the encryption settings.
- Once the encryption is finished, you will have an encrypted version of your file or folder in the location you specified.
To access the encrypted file or folder, you will need to mount the TrueCrypt volume that contains it. Follow the steps for mounting a volume, and once the volume is mounted, you can access the encrypted file or folder as if it were a regular file or folder on your system.
It’s important to note that any changes made to the encrypted file or folder will be reflected in the decrypted version when the volume is mounted. This ensures that you can seamlessly work with your data while it remains protected.
By utilizing the encryption capabilities of TrueCrypt, you can safeguard specific files and folders, preserving the confidentiality and integrity of your sensitive information.
Encrypting an Entire Drive with TrueCrypt
In addition to encrypting individual files and folders, TrueCrypt or its alternative also offers the capability to encrypt entire drives, including system drives. Encrypting an entire drive ensures that all the data stored on the drive is securely protected from unauthorized access. Here’s a step-by-step guide on how to encrypt an entire drive with TrueCrypt:
- Launch TrueCrypt and make sure the software is running.
- In the TrueCrypt main window, click on the “System” menu and select “Encrypt System Partition/Drive” option.
- Follow the instructions in the Wizard to create a TrueCrypt Rescue Disk. This disk will be used to restore your system in case of emergencies.
- Choose whether you want to encrypt the system partition/drive or the entire system drive including the system partition.
- Select the drive you want to encrypt from the available options.
- Set your preferred encryption algorithm, key size, and other encryption settings.
- Choose a strong password and, if desired, select any keyfile(s) to enhance the security of the encrypted drive.
- Click on the “Encrypt” button to initiate the encryption process.
- Read and follow the instructions provided by the Wizard carefully.
- Wait for the encryption process to complete. This can take a significant amount of time depending on the size of the drive and the encryption settings.
- Once the encryption is finished, you will have an encrypted drive that requires authentication before it can be accessed.
After encrypting an entire drive, you will need to enter the password and, if applicable, provide any required keyfile(s) every time you start your computer. This ensures that the drive remains inaccessible to unauthorized users.
It’s crucial to keep the password and keyfile(s) secure and in a separate location from the encrypted drive to prevent unauthorized access and ensure data integrity.
Encrypting an entire drive with TrueCrypt provides an additional layer of security, protecting all the data stored on the drive and ensuring that even if the drive falls into the wrong hands, the information remains confidential and inaccessible.
Encrypting Your System Drive with TrueCrypt
Encrypting your system drive is an essential step to enhance the security and confidentiality of your entire operating system. With TrueCrypt or its alternative, you can encrypt the system drive, ensuring that all the data, files, and configuration settings are protected from unauthorized access. Here’s a step-by-step guide on how to encrypt your system drive using TrueCrypt:
- Launch TrueCrypt and make sure the software is running.
- In the TrueCrypt main window, click on the “System” menu and select “Encrypt System Partition/Drive” option.
- Follow the instructions in the Wizard to create a TrueCrypt Rescue Disk. This disk will be used to restore your system in case of emergencies.
- Choose whether you want to encrypt the system partition/drive or the entire system drive including the system partition.
- Select the system drive from the available options. It is important to note that encrypting the system drive requires administrative privileges.
- Set your preferred encryption algorithm, key size, and other encryption settings. It is recommended to use strong encryption algorithms like AES with a large key size for maximum security.
- Choose a strong password and, if desired, select any keyfile(s) to provide an additional layer of security.
- Click on the “Encrypt” button to initiate the encryption process.
- Follow the instructions provided by the TrueCrypt Wizard carefully.
- TrueCrypt will restart your computer and start the encryption process. The time required for encryption depends on the size of the system drive.
- You will be prompted to enter your password and, if applicable, provide any required keyfile(s) every time you start your computer to access the encrypted system drive.
- Once the encryption is complete, you will have a fully encrypted system drive, ensuring the protection of your operating system and all the data stored on it.
It is crucial to remember your password and, if applicable, keep any keyfile(s) secure and in a separate location from the encrypted system drive. This prevents unauthorized access and ensures the integrity of your encrypted system.
By encrypting your system drive with TrueCrypt, you add another layer of security to your operating system, keeping your sensitive data and personal information safe from potential threats and unauthorized access.
Backing Up and Restoring TrueCrypt Volumes
Regularly backing up your TrueCrypt volumes is crucial to ensure the safety and accessibility of your encrypted data. Backups serve as a precautionary measure in case of data loss, corruption, or hardware failures. Additionally, having a reliable backup strategy allows for easier restoration of encrypted volumes. Follow the steps below to back up and restore TrueCrypt volumes:
Backing Up TrueCrypt Volumes:
- Locate the TrueCrypt volume that you want to back up.
