Reasons to Encrypt Data on Your Mobile Device
With the increasing reliance on mobile devices for various activities, it has become crucial to prioritize data security. One of the most effective ways to safeguard your information is by encrypting the data on your Android or iOS device. Encryption is the process of converting your data into a form that is unreadable to anyone without the proper decryption key.
But why should you encrypt your mobile device data? Here are some compelling reasons:
- Protects Personal Information: Your mobile device often contains sensitive personal information such as banking details, credit card numbers, and social media login credentials. Encrypting your data ensures that this information is not easily accessible if your device falls into the wrong hands.
- Prevents Identity Theft: Encrypting your data makes it significantly harder for cybercriminals to steal your identity. Even if your device gets lost or stolen, the encrypted data will remain secure and unreadable.
- Safe Online Transactions: If you frequently make online transactions or access sensitive financial information through your mobile device, encryption provides an extra layer of security. It ensures that hackers cannot intercept your data as it travels over the internet.
- Safeguards Personal and Business Emails: Email communication can contain valuable information, ranging from personal conversations to business-related documents. Encrypting emails ensures that only the intended recipient can access the contents, protecting the privacy and confidentiality of the messages.
- Secures Stored Documents and Files: Many mobile devices have built-in storage options where you can save documents, photos, and other files. Encryption safeguards these files from unauthorized access, preventing sensitive information from leaking.
- Compliance with Regulations: In certain industries, such as finance and healthcare, there are strict regulations regarding the protection of customer data. Encryption helps ensure compliance with these regulations and protects both your reputation and legal standing.
Understanding Encryption
Encryption is a fundamental concept in data security that involves converting plain text or data into an unreadable format known as ciphertext. This transformation is achieved through the use of algorithms and encryption keys. Only individuals with the proper decryption key can revert the ciphertext back into its original format, rendering it readable.
There are two primary types of encryption: symmetric encryption and asymmetric encryption.
Symmetric Encryption: In symmetric encryption, the same key is used for both the encryption and decryption processes. This key is shared between the sender and the recipient, ensuring secure communication. Symmetric encryption algorithms, such as Advanced Encryption Standard (AES), are highly efficient and widely used.
Asymmetric Encryption: Asymmetric encryption, also known as public-key encryption, uses two different keys: the public key and the private key. The public key is available to everyone, while the private key is kept secret by the owner. When someone wants to send encrypted data, they use the recipient’s public key to encrypt the message. The recipient then uses their private key to decrypt the message. Popular algorithms for asymmetric encryption include RSA and Elliptic Curve Cryptography (ECC).
Encryption plays a crucial role in maintaining data privacy and security. It prevents unauthorized access to sensitive information and mitigates the risk of data breaches and identity theft. Additionally, encryption is vital for ensuring secure communication channels, both online and offline.
It’s important to note that encryption alone does not guarantee absolute security. It is just one piece of the puzzle in a comprehensive data protection strategy. Other measures, such as strong passwords, regular software updates, and secure network connections, should also be implemented to enhance overall security.
Android Encryption Options
Android devices offer several encryption options that enhance the security of your data. These options provide different levels of protection and can be tailored to suit your specific needs. Let’s explore some of the Android encryption options:
- Full Disk Encryption (FDE): This is the default encryption option available on most Android devices. FDE encrypts the entire device’s storage, including system files, apps, and media. It ensures that all data remains secure, even if the device is lost or stolen. FDE requires you to set a secure lock screen password, PIN, or pattern, as this serves as the encryption key.
- File-Based Encryption (FBE): Introduced in Android 7.0 Nougat, FBE encrypts each user’s data individually. This means that each user profile on a multi-user device has its own encryption key. FBE provides enhanced security by preventing one user from accessing another user’s data. It also allows for more flexibility in managing encrypted files.
- Secure Folder: Some Android devices, such as Samsung Galaxy phones, have a feature called Secure Folder. It creates a separate, encrypted space on your device where you can store sensitive data, such as photos, documents, and apps. To access the Secure Folder, you need to provide a separate passcode or biometric authentication.
- SD Card Encryption: If your device supports expandable storage via an SD card, you can encrypt the data stored on the card. This prevents unauthorized access to the contents of the card, even if it is removed from the device. To enable SD card encryption, go to the device settings and navigate to the storage settings.
- App-level Encryption: Some apps offer their own encryption options to protect specific data or files within the app. For example, password managers and secure messaging apps often provide end-to-end encryption for the data they store or transmit. Check the settings of individual apps to see if they offer any encryption features.
Android encryption options provide a robust defense against data breaches and unauthorized access. It is recommended to enable encryption on your Android device to keep your personal and sensitive information secure.
