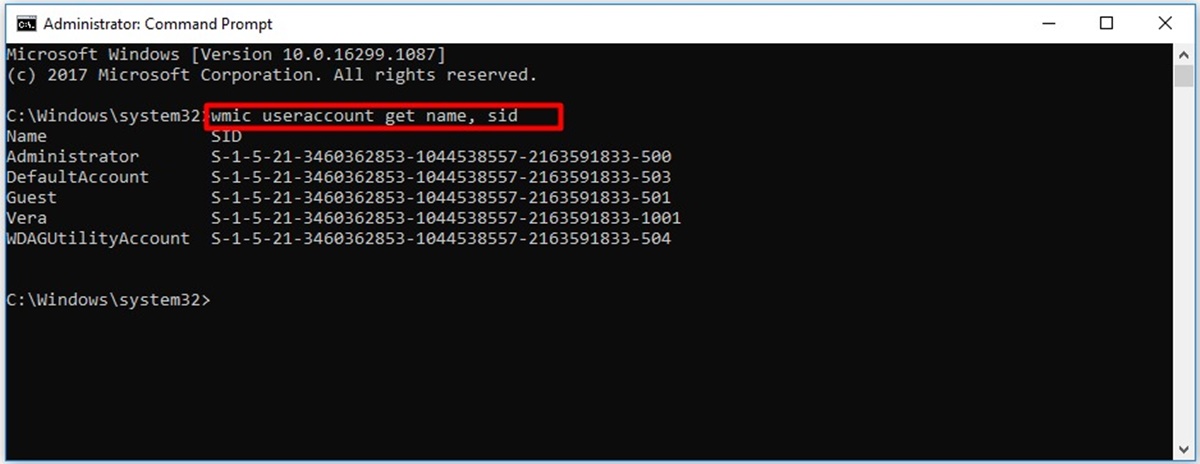
What Is an SID?
A Security Identifier (SID), also known as a SID number, is a unique alphanumeric string that is assigned to each user, group, or computer account in a Windows-based operating system. It serves as a unique identifier and is used to control access to various resources and objects within the system.
The SID plays a critical role in maintaining the security and integrity of a Windows environment. It allows the operating system to differentiate between different entities, ensuring that each user or group is granted the appropriate level of access to files, folders, applications, and other system resources.
The SID structure consists of a fixed-length prefix and a variable-length identifier authority value. The prefix remains the same for all SIDs, while the identifier authority value is unique to each entity. This combination ensures that each SID is globally unique and can be easily identified within the system.
There are different components that make up an SID, including the revision level, a domain or local identifier authority, and a relative identifier (RID). The revision level specifies the version of the SID structure, while the identifier authority value identifies the security authority responsible for generating the SID. The RID represents a unique value assigned to each account within the domain or local system.
SIDs can be presented in different formats, including the string format, the binary format, and the hexadecimal format. These formats allow for easy representation and interpretation of SIDs in various system configurations and applications.
SIDs have numerous applications in Windows security. They are closely tied to user accounts, group accounts, access control, active directory, security policies, file permissions, registry permissions, and more. Understanding SIDs and their role in the Windows environment is essential for managing and troubleshooting user accounts, access rights, and overall system security.
Definition of SID
A Security Identifier (SID) is an alphanumeric string that serves as a unique identifier for each user, group, or computer account in a Windows-based operating system. It is an essential component of the Windows security model and plays a vital role in controlling access to system resources.
The SID, also referred to as a SID number, is assigned during the creation of a user, group, or computer account. It is stored in the security database of the operating system and is used to validate the authenticity and permissions of the account.
Each SID consists of a fixed-length prefix and a variable-length identifier authority value. The prefix remains the same for all SIDs, while the identifier authority value is unique and assigned by a security authority. This combination ensures that the SID is globally unique and can be easily identified within the system.
SIDs are represented in different formats, including string format, binary format, and hexadecimal format. The string format is the most commonly used format and is easily readable by humans. It consists of a series of numbers and characters, such as “S-1-5-21-3623811015-3361044348-30300820-1013”.
The SID is used extensively in Windows security mechanisms. It is used to control access to files, folders, applications, and other system resources. By associating SIDs with specific permissions, the operating system can ensure that only authorized users or groups can access and modify the resources.
Furthermore, SIDs are used in various security-related operations, such as authentication, authorization, access control lists (ACLs), and auditing. They are essential for enforcing security policies, determining user rights and privileges, and tracking user activity within the system.
Purpose of SID
The Security Identifier (SID) serves a crucial purpose in a Windows-based operating system. Its primary function is to uniquely identify user accounts, group accounts, and computer accounts, allowing the system to control access to resources based on the assigned permissions.
One of the key purposes of the SID is to ensure secure authentication and authorization processes. When a user logs into a Windows system, the SID associated with their account is used to verify their identity. The system checks the user’s SID against the access control lists (ACLs) of various resources to determine their level of access.
