Understanding Firewalls
A firewall is a network security device that acts as a barrier between your computer or network and the internet. Its primary function is to monitor and control incoming and outgoing network traffic based on predetermined security rules. By doing so, it helps protect your system from unauthorized access, malicious activities, and potential threats.
Firewalls can be implemented in different forms, including software-based firewalls that run on individual computers, hardware-based firewalls that are installed on network routers, and cloud-based firewalls provided by internet service providers or security companies. Regardless of the form, the fundamental purpose of a firewall remains the same: to control traffic flow and ensure the security of your network.
Firewalls work by examining each packet of data that enters or leaves your network. They analyze information such as the source and destination IP addresses, port numbers, and protocol types to determine whether to allow or block the data. Think of a firewall as a gatekeeper that filters the data traffic based on predefined rules and policies.
There are two main types of firewalls: inbound firewalls and outbound firewalls. Inbound firewalls protect your network by filtering incoming traffic, while outbound firewalls monitor and control outgoing traffic. Both types work together to create a secure network environment.
In addition to traffic filtering, firewalls offer various other security features. These may include intrusion detection and prevention systems, virtual private network (VPN) support, and deep packet inspection. These additional features enhance the overall security of your network and protect against advanced threats.
It is important to note that while firewalls are an essential component of network security, they are not foolproof. They provide an important layer of defense, but they should be complemented with other security measures, such as antivirus software, regular system updates, and user education on safe browsing practices.
Now that you have a basic understanding of firewalls, let’s explore why it is crucial to allow programs through a firewall and how to do it on different operating systems.
Why You Need to Allow Programs Through a Firewall
A firewall acts as a protective barrier between your computer or network and the outside world. It is designed to block unauthorized access and filter network traffic. However, there are instances where you may need to allow certain programs through the firewall. Here’s why:
1. Communication and functionality: Some programs require internet access to function properly. This includes software that relies on online updates, cloud-based applications, and programs that need to communicate with servers or other devices over the network. By allowing these programs through the firewall, you ensure their uninterrupted functionality and enable them to establish the necessary connections.
2. Software updates and patches: Many software vendors release regular updates and security patches to address vulnerabilities and improve performance. Allowing these updates through the firewall ensures that your programs stay up to date, enhancing their stability and protection against potential threats. Without allowing these updates, your software may become outdated and susceptible to security breaches.
3. Collaborative work and remote access: In today’s digital age, collaboration and remote access have become commonplace. Allowing programs through the firewall enables seamless collaboration between team members, regardless of their physical location. Remote desktop software, virtual private network (VPN) clients, and video conferencing applications are examples of programs that may require access through the firewall to establish secure connections and facilitate remote work.
4. Gaming and online entertainment: Online gaming, streaming services, and other forms of online entertainment often require access to specific ports and protocols. By allowing these programs through the firewall, you ensure a smooth gaming or streaming experience, as the necessary network traffic is not blocked. It is important to note that while allowing these programs may be necessary for functionality, it is crucial to exercise caution and only allow trusted and legitimate applications.
5. Custom applications and services: In some cases, you may be using custom-developed applications or services that require network access. These could be proprietary software solutions, web applications, or specialized services specific to your industry. Allowing these programs through the firewall is necessary for them to function as intended and provide the desired service to your organization.
By allowing programs through the firewall, you strike a balance between network security and the functionality and productivity of your systems. However, it is essential to carefully consider the programs you allow and ensure that they come from trusted sources. Additionally, keeping your firewall rules up to date and regularly reviewing the allowed programs is crucial to maintain a secure and well-protected network environment.
