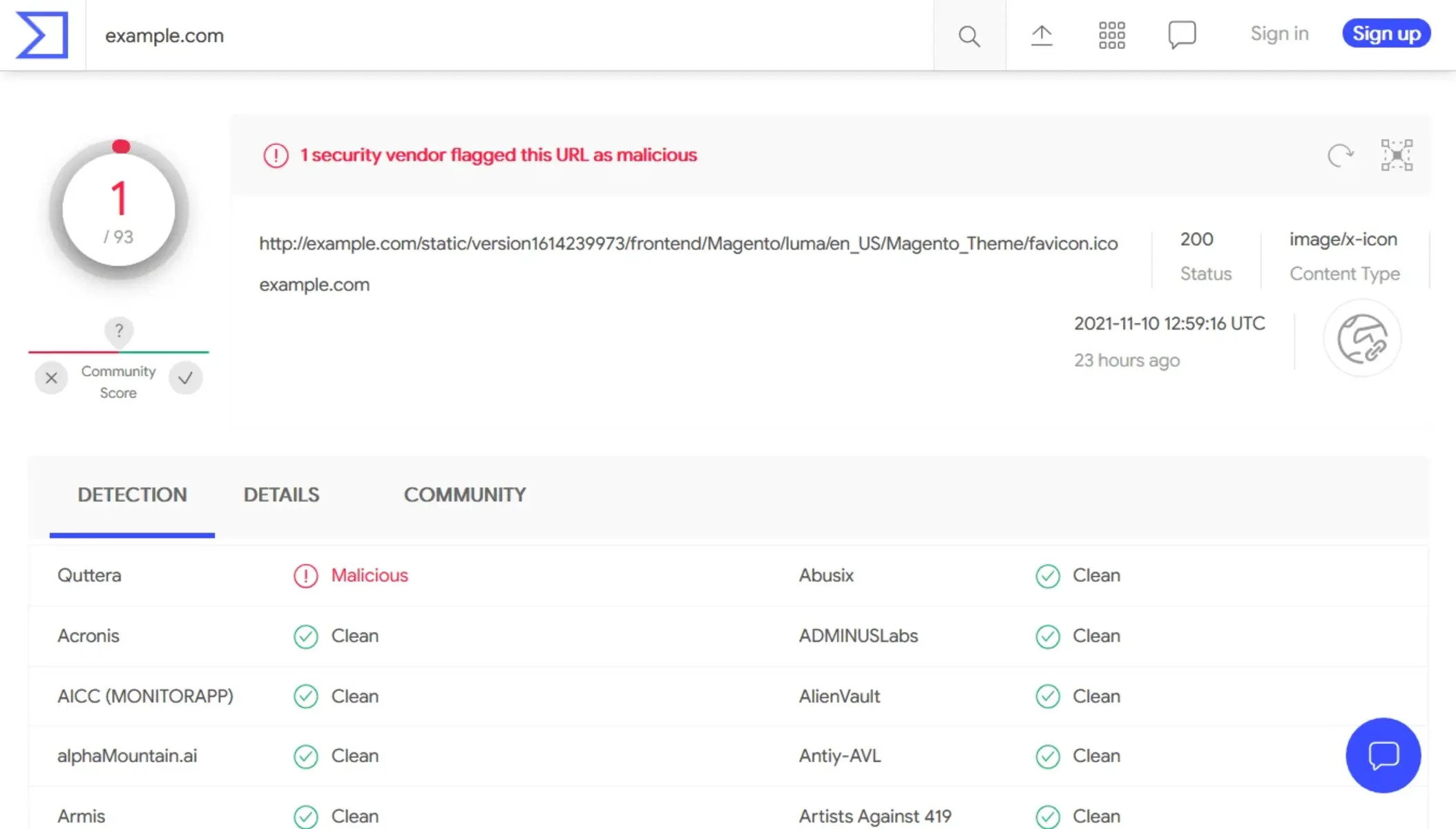
Why use a second opinion malware scanner?
