The Evolution of iPhone Security Features
The evolution of iPhone security features has been a remarkable journey, marked by a relentless pursuit of innovation and excellence. From the early days of passcodes to the introduction of Touch ID and the latest advancement in biometric authentication with Face ID, Apple has consistently raised the bar for smartphone security.
In 2013, Apple revolutionized the way users interacted with their iPhones by introducing Touch ID, a fingerprint recognition system that provided a convenient and secure method for unlocking devices and authorizing transactions. This breakthrough technology not only enhanced user convenience but also set a new standard for biometric authentication in the smartphone industry.
Building on the success of Touch ID, Apple continued to push boundaries with the introduction of Face ID in 2017. This sophisticated facial recognition system brought a new level of security and convenience to iPhone users. By leveraging advanced technologies such as depth-sensing cameras and neural networks, Face ID redefined the authentication experience, allowing users to unlock their devices and authenticate secure transactions with just a glance.
The integration of Face ID into the iPhone 12 represents the culmination of years of research and development, showcasing Apple's unwavering commitment to enhancing user privacy and security. With Face ID, iPhone 12 users can enjoy a seamless and intuitive authentication process that adapts to changes in their appearance over time, ensuring reliable and secure access to their devices and sensitive data.
As the iPhone continues to evolve, it is evident that Apple's dedication to security remains a top priority. The evolution of iPhone security features reflects a proactive approach to staying ahead of emerging threats and addressing the evolving needs of users in an increasingly digital world. With each iteration, Apple continues to refine and elevate the security capabilities of its devices, setting a benchmark for the industry and empowering users with confidence in the protection of their personal information.
The journey from passcodes to Touch ID and Face ID underscores Apple's relentless pursuit of innovation and its unwavering commitment to redefining the standards of smartphone security. As technology advances and new challenges emerge, Apple's legacy of pioneering security features ensures that iPhone users can embrace the future with confidence, knowing that their devices are equipped with the most advanced and reliable security measures available.
Understanding Face ID Technology
Face ID technology represents a groundbreaking leap in biometric authentication, leveraging advanced hardware and software to deliver a seamless and secure user experience. At its core, Face ID utilizes the TrueDepth camera system, which is meticulously engineered to capture precise facial data with remarkable accuracy. This sophisticated system consists of an infrared camera, a flood illuminator, a dot projector, and a front camera, working in harmony to create a detailed depth map of the user's face.
The infrared camera plays a pivotal role in Face ID's functionality, as it is capable of capturing infrared images even in low-light conditions. This enables Face ID to operate reliably in various lighting environments, ensuring consistent performance regardless of the surrounding conditions. The flood illuminator further enhances the system's capabilities by projecting infrared light onto the user's face, allowing the infrared camera to accurately capture facial features, even in complete darkness.
The dot projector is a key component that contributes to the exceptional accuracy of Face ID. By projecting thousands of invisible infrared dots onto the user's face, the dot projector creates a precise three-dimensional map, capturing the unique contours and features of the user's facial structure. This intricate mapping process enables Face ID to recognize even subtle changes in the user's appearance, ensuring reliable authentication in diverse scenarios.
The front camera, equipped with advanced technologies, works in tandem with the other components to capture high-resolution images of the user's face. This comprehensive facial data, combined with depth information generated by the TrueDepth camera system, forms the foundation for Face ID's robust and secure authentication process.
In addition to the hardware components, Face ID relies on sophisticated algorithms powered by neural networks to process and analyze facial data. These algorithms adapt to the user's facial changes over time, continuously refining the facial recognition process to maintain high accuracy and security. By leveraging machine learning capabilities, Face ID can distinguish between real faces and replicas, providing a formidable defense against unauthorized access attempts.
The integration of hardware and software in Face ID technology exemplifies Apple's unwavering commitment to delivering a secure and user-centric authentication solution. With its ability to adapt to various environmental factors and its advanced depth-sensing capabilities, Face ID sets a new standard for biometric authentication, offering a seamless and intuitive user experience while upholding uncompromising security standards.
