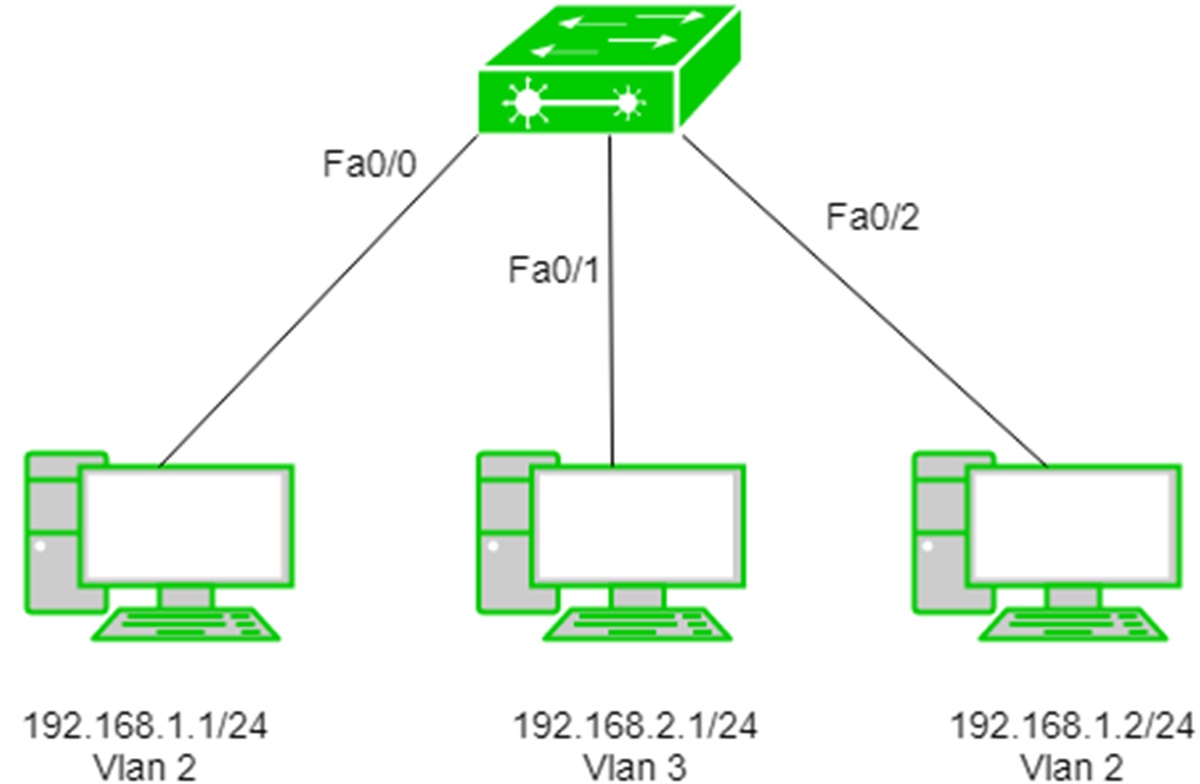
Benefits of VLANs
VLANs, or Virtual Local Area Networks, offer a range of benefits for organizations looking to enhance their network security, performance, and management. By dividing a physical network into multiple logical segments, VLANs bring flexibility and efficiency to network administration. Here are some key advantages of implementing VLANs:
- Enhanced Network Security: VLANs provide a robust security solution by isolating different groups of users or departments. This isolation prevents unauthorized access to sensitive information and reduces the risk of data breaches. VLANs also enable the implementation of access control lists (ACLs) to control traffic between VLANs, further strengthening network security.
- Improved Network Performance: By separating network traffic into distinct VLANs, organizations can reduce network congestion and improve overall performance. VLANs help optimize bandwidth usage and minimize broadcast storms, which can occur when network devices flood the network with unnecessary broadcast messages.
- Simplified Network Management: VLANs allow network administrators to logically group users and network resources based on department, function, or any other criteria. This logical segmentation simplifies network management tasks, such as adding or removing users and applying network policies. Instead of making changes to the entire network, administrators can focus on specific VLANs, making troubleshooting and maintenance more efficient.