By using SIDs, administrators can grant or deny privileges to specific users or groups, ensuring that sensitive data and critical system resources remain protected. For example, administrators can assign specific SIDs to certain files or folders, allowing only authorized users or groups to access and modify them.
The SID also plays a central role in access control. It allows administrators to define granular permissions for files, folders, and other resources. By associating SIDs with access control lists, administrators can specify which users or groups have read, write, or execute permissions for a particular resource.
In addition to access control, SIDs facilitate efficient administration of user accounts and group management. Administrators can easily track and manage user accounts by referencing their SIDs, eliminating any confusion or conflicts that may arise from similar usernames or display names.
SIDs are also utilized in auditing and monitoring activities. Security logs and event logs often include SIDs to identify the user or group responsible for a particular action. This helps in investigating security breaches, tracking system activity, and ensuring accountability within the network.
Overall, the purpose of SIDs is to establish a secure and efficient system for managing user accounts, controlling access to resources, and maintaining the integrity of a Windows-based operating system. The unique identification provided by SIDs allows for precise and effective security management, ensuring that only authorized entities can access and modify critical system components.
Structure of SID
The Security Identifier (SID) has a specific structure that allows it to serve as a unique identifier within a Windows-based operating system. Understanding the components of the SID structure is important for effectively managing and configuring security permissions.
Every SID consists of a fixed-length prefix and a variable-length identifier authority value. The prefix is the same for all SIDs and helps identify it as a security identifier. The prefix is represented by the “S-1-” string.
The identifier authority value is a variable-length field that identifies the security authority responsible for generating the SID. It helps differentiate between SIDs generated by different security principals, such as Windows local accounts, domain accounts, or well-known security principals.
For example, the identifier authority value “5” denotes a security principal generated by a Windows local account, while the identifier authority value “21” represents a security principal generated by a domain account.
In addition to the prefix and identifier authority value, the SID structure also includes a relative identifier (RID). The RID is a unique value assigned to each user, group, or computer account within the domain or local system. It is used to distinguish between multiple accounts with the same identifier authority value.
When combined, the identifier authority value and the RID create a globally unique identifier, ensuring that each SID is uniquely identified within the operating system. This uniqueness is crucial for maintaining accurate security permissions and preventing conflicts between different accounts.
It’s important to note that the structure of the SID remains consistent across different user accounts, group accounts, and computer accounts. This consistency allows the operating system to easily identify and validate SIDs during authentication and access control processes.
The structure of the SID can be represented in different formats, including string format, binary format, and hexadecimal format. The string format is the most commonly used and easily understandable by humans. It follows the pattern “S-1-identifier authority value-RID”. For example, “S-1-5-21-3623811015-3361044348-30300820-1013”.
Having a clear understanding of the structure of the SID enables administrators to accurately configure security permissions, troubleshoot access issues, and manage user accounts effectively within the Windows-based operating system.
Components of SID
The Security Identifier (SID) consists of several components that work together to uniquely identify user accounts, group accounts, and computer accounts within a Windows-based operating system. Understanding these components is essential for effectively managing and configuring security permissions.
The first component of the SID is the prefix, which is a fixed-length string that helps identify it as a security identifier. The prefix is represented by the “S-1-” string, indicating that it is a SID within the Windows security model.
Next is the identifier authority value, which is a variable-length field that identifies the security authority responsible for generating the SID. It distinguishes between SIDs generated by different security principals, such as Windows local accounts, domain accounts, or well-known security principals.
The identifier authority value is represented as a series of numbers, such as “5” for a Windows local account or “21” for a domain account. This value plays a crucial role in ensuring that SIDs are unique within the system.
Another component of the SID is the relative identifier (RID). The RID is a unique value assigned to each user, group, or computer account within the domain or local system. It helps differentiate between multiple accounts with the same identifier authority value.
For example, in the SID “S-1-5-21-3623811015-3361044348-30300820-1013”, the RID is “1013”. This value, combined with the identifier authority value, creates a globally unique identifier for a specific account within the operating system.
Additionally, the SID may contain subauthorities, which are optional components that further refine the identification process. Subauthorities are represented by a series of numbers following the RID and are used in specific scenarios, such as identifying domain groups or built-in Windows groups.
The SID structure ensures that each account within the Windows environment is uniquely identified and can be easily referenced in the system. By combining the prefix, identifier authority value, RID, and optional subauthorities, the SID provides a comprehensive representation of a security principal within the operating system.
Understanding the components of the SID is crucial for managing access controls, configuring permissions, and troubleshooting security-related issues. By grasping the inner workings of the SID, administrators can effectively manage user accounts, group accounts, and computer accounts, ensuring the security and integrity of the Windows-based operating system.
