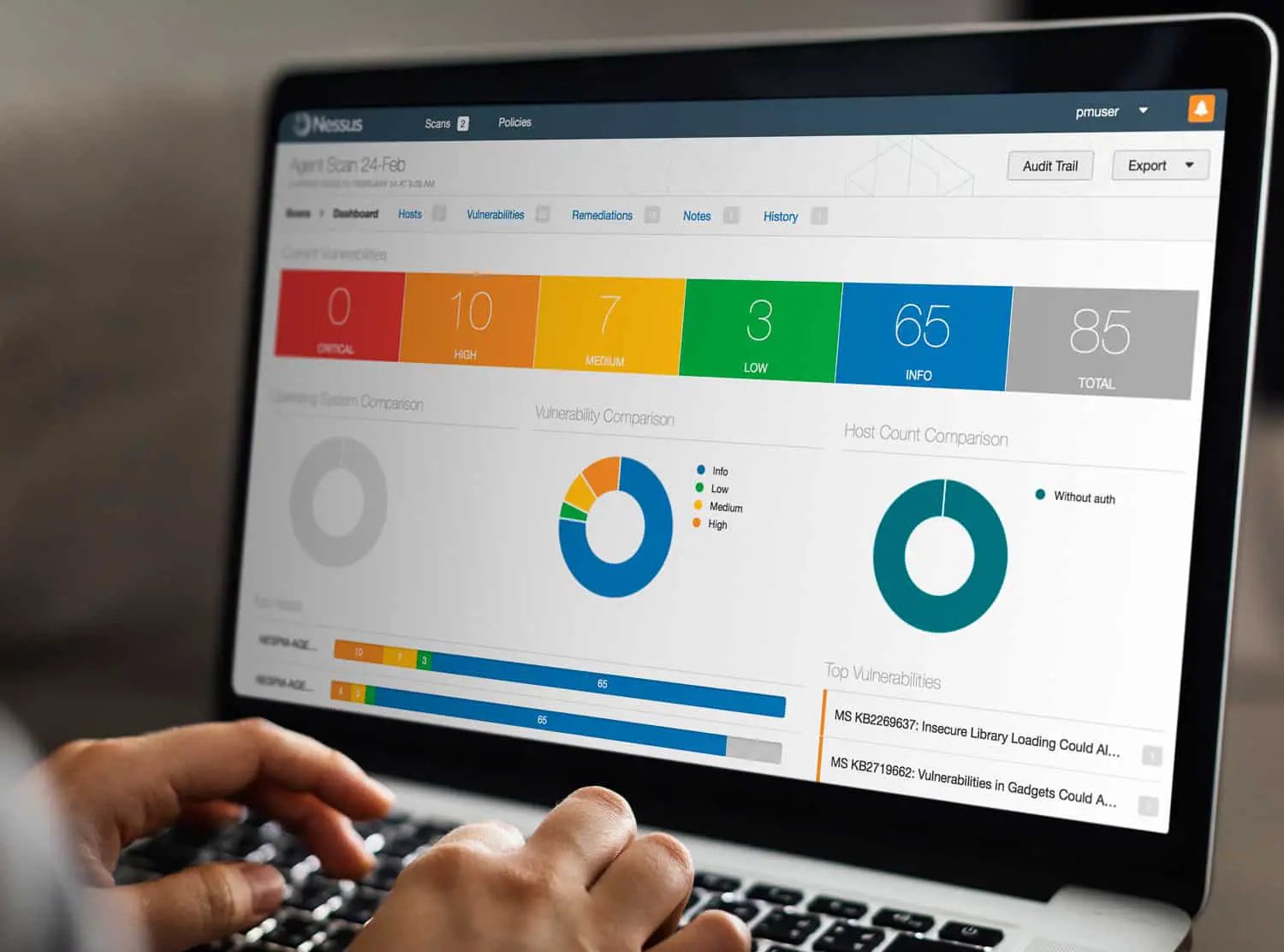
Overview of Nessus Scanner
Nessus Scanner is a powerful tool used for vulnerability assessment and network scanning. It is widely recognized as one of the most comprehensive and widely used vulnerability scanners available in the market today. Developed by Tenable Network Security, Nessus helps organizations identify and mitigate potential security risks in their IT infrastructure.