When it comes to protecting your computer and sensitive information from malware attacks, relying on a single antivirus software may not always be enough. This is where a second opinion malware scanner can be a valuable tool in your cybersecurity arsenal.
First and foremost, using a second opinion malware scanner can help to provide an extra layer of protection. While your primary antivirus software may be effective in detecting and removing most types of malware, it’s not infallible. New and emerging threats can often slip past even the most advanced security systems. By utilizing a different malware scanner, you can identify any potential threats that may have been missed and take appropriate action.
Furthermore, a second opinion malware scanner can help to confirm the accuracy of your initial scan results. Sometimes, antivirus software can produce false positives or false negatives, flagging legitimate files as malware or failing to detect malicious code. By using a different scanning tool, you can verify the accuracy of the initial scan and ensure that your system is truly clean or identify any lingering threats that were missed.
Another benefit of using a second opinion malware scanner is the opportunity to access a wider range of detection techniques. Different scanning tools employ various methods to identify malware, such as signature-based detection, behavior analysis, heuristic analysis, and machine learning algorithms. By using multiple scanners, you can leverage the strengths of each technique and increase the chances of detecting any potential threats.
Moreover, a second opinion malware scanner can provide peace of mind, especially in cases where you suspect that your system has been compromised but your primary antivirus software did not detect anything malicious. It allows you to independently verify the security status of your computer and take appropriate action if necessary.
Last but not least, using a second opinion malware scanner can also help to mitigate the risk of zero-day attacks. Zero-day vulnerabilities are software vulnerabilities that are unknown to the software vendor and do not yet have a patch available. Traditional antivirus software may not have the ability to detect zero-day threats, as they rely on known signatures. By using a second opinion malware scanner, you can increase your chances of discovering and defending against unknown threats.
Benefits of using a second opinion malware scanner
Using a second opinion malware scanner can offer several significant benefits that enhance your computer’s security and protect your personal information from malicious threats. Here are some of the key advantages:
- Enhanced Detection: One of the main benefits of utilizing a second opinion malware scanner is the improved detection capability. Different scanners employ varying detection techniques, such as heuristics, behavioral analysis, and machine learning algorithms. This diversity increases the likelihood of catching any malware that may have been missed by your primary antivirus software.
- Validation of Results: False positives and false negatives can occur with any antivirus software. By cross-checking the results with a second opinion scanner, you can validate the accuracy of the initial scan. Confirming the presence or absence of malware ensures that you can take appropriate actions to protect your computer.
- Added Layer of Security: Using a second opinion malware scanner provides an additional layer of security to safeguard your system from evolving threats. It acts as a backup, ensuring that if one scanner misses a particular malware strain, another scanner might detect and remove it. This redundancy is especially beneficial against zero-day attacks, where unknown threats are exploited before software vendors can release patches.
- Peace of Mind: The reassurance provided by a second opinion malware scan is invaluable. It allows you to verify the integrity of your computer system independently and serves as an extra precautionary measure against potential threats that might have gone undetected.
- Complementary Detection Techniques: Each malware scanner employs different detection techniques, such as signature-based analysis and behavioral monitoring. By utilizing multiple scanners, you can take advantage of a broader range of detection mechanisms and increase your overall security posture.
- Protection against Advanced Malware: Advanced malware, such as rootkits and polymorphic viruses, can evade detection by traditional antivirus software. Using a second opinion scanner, which often utilizes advanced scanning algorithms, helps to identify and eliminate these complex threats.
- Free Alternatives: Many second opinion malware scanners offer free versions that can complement your existing antivirus software without any additional cost. These free options provide an affordable way to enhance your system’s security without compromising your budget.
How to choose a reliable second opinion malware scanner
With numerous second opinion malware scanners available in the market, it is essential to choose a reliable and trustworthy option. Here are some factors to consider when selecting a second opinion malware scanner:
- Reputation and Trustworthiness: Look for reputable software vendors with a proven track record in the cybersecurity industry. Read reviews and check online forums to gauge the trustworthiness and effectiveness of the scanner.
- Detection Capabilities: Opt for a scanner that utilizes advanced detection techniques, such as behavior analysis, heuristics, and machine learning algorithms. This ensures higher accuracy and detection rates for both known and unknown malware.