Steps to Allow a Program Through Windows Firewall
Windows Firewall is a built-in security feature in Windows operating systems that helps protect your computer from unauthorized access. To allow a program through Windows Firewall, follow these steps:
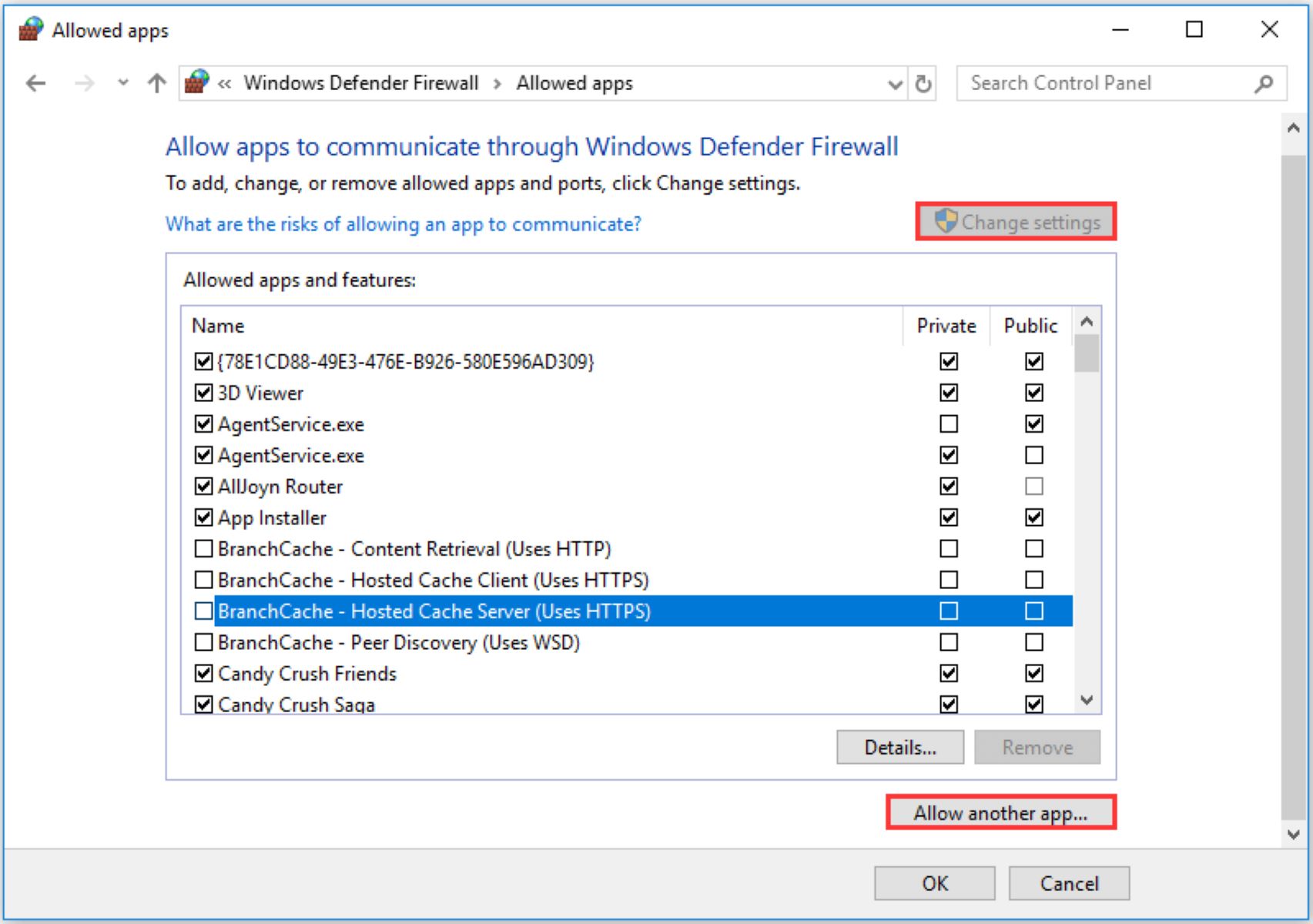
- Open the Windows Start menu and search for “Windows Security” or “Windows Defender Firewall”. Click on the corresponding result to open the Windows Security app.
- In the Windows Security app, click on the “Firewall & network protection” option.
- Click on the “Allow an app through firewall” or “Allow an app or feature through Windows Defender Firewall” option.