The primary function of Nessus Scanner is to perform vulnerability assessments by scanning networks, systems, and applications for known vulnerabilities. It uses a vast database of vulnerability checks to identify potential weaknesses that hackers could exploit. By detecting vulnerabilities and providing detailed reports, Nessus enables organizations to take proactive measures to secure their networks and protect against potential cyber threats.
With its user-friendly interface and extensive feature set, Nessus Scanner offers a wide range of capabilities to fulfill the needs of both small businesses and large enterprises. It supports multiple platforms, including Windows, Linux, and macOS, making it a versatile tool for various operating environments.
One of the key benefits of Nessus Scanner is its ability to identify vulnerabilities across different types of devices, including servers, network devices, databases, and web applications. It can also detect misconfigurations and compliance issues, ensuring that organizations are adhering to industry best practices and regulatory requirements.
Moreover, Nessus Scanner provides real-time vulnerability scanning, enabling organizations to continuously monitor their IT infrastructure and promptly address any newly discovered vulnerabilities. It offers automatic updates that keep the vulnerability database up-to-date, ensuring that organizations can stay on top of emerging threats.
Another notable feature of Nessus Scanner is its ability to generate comprehensive reports that provide detailed information on identified vulnerabilities, their severity levels, and recommended remediation actions. These reports can be customized according to the organization’s specific requirements and shared with relevant stakeholders, such as IT administrators and security teams.
Overall, Nessus Scanner is a powerful and versatile tool that plays a crucial role in ensuring the security and integrity of an organization’s IT infrastructure. By efficiently identifying vulnerabilities and providing actionable insights, it empowers organizations to proactively mitigate risks and safeguard their critical assets from potential cyber threats.
History of Nessus Scanner
The history of Nessus Scanner dates back to the late 1990s when Renaud Deraison, the founder of Tenable Network Security, developed the initial version of the tool. Inspired by his desire to create a powerful vulnerability scanning tool, Deraison released Nessus in 1998 as an open-source project.
Initially, Nessus was designed to be a free and community-driven security tool, widely embraced by the security community for its effectiveness in identifying vulnerabilities. Its popularity grew rapidly, attracting a dedicated user base. However, in 2005, Tenable adopted a new business model and introduced a commercial version of Nessus, known as Nessus Professional.
Over the years, Nessus Scanner has undergone significant advancements and improvements, reflecting the ever-evolving landscape of cybersecurity. Tenable continues to enhance the tool to address emerging threats and meet the changing needs of organizations.
In 2019, Tenable introduced Nessus Essentials, a free version of Nessus Scanner aimed at providing basic security scanning capabilities for small businesses and home users. This move expanded the accessibility of Nessus, allowing a broader audience to benefit from its powerful features.
Recently, Tenable launched Nessus Cloud, a cloud-based offering that provides organizations with a scalable and flexible vulnerability assessment solution. Leveraging the cloud infrastructure, Nessus Cloud enables businesses to automate scanning, efficiently manage their security risks, and gain real-time visibility into their vulnerabilities.
Today, Nessus Scanner is recognized as a leading vulnerability assessment tool, widely used by organizations of all sizes across various industries. Its continuous innovation and commitment to ensuring the security and integrity of IT infrastructures have contributed to its reputation as a trusted and reliable solution.
Looking ahead, as the cybersecurity landscape continues to evolve, Nessus Scanner is expected to remain an essential tool for organizations in their efforts to detect, mitigate, and manage vulnerabilities, protecting critical assets from potential cyber threats.
How Does Nessus Scanner Work?