SID Formats
The Security Identifier (SID) can be represented in different formats, providing flexibility and ease of use in various system configurations and applications. Understanding these formats is essential for working with and interpreting SIDs within a Windows-based operating system.
The most commonly used format for representing SIDs is the string format. In this format, the SID is represented as a series of numbers and characters, such as “S-1-5-21-3623811015-3361044348-30300820-1013”. This format is human-readable and widely used in user interfaces, security management tools, and configuration files.
Another format is the binary format, where the SID is represented as a binary data structure. This format is primarily used within the operating system and is not easily readable by humans. It is commonly used in system-level operations, such as authentication and access control, where efficiency and performance are critical.
The hexadecimal format is another representation of the SID that provides a compact and concise way to represent the binary data structure. In this format, the SID is represented as a series of hexadecimal numbers and characters. For example, “S-1-5-21-59FBDB8A-4EBD3A51-1013”. This format is often used in network protocols, registry entries, and scripting languages.
It’s important to note that regardless of the format used, the information contained within the SID remains the same. The format is merely a representation of the underlying SID structure, allowing for easy interpretation and manipulation in different contexts.
When working with SIDs, it’s crucial to ensure that the format is correctly specified and used. Incorrectly formatted SIDs can lead to access issues, security vulnerabilities, and system errors. Therefore, it’s important to follow the appropriate format guidelines and standards provided by the operating system and the applications being utilized.
Types of SIDs
Within a Windows-based operating system, there are several types of Security Identifiers (SIDs) that are used to uniquely identify different entities and security principals. Understanding these types of SIDs is important for effective management of user accounts, group accounts, and computer accounts.
1. Well-Known SIDs: These SIDs are standardized and pre-defined by the operating system. They identify commonly used security principals, such as the built-in Administrators group (S-1-5-32-544) or the Everyone group (S-1-1-0). Well-known SIDs simplify the process of assigning permissions and access rights to common system resources.
2. Domain SIDs: These SIDs are generated and assigned to user accounts, group accounts, and computer accounts that belong to a particular domain within a Windows Active Directory environment. Domain SIDs typically start with the identifier authority value “5” and are followed by a series of numbers unique to the domain.
3. Local SIDs: These SIDs are generated and assigned to user accounts, group accounts, and computer accounts that exist within a specific Windows local system. Local SIDs are used in standalone systems or workgroup environments where Active Directory is not present. Local SIDs commonly start with the identifier authority value “21” and are followed by a series of numbers unique to the local system.
4. Relative SIDs: These SIDs are generated dynamically by combining the identifier authority value and a relative identifier (RID). Relative SIDs are used to identify user accounts, group accounts, and computer accounts that are specific to a domain or a local system. RIDs are unique values assigned to each account and are combined with the identifier authority to create a globally unique SID.
5. Object SIDs: These SIDs are assigned to security objects, such as files, folders, registry keys, and printers. Object SIDs grant or deny access permissions to these resources. Object SIDs can be used to facilitate access control and authorization, ensuring that only authorized entities can interact with specific resources.
Understanding the different types of SIDs allows administrators to effectively manage and configure security permissions, control access to resources, and maintain the integrity of the Windows-based operating system. Whether it’s working with well-known SIDs, domain SIDs, local SIDs, relative SIDs, or object SIDs, a comprehensive understanding of these identifiers is crucial for maintaining a secure and efficient system environment.
SID and Windows Security
The Security Identifier (SID) plays a fundamental role in the overall security of a Windows-based operating system. It is intricately woven into the fabric of Windows security mechanisms and is used to control access to resources, enforce permissions, and maintain the integrity of the system.
One key aspect of Windows security that relies heavily on SIDs is the authentication process. When a user attempts to log into a Windows system, their SID is used to validate their identity. The operating system checks the SID against the access control lists (ACLs) of various resources to determine if the user has the necessary permissions to access them.
Access control is another crucial aspect of Windows security that depends on SIDs. Access Control Lists (ACLs) contain entries that associate SIDs with specific permissions for resources, such as files, folders, and registry keys. By associating SIDs with access rights, Windows ensures that only authorized users or groups can interact with and modify these resources, effectively safeguarding sensitive data and system components.
SIDs are also central to user account management and group membership within Windows security. Whenever a new user account is created, a unique SID is generated and assigned to that account. This SID is then used to track and manage the account’s permissions, privileges, and access rights throughout the system.
Similarly, group accounts in Windows rely on SIDs to define membership and permissions. Each group account is assigned a unique SID, and user accounts are associated with these groups through their SIDs. This enables administrators to efficiently manage and configure permissions for multiple users by working with group SIDs rather than individual user SIDs.
Furthermore, SIDs are instrumental in auditing and monitoring activities within the Windows environment. When security events occur, such as file access attempts or changes to system settings, SIDs are logged in the security logs and event logs. This allows administrators to track and investigate system activity, identify potential security breaches, and maintain accountability within the network.