- Increased Flexibility and Scalability: With VLANs, organizations have the flexibility to reconfigure their network infrastructure without physically relocating devices. VLANs can easily be extended across physical switches, enabling efficient resource utilization and accommodating changes in organizational structure or network requirements.
- Cost Savings: VLANs can help organizations reduce costs by eliminating the need for separate physical networks for different departments or user groups. Instead of deploying multiple cable runs and additional networking equipment, VLANs leverage existing infrastructure to create logical network segments.
Overall, VLANs provide a powerful solution for network segmentation, security, and management. By implementing VLANs, organizations can ensure a more efficient, secure, and scalable network infrastructure.
How VLANs Work
VLANs, or Virtual Local Area Networks, function by logically segmenting a physical network into smaller, isolated virtual networks. This segmentation is achieved through the use of VLAN tags, which are embedded within Ethernet frames to identify and control traffic flow. Here’s a closer look at how VLANs work:
VLAN Tagging: When a device sends an Ethernet frame, a VLAN tag is added to the frame’s header. This tag contains information about the VLAN to which the frame belongs. The VLAN tag consists of a 12-bit VLAN identifier (VID) that uniquely identifies the VLAN. Devices connected to the same VLAN share the same VLAN tag.
Switch Port Configuration: Switch ports can be assigned to specific VLANs to control where traffic is allowed to flow. Ports can be configured as access ports, which can only be associated with a single VLAN, or as trunk ports, which carry traffic for multiple VLANs. Trunk ports typically connect switches together and use VLAN tagging to distinguish traffic between different VLANs.
Network Segmentation: By assigning devices and switch ports to different VLANs, network administrators can segment traffic based on specific criteria, such as department, location, or function. Devices within the same VLAN can communicate with each other, while devices across different VLANs require a routing device to enable communication.
Inter-VLAN Routing: VLANs are designed to be isolated from one another, but there are cases where communication between VLANs is necessary. This is where inter-VLAN routing comes into play. A router or Layer 3 switch is used to route traffic between different VLANs, allowing devices in separate VLANs to communicate with each other.
VLAN Management: VLANs need to be properly managed to ensure their effectiveness. This involves tasks such as assigning VLAN tags, configuring switch ports, and implementing VLAN membership policies. Network administrators can use VLAN management tools or network management software to streamline these tasks and ensure the smooth operation of the VLAN infrastructure.
Overall, VLANs work by leveraging VLAN tagging to create separate virtual networks within a physical network infrastructure. This segmentation provides improved network security, performance, and flexibility, allowing organizations to optimize their network resources and meet their specific network requirements.
Types of VLANs
There are various types of VLANs that organizations can implement based on their specific network requirements. Each type serves a different purpose and facilitates different types of communication and management. Here are some common types of VLANs:
- Port-Based VLANs: Port-based VLANs are the most basic type of VLAN and are configured based on switch ports. Each switch port is assigned to a specific VLAN, and devices connected to those ports belong to that VLAN. Port-based VLANs are simple to configure and provide a straightforward way to segment a network.
- MAC-Based VLANs: MAC-based VLANs use the MAC (Media Access Control) address of a device to assign it to a specific VLAN. Devices with specific MAC addresses are associated with particular VLANs, allowing network administrators to create VLANs based on the physical devices connected to the network. This type of VLAN enables granular control over device-to-VLAN mapping.
- Protocol-Based VLANs: Protocol-based VLANs categorize network traffic based on protocols, such as IP, IPX, or AppleTalk. Traffic of a specific protocol is assigned to a corresponding VLAN, ensuring that different network protocols are logically separated. This type of VLAN is useful in environments where there is a mix of protocols being used.
- Dynamic VLANs: Dynamic VLANs automatically assign devices to VLANs based on certain criteria, such as authentication credentials or device attributes. This type of VLAN allows for dynamic and flexible network assignment, making it ideal for environments where devices frequently connect and disconnect from the network.