- A list of allowed apps and features will appear. Click on the “Change settings” button, which may require administrator permission.
- To allow a new program, click on the “Allow another app” or “Allow another program” button.
- A new window will appear, displaying a list of installed programs. If the desired program is listed, select it and click “Add”. If the program is not listed, click on the “Browse” button to locate the program’s executable file on your computer.
- After selecting the program, make sure that the checkboxes for both “Private” and “Public” networks are checked. This will allow the program to communicate on both private and public networks, depending on your network settings and preferences.
- Click “OK” to save the changes and exit the settings window.
Your selected program is now allowed through Windows Firewall, and it will be able to establish network connections as needed. It is important to note that allowing a program through the firewall does grant it network access, so exercise caution and only allow programs that are trustworthy and necessary for your system’s functionality.
Remember that these instructions may differ slightly depending on the version of Windows you are using. If you encounter any difficulties, consult the official Microsoft documentation or seek additional support from the Windows community.
Steps to Allow a Program Through Mac Firewall
The macOS operating system includes a built-in firewall called “Firewall Options” that helps protect your Mac from unauthorized network connections. To allow a program through the Mac firewall, follow these steps:
- Open the Apple menu and select “System Preferences”.
- In the System Preferences window, click on “Security & Privacy”.
- Click on the “Firewall” tab.
- Click on the lock icon in the bottom left corner of the window and enter your administrator password to make changes.
- Click on the “Firewall Options” button.
- In the Firewall Options window, click on the “+” symbol to add a new program or application.
- Browse through your applications and select the program you want to allow through the firewall. You can usually find applications in the “Applications” folder on your Mac.
- After selecting the program, click “Add” to add it to the allowed program list or click “OK” to save your changes. If necessary, repeat the process to add more programs.
- Close the Firewall Options window, and your selected programs will now be allowed through the Mac firewall.
Note that allowing a program through the firewall grants it network access, so only allow programs that you trust and that are necessary for your system’s functionality. It is recommended to regularly review the allowed programs and remove any that are no longer needed.
These instructions may vary slightly depending on the version of macOS you are using. If you encounter any issues or need further assistance, consult the official Apple documentation or seek support from the Mac user community.
Steps to Allow a Program Through Linux Firewall
Linux distributions typically come with a firewall system called iptables or a newer alternative called nftables. The specific steps for allowing a program through the Linux firewall may vary depending on the distribution and version you are using. However, the general process involves the following steps:
- Open a terminal window on your Linux system.
- Depending on your distribution, you may need to switch to the root user or use the sudo command to run commands with administrative privileges.
- Identify the firewall management tool that your Linux distribution uses. The most common tools are iptables and nftables. You can check which tool is being used by running the appropriate command, such as
iptables -Vfor iptables ornft --versionfor nftables. - Construct the necessary rule to allow the program through the firewall. This typically involves specifying the program’s port number and the protocol it uses (such as TCP or UDP).
- Enter the command to add the rule to the firewall configuration. For example, if you are using iptables, the command might be something like
iptables -A INPUT -p tcp --dport 80 -j ACCEPT, which allows incoming traffic on port 80 for the TCP protocol. - Repeat the process for any additional ports or protocols that the program requires.
- Save the firewall rules so that they persist across reboots. The method for doing this can vary depending on the Linux distribution. Some distributions use the iptables-save or nft list rules commands, while others may have specific configuration files where you need to add the rules manually.
It’s important to note that the command syntax and configuration locations may differ between distributions and versions of Linux. It is recommended to consult the documentation specific to your distribution or seek guidance from the Linux community for detailed instructions.
Additionally, it’s crucial to exercise caution when modifying your firewall configuration. Incorrectly configuring the firewall rules can result in unintended security vulnerabilities or disruption to your network communication. If you are unsure or uncomfortable with modifying the firewall settings manually, consider utilizing a user-friendly firewall management tool or seeking assistance from a knowledgeable Linux administrator.