Nessus Scanner operates by conducting comprehensive vulnerability assessments on networks, systems, and applications. It follows a systematic approach to identify potential vulnerabilities and assess the overall security posture of an organization’s IT infrastructure.
The scanning process begins with Nessus Scanner conducting an inventory of the network, identifying all active hosts and devices within the specified IP range. It then performs service detection to determine the services running on each host, such as web servers, email servers, and database servers.
Once the initial inventory and service detection are complete, Nessus Scanner proceeds to conduct a vulnerability scan. It leverages a vast database of known vulnerabilities to compare the identified services and devices against its vulnerability checks. These checks are constantly updated to incorporate the latest security threats and vulnerabilities.
Nessus Scanner employs a variety of techniques during the vulnerability scan, including port scanning, banner grabbing, and in-depth analysis of network protocols. By interacting with the target system, it attempts to identify security weaknesses that could be exploited by attackers.
The results of the vulnerability scan are then analyzed to prioritize potential risks based on the severity and impact of each vulnerability. Nessus Scanner assigns a severity rating, such as critical, high, medium, or low, to each vulnerability detected, allowing organizations to focus their remediation efforts accordingly.
In addition to scanning for vulnerabilities, Nessus Scanner also checks for common misconfigurations and compliance issues. It assesses the IT infrastructure against industry best practices and regulatory standards, providing organizations with insights into their overall security posture and ensuring adherence to required security controls.
Once the scan is complete, Nessus Scanner generates detailed reports that highlight the vulnerabilities detected, their severity levels, and suggested remediation actions. These reports can be customized to suit the organization’s specific requirements and shared with relevant stakeholders, such as IT administrators and security teams.
Organizations can also schedule regular scans using Nessus Scanner to ensure continuous monitoring of their IT infrastructure. This proactive approach allows them to stay ahead of emerging threats and address vulnerabilities in a timely manner.
Overall, Nessus Scanner works by systematically scanning networks, systems, and applications for vulnerabilities, identifying risks, and providing actionable insights to help organizations strengthen their security defenses and protect their critical assets.
Features of Nessus Scanner
Nessus Scanner offers a wide range of features and capabilities that make it a powerful and comprehensive vulnerability assessment tool. These features enable organizations to efficiently identify, assess, and manage potential security risks within their IT infrastructure.
1. Vulnerability Scanning: Nessus Scanner conducts thorough vulnerability scans on networks, systems, and applications, identifying potential weaknesses that could be exploited by attackers.
2. Extensive Vulnerability Database: It maintains an extensive database of vulnerability checks, constantly updated to include the latest security threats and vulnerabilities, ensuring accurate and comprehensive scanning results.
3. Real-Time Monitoring: Nessus Scanner provides real-time monitoring of vulnerabilities, allowing organizations to stay continuously aware of potential risks and promptly remediate any newly discovered vulnerabilities.
4. Multi-Platform Support: It supports various operating systems, including Windows, Linux, and macOS, making it compatible with diverse IT environments.
5. Compliance Checking: Nessus Scanner checks for compliance with industry best practices and regulatory standards, helping organizations ensure that their IT infrastructure meets required security controls.
6. Misconfiguration Detection: It identifies common misconfigurations in systems and network devices that could expose organizations to security risks.
7. Web Application Scanning: Nessus Scanner scans web applications for vulnerabilities, including issues related to code injection, cross-site scripting (XSS), and insecure configurations.
8. Reports and Remediation Guidance: It generates detailed reports that provide comprehensive information on identified vulnerabilities, their severity levels, and recommended remediation actions. These reports can be customized and shared with relevant stakeholders.
9. Integration with Other Security Tools: Nessus Scanner integrates with other security tools and platforms, enabling seamless collaboration and streamlining vulnerability management processes.
10. Automation and Scheduling: It allows organizations to automate vulnerability scans, schedule regular scans, and receive notifications of newly discovered vulnerabilities.