- Scan Speed: Consider the scanning speed of the software. A reliable second opinion malware scanner should be efficient in scanning your system without significantly slowing down its performance.
- Compatibility: Ensure that the scanner is compatible with your operating system and integrates well with your existing antivirus software. Compatibility issues can lead to system conflicts, reducing the effectiveness of both scanners.
- Automatic Updates: Regularly updated malware definitions are vital for effective malware detection. Choose a scanner that offers automatic updates to ensure it stays up-to-date with the latest threats.
- User-Friendly Interface: A user-friendly interface makes it easier to navigate the scanner’s features and settings. Look for a scanner that offers a well-designed interface and clear instructions for scanning and removing malware.
- Customer Support: Consider the availability and quality of customer support provided by the scanner’s vendor. Prompt assistance can be crucial if you encounter any issues or have questions regarding the scanner’s usage.
- Additional Features: Some second opinion malware scanners offer extra features, such as real-time monitoring, web protection, and email scanning. Assess your needs and choose a scanner that provides the features that complement your existing security measures.
- Cost: While cost should not be the sole deciding factor, consider the pricing options and value for money offered by the scanner. Many reliable second opinion scanners offer free versions with limited features, as well as paid versions with more advanced capabilities.
By taking these factors into account, you can select a reliable second opinion malware scanner that meets your specific requirements and provides enhanced protection for your computer system.
Top second opinion malware scanners on the market
When it comes to choosing a reliable second opinion malware scanner, there are several options available. Here are some of the top scanners that have gained popularity in the cybersecurity industry:
- Malwarebytes: Malwarebytes is a well-known name in the world of cybersecurity. Its second opinion scanner offers powerful malware detection capabilities, utilizing behavior-based analysis to identify and remove both known and unknown threats.
- HitmanPro: HitmanPro is another popular choice for a second opinion malware scanner. It uses cloud-based scanning technology to detect and eliminate malware in real-time. HitmanPro is known for its fast scanning speed and thorough detection rates.
- Zemana AntiMalware: Zemana AntiMalware is a lightweight and user-friendly scanner that provides reliable second opinion scanning. It utilizes its unique Scan Cloud technology to identify and remove malware effectively, including hard-to-detect rootkits and zero-day threats.
- Emsisoft Emergency Kit: Emsisoft Emergency Kit is a portable scanner that does not require installation, making it convenient for on-the-go use. It offers comprehensive malware detection and removal capabilities, including advanced behavioral analysis, making it highly effective in combating threats.
- SUPERAntiSpyware: SUPERAntiSpyware is a versatile scanner that focuses on detecting and removing spyware, adware, and other potentially unwanted programs (PUPs). It provides a reliable second opinion for malware scanning and has a reputation for high detection rates.
- Norton Power Eraser: Norton Power Eraser is a specialized scanner from Norton, a leading cybersecurity company. It is designed to detect and remove aggressive threats that may be difficult to eliminate with traditional antivirus software. Norton Power Eraser is known for its thorough scans and effective removal of persistent malware.
It’s important to note that these are just a few examples of the top second opinion malware scanners available. Each scanner has its strengths and features, so it’s essential to evaluate your specific needs and choose the scanner that best aligns with your requirements.
Remember to regularly update the scanner and use it in conjunction with your primary antivirus software for comprehensive protection against malware and other security threats.
How often should you use a second opinion malware scanner?
The frequency of using a second opinion malware scanner depends on various factors, including your computer usage habits, the sensitivity of the information stored on your system, and the level of risk you are willing to tolerate. While there is no one-size-fits-all answer, here are some considerations to help you determine how often to use a second opinion malware scanner:
- Regular Scans: It is generally recommended to run a full scan with your primary antivirus software at least once a week. Supplementing this with a second opinion malware scan, preferably with a different scanner, can provide an extra layer of security. Conducting a full system scan with a second opinion scanner every one to two weeks can help catch any threats that might have been missed by your primary scanner.