Setting Up Encryption on an Android Device
Enabling encryption on your Android device is a straightforward process that ensures the security of your data. Here are the steps to set up encryption on an Android device:
- Before you start, it is crucial to back up your device and ensure that the battery is charged.
- Go to the device settings by swiping down from the top of the screen and tapping the gear icon or by accessing the settings app from the app drawer.
- Scroll down and select the “Security” or “Lock Screen & Security” option.
- Look for the “Encrypt Device” or “Encrypt Phone” option. Note that the exact label may vary depending on the Android version and device model.
- Tap on the encryption option, and you will be prompted to set a secure lock screen PIN, password, or pattern if you haven’t already.
- Follow the on-screen instructions to complete the encryption process. This may take some time, so make sure your device is plugged in or has sufficient battery life.
- Once the encryption process is complete, your device will require the lock screen credentials every time you power it on or unlock it.
It is important to note that encrypting your device may cause a slight performance impact, as the system needs to decrypt the data in real-time when it is accessed. However, modern devices are equipped to handle encryption without significant usability issues.
Remember to choose a strong and unique lock screen PIN, password, or pattern to further enhance the security of your encrypted device.
If you ever decide to disable encryption, you can do so by following the same steps outlined above and selecting the “Decrypt Device” or “Decrypt Phone” option. However, keep in mind that disabling encryption will expose your data to potential security risks, so only do it if absolutely necessary.
Encryption on iOS Devices
iOS devices, such as iPhones and iPads, come with built-in encryption features that ensure the security of your data. Apple has prioritized user privacy and includes robust encryption protocols to protect sensitive information. Here’s an overview of encryption on iOS devices:
- Data Protection: iOS devices employ a feature called Data Protection, which uses a combination of hardware and software encryption. This means that your data is automatically encrypted when your device is locked. Data Protection uses your passcode as the encryption key, making it nearly impossible for unauthorized access to your data.
- iMessage and FaceTime: Apple’s encrypted messaging and calling services, iMessage and FaceTime, use end-to-end encryption. This means that the content of your messages or calls is encrypted in transit and can only be decrypted by the intended recipient. This ensures that your conversations remain private and secure.
- iCloud Backup: When you back up your iOS device to iCloud, the backup is encrypted before being uploaded to the cloud. This means that even if a third party gains access to your iCloud backup, they won’t be able to read the contents without the proper encryption key.
- Secure Enclave: iOS devices that have a Touch ID or Face ID feature are equipped with a specialized chip called the Secure Enclave. It stores sensitive information, such as your biometric data or passcode, securely on the device. The Secure Enclave ensures that even Apple cannot access your data, further protecting your privacy.
- App-level Encryption: Many apps available on the App Store implement their own encryption methods to protect your data. This includes password managers, secure note-taking apps, and document storage apps. Look for apps that explicitly mention end-to-end encryption or data encryption in their privacy and security features.
Encryption on iOS devices is designed to prioritize user privacy and protect sensitive data. By default, iOS devices offer strong encryption to ensure that your personal information remains secure from unauthorized access.
It is important to regularly update your iOS device to the latest software version to benefit from the latest security patches and enhancements. Additionally, enable a secure lock screen passcode or biometric authentication to further enhance the security of your device.
Enabling Encryption on an iPhone or iPad
Enabling encryption on your iPhone or iPad is a crucial step in securing your data and maintaining your privacy. Apple has made it easy to enable encryption on iOS devices. Here’s how you can enable encryption:
- Before proceeding, ensure that your device is updated to the latest iOS version to benefit from the latest encryption features and security patches.