- Community VLANs: Community VLANs group devices that share common requirements or functions, regardless of their physical location or department. Devices within a community VLAN can communicate with each other, but the VLAN is isolated from other VLANs. This type of VLAN is beneficial for facilitating collaboration and resource sharing among specific groups.
In addition to these types, organizations can also create a combination of VLANs to meet their unique network needs. For example, they may utilize a combination of port-based, MAC-based, and protocol-based VLANs to achieve a fine-grained level of network segmentation and control.
The choice of VLAN type depends on factors such as network size, complexity, desired levels of control, and the specific network environment. By selecting the appropriate VLAN type(s), organizations can effectively manage their network resources, optimize performance, and enhance network security.
VLAN Tagging
VLAN tagging plays a crucial role in the functioning of Virtual Local Area Networks (VLANs). It involves adding specific identifying information to Ethernet frames, allowing switches and devices to understand which VLAN the frame belongs to. VLAN tagging enables the proper routing and forwarding of traffic within VLAN-based networks. Here’s a closer look at VLAN tagging:
VLAN Tag Formats: VLAN tags follow a specific format defined by the IEEE 802.1Q standard. The VLAN tag is inserted into the Ethernet frame’s header and consists of a 4-byte (32-bit) field. The tag incorporates a 12-bit VLAN identifier (VID) that indicates the VLAN to which the frame belongs.
Tagged and Untagged Frames: Frames can be either tagged or untagged. Untagged frames are regular Ethernet frames that do not contain a VLAN tag. They are typically used in access ports, where a device is directly connected to a specific VLAN. Tagged frames, on the other hand, include a VLAN tag and are used to carry traffic between switches or devices within a VLAN.
Port-Based VLAN Tagging: In port-based VLAN tagging, each switch port is assigned to a specific VLAN. All frames received on that port are automatically assigned the corresponding VLAN tag. This tagging is transparent to the connected devices, which do not need to be VLAN-aware.
802.1Q Tagging: The 802.1Q tagging is the most commonly used VLAN tagging method. It allows for interoperability between different network devices and is supported by most Ethernet switches. With 802.1Q tagging, frames are inserted with a VLAN tag that contains the VID, indicating the VLAN to which the frame belongs.
Q-in-Q Tagging: Q-in-Q tagging, or double tagging, is an extension of 802.1Q tagging. It enables the encapsulation of VLAN-tagged frames within another VLAN tag. This technique is helpful for service providers or organizations that need to transport VLAN-tagged traffic over a provider’s network without the risk of VID overlap.
VLAN Tag Preservation: When frames traverse a network, it’s essential to preserve VLAN tags to ensure proper routing and forwarding. Switches, routers, and other network devices must support VLAN tagging by recognizing and preserving the tags throughout the network infrastructure.
VLAN tagging allows for the efficient and secure transmission of traffic in VLAN-based networks. It enables switches and devices to classify and route traffic based on the VLAN tags, ensuring that frames reach the intended VLANs. By understanding and implementing VLAN tagging correctly, organizations can establish and maintain effective network segmentation, enhancing network performance and security.
VLAN Trunking Protocol (VTP)
VLAN Trunking Protocol (VTP) is a Cisco proprietary protocol that simplifies the management and configuration of VLANs in a network. It allows for the seamless propagation of VLAN information across switches, reducing administrative overhead and ensuring consistency in VLAN configurations. Let’s delve into the key aspects of VTP:
VTP Operation: VTP operates in a client-server model, where one switch acts as the VTP server and others act as VTP clients. The server is responsible for managing and distributing VLAN information, while the clients receive and synchronize VLAN updates from the server.
VTP Messages: VTP exchanges information through VTP advertisements, which contain details about VLANs, including their names, numbers, and parameter settings. When a switch receives an advertisement, it can update its VLAN database and forward the advertisement to other switches to ensure consistency across the network.