- After Suspicious Activities: If you notice any unusual behavior on your computer, such as frequent crashes, slow performance, or unexplained system changes, it is advisable to conduct a thorough scan with a second opinion malware scanner. This can help identify and remove any hidden malware that might be causing these issues.
- Upon Software or System Installation: Installing new software or making significant system changes can potentially introduce vulnerabilities or malicious code. It is a good practice to run a second opinion scan after such installations or updates to ensure that your system remains secure.
- When Visiting Potentially Risky Websites: If you regularly visit websites that are known for carrying a higher risk of malware, such as torrent or adult content sites, it is recommended to run a second opinion malware scan after each visit. This helps to mitigate the chances of inadvertently downloading and installing malware on your system.
- When Removable Media is Connected: Viruses and malware can be transmitted through infected USB drives or external storage devices. It is important to scan such media with a second opinion malware scanner before accessing or transferring files to your computer to prevent any potential infection.
- After Network Attacks or Security Breaches: If you suspect that your computer has been compromised, such as in the case of a network attack or security breach, it is crucial to conduct a comprehensive scan with a reliable second opinion malware scanner. This is to ensure that all traces of malware or potentially unwanted programs are detected and removed.
Ultimately, the frequency of using a second opinion malware scanner should be tailored to your specific circumstances. Consider your level of exposure to potential threats and adjust the scanning frequency accordingly. Remember that prevention is key in maintaining a secure system, so it’s better to err on the side of caution and conduct regular scans to maintain optimal security.
Common misconceptions about second opinion malware scanners
Despite the numerous benefits of using a second opinion malware scanner, there are some common misconceptions that can lead to confusion or hesitation in utilizing this valuable tool. Let’s debunk a few of these misconceptions:
- Misconception 1: Multiple scanners cause conflicts: One common misconception is that running multiple malware scanners simultaneously can lead to conflicts and system instability. While it’s true that running two real-time antivirus programs simultaneously can cause conflicts, using a second opinion scanner for periodic scans does not pose the same risk. Simply ensure that the second opinion scanner is not running in real-time mode to avoid conflicts.
- Misconception 2: Second opinion scanners always produce different results: Another misconception is that every second opinion scanner will always provide different results from the primary antivirus software. While it is true that different scanners may have varying detection rates and techniques, it does not necessarily mean that they will always produce conflicting results. In fact, it’s common for second opinion scanners to validate the accuracy of the primary scan results rather than contradicting them.
- Misconception 3: Second opinion scanners are unnecessary if you have a reliable antivirus: While having a reliable antivirus is crucial, no single security software can provide 100% protection against all types of malware. Second opinion scanners serve as an additional layer of defense, using different detection techniques to catch any threats that might have been missed by the primary antivirus software. It’s always better to have a multi-layered approach to enhance your system’s security.
- Misconception 4: Second opinion scanners impact system performance: Some people believe that running a second opinion malware scan will significantly slow down their computer’s performance. However, most modern malware scanners are designed to be lightweight and utilize system resources efficiently. When used for periodic scans, second opinion scanners should have minimal impact on your system’s performance.
- Misconception 5: Second opinion scanners are only for advanced users: It’s a common misconception that utilizing a second opinion malware scanner requires advanced technical knowledge. However, most second opinion scanners come with user-friendly interfaces and straightforward scanning options. They are designed to be accessible to users of all levels of expertise, making it easy for anyone to perform a scan and interpret the results.
Understanding these misconceptions can help you make informed decisions about incorporating a second opinion malware scanner into your cybersecurity routine. By dispelling these myths, you can take full advantage of the added protection and peace of mind that a second opinion scanner can offer.
Tips for interpreting second opinion malware scan results
Interpreting the results of a second opinion malware scan is crucial for accurately assessing the security status of your computer. Here are some tips to help you understand and interpret the scan results effectively:
- Scan Summary: Pay attention to the scan summary, which provides an overview of the scan results. It typically includes information on the number of files scanned, threats detected, and actions taken. This summary gives you an initial understanding of the scan’s outcome.