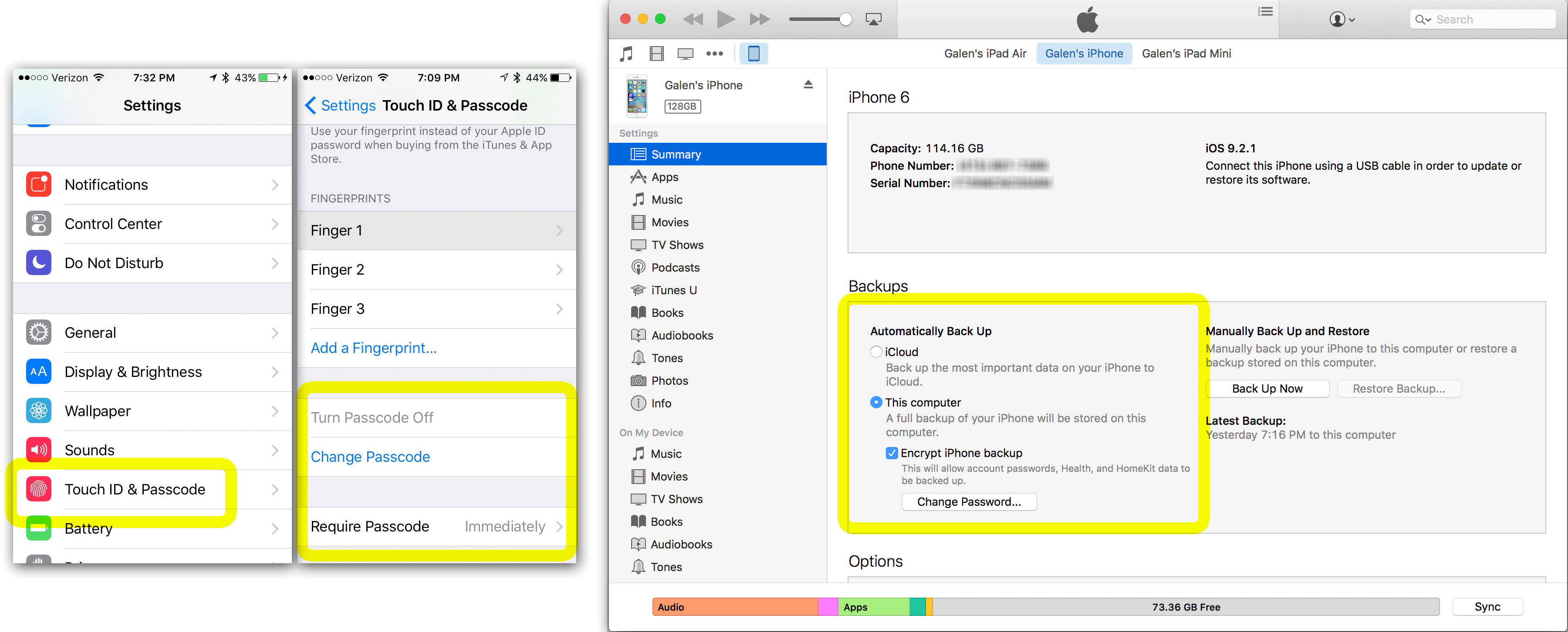
- Go to the “Settings” app on your device by tapping on the gear icon located on the home screen.
- Scroll down and tap on the “Touch ID & Passcode” or “Face ID & Passcode” option, depending on your device model.
- If prompted, enter your device passcode to access the passcode settings.
- Scroll down and look for the “Data Protection” or “Encrypt iPhone Backup” option. Tap on it to enable encryption.
- Follow the on-screen instructions to create a secure backup password. This password will be used to encrypt and decrypt your backup data. Choose a strong and unique password that you will remember, as losing this password may result in permanent data loss.
- Once you have set a backup password, the encryption process will begin. This process may take some time, depending on the amount of data on your device.
- When the encryption process is complete, your device backups will be encrypted, ensuring that your data remains secure.
It’s important to note that enabling encryption for device backups is not the same as encrypting the entire device. To encrypt the entire device, you need to set a passcode or use biometric authentication (such as Touch ID or Face ID) on your device. This will activate the device’s built-in encryption features.
By enabling encryption on your iPhone or iPad, you add an additional layer of security to prevent unauthorized access to your data. It ensures that even if your device is lost or stolen, your personal information remains protected.
Remember to regularly back up your encrypted device using iTunes or iCloud to ensure that your data is securely stored and accessible in case of any unforeseen circumstances.
Choosing the Right Encryption Method
When it comes to encryption, selecting the right method is crucial to ensure the security and integrity of your data. There are various encryption methods available, each with its own strengths and use cases. Here are some factors to consider when choosing the right encryption method:
- Security Level: Assess the sensitivity of the data you want to encrypt. For highly confidential information, such as financial or medical records, opt for strong encryption methods like AES-256 or RSA encryption. These algorithms provide robust security and are widely recognized.
- Key Management: Consider how the encryption keys will be managed. Symmetric encryption requires the same key for both encryption and decryption, so key distribution and protection are critical. Asymmetric encryption, on the other hand, uses a public key for encryption and a private key for decryption, simplifying key management to some extent.
- Performance: Evaluate the performance impact of the encryption method. Some encryption algorithms, particularly those with long key lengths, can be computationally intensive and may slow down data processing. Choose an encryption method that strikes a balance between security and performance for your specific use case.
- Platform Compatibility: Consider the platforms or devices that need to work with the encrypted data. Ensure that the chosen encryption method is compatible with the platforms you are using, whether it is Android, iOS, Windows, or others.
- Industry Standards and Compliance: If you work in an industry with specific data security regulations, ensure that the chosen encryption method meets the required standards. Industries like finance and healthcare often have strict compliance requirements, and using approved encryption methods is essential.