VTP Modes: There are three VTP modes: server, client, and transparent. The VTP server is the switch responsible for managing VLANs and propagating their information. VTP clients receive VLAN updates from the server and cannot make changes to VLAN configurations. Transparent mode switches do not participate in VTP updates but can still create and modify VLANs locally.
VTP Pruning: VTP pruning is a feature that limits the unnecessary flooding of broadcast traffic onto VLANs that do not require it. By enabling VTP pruning, switches can dynamically prune VLANs on trunk links, ensuring that broadcast traffic only reaches the VLANs that need it. This improves network performance and reduces bandwidth utilization.
VTP Versions: VTP has multiple versions, with the most common being VTPv2 and VTPv3. VTPv2 provides basic VLAN configuration and management capabilities, while VTPv3 offers enhancements such as support for extended VLANs and improved security through authentication.
VTP Security: VTP also includes security features to protect against unauthorized changes or disruptions. These include VTP passwords, which ensure that switches must authenticate before participating in VTP updates, and VTP pruning domain names, which prevent unauthorized switches from joining the VLAN domain.
VTP simplifies VLAN management by enabling centralized configuration and distribution of VLAN information. It reduces the chances of misconfigurations and inconsistencies, making VLAN administration more efficient. However, it’s essential to carefully plan and configure VTP to prevent unintended consequences and ensure network stability and security.
Inter-VLAN Routing
Inter-VLAN routing is the process of enabling communication between different VLANs within a network. Since VLANs are designed to isolate traffic by default, inter-VLAN routing is necessary to facilitate the exchange of data and resources between VLANs. Here’s how inter-VLAN routing works:
Layer 3 Switch or Router: To perform inter-VLAN routing, a layer 3 switch or router is required. These devices have the capability to route traffic between different VLANs based on their IP addresses. Layer 3 switches are often preferred as they offer faster routing speeds compared to traditional routers.
Virtual Interfaces: The layer 3 switch or router needs to have virtual interfaces (SVIs) configured for each VLAN involved in inter-VLAN routing. Each SVI is associated with a specific VLAN and acts as the default gateway for devices within that VLAN. These virtual interfaces enable the routing of traffic between VLANs.
Routing Protocols and Static Routes: Inter-VLAN routing can be accomplished using routing protocols, such as OSPF or EIGRP, to dynamically exchange routing information and determine the best path for traffic between VLANs. Alternatively, static routes can be manually configured to specify the routes between VLANs. The choice between dynamic routing protocols and static routes depends on the network’s complexity and scalability requirements.
Access Control Lists (ACLs): ACLs can be implemented to control the traffic flow between VLANs. By applying ACLs to the SVIs, network administrators can enforce security policies, allowing or denying specific types of traffic between VLANs. ACLs provide an additional layer of security and control over inter-VLAN communication.
Routing Configuration: The routing configuration involves assigning the appropriate IP addresses to the SVIs associated with each VLAN. The layer 3 switch or router needs to be configured to route traffic between the VLANs and ensure connectivity. The configuration can be done via a command-line interface or a graphical user interface provided by the network device manufacturer.
Inter-VLAN routing is crucial for enabling efficient communication and resource sharing across VLANs. It allows devices in one VLAN to communicate with devices in another VLAN, facilitating collaboration and access to shared resources. By implementing inter-VLAN routing, organizations can accommodate different network requirements and enhance the flexibility and scalability of their networks.
VLAN Security
VLANs provide a significant level of network segmentation and isolation, which helps enhance security by reducing the attack surface and limiting the scope of potential security breaches. However, ensuring VLAN security requires additional measures beyond simply implementing VLANs. Here are some essential considerations for securing VLANs:
VLAN Access Control: Controlling access to VLANs is crucial for maintaining security. This can be achieved through port-based access control, where switch ports are configured to only allow specific devices to connect to a particular VLAN. By implementing strict access control, organizations can prevent unauthorized devices from joining VLANs and accessing sensitive resources.
