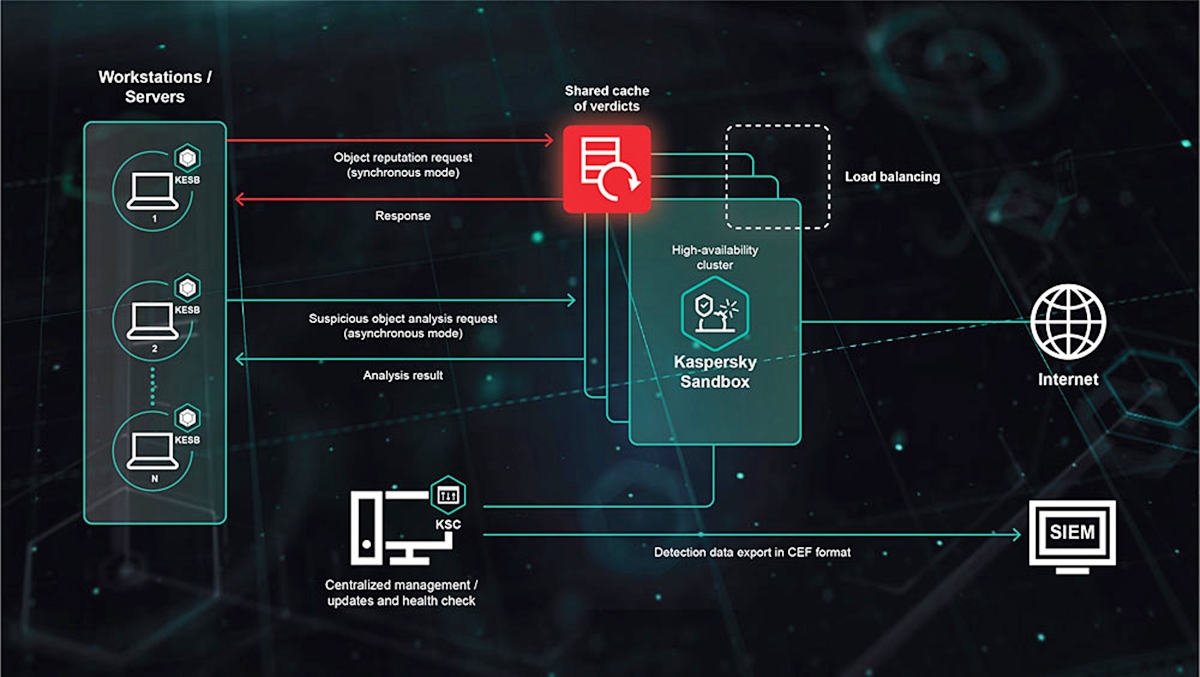
What is a Malware Sandbox?
A malware sandbox is a controlled, isolated virtual environment that is used to analyze and execute hazardous software, such as malware samples or suspicious files, in a secure manner. It provides cybersecurity professionals with a safe space to study the behavior and characteristics of malware without risking the integrity of their systems.
In a malware sandbox, the malicious code is executed in a controlled environment, separate from the rest of the network, operating system, or applications. This isolation prevents the malware from spreading or causing any damage to the host system. By observing the behavior and actions of the malware, analysts can gain valuable insights into its capabilities, intentions, and potential threats it poses.
The primary purpose of a malware sandbox is to detect and analyze unknown or zero-day malware. These are types of malware that have not been previously identified or have no known signature or pattern. Traditional antivirus software often relies on signature-based detection, which means it can only detect malware that matches a pre-defined set of known malicious signatures. However, zero-day malware can bypass these signature-based defenses, making them a significant threat.
By running suspicious files or URLs in a malware sandbox, security experts can observe their behavior and identify any malicious activities or indicators of compromise. This analysis helps in understanding the functionality, propagation methods, network communication, and payload delivery mechanisms of the malware.
Malware sandboxes can be implemented as a physical or virtual appliance, or they can be cloud-based solutions. These sandboxes utilize various techniques, such as system monitoring, behavioral analysis, dynamic code analysis, and network traffic analysis, to detect and analyze malware.
Overall, a malware sandbox is an essential tool in the arsenal of cybersecurity professionals. It provides a safe environment to study malware and helps organizations stay ahead of evolving threats by understanding the tactics and techniques employed by malicious actors.
How Does a Malware Sandbox Work?
A malware sandbox functions by isolating potentially harmful software within a controlled environment to analyze its behavior and determine its threat level. Let’s explore the key steps involved in the workings of a malware sandbox:
1. Execution: When a suspicious file or URL is submitted to the sandbox, it is executed in an isolated environment. This environment is designed to emulate a real operating system, providing the malware with the necessary resources to run.