- Create a new folder or choose an existing folder on either an external storage device or a cloud service to store the backup.
- Copy and paste the TrueCrypt volume file to the designated backup folder.
- Ensure that you securely store the backup in a separate and safe location, ideally different from where the original volume is stored.
- Consider creating multiple backup copies or implementing a regular backup schedule to ensure redundancy and data protection.
Restoring TrueCrypt Volumes:
- Launch the TrueCrypt software and navigate to the location of your backup volume.
- Choose or create an appropriate location to restore the TrueCrypt volume. Ensure that there is sufficient storage space available.
- Copy and paste the backed-up TrueCrypt volume file to the desired location for restoration.
- Open the TrueCrypt software and click on the “Select File” button.
- Browse to locate the restored TrueCrypt volume file.
- Click on the “Mount” button to initiate the mounting process.
- Enter your password or provide the necessary keyfile(s) when prompted.
- Once successfully mounted, you can access the restored TrueCrypt volume and work with your data as before.
Regularly backing up your TrueCrypt volumes ensures that you have additional copies of your encrypted data, thus minimizing the risk of data loss or inaccessibility. If needed, restoring a TrueCrypt volume from a backup allows you to regain access to your encrypted files and folders quickly and efficiently.
Securely Deleting Files and Volumes
Properly and securely deleting files and volumes is essential to ensure that sensitive data cannot be recovered by unauthorized individuals. Simply deleting files or formatting volumes may not completely erase the data, as it can potentially be recovered using specialized software. TrueCrypt or its alternative provides reliable methods to securely delete files and volumes, making data recovery virtually impossible. Here are some guidelines on how to securely delete files and volumes:
Securely Deleting Files:
- Launch TrueCrypt and mount the volume that contains the file you want to securely delete.
- Navigate to the file you wish to delete and ensure that no other applications have the file open or in use.
- Select the file and press the “Delete” key or right-click and choose the “Delete” option.
- When prompted, select the option to securely delete the file. TrueCrypt will overwrite the file with random data, making it extremely difficult to recover.
Securely Deleting Volumes:
- Launch TrueCrypt and mount the volume that you want to securely delete.
- In the TrueCrypt main window, select the mounted volume from the drive list.
- Click on the “Volumes” menu and choose the “Permanently Decrypt” option.
- TrueCrypt will prompt you for confirmation. Ensure that you have backed up any important data inside the volume before proceeding.
- Follow the instructions provided by TrueCrypt to complete the process of permanently decrypting and deleting the volume.
By securely deleting files and volumes through TrueCrypt, you can rest assured that the data is effectively erased and cannot be recovered using conventional methods. It is crucial to note that securely deleting data is irreversible, so always exercise caution and double-check that you have backed up any valuable information before proceeding.
Remember that securely deleting files and volumes is an essential step in maintaining data privacy and preventing unauthorized access to sensitive information.
Best Practices for Using TrueCrypt
When using TrueCrypt or its alternative to encrypt your files and protect your sensitive data, it is important to follow best practices to ensure the highest level of security and usability. Here are some key guidelines to consider when using TrueCrypt:
- Choose strong passwords: Select passwords that are long, complex, and unique. Avoid using easily guessable information or common words.
- Enable two-factor authentication: Take advantage of TrueCrypt’s ability to use keyfiles in addition to passwords for an extra layer of security.
- Regularly back up your volumes: Create backups of your encrypted volumes to protect against data loss or corruption. Store the backups in a separate and secure location.
- Securely delete files: Use TrueCrypt’s secure file deletion feature to ensure that sensitive data is unrecoverable.
- Keep TrueCrypt software up to date: Stay informed about updates or security patches released for TrueCrypt or its alternative. Regularly update your software to benefit from the latest advancements and bug fixes.
- Protect against physical theft: If using a laptop or portable device, ensure it is adequately secured, and keep a backup of your TrueCrypt volumes in a separate location.
- Use caution when using public computers: Avoid accessing TrueCrypt volumes or entering passwords on public computers, as they may be compromised or infected with malware.
- Be cautious of phishing attempts: Beware of phishing scams or social engineering attacks that may attempt to trick you into revealing your TrueCrypt password or keyfiles.
- Report any vulnerabilities: If you discover any potential vulnerabilities or issues with TrueCrypt or its alternative, report them to the appropriate developers to help improve the security of the software.
- Stay informed: Keep yourself updated on the latest encryption techniques, security practices, and encryption software offerings. This will help you make informed decisions and further enhance your data protection.
Following these best practices will help you maintain a robust security posture when using TrueCrypt. By combining strong passwords, two-factor authentication, backups, and regular software updates, you can ensure the confidentiality and integrity of your encrypted data.
Remember to regularly review and update your security practices as technology evolves and new threats emerge.