These features make Nessus Scanner an essential tool for organizations seeking to enhance their security posture, effectively manage vulnerabilities, and protect their critical assets from potential cyber threats. With its robust capabilities and user-friendly interface, Nessus Scanner continues to be a trusted solution for vulnerability assessment across various industries.
Different Versions of Nessus Scanner
Nessus Scanner offers various versions that cater to the diverse needs and requirements of organizations, ranging from small businesses to large enterprises. Each version provides unique features and capabilities, allowing organizations to choose the one that best suits their specific vulnerability assessment needs.
1. Nessus Essentials: This is the free version of Nessus Scanner, designed for small businesses and home users. While offering basic vulnerability scanning capabilities, it provides a cost-effective solution for organizations with limited resources.
2. Nessus Professional: This is the commercial version of Nessus Scanner, providing advanced features and enhanced scanning capabilities. It offers comprehensive vulnerability scanning, compliance checking, and detailed reporting, making it suitable for medium to large enterprises with more complex IT infrastructures.
3. Nessus Manager: Nessus Manager is a centralized vulnerability management platform that allows organizations to efficiently manage multiple Nessus Scanners. It provides centralized reporting, policy creation and enforcement, and a collaborative workbench for teams, making it ideal for organizations with a larger scale of vulnerability assessment needs.
4. Nessus Cloud: Nessus Cloud is a cloud-based vulnerability assessment solution that offers scalability and flexibility. It leverages the power of the cloud to automate scanning processes and provides real-time visibility into vulnerabilities. Nessus Cloud is suitable for organizations with dynamic and distributed IT infrastructures.
5. Tenable.io: Tenable.io is an advanced vulnerability management platform that offers a comprehensive suite of security solutions, including vulnerability scanning, compliance management, and asset discovery. It provides a centralized view of vulnerabilities across the IT infrastructure and offers integration with other security tools, allowing organizations to streamline their vulnerability management processes.
These different versions of Nessus Scanner cater to organizations of various sizes and complexities. This allows organizations to choose the version that aligns with their specific requirements, helping them effectively identify and manage vulnerabilities within their IT infrastructure.
It’s important for organizations to assess their needs and evaluate the features and capabilities offered by each version before selecting the appropriate version of Nessus Scanner. By choosing the right version, organizations can ensure they have the necessary tools and functionalities to secure their IT systems and protect against potential cyber threats.
Benefits of Using Nessus Scanner
Nessus Scanner offers numerous benefits to organizations that utilize it for vulnerability assessment and network scanning. These benefits enhance an organization’s ability to identify and mitigate potential security risks, ultimately strengthening their overall security posture.
1. Improved Risk Management: By conducting comprehensive vulnerability scans, Nessus Scanner helps organizations identify and prioritize potential risks. This enables them to proactively mitigate vulnerabilities and reduce the likelihood of successful cyberattacks.
2. Time and Cost Savings: Nessus Scanner automates the vulnerability scanning process, saving organizations time and effort compared to manual approaches. Moreover, it helps organizations identify vulnerabilities before they can be exploited, reducing the potential financial and reputational costs associated with security breaches.
3. Enhanced Compliance: Nessus Scanner helps organizations ensure compliance with industry standards and regulatory requirements. It performs checks against best practices and various compliance frameworks, assisting organizations in maintaining a secure and compliant IT infrastructure.
4. Real-Time Monitoring: Nessus Scanner supports real-time vulnerability scanning, continuously monitoring the IT infrastructure for new vulnerabilities. This allows organizations to quickly identify and address emerging threats, reducing their exposure to potential risks.
5. Comprehensive Reporting: Nessus Scanner generates detailed reports that provide organizations with a clear view of their vulnerabilities, their severity levels, and suggested remediation actions. These reports facilitate informed decision-making and help organizations prioritize their vulnerability management efforts.