Overall, SIDs are a foundational component of Windows security. By providing unique identification for user accounts, group accounts, and resources, SIDs enable the secure and controlled access of critical system assets. With this central role in authentication, access control, account management, and auditing, SIDs are key to maintaining a robust and secure Windows environment.
SID and User Accounts
The Security Identifier (SID) is closely tied to user accounts within a Windows-based operating system. It plays a crucial role in identifying and managing user accounts, ensuring secure access to system resources, and maintaining the integrity of the system.
When a user account is created in a Windows environment, a unique SID is generated and assigned to that account. This SID serves as the primary identifier for the user and allows the operating system to associate the account with its associated permissions, privileges, and access rights.
The SID assigned to a user account remains constant throughout the account’s lifecycle, even if the account is renamed. This ensures that the account’s unique identifier remains consistent, facilitating smooth management of access controls and security configurations.
By associating SIDs with user accounts, Windows can enforce fine-grained access control. Access Control Lists (ACLs) contain entries that link SIDs to specific permissions for various system resources, such as files, folders, or applications. This allows administrators to grant or deny access to specific users based on their associated SID.
Moreover, SIDs are utilized when granting or limiting privileges to user accounts. Privileges determine the actions a user can perform on the system, such as the ability to install software, modify system settings, or manage user accounts. By associating the appropriate SIDs with user accounts, administrators can assign privileges on an individual basis.
SIDs also play a crucial role in group membership management. When a user account is added or removed from a group, the SID associated with the user is added or removed from the group’s membership list. This linking of user account SIDs and group account SIDs allows for efficient management of user permissions and access through group-based configurations.
SID and Group Accounts
The Security Identifier (SID) is integral to the management and functionality of group accounts within a Windows-based operating system. SIDs enable efficient administration of group memberships and provide a foundation for controlling access to system resources.
Group accounts serve as collections of user accounts, allowing administrators to apply permissions, privileges, and settings to multiple users simultaneously. Each group account is assigned a unique SID, which serves as the identifier for that specific group within the Windows environment.
When a user account is added to a group, the SID associated with the user account is added to the group’s membership list. This mechanism provides an efficient way for administrators to manage user permissions and access across multiple users.
The use of SIDs in group accounts enables administrators to grant or deny access to resources based on group membership. Access Control Lists (ACLs) associate SIDs with specific permissions for files, folders, and other resources. By adding or removing the group’s SID from an ACL, administrators can instantly adjust the permissions for all users in that group.
SIDs also play a crucial role in nested group membership. Nested groups allow for hierarchical organization of user accounts, where a group can be a member of another group. This hierarchy allows for more granular access control and simplifies permission management for large organizations. Each group has its own unique SID, ensuring proper identification and differentiation within the Windows environment.
By leveraging the power of group accounts and SIDs, Windows provides a flexible and scalable approach to managing access control and security. SIDs enable efficient membership management, simplify permission assignments, and streamline the administration of user permissions across the system.
Furthermore, SIDs contribute to the flexibility and versatility of group accounts by allowing cross-domain and cross-forest group memberships. An SID can be used to identify and manage group memberships across different domains or forest boundaries, enhancing the administration and coordination of user access throughout the Windows network.
SID and Access Control
The Security Identifier (SID) is a critical component in implementing access control mechanisms within a Windows-based operating system. SIDs enable precise control over the permissions and privileges granted to users, groups, and processes, ensuring the security and integrity of system resources.
SIDs are associated with access control lists (ACLs), which are used to specify the permissions for various system resources, such as files, folders, registry keys, and printers. Each ACL entry links a specific SID to a set of permissions, defining what actions can be performed on the resource.
By associating SIDs with ACLs, administrators can grant or deny access to specific users or groups based on their assigned SIDs. When a user or group attempts to access a resource, the operating system checks the associated SID against the ACL entries to determine whether to allow or deny the requested action.
Access control based on SIDs provides fine-grained control over resource permissions. The permissions associated with each SID can include read, write, execute, modify, delete, and more, giving administrators the ability to precisely define the level of access each user or group has to a resource.
SIDs are also utilized in role-based access control (RBAC), where permissions are assigned based on predefined roles rather than individual users. In RBAC, SIDs are associated with role groups, and users are assigned to these roles by their SIDs. This simplifies access control management by allowing for the efficient assignment and modification of permissions based on group membership.
Additionally, SIDs play a crucial role in auditing and logging activities within the Windows environment. When security events occur, such as resource access attempts or changes to permissions, SIDs are recorded in the security logs and event logs. This enables administrators to track and investigate system activity, helping identify potential security breaches and ensuring accountability.