Troubleshooting Common Issues
While allowing a program through a firewall is typically a straightforward process, there are occasional issues that can arise. Here are some common problems you may encounter and possible solutions:
1. Program still blocked: After following the steps to allow a program through the firewall, you might find that the program is still being blocked. Double-check that you have correctly added the program to the allowed list and that the firewall settings are properly configured. Additionally, ensure that there are no conflicting rules or other security measures blocking the program’s access.
2. Incorrect port or protocol: If a program relies on specific ports or protocols, ensure that you have correctly specified them when configuring the firewall rules. Confirm the required ports and protocols with the program’s documentation or the vendor’s support resources.
3. Different firewall software: If you are using a third-party firewall software instead of the default system firewall, the steps for allowing a program through the firewall may differ. Consult the documentation provided by the firewall software vendor for specific instructions.
4. Multiple network profiles: Some operating systems, such as Windows, have different network profiles (such as “Public” and “Private”) with separate firewall settings. Make sure you are allowing the program through the appropriate network profile to ensure its access in the desired network environment.
5. Firewall conflicts: If you have multiple firewalls or security software installed on your system, they may conflict with each other and cause issues. Verify that there are no conflicting firewall rules or overlapping security measures that could prevent the program from accessing the network.
6. Firewall rule order: In some cases, the order of the firewall rules can affect their effectiveness. Ensure that the rule allowing the program through the firewall is placed correctly within the rule hierarchy. If necessary, adjust the rule order to prioritize the program’s access.
7. Restarting the program: If you have made changes to the firewall settings while the program was running, try restarting the program. This can ensure that it applies the new firewall permissions and establishes the necessary network connections.
8. Administrative privileges: Depending on your operating system, certain firewall configurations may require administrative privileges. Make sure you have the necessary privileges to modify firewall settings and add rules.
If you encounter persistent issues or are unsure how to resolve a specific problem, it is recommended to consult the official documentation for your operating system or seek support from the vendor or a qualified IT professional. They can provide guidance specific to your system configuration and help troubleshoot any complex issues related to program access through the firewall.
Other Considerations for Allowing Programs Through a Firewall
When allowing programs through a firewall, there are some additional considerations to keep in mind in order to maintain a secure and well-functioning network environment:
1. Regularly review and update firewall rules: It’s important to periodically review the programs that are allowed through the firewall. Remove any programs that are no longer necessary or trusted to reduce the attack surface and minimize potential security risks.
2. Practice the principle of least privilege: Only allow programs that require network access. Avoid a “blanket allowance” approach where all programs have unrestricted access through the firewall. By granting minimal access privileges, you reduce the potential for unauthorized communication and minimize the impact of compromised programs.
3. Monitor network traffic: Use network monitoring tools or intrusion detection systems to monitor incoming and outgoing network traffic. This can help detect any suspicious or unauthorized activities and alert you to potential security breaches.
4. Keep programs updated: Ensure that all programs allowed through the firewall are regularly updated. Outdated programs may have known vulnerabilities that can be exploited by attackers. Keeping programs up to date with the latest patches and security updates is crucial for maintaining a secure system.
5. Enable logging and review logs: Enable firewall logging and regularly review the logs to identify any unusual or unauthorized access attempts. Log analysis can provide valuable insights into network activity and help detect and respond to potential security incidents.
6. Use additional security layers: While firewalls are an important security measure, they are not the only line of defense. Complement the firewall with other security layers such as antivirus software, intrusion detection systems, and strong password policies to create a comprehensive security posture.
7. Educate users: User awareness and education play a critical role in network security. Train users on safe computing practices, such as avoiding suspicious downloads, being cautious with email attachments, and practicing good password hygiene. This minimizes the risk of accidentally executing malicious programs and decreases the chances of firewall breaches.
8. Test firewall configurations: Periodically test the effectiveness of your firewall configurations by conducting penetration testing or vulnerability scanning. This can help identify any potential weaknesses in your firewall rules and ensure that they are properly configured to protect your network.
By considering these additional factors when allowing programs through your firewall, you can strengthen your network security and ensure that your systems remain protected from unauthorized access and potential threats.