6. Scalability: Nessus Scanner offers scalability, allowing organizations to adapt the tool to their changing needs as their IT infrastructure expands or undergoes modifications. This ensures that the vulnerability assessment process remains effective and efficient, even as the organization grows.
7. Cross-Platform Support: Nessus Scanner is compatible with various operating systems, including Windows, Linux, and macOS. This flexibility enables organizations to assess vulnerabilities across their entire IT ecosystem, regardless of the platforms and devices they use.
8. Continuous Updates: Nessus Scanner benefits from regular updates to its vulnerability database, ensuring that organizations have the latest security checks and can stay ahead of emerging threats. These updates help organizations maintain an up-to-date understanding of their vulnerabilities.
9. Integration Capabilities: Nessus Scanner can be easily integrated with other security tools and platforms, allowing organizations to streamline their vulnerability management processes. Integration enables cohesive security workflows and enhances overall security operations.
10. Proactive Security Posture: By identifying vulnerabilities and providing actionable insights, Nessus Scanner empowers organizations to take a proactive approach to their security posture. It enables them to implement appropriate security controls, reduce the attack surface, and protect critical assets from potential cyber threats.
Overall, the benefits of using Nessus Scanner extend beyond risk reduction. It allows organizations to optimize their vulnerability management processes, maintain compliance, and enhance their overall security posture in an ever-evolving threat landscape.
Challenges and Limitations of Nessus Scanner
While Nessus Scanner offers many benefits, it’s important to understand and address the challenges and limitations that organizations may encounter when using this vulnerability assessment tool.
1. False Positives and False Negatives: Nessus Scanner, like any scanning tool, can produce false positives and false negatives. False positives occur when the tool flags an issue as a vulnerability when it is not, while false negatives occur when the tool fails to detect an actual vulnerability. These inaccuracies can lead to wasted time and resources if not carefully validated.
2. Complexity of Configuration: Configuring and fine-tuning Nessus Scanner to meet specific organizational needs can be complex, especially for organizations with complex IT infrastructures. The tool offers a wide range of options and settings, requiring expertise and time to properly configure for optimal vulnerability scanning results.
3. Performance Impact: Depending on the size and complexity of the network, running Nessus Scanner can cause performance issues or network congestion. Scanning a large number of hosts simultaneously or using aggressive scanning techniques might overload the network and impact other business-critical operations.
4. Limited Coverage of Zero-Day Vulnerabilities: Nessus Scanner relies on a vulnerability database that contains known vulnerabilities. However, it may not detect zero-day vulnerabilities, as they are newly discovered and not yet included in the database. Organizations should complement Nessus Scanner with other security measures to address this limitation.
5. Lack of Contextual Understanding: Nessus Scanner relies solely on technical scanners and may lack contextual understanding of an organization’s specific business operations and security needs. This can result in misclassification of vulnerabilities or overlooking potential security risks that require a deeper understanding of the organization’s environment.
6. Limited Application Security Testing: Although Nessus Scanner includes some functionality to scan web applications, it may not be as robust as dedicated application security testing tools. Organizations with a strong focus on application security should consider using specialized tools in addition to Nessus Scanner.
7. Resources and Training: Utilizing Nessus Scanner effectively requires dedicated resources, including trained personnel who can configure, manage, and interpret the scan results. Organizations must invest in proper training and ongoing support to maximize the benefits of using the tool.
8. Complex Licensing Structure: The licensing structure of Nessus Scanner can be complex, especially for larger organizations or those with multiple locations. Understanding the licensing requirements and optimizing the licensing model for the organization’s needs can present a challenge.
Despite these challenges and limitations, Nessus Scanner remains a valuable tool for vulnerability assessment. It is crucial for organizations to consider these factors and make informed decisions to mitigate potential risks and maximize the benefits of using Nessus Scanner within their specific context.