Overall, the use of SIDs in access control provides a robust and flexible framework for managing permissions and securing system resources. SIDs allow administrators to implement precise control over user and group access, ensuring that only authorized individuals can perform specific actions. By leveraging SIDs in access control, administrators can enforce security policies, minimize unauthorized access, and protect sensitive data within the Windows operating system.
SID and Active Directory
The Security Identifier (SID) plays a vital role in the context of Active Directory, which is a directory service developed by Microsoft for Windows-based operating systems. SIDs are used extensively within Active Directory to uniquely identify objects, such as user accounts, group accounts, and computer accounts.
In an Active Directory environment, each object, including user accounts and group accounts, is assigned a unique SID. This SID is used to differentiate and identify the objects within the directory, regardless of their location in the network.
One of the primary benefits of using SIDs in Active Directory is the ability to maintain consistent object identification across network boundaries. SIDs remain the same throughout an object’s lifecycle, whether it is moved between domains, forests, or organizational units. This ensures that objects retain their assigned permissions, group memberships, and access rights, even when the directory structure undergoes changes.
SIDs are an essential component in the implementation of access control within Active Directory. Access Control Lists (ACLs) associate SIDs with specific permissions for directory objects. Administrators can assign permissions based on SIDs, ensuring that the appropriate users or groups have the necessary access rights to perform actions such as reading, modifying, or deleting objects within the directory.
Furthermore, SIDs facilitate the implementation of group policies within Active Directory. Group policies allow administrators to define and enforce centralized settings and configurations for user accounts and computers. By associating SIDs with group policies, administrators can efficiently apply specific policies to appropriate groups, ensuring consistent configurations and security settings throughout the network.
Active Directory also leverages SIDs for trust relationships between domains and forests. Trust relationships enable secure communication and resource sharing between different domains or forests. The use of SIDs in trust relationships ensures that objects from trusted domains or forests are correctly identified and granted the appropriate access rights within the network.
SIDs are also crucial in the replication process within Active Directory. When objects are replicated between domain controllers, their SIDs form the basis for uniquely identifying and resolving conflicts that may arise during the replication process.
SID and Security Policies
The Security Identifier (SID) plays a significant role in the implementation of security policies within a Windows-based operating system. SIDs enable administrators to enforce consistent security configurations and settings across the network, ensuring the protection of system resources and data.
Security policies in Windows include a wide range of settings, such as password complexity requirements, account lockout policies, user rights assignments, audit policies, and more. These policies define the security parameters that govern user access, authentication, and authorization within the system.
When configuring security policies, administrators often associate SIDs with various settings and permissions. This allows policies to be applied to specific users, groups, or security principals based on their assigned SIDs.
For example, when defining user rights assignments in a security policy, SIDs are used to specify which users or groups have particular privileges, such as the ability to log on locally, change system time, or manage user accounts. By associating SIDs with user rights, policies can be tailored to specific user or group requirements.
Similarly, SIDs are utilized when configuring audit policies to track and monitor system activity. Administrators can specify which SIDs should be audited for specific events or actions, enabling the collection of relevant security logs. This ensures that auditing is focused on the appropriate entities within the network.
Active Directory Group Policy Objects (GPOs) leverage SIDs to enforce security policies across domains and organizational units. By linking SIDs to GPOs, administrators can easily apply security configurations, control access permissions, and manage security settings for different user accounts, group accounts, or computer accounts within the network.
SIDs also play a crucial role in implementing security policies that involve access control and restrictions. SIDs are associated with access control lists (ACLs), which define the permissions granted or denied to users or groups for various resources. Policies can be configured to utilize SIDs in ACLs to restrict or allow access to sensitive information or critical system components.
SID and File Permissions
The Security Identifier (SID) is a crucial component in managing file permissions within a Windows-based operating system. SIDs are used to associate specific users or groups with permissions, ensuring secure and controlled access to files and folders.
File permissions determine what actions can be performed on a file or folder, such as reading, writing, modifying, or deleting. SIDs provide a unique identifier for users and groups, enabling administrators to assign permissions based on their associated SIDs.
Access Control Lists (ACLs) are used to define file permissions, and SIDs are an integral part of ACL entries. Each entry in an ACL links a specific SID to a set of permissions, allowing or denying access to the associated entity.
When a file or folder is accessed, the operating system checks the SID associated with the user or group against the ACL entries to determine if the requested action should be granted or denied.
SIDs provide several advantages when it comes to file permissions. Firstly, they allow for granular control over access privileges. Administrators can assign permissions to specific users or groups by associating their SIDs with appropriate entries in the ACL. This ensures that only authorized entities can interact with the file or folder, minimizing the risk of unauthorized access or data breaches.
Secondly, SIDs facilitate efficient management of file permissions. When a user or group’s membership changes, such as adding or removing users from a group, the associated SIDs within the ACL entries are automatically updated. This dynamic updating simplifies permission management and ensures that file permissions remain up to date as the user or group membership changes.