How to Set Up Face ID on iPhone 12
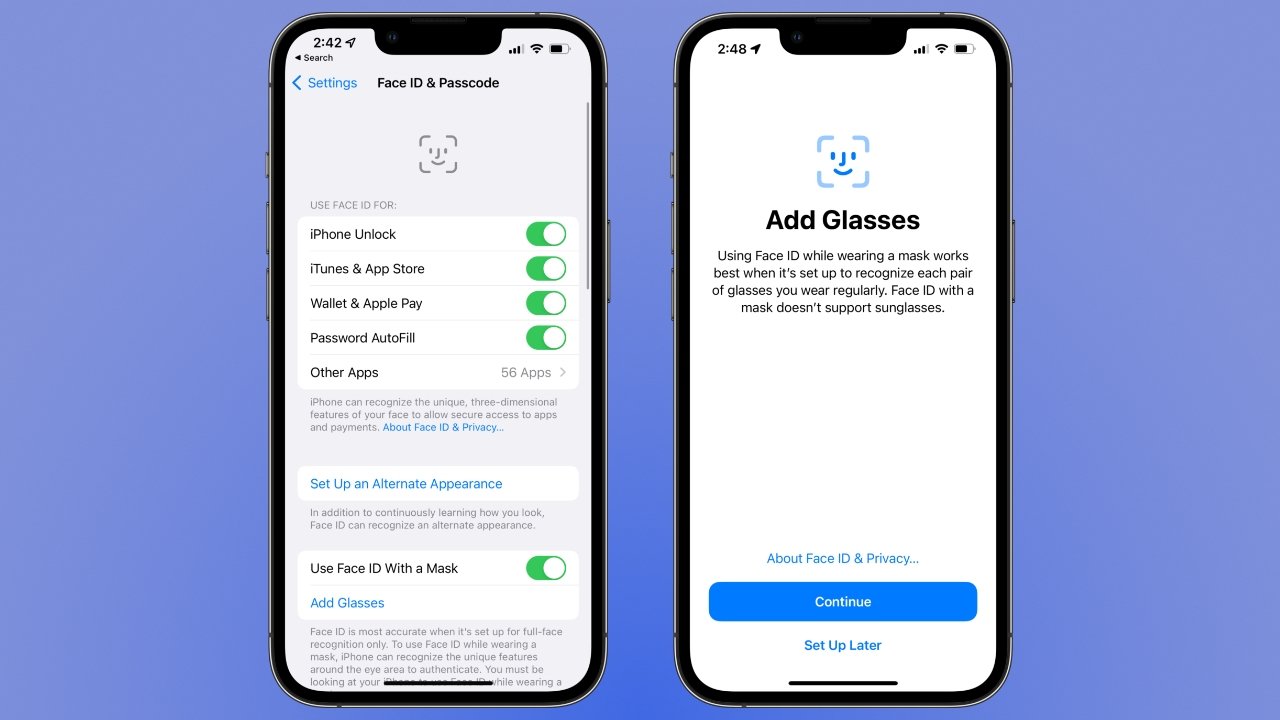
Setting up Face ID on your iPhone 12 is a straightforward process that empowers you to experience the seamless convenience and enhanced security offered by this advanced biometric authentication technology. To begin, navigate to the "Settings" app on your iPhone 12 and select "Face ID & Passcode." You will be prompted to enter your device passcode to proceed.
Once you have entered your passcode, select "Set Up Face ID" to initiate the setup process. Position your face within the frame on the screen, ensuring that it is clearly visible and well-lit. The TrueDepth camera system will then capture a detailed image of your face, mapping its unique contours and features with precision.
During the setup, you will be instructed to perform specific movements, such as gently moving your head in a circular motion. This allows the TrueDepth camera to capture different angles of your face, enhancing the accuracy and adaptability of Face ID. The setup process is designed to comprehensively capture your facial data, enabling Face ID to recognize you from various perspectives and under different lighting conditions.
After the initial scan is complete, you will be prompted to repeat the process for a second time to ensure thorough and accurate facial mapping. Once both scans are successfully completed, Face ID will be fully set up and ready for use.
It is important to note that Face ID is designed to continuously adapt to changes in your appearance, such as hairstyles, facial hair, and accessories. This adaptive capability ensures that Face ID remains reliable and secure, even as your appearance evolves over time.
Upon completing the setup, you can immediately begin using Face ID to unlock your iPhone 12, authenticate secure transactions, and access protected apps and data. The seamless integration of Face ID into the iPhone 12's user interface enhances the overall user experience, offering a swift and intuitive authentication process that prioritizes both security and convenience.
By following these simple steps to set up Face ID on your iPhone 12, you can unlock the full potential of this cutting-edge biometric authentication technology, enjoying a heightened level of security and a frictionless user experience that aligns with Apple's commitment to innovation and user-centric design.
Using Face ID for Secure Authentication
Using Face ID for secure authentication on the iPhone 12 represents a paradigm shift in the way users interact with their devices. The seamless integration of Face ID into the authentication process elevates security to a new level while enhancing the overall user experience.