How to Use Nessus Scanner
Using Nessus Scanner effectively requires careful planning, proper configuration, and consistent implementation. Here are the key steps to successfully utilize Nessus Scanner for vulnerability assessment:
1. Planning: Before using Nessus Scanner, define your scanning objectives and scope. Determine the assets, networks, and applications you want to assess for vulnerabilities. This step helps ensure that the scanning process aligns with your organization’s specific needs and priorities.
2. Installation and Setup: Install Nessus Scanner on a dedicated host or virtual machine. Ensure that the system meets the hardware and software requirements specified by Tenable. Once installed, create user accounts, configure network settings, and update the vulnerability database to the latest version.
3. Scanning Configuration: Customize the scanning configuration to suit your requirements. Specify the IP range or target hosts to be scanned, determine the scanning intensity, select vulnerability and compliance checks, and configure scan timing and frequency. Fine-tuning these settings helps optimize the scanning process.
4. Launching Scans: Initiate vulnerability scans based on your defined configurations. Schedule regular scans to ensure continuous monitoring of your IT infrastructure. Validate that the scans are running smoothly and that the progress and results are tracked effectively.
5. Analyzing Results: Once a scan is completed, analyze the scan results. Review the identified vulnerabilities, their severity levels, and any compliance issues found. Prioritize the vulnerabilities based on the risk they pose to your organization.
6. Remediation Planning: Develop a remediation plan based on the prioritized vulnerabilities. Assign responsibilities and establish a timeline for fixing the identified issues. Consider the available resources, potential impacts, and any required coordination with other teams or stakeholders.
7. Implementing Fixes: Implement the necessary fixes and security patches to address the vulnerabilities. Ensure that the remediation activities are properly documented and tracked. Conduct follow-up scans to verify that the vulnerabilities have been successfully remediated.
8. Reporting: Generate comprehensive reports to communicate the vulnerabilities, their severity levels, and the remediation actions taken. Customize the reports to suit the needs of different stakeholders, whether it be senior management, security teams, or compliance auditors.
9. Continuous Monitoring and Updating: Regularly update Nessus Scanner’s vulnerability database to ensure it includes the latest security checks. Schedule periodic scans to maintain visibility of your organization’s vulnerabilities and respond promptly to any new risks.
10. Ongoing Training: Provide training to the security team and relevant stakeholders on how to effectively use Nessus Scanner. Stay updated on the latest threats, vulnerabilities, and scanning techniques to maximize the tool’s effectiveness.
By following these steps, organizations can leverage the power of Nessus Scanner to identify vulnerabilities, prioritize remediation efforts, and enhance the security of their IT infrastructure.
Best Practices for Using Nessus Scanner
To make the most out of Nessus Scanner and ensure effective vulnerability assessment, it is important to follow best practices throughout the scanning process. Here are some key guidelines to consider:
1. Regularly Update Nessus Scanner: Keep Nessus Scanner and its vulnerability database up to date. Regularly install the latest patches, updates, and plugins provided by Tenable to ensure accurate and comprehensive vulnerability scanning results.
2. Configure Scans Based on Context: Tailor the scanning configurations to your organization’s specific needs and environment. Consider factors such as network topology, business-critical assets, and compliance requirements when defining scan settings and target hosts.
3. Schedule Regular Scans: Set up a scanning schedule to ensure continuous monitoring of your IT infrastructure. Regularly conduct vulnerability scans to identify new risks and promptly address any emerging vulnerabilities.
4. Validate Scan Results: Before taking remediation actions, validate the identified vulnerabilities to ensure accurate findings. Prioritize the vulnerabilities based on their severity level and the potential impact they may have on your organization.
5. Collaborate with Stakeholders: Engage with different stakeholders, including IT teams, security teams, and management, to ensure effective vulnerability management. Foster collaboration and communication to facilitate prompt remediation actions and ensure alignment with organizational goals.
6. Implement a Patch Management Process: Integrate Nessus Scanner with a robust patch management process to address identified vulnerabilities. Regularly apply security patches and updates to remediate vulnerabilities in a timely manner.