Moreover, SIDs enable the inheritance of file permissions. When a folder inherits permissions from its parent, the SIDs associated with the parent’s ACL entries will also be inherited. This allows for streamlined permission propagation, reducing the administrative effort required to configure permissions for multiple files or folders.
Lastly, SIDs facilitate cross-domain or cross-forest file permissions. When accessing files or folders across different domains or forests, the SIDs associated with users or groups are used to verify their access rights. This ensures that access permissions are correctly applied, even in complex network environments.
SID and Registry Permissions
The Security Identifier (SID) is instrumental in managing registry permissions within a Windows-based operating system. SIDs are used to associate specific users or groups with permissions, allowing for controlled and secure access to registry keys and values.
Similar to file permissions, registry permissions determine what actions can be performed on specific registry keys or values, such as reading, writing, modifying, or deleting. SIDs provide a unique identifier for users and groups, enabling administrators to assign permissions based on their associated SIDs.
Registry keys and values are protected by access control lists (ACLs), and each ACL entry is linked to a specific SID. This association allows administrators to specify the permissions granted or denied to the associated entity within the registry.
When an application or process attempts to access a registry key or value, the operating system checks the SID associated with the user or group against the ACL entries to determine if the requested action should be allowed or denied.
SIDs offer several advantages when it comes to managing registry permissions. Firstly, they enable administrators to assign permissions at a granular level. By associating SIDs with specific registry keys or values in the ACL entries, administrators can control who can access, modify, or delete them. This ensures that only authorized users or groups can interact with the registry and helps protect critical system configurations and sensitive data.
Secondly, SIDs simplify the management of registry permissions. When a user or group’s membership changes, such as adding or removing users from a group, the associated SIDs within the ACL entries are automatically updated. This dynamic updating of SIDs minimizes administrative effort and ensures that registry permissions remain consistent as user or group membership changes.
Additionally, SIDs allow for the inheritance of registry permissions. When a parent registry key has permissions defined, child keys can inherit these permissions. The SIDs associated with the parent’s ACL entries are also inherited, reducing the need to explicitly define permissions for each individual key. This inheritance ensures consistency and simplifies the management of registry permissions.
Lastly, SIDs enable the application of registry permissions across different domains or forests. When accessing registry keys or values in a multi-domain or multi-forest environment, the SIDs associated with users or groups are used to verify their access rights. This ensures that access permissions are correctly applied, even in complex network configurations.
Overall, SIDs provide a reliable and scalable approach to managing registry permissions in a Windows environment. By utilizing SIDs, administrators can enforce secure access controls, protect critical registry configurations, and maintain regulatory compliance within the system.
Troubleshooting SID Issues
Troubleshooting Security Identifier (SID) issues can be crucial in resolving access and permission problems within a Windows-based operating system. SIDs are essential for accurately identifying and controlling user accounts, group accounts, and access to system resources. Here are some common troubleshooting steps for resolving SID-related issues:
1. Verify SID correspondence: Ensure that the SID associated with an object, such as a user account or group account, matches the expected SID. Mismatches can occur during migrations, domain changes, or account re-creations. Tools like the PowerShell command “Get-ADUser” or third-party tools can assist in verifying SIDs.
2. Check permissions: Review the permissions associated with the object’s SID. Use the appropriate tool, such as the Security tab in File Explorer or the Registry Editor, to examine the ACLs and verify if the necessary permissions are granted to the SID.
3. Resolve invalid SIDs: If an invalid SID is encountered, it typically means the associated account or object has been deleted or does not exist. Use tools like the SubInACL command-line tool or PowerShell scripts to remove or fix invalid SIDs from ACLs.
4. Troubleshoot access denied errors: If a user encounters “Access Denied” errors, ensuring the correct SID is assigned the appropriate permissions is essential. Verify the user’s permissions, group membership, and any inherited permissions to determine the cause of the access issue.
5. Investigate missing or unknown SIDs: If a SID shows as “unknown” or is missing from ACLs, it could indicate a problem with the associated account or object. Verify if the account or object has been deleted or if there are synchronization issues between domain controllers. Resolve any synchronization problems and update ACLs accordingly.
6. Resolve SID conflicts: SID conflicts can occur when two different objects have the same SID. This usually happens during account migrations or SID duplication. To resolve conflicts, use tools such as the PowerShell cmdlet “Test-ComputerSecureChannel” for computer accounts or the “NewSid” utility for user accounts.
7. Check for SID history: In scenarios involving migrations or domain changes, migrated objects may retain a SID history. Ensure that the SID history is correctly maintained and replicated across all relevant domains to avoid permission issues.
8. Monitor event logs: Check the security event logs for any SID-related errors or warnings. Event IDs such as 4625 (failed logon attempts), 560 (object access), or 577 (privileged service operation) can provide insights into SID-related issues and help identify the source of the problem.