Private VLANs (PVLANs): PVLANs provide an additional layer of isolation by dividing a VLAN into sub-VLANs, known as secondary VLANs. PVLANs restrict communication between devices within the same PVLAN, while allowing communication with devices in other, designated PVLANs. This is particularly useful for scenarios where there is a need to isolate sensitive systems or guest networks from other VLANs.
VLAN Segmentation: Proper VLAN segmentation is essential for preventing unauthorized access across different network segments. Critical systems, such as servers or sensitive data, can be placed in separate VLANs and protected with stricter access controls. By separating traffic into different VLANs based on security requirements, organizations can minimize the risk of unauthorized access or lateral movement.
VLAN Monitoring: Implementing VLAN monitoring tools and protocols allows network administrators to keep track of network traffic and detect any abnormal activity or unauthorized attempts to access VLANs. Monitoring tools provide insights into network behavior, aiding in identifying and responding to potential security threats in a timely manner.
Network Segmentation and Perimeter Security: VLANs should be used alongside other security measures, such as firewalls and intrusion prevention systems (IPS), to protect against external threats. Segmenting the network into VLANs provides an additional layer of defense, complementing perimeter security measures by containing potential breaches and limiting the impact on the overall network.
Regular Auditing and Updates: Regular audits should be conducted to identify any security vulnerabilities or misconfigurations within VLANs. It is also crucial to keep network devices, including switches and routers, up to date with the latest firmware and security patches to address any known vulnerabilities and ensure the integrity of VLAN security measures.
Implementing and maintaining robust VLAN security practices is essential for protecting sensitive data, preventing unauthorized access, and minimizing the impact of security breaches. By combining VLAN security measures with other network security best practices, organizations can create a layered security approach that effectively protects their networks and the resources contained within them.
VLAN Management
Effective VLAN management is crucial for maintaining a well-organized and secure network infrastructure. It involves various tasks and processes to ensure proper configuration, monitoring, and maintenance of VLANs. Here are some key aspects of VLAN management:
VLAN Planning: Proper planning is essential before implementing VLANs. This involves identifying the VLAN requirements and determining the number of VLANs needed, based on factors such as departmental segregation, security requirements, and network traffic patterns. Planning ensures that VLANs are structured in a way that aligns with the organization’s network goals and optimizes network performance.
VLAN Documentation: Documentation is crucial for effective VLAN management. It should include a comprehensive record of VLAN configurations, including VLAN IDs, names, associated subnets, associated switches, and any specific VLAN settings or policies. Having accurate and up-to-date documentation helps with troubleshooting, network maintenance, and future expansions or modifications.
VLAN Provisioning and Configuration: VLAN provisioning involves creating and configuring VLANs on network devices, such as switches and routers. This includes assigning VLAN IDs, VLAN names, and VLAN parameters, such as IP address ranges or VLAN membership policies. Automated provisioning tools or network management software can simplify and streamline this process.
VLAN Monitoring and Troubleshooting: Regular monitoring of VLAN traffic and performance is important to identify potential issues or anomalies. Network administrators should utilize monitoring tools to track VLAN utilization, detect unusual traffic patterns, and troubleshoot any connectivity or performance problems. By actively monitoring VLANs, administrators can ensure optimal network performance and promptly address any issues that arise.
VLAN Maintenance and Updates: VLAN configurations may need to be updated or modified as network requirements evolve. This could include adding or removing VLANs, adjusting VLAN parameters, or reconfiguring VLAN membership. It’s crucial to plan and schedule regular maintenance windows to perform necessary updates, patches, and configuration changes to ensure the stability and security of VLANs.
Training and Education: Network administrators and IT personnel should receive appropriate training on VLAN management, configuration best practices, and troubleshooting techniques. Understanding VLAN concepts, protocols, and security measures enables administrators to confidently manage and maintain VLANs and respond effectively to any VLAN-related issues or incidents.
Efficient VLAN management is essential for maintaining an organized and secure network infrastructure. By implementing proper planning, documentation, provisioning, monitoring, troubleshooting, maintenance, and training practices, organizations can maximize the benefits of VLANs, optimize network performance, and effectively manage their network resources.