Upon activating the iPhone 12, Face ID immediately engages, scanning the user's face with remarkable precision. This swift and effortless authentication method eliminates the need for manual input, providing a frictionless experience that aligns with Apple's commitment to user-centric design.
The robust security measures embedded within Face ID ensure that unauthorized access attempts are effectively thwarted. By leveraging advanced depth-sensing technologies and neural networks, Face ID distinguishes between the user's authentic face and unauthorized replicas, offering a formidable defense against fraudulent access.
Furthermore, Face ID adapts to changes in the user's appearance over time, ensuring that variations in hairstyles, facial hair, and accessories do not compromise the authentication process. This adaptive capability underscores the reliability and resilience of Face ID, reinforcing its position as a secure and user-friendly authentication solution.
In addition to unlocking the device, Face ID extends its secure authentication capabilities to various applications and services, safeguarding sensitive data and transactions. Whether authorizing app installations, authenticating Apple Pay transactions, or accessing password-protected content, Face ID seamlessly integrates security into every interaction, empowering users with confidence in the protection of their personal information.
The convenience of using Face ID for secure authentication is further exemplified by its intuitive and versatile functionality. With a simple glance, users can effortlessly unlock their devices and access protected content, streamlining their daily interactions with the iPhone 12. This streamlined authentication process not only enhances user convenience but also reinforces the robust security posture of the device.
By embracing Face ID for secure authentication, users can experience a seamless and intuitive interaction with their iPhone 12, underpinned by uncompromising security measures. The integration of advanced biometric authentication technology into the fabric of the device reflects Apple's unwavering commitment to delivering a secure, user-centric, and innovative user experience.
In essence, leveraging Face ID for secure authentication on the iPhone 12 transcends traditional security paradigms, ushering in a new era of effortless yet robust user authentication that aligns with the evolving needs and expectations of modern smartphone users.
Advantages and Limitations of Face ID
Face ID, as a cutting-edge biometric authentication technology integrated into the iPhone 12, offers a host of advantages that redefine the user authentication experience. At the same time, it is important to acknowledge the limitations that accompany this innovative technology.
Advantages of Face ID
-
Unparalleled Security: Face ID leverages advanced depth-sensing technologies and neural networks to provide a highly secure authentication method. The intricate facial mapping process, combined with adaptive machine learning algorithms, distinguishes the user's authentic face from unauthorized replicas, offering robust protection against unauthorized access attempts.
-
Seamless User Experience: The integration of Face ID into the authentication process of the iPhone 12 delivers a seamless and intuitive user experience. With a simple glance, users can effortlessly unlock their devices, access protected content, and authorize secure transactions, eliminating the need for manual input and streamlining daily interactions with the device.
-
Adaptive Capability: Face ID adapts to changes in the user's appearance over time, ensuring reliable authentication even as hairstyles, facial hair, and accessories evolve. This adaptive capability enhances user convenience while maintaining the integrity of the authentication process.
-
Versatile Application: Beyond device unlocking, Face ID extends its secure authentication capabilities to various applications and services, including Apple Pay transactions, app installations, and password-protected content. This versatile application of Face ID reinforces its role as a comprehensive security solution.
Limitations of Face ID
-
Dependence on Line of Sight: Face ID requires the user's face to be within the line of sight of the TrueDepth camera for authentication. This may pose a limitation in scenarios where the device is positioned at an angle or when the user's face is partially obstructed.
-
Challenges in Certain Conditions: While Face ID performs reliably in various lighting conditions, including low-light environments, it may encounter challenges in extremely bright or direct sunlight, potentially impacting the authentication process.
-
Multiple User Support: Face ID is designed to recognize the primary user's face, which may present limitations in scenarios where multiple users share the same device and require individualized authentication.
-
Privacy Concerns: Although Face ID is engineered with a strong emphasis on user privacy and data security, some individuals may have privacy concerns related to the collection and storage of facial data for authentication purposes.
In summary, the advantages of Face ID, including its robust security, seamless user experience, adaptive capability, and versatile application, position it as a formidable biometric authentication solution. However, it is essential to consider the limitations associated with Face ID, such as its dependence on line of sight, challenges in certain conditions, multiple user support, and privacy concerns, to gain a comprehensive understanding of its capabilities and considerations for usage.
Tips for Enhancing Face ID Security
Enhancing the security of Face ID on the iPhone 12 involves implementing proactive measures to optimize its performance and fortify its resilience against potential security risks. By leveraging the following tips, users can maximize the effectiveness of Face ID while reinforcing the protection of their personal information.