9. Consider SID filtering and trust relationships: In complex network environments with trust relationships between domains or forests, ensure SID filtering is correctly configured to prevent unauthorized access. Check trust relationships and investigate any issues impacting the resolution of SIDs across domains.
10. Consult documentation and support resources: When faced with persistent SID issues, referring to official documentation, knowledge bases, or seeking assistance from Microsoft support resources can provide valuable insights and guidance to resolve complex problems.
By following these troubleshooting steps and leveraging the appropriate tools, administrators can effectively diagnose and resolve SID-related issues, ensuring proper access control, permissions, and system integrity within a Windows environment.
SID Best Practices
Following best practices regarding Security Identifiers (SIDs) is crucial for maintaining a secure and well-managed Windows-based operating system. Adhering to these practices can help ensure accurate identification of entities, effective access control, and simplified management of user accounts and permissions.
1. Understand and document SIDs: Familiarize yourself with the concept and structure of SIDs. Document the SIDs associated with critical user accounts, group accounts, and security principals within your environment. This information will be helpful for troubleshooting, auditing, and managing permissions in the future.
2. Regularly review and update permissions: Conduct regular audits of ACLs and permissions associated with SIDs. Ensure that permissions align with the principle of least privilege, granting only the necessary access rights for users and groups. Regularly review and adjust permissions based on organizational requirements and changes in user groupings.
3. Follow secure account management practices: When creating user accounts or group accounts, assign unique SIDs and adhere to proper naming conventions. Avoid using generic or easily guessable names that could compromise security.
4. Implement strong password policies: Strong passwords add an extra layer of security to user accounts. Enforce password complexity requirements, such as minimum length, inclusion of alphanumeric characters, and regular password changes.
5. Regularly validate SIDs and group memberships: Verify and reconcile SIDs and group memberships periodically to address any discrepancies or discrepancies that might arise due to changes in your network structure, such as domain migrations or reorganizations.
6. Document and follow proper SID resolution procedures: Develop clear procedures for resolving conflicts, invalid SIDs, and unknown SIDs. This includes steps to remove obsolete or incorrect SIDs, as well as reassigning SIDs in case of conflicts or duplication.
7. Regularly monitor event logs: Monitor security event logs for any SID-related errors or suspicious activities. Regularly review these logs to identify and address potential security threats or issues.
8. Practice backup and recovery of SIDs: Incorporate SID backups as part of your data backup strategy. Take periodic backups of critical SID-related configurations, such as access control lists and group memberships, to ensure recoverability in case of system failures.
9. Stay updated on security best practices: Continuously stay informed about security best practices, industry trends, and emerging threats. Regularly check for security updates, patches, and recommendations from reputable sources, such as Microsoft’s Security Compliance Toolkit, to ensure your SID-related configurations align with the latest security standards.
10. Regularly train and educate users: Educate users about the importance of SIDs, access control, and secure account management. Promote awareness about best practices for creating strong passwords and following security policies to minimize the risk of account compromises.
By following these SID best practices, you can reinforce the security of your Windows-based operating system, enhance access control, and streamline the management of user accounts and permissions.
SID vs. UID (User Identifier)
When it comes to identifying users within a computer system, two commonly used terms are the Security Identifier (SID) and the User Identifier (UID). While both serve to uniquely identify users, there are significant differences between the two.
The SID is primarily used in Windows-based operating systems, whereas the UID is commonly associated with Unix-like systems and Linux-based operating systems.
SIDs are alphanumeric strings that uniquely identify user accounts, group accounts, and computer accounts within a Windows environment. They are essential for controlling access to system resources and maintaining secure authentication and authorization processes. SIDs are globally unique within the Windows network and are associated with access control lists (ACLs) to determine resource permissions.
On the other hand, UIDs are numeric identifiers assigned to each user account within Unix-like systems. UIDs are stored in the user account databases of these systems, such as the /etc/passwd file. UIDs help distinguish and manage user accounts, allowing the operating system to determine ownership of files, directories, and processes.
One key difference between SIDs and UIDs lies in their structure and format. SIDs are structured as hierarchical strings, composed of a prefix, an identifier authority value, and a relative identifier (RID). UIDs are simply numeric values and are typically assigned incrementally as new user accounts are created.
Another distinction is in how SIDs and UIDs are used for access control. SIDs utilize ACLs to define permissions for resources within a Windows environment, ensuring that only authorized users or groups can access and modify them. UIDs, on the other hand, are primarily used to determine ownership of files, allowing the operating system to enforce file-level access controls.
Furthermore, SIDs play a crucial role in managing user accounts across different domains and forests within a Windows network, ensuring consistency and security. UIDs, however, are typically limited to a single system or network and do not have the same level of cross-domain functionality as SIDs.