- Threat Categories: Second opinion scanners often categorize detected threats based on their severity, such as low, medium, or high risk. Understand the significance of each category to prioritize the threats that require immediate action.
- Malware Names: Take note of the names of detected malware or potentially unwanted programs (PUPs). Research these names to gain insights into their behavior, impact, and recommended removal methods. Trusted cybersecurity resources and forums can provide valuable information about specific threats.
- Quarantine or Removal: Review the actions taken by the scanner for each detected threat. Some scanners may automatically quarantine or remove threats, while others may require manual intervention. Understand the steps required to address each threat effectively.
- False Positives: False positives can occur, where legitimate files or programs are mistakenly identified as malware. Before taking any action, consider whether the detected threat could be a false positive. Cross-referencing with your primary antivirus software’s scan results or conducting additional research can help confirm the legitimacy of the detection.
- Scan Details: Dive into the scan details to get more specific information about each detected threat. Look for details such as file paths, file sizes, infection types, and the potential impact on your system. This information can help you assess the severity of each threat and determine the appropriate course of action.
- Follow-up Actions: After understanding the scan results, initiate appropriate follow-up actions. This may involve quarantining or deleting detected malware, updating your primary antivirus software, or seeking professional assistance if the threats are complex or persistent.
Remember, interpreting the results of a second opinion malware scan requires a balance of caution and knowledge. If you are uncertain about a particular threat or need further clarification, seek guidance from cybersecurity professionals or the support resources provided by the scanner’s vendor.
By following these tips and staying informed, you can effectively interpret the results of a second opinion malware scan and take appropriate measures to maintain a secure and protected computer system.
Integrating a second opinion malware scanner into your cybersecurity routine
Incorporating a second opinion malware scanner into your cybersecurity routine can significantly enhance your overall protection against malicious threats. Here are some steps to help you effectively integrate a second opinion malware scanner into your routine:
- Choose a Reliable Scanner: Select a reputable and trustworthy second opinion malware scanner that aligns with your needs and requirements. Consider factors such as detection capabilities, compatibility with your primary antivirus software, and user-friendliness.
- Install and Update Regularly: Install the second opinion scanner on your system and ensure that it is up to date with the latest malware definitions. Regular updates guarantee that the scanner can detect and remove newer threats effectively.
- Schedule Regular Scans: Set a schedule for running periodic scans with the second opinion malware scanner. The frequency of these scans can vary based on your computer usage and risk profile, as discussed earlier. Establish a routine that allows for regular scans without disrupting your workflow.
- Scan Removable Media: Whenever you connect a USB drive or external storage device to your computer, perform a scan with the second opinion scanner before accessing any files. This helps prevent malware from spreading through removable media.
- Supplement Traditional Antivirus: Understand that a second opinion scanner is not a replacement for traditional antivirus software. Instead, use it as a supplementary tool to provide an additional layer of protection. Run scans with both your primary antivirus software and the second opinion scanner for comprehensive coverage.
- Stay Informed: Stay updated with the latest cybersecurity news, emerging threats, and best practices. Regularly educate yourself on new malware trends and vulnerabilities. This knowledge enables you to make informed decisions regarding your cybersecurity and take appropriate actions based on evolving threats.
- Practice Safe Computing Habits: Alongside using a second opinion malware scanner, adhere to safe computing habits. Avoid clicking on suspicious links, refrain from downloading files from untrusted sources, keep your operating system and software up to date, and utilize strong and unique passwords. These practices contribute to a holistic and robust cybersecurity posture.
- Seek Professional Assistance when Needed: If you encounter complex or persistent malware threats that are challenging to remove, consider seeking assistance from cybersecurity professionals or forums. They can provide expert guidance and help you navigate through more advanced security challenges.
By incorporating these steps into your cybersecurity routine, you can effectively integrate a second opinion malware scanner and enhance your computer’s protection against malware and other malicious threats.
Potential downsides of using a second opinion malware scanner
While there are numerous benefits to using a second opinion malware scanner, it’s important to be aware of potential downsides that may come with its usage. Here are a few considerations:
- System Resource Usage: Utilizing a second opinion malware scanner can consume additional system resources, which may lead to a slight impact on your computer’s performance. This is especially true during full system scans when the scanner is actively checking numerous files. However, many modern scanners are designed to be lightweight and optimized for minimal impact.