7. Document and Track Remediation Actions: Maintain proper documentation and tracking of remediation efforts. Establish a system to record the status of remediation activities, responsibilities, and timelines. This helps ensure accountability and facilitates reporting and auditing processes.
8. Continuously Monitor Emerging Threats: Stay informed about the latest security threats and vulnerabilities. Regularly review security advisories, subscribe to security mailing lists, and participate in the cybersecurity community to stay ahead of emerging risks and adapt scanning practices accordingly.
9. Train Personnel: Provide adequate training to personnel responsible for using Nessus Scanner. Educate them on scanning techniques, configuration best practices, and interpretation of scan results. This empowers them to leverage the tool effectively and make informed decisions regarding vulnerability management.
10. Regularly Review and Update Security Policies: Review and update security policies and procedures based on insights gained from Nessus Scanner. Continuously assess and adapt security controls, access controls, and configurations to align with identified vulnerabilities and emerging threats.
By following these best practices, organizations can optimize the use of Nessus Scanner for vulnerability assessment and effectively enhance their overall security posture.
Alternatives to Nessus Scanner
While Nessus Scanner is a widely-used and powerful vulnerability assessment tool, there are several alternatives available in the market that organizations can consider based on their specific needs and requirements. Here are some popular alternatives to Nessus Scanner:
1. OpenVAS: OpenVAS (Open Vulnerability Assessment System) is an open-source vulnerability scanner that offers similar capabilities to Nessus. It provides a comprehensive scanning engine, a large vulnerability database, and supports multi-platform scanning. OpenVAS is known for its ease of use and regular updates.
2. Qualys Vulnerability Management: Qualys Vulnerability Management is a cloud-based vulnerability assessment and management platform. It offers real-time scanning, robust reporting, and integration with other security tools. Qualys is known for its scalability, global scanning capabilities, and extensive compliance checks.
3. Rapid7 Nexpose: Rapid7 Nexpose is a vulnerability management solution that combines vulnerability scanning with threat intelligence. It provides comprehensive scanning capabilities, adaptive risk ratings, and integration with other security systems. Rapid7 Nexpose is known for its advanced analytics and comprehensive reporting.
4. BeyondTrust BeyondInsight: BeyondTrust BeyondInsight is a vulnerability management platform that includes vulnerability scanning along with privileged access management capabilities. It offers detailed reporting, risk scoring, and integration with privileged access controls. BeyondTrust BeyondInsight is known for its focus on privileged access security.
5. Acunetix: Acunetix is a web application security scanner that specializes in identifying vulnerabilities in web applications. It offers features such as comprehensive scanning, vulnerability trending, and integration with development tools. Acunetix is known for its emphasis on web application security testing.
6. Tenable.io: Tenable.io is a comprehensive vulnerability management platform that includes vulnerability scanning capabilities. It offers advanced analytics, remediation guidance, and integration with various security tools. Tenable.io is known for its scalability, flexibility, and comprehensive coverage.
7. Qualys WAS: Qualys Web Application Scanning (WAS) is a web application vulnerability scanner that focuses on identifying security vulnerabilities in web applications. It offers automated scanning, in-depth analysis, and integration with other Qualys products. Qualys WAS is known for its extensive web application coverage.
8. Trustwave App Scanner: Trustwave App Scanner is a web application vulnerability scanner that helps identify vulnerabilities in web applications. It provides scanning automation, industry-specific compliance checks, and integration with other security tools. Trustwave App Scanner is known for its ease of use and comprehensive scanning capabilities.
These alternatives to Nessus Scanner offer various features and capabilities that cater to different aspects of vulnerability assessment and security management. Organizations should evaluate their specific requirements and conduct thorough research to select the most suitable alternative to fulfill their needs.
Ultimately, the choice of a vulnerability scanner should be based on factors such as scanning capabilities, integration options, cost, support, and compatibility with the organization’s IT infrastructure.