While SIDs are specific to Windows environments and UIDs to Unix-like systems, there are cases where cross-platform compatibility is required. In these cases, solutions such as the Lightweight Directory Access Protocol (LDAP) can be utilized to bridge the gap between Windows and Unix-like systems, enabling translation and synchronization of user identities across platforms.
SID vs. GUID (Globally Unique Identifier)
When working with systems that require unique identification of entities, two commonly used terms are the Security Identifier (SID) and the Globally Unique Identifier (GUID). While both serve the purpose of providing unique identification, there are important distinctions between the two.
SIDs are primarily used in Windows-based operating systems to identify users, groups, and computer accounts. SIDs are alphanumeric strings with a hierarchical structure that is specific to the Windows security model. They are globally unique within the Windows network and play a critical role in access control, authentication, and authorization processes.
On the other hand, GUIDs are more generic and widely used across different platforms and systems. GUIDs are also alphanumeric strings, but they follow a specific structure defined by the Distributed Computing Environment (DCE) standard. GUIDs are globally unique identifiers and are generated using various algorithms to minimize the likelihood of collisions.
One key distinction between SIDs and GUIDs lies in their usage and scope. SIDs are specific to Windows environments and are primarily used for access control and security-related operations within the Windows security model. GUIDs, on the other hand, are not tied to any particular system or platform and have a broader applicability across different programming languages, databases, and software frameworks.
Another difference is the format and structure of SIDs versus GUIDs. SIDs have a hierarchical structure consisting of a prefix, an identifier authority value, and a relative identifier (RID). This structure helps ensure uniqueness within the Windows environment. GUIDs, however, follow a flat structure and do not have hierarchical components. GUIDs are typically represented as 128-bit values in hexadecimal format, offering a larger pool of possible unique identifiers.
In terms of purpose, SIDs are predominantly used for access control, authentication, and authorization within Windows environments. They are closely tied to user accounts, group accounts, and resource permissions. In contrast, GUIDs have a broader range of applications. They are commonly used for generating unique identifiers in various scenarios, such as database records, file naming, application development, and distributed systems communication.
While SIDs are more constrained in their usage and specific to the Windows platform, GUIDs offer greater versatility and can be used across different platforms, systems, and programming languages. GUIDs provide a reliable means of generating unique identifiers for a wide range of purposes, facilitating interoperability and compatibility.
Overall, SIDs and GUIDs serve distinct but important functions in uniquely identifying entities within different contexts. SIDs excel in providing security-focused identification within Windows environments, while GUIDs offer a more general-purpose unique identifier solution applicable across various systems and platforms.
SID Limitations and Challenges
While Security Identifiers (SIDs) play a crucial role in the Windows security model, they also come with their own set of limitations and challenges. It’s important to be aware of these limitations to effectively manage and troubleshoot SID-related issues:
1. Complexity in cross-platform environments: SIDs are specific to Windows environments and may not have direct interoperability with other operating systems. This can pose challenges when working in cross-platform environments, requiring additional effort to synchronize and manage identities across different systems or platforms.
2. Migration and compatibility issues: Migrating user accounts, groups, or security principals between different domains, forests, or systems can lead to compatibility issues with SIDs. Mismatches or inconsistencies in the SID structures can impact access control, permissions, and user/group mappings, requiring careful planning and proper validation during migration processes.
3. Difficulty in renaming accounts: Renaming user accounts or group accounts can be challenging due to the dependence on SIDs. Changing an account’s name does not automatically update its associated SID, potentially causing inconsistencies between the account’s name and its underlying SID. Proper steps and tools are required to reconcile the changes and maintain consistency.
4. Complexity in troubleshooting: When troubleshooting access issues or permission conflicts, identifying the specific SID associated with an account or group can be challenging. Troubleshooting SID-related issues requires in-depth knowledge of the Windows security model, command-line tools, and understanding of ACLs and permissions.
5. SID conflicts or duplication: Conflicts or duplications in SIDs can occur when migrating accounts or during domain restructuring. If two different security principals possess the same SID, this can lead to permissions problems, access denials, and inconsistencies in user or group management. Resolving SID conflicts requires careful analysis and steps to ensure accurate identification and differentiation of security principals.
6. Performance impact: Extensive use of SIDs in access control and permissions can impact system performance, particularly in environments with a large number of users and groups or complex ACL configurations. Regular audits and optimizations of permissions can help mitigate potential performance bottlenecks.
7. Potential for information leakage: In certain scenarios, the presence of SIDs in file system metadata or other system components can inadvertently expose internal information about the system configuration, domain structure, or user accounts. Proper security measures should be taken to minimize the risk of unauthorized access or disclosure of sensitive information.
Despite these limitations and challenges, SIDs remain an essential component of the Windows security model. Understanding their limitations and implementing appropriate management and troubleshooting practices can help mitigate their impact and maintain a secure and well-managed system environment.