- Compatibility Issues: In some cases, running a second opinion malware scanner alongside your primary antivirus software may result in compatibility issues. These conflicts can occur if both scanners attempt to perform real-time scanning simultaneously. It’s crucial to ensure that the two scanners are compatible and configured in a way that prevents conflicts.
- Increased False Positive Rate: Using multiple malware scanners may lead to a higher chance of false positives. False positives occur when legitimate files or programs are mistakenly identified as malware. While false positives are generally rare, the likelihood of encountering them may increase with the use of multiple scanners. It’s important to carefully review and verify suspicious detections to avoid erroneous removal of harmless files.
- Additional Time Investment: Incorporating a second opinion malware scanner into your cybersecurity routine requires additional time for regular scans. Depending on the size of your system and the frequency of scans, this can impact your overall productivity. However, the added protection and peace of mind that come with using a second opinion scanner often outweigh the time investment.
- Overlapping Detection: There is a possibility that both your primary antivirus software and the second opinion malware scanner may detect the same threat. This overlapping detection can sometimes create confusion or duplication of efforts. However, using multiple scanners increases the likelihood of catching any missed threats and provides a more comprehensive security approach.
- Complexity of Interpretation: Interpreting scan results from multiple scanners can sometimes be challenging, especially if the scanners provide conflicting reports or use different categorization methods. It requires a thorough understanding of each scanner’s scanning techniques, threat categorization, and false positive rates to effectively assess the security status of your computer.
While these potential downsides should be taken into consideration, they are often outweighed by the benefits that a second opinion malware scanner provides. By understanding these factors and mitigating any associated risks, you can make informed decisions about incorporating a second opinion scanner into your cybersecurity strategy.
Final thoughts on the importance of second opinion malware scanners
Second opinion malware scanners play a crucial role in fortifying your computer’s security and protecting your sensitive information from malicious threats. While they may have some potential downsides, the benefits of incorporating a second opinion scanner into your cybersecurity routine far outweigh any drawbacks. Here are some final thoughts on the importance of using second opinion malware scanners:
- Enhanced Protection: By utilizing a second opinion scanner, you add an extra layer of defense against malware that may have evaded detection by your primary antivirus software. This comprehensive approach improves your chances of catching and mitigating potential threats.
- Validation and Accuracy: Second opinion scanners enable you to validate the accuracy of scan results produced by your primary antivirus software. They provide an independent assessment, helping to identify false positives or confirm the presence of missed threats. This validation increases your confidence in the security status of your system.
- Broadened Detection Techniques: Each scanner employs different detection methods, such as behavior analysis, heuristics, or machine learning algorithms. Integrating a second opinion scanner exposes your system to a wider range of detection techniques, ensuring that a broader spectrum of threats is identified and removed.
- Peace of Mind: Incorporating a second opinion scanner offers peace of mind. It allows you to independently verify the security status of your computer and take proactive steps to address any potential threats. This reassurance is especially valuable in today’s interconnected digital landscape.
- Adaptability to Evolving Threats: Cyber threats are constantly evolving, with new and sophisticated malware emerging regularly. Second opinion scanners provide an additional means to stay ahead of these threats. Their ability to detect zero-day and emerging malware helps protect your system against unknown and previously unseen threats.
- Complementary to Existing Measures: Second opinion scanners are not meant to replace your primary antivirus software but rather complement it. By integrating a second opinion scanner into your cybersecurity routine, you build a multi-layered defense strategy that reduces the chances of malware evading detection and compromise.
Ultimately, using a second opinion malware scanner is an essential practice in safeguarding your computer and personal data from the ever-increasing threat landscape. It goes hand in hand with other best practices, such as practicing safe computing habits, keeping software up to date, and regularly backing up your important files. By adopting a proactive approach to cybersecurity, you can minimize the risks and enjoy a safer and more secure digital experience.