-
Enroll Alternate Appearances: To enhance the adaptability of Face ID, consider enrolling alternate appearances, such as different hairstyles, facial hair configurations, or accessories. This ensures that Face ID can reliably authenticate the user across a diverse range of appearances, further bolstering its adaptive capability.
-
Regularly Update Facial Data: Periodically updating the facial data captured by Face ID can contribute to its accuracy and responsiveness. This practice is particularly beneficial when significant changes occur in the user's appearance, as it allows Face ID to adapt to these modifications and maintain reliable authentication.
-
Enable Attention Awareness: Activating the Attention Awareness feature within Face ID settings enhances security by requiring the user's attention to be directed towards the device for authentication. This additional layer of verification mitigates the risk of unauthorized access attempts using replicas or unauthorized access while the user is not actively engaging with the device.
-
Use Strong Passcode as Backup: While Face ID offers seamless authentication, it is prudent to utilize a strong alphanumeric passcode as a backup authentication method. In the event of Face ID encountering challenges, the passcode serves as a reliable fallback, ensuring uninterrupted access to the device and sensitive data.
-
Exercise Caution with Face ID Usage: When using Face ID for sensitive transactions or authentication, exercise caution in ensuring that the device's environment is secure. Avoid authenticating in the presence of unfamiliar individuals or in untrusted settings to minimize the risk of unauthorized access.
-
Regularly Review Security Settings: Periodically reviewing and adjusting Face ID security settings allows users to optimize its performance based on their evolving security needs. This includes evaluating attention awareness, alternate appearance enrollment, and passcode usage to align with individual security preferences.
By implementing these proactive measures, users can elevate the security of Face ID on the iPhone 12, fostering a robust and resilient authentication environment that aligns with Apple's commitment to user privacy and data security. These tips empower users to harness the full potential of Face ID while proactively safeguarding their digital identity and personal information.
Comparing Face ID with Other Biometric Authentication Methods
When comparing Face ID with other biometric authentication methods, it becomes evident that each approach offers unique advantages and considerations. Understanding the distinctions between Face ID and alternative biometric authentication methods provides valuable insights into their respective capabilities and suitability for diverse user scenarios.
Face ID vs. Touch ID
Face ID and Touch ID represent two distinct biometric authentication methods, each with its own set of strengths. While Touch ID relies on fingerprint recognition, Face ID leverages facial recognition technology. Touch ID offers a tactile and discreet authentication method, ideal for scenarios where visual confirmation may be impractical. In contrast, Face ID excels in delivering a seamless and hands-free authentication experience, eliminating the need for physical contact with the device. The choice between Face ID and Touch ID often hinges on user preferences for tactile interaction and environmental considerations.
Face ID vs. Iris Scanning
Iris scanning, another biometric authentication method, involves capturing and analyzing the unique patterns of the user's iris. When comparing Face ID with iris scanning, both methods prioritize accuracy and security. However, Face ID offers a more intuitive and user-friendly authentication process, as it does not require the user to position their eyes precisely within a designated area, as is the case with iris scanning. Face ID's adaptability to changes in the user's appearance further enhances its practicality in real-world usage scenarios.
Face ID vs. Voice Recognition
Voice recognition, while distinct from facial recognition, shares common ground in providing a hands-free authentication experience. Face ID and voice recognition differ in their reliance on visual and auditory cues, respectively. Face ID's ability to authenticate users in diverse lighting conditions and its resistance to unauthorized access attempts using replicas distinguish it from voice recognition. Voice recognition, on the other hand, offers a compelling alternative for users seeking a non-visual authentication method, particularly in scenarios where facial recognition may be impractical or undesirable.
Face ID vs. Fingerprint Scanning
Fingerprint scanning, akin to Touch ID, offers a tactile and precise authentication method. When comparing Face ID with fingerprint scanning, the choice often revolves around user preferences for hands-free interaction and environmental considerations. While fingerprint scanning excels in scenarios where tactile interaction is preferred, Face ID's adaptability to changes in the user's appearance and its seamless integration into the device's user interface position it as a compelling biometric authentication method for diverse user scenarios.
In essence, the comparison of Face ID with other biometric authentication methods underscores the diversity of options available to users, each catering to unique preferences and usage scenarios. While Face ID excels in delivering a seamless and secure authentication experience, the considerations outlined in the comparison provide valuable insights for users seeking to align their authentication method with their individual needs and preferences.