- Future-proofing: Look for encryption methods that have withstood the test of time and are widely accepted in the security community. Choosing established and well-vetted algorithms increases the likelihood of long-term compatibility, support, and resilience against emerging threats.
It’s important to note that encryption methods alone will not provide complete security. Implementing key management best practices, regularly updating software and systems, and maintaining strong access controls are essential components of a comprehensive security strategy.
Consider consulting with a security professional or conducting thorough research to select the encryption method that best fits your specific needs. By selecting the right encryption method, you can ensure the confidentiality and integrity of your data, protecting it from unauthorized access and potential threats.
Managing Encrypted Data on Your Mobile Device
Properly managing encrypted data on your mobile device is essential to maintain data security and accessibility. Here are some important considerations for managing encrypted data:
- Backup and Recovery: It is crucial to regularly back up your encrypted data to prevent data loss. Utilize encrypted backup options provided by your device’s operating system or trusted third-party applications. This ensures that you have a secure copy of your data in case of device loss, damage, or other unforeseen circumstances.
- Password and Key Management: Safeguard your encryption keys and passwords. Choose strong, unique, and complex passwords or passphrases for your encrypted data. Consider using a password manager to securely store and manage your passwords. Additionally, keep your device lock screen password or PIN confidential and avoid using easily guessable combinations.
- Software Updates: Keep your mobile device’s operating system and encryption-related software up to date. Regularly install updates and security patches provided by the device manufacturer or trusted software vendors. These updates often address vulnerabilities and enhance encryption protocols, bolstering the overall security of your encrypted data.
- Data Sharing and Transmission: Be cautious when sharing or transmitting encrypted data. Ensure that the recipients of the data have access to the necessary encryption keys or passwords to decrypt the information. Consider using secure channels, such as encrypted messaging apps or secure file transfer protocols, for transmitting sensitive encrypted data.
- Regular Security Audits: Periodically review your device’s security settings and encryption configurations. Conduct security audits to identify any vulnerabilities or misconfigurations that could compromise the security of your encrypted data. Consult with cybersecurity professionals or utilize security assessment tools to ensure proper encryption implementation.
- Data Disposal: When disposing of an encrypted mobile device, it is important to properly erase all data. Follow manufacturer guidelines for factory resetting, which typically includes securely wiping all stored data and encryption keys. This prevents unauthorized access to your encrypted data after you no longer possess the device.
By following these best practices, you can effectively manage your encrypted data and mitigate the risk of unauthorized access or data loss. Remember that encryption is just one aspect of a comprehensive data security strategy, so it is important to implement other security measures like strong access controls, network security, and user awareness to further protect your data.
Frequently Asked Questions about Mobile Device Encryption
Mobile device encryption is a topic that can raise several questions. Here are answers to some commonly asked questions about mobile device encryption:
- What is mobile device encryption?
Mobile device encryption is the process of converting data on a mobile device into an unreadable format using encryption algorithms. This ensures that even if the device is lost, stolen, or accessed by unauthorized individuals, the data remains secure and protected. - Why is mobile device encryption important?
Mobile device encryption is important because it prevents unauthorized access to sensitive information, such as personal data, financial records, or confidential business data. Encrypting your mobile device safeguards your data, ensuring privacy, and protecting against identity theft and data breaches. - How does mobile device encryption work?
Mobile device encryption works by mathematically transforming data into ciphertext using encryption algorithms. This transformation makes the data unreadable without the encryption key. Encryption keys are either derived from a user’s passcode or created during initialization. When the device is unlocked or when the correct passcode is entered, the data is decrypted and made readable. - Does mobile device encryption impact device performance?
Enabling encryption on a mobile device can cause a slight performance impact, as the device needs to decrypt data in real-time. However, with modern devices and efficient encryption algorithms, the impact on typical device operations is minimal and often goes unnoticed by the user. - Can encrypted data be recovered if the encryption key is lost?
If the encryption key is lost and there is no way to recover it, the encrypted data is essentially rendered permanently inaccessible. This is why it is important to securely manage encryption keys and keep backup copies in a safe and accessible location. - Can encrypted data be decrypted without the encryption key?
Without the correct encryption key, it is extremely difficult, if not impossible, to decrypt encrypted data. Modern encryption algorithms are designed with highly secure encryption methods, making it infeasible to decrypt the data without the key.
Mobile device encryption is a vital security measure that protects sensitive data from unauthorized access. It ensures privacy, and in the event of device loss or theft, mitigates the risk of data breaches. By understanding mobile device encryption and its significance, users can take the necessary steps to secure their data effectively.