2. Behavior Monitoring: The sandbox closely monitors the behavior of the malware during execution. It tracks file system modifications, registry changes, network communication, and any other actions performed by the malicious code.
3. Dynamic Analysis: The sandbox employs various techniques, such as dynamic code analysis, to understand the behavior of the malware in runtime. It examines the sequence of instructions executed by the malware to identify any malicious activities or patterns.
4. Network Traffic Analysis: The sandbox captures and analyzes network traffic generated by the malware. This analysis helps in uncovering any suspicious network connections, data exfiltration attempts, or communication with command-and-control servers.
5. Payload Analysis: If the malware contains a payload, such as a malicious file or script, the sandbox extracts and analyzes it separately. This allows for a deeper understanding of the specific actions the payload performs.
6. Reporting and Alerting: Throughout the analysis process, the sandbox generates detailed reports on the behavior and characteristics of the malware. It may also trigger alerts if it identifies any malicious or suspicious activities.
By following these steps, a malware sandbox provides valuable insights into the behavior and capabilities of the analyzed malware. This information can then be used to enhance threat intelligence, develop effective countermeasures, and strengthen overall cybersecurity defenses.
Benefits of Using a Malware Sandbox
The use of a malware sandbox offers several important benefits for organizations in their cybersecurity efforts. Let’s explore some of the key advantages:
1. Threat Detection: A malware sandbox provides an effective means of detecting and analyzing unknown or zero-day malware. By executing suspicious files within the isolated environment, security teams can identify and understand the behavior of previously unseen threats.
2. Behavior Analysis: Sandbox environments allow for in-depth behavior analysis of malware. Security experts can observe how the malicious code interacts with the system, what processes it initiates, and how it attempts to evade detection. This information helps in developing countermeasures and enhancing overall threat awareness.
3. Risk Mitigation: By executing malware samples in an isolated environment, the sandbox prevents any harm to the host systems. This isolation reduces the risk of malware spreading throughout the network or causing damage to critical infrastructure and sensitive data.
4. Incident Response: Malware sandboxes play a crucial role in incident response processes. They allow security teams to analyze potential threats in a controlled environment, gather valuable information, and make informed decisions regarding containment, remediation, and prevention of future attacks.
5. Training and Research: Malware sandboxes also serve as valuable tools for training and research purposes. Security professionals can use them to simulate real-world attack scenarios, test security tools, and explore new malware trends and techniques.
6. Enhanced Threat Intelligence: By studying the behavior and characteristics of different malware samples, organizations can develop comprehensive threat intelligence. This knowledge assists in identifying common attack patterns, understanding the tactics of threat actors, and improving proactive defense strategies.
7. Improved Security Effectiveness: Integrating a malware sandbox into the security stack enhances overall security effectiveness. It allows for more accurate detection and faster response to emerging threats, ultimately reducing the organization’s risk exposure and potential impact of cybersecurity incidents.
Types of Analysis Performed in a Malware Sandbox
A malware sandbox enables various types of analysis to be conducted on suspicious files or URLs. These analyses help security teams gain comprehensive insights into the behavior and characteristics of malware. Let’s explore some of the key types of analysis performed in a malware sandbox:
1. Static Analysis: Static analysis involves examining the characteristics of a file or code without executing it. In a malware sandbox, static analysis techniques include extracting metadata, such as file attributes, header information, and imports/exports, to identify potential indicators of malicious intent.
2. Dynamic Analysis: Dynamic analysis involves monitoring the behavior of malware as it executes within the sandbox. This analysis allows security experts to observe the actions and interactions of the malware with the underlying system, capturing information such as system calls, registry modifications, and network communications.
3. Behavioral Analysis: Behavioral analysis focuses on studying how malware behaves within the sandbox environment. It involves monitoring and documenting the specific actions performed by the malware, including file system modifications, process creation, network connections, and attempts to evade detection or spread.
4. Code Analysis: Code analysis involves examining the underlying code of the malware to understand its functionality and potential vulnerabilities. This analysis helps in identifying exploit techniques, encryption methods, obfuscation mechanisms, and any other code-level characteristics that may be informative for devising mitigation strategies.
5. Network Traffic Analysis: Malware often relies on network connections to communicate with command-and-control servers, transfer data, or download additional payloads. Network traffic analysis in a malware sandbox helps in identifying suspicious or malicious connections, analyzing communication protocols, and detecting potential data exfiltration attempts.
6. Payload Analysis: Malware may contain payloads such as malicious files or scripts that are designed to execute specific actions. Analyzing these payloads within a malware sandbox allows security teams to isolate and understand the specific functionalities, obfuscation techniques, or destructive capabilities of the payload.
7. Heuristic Analysis: Heuristic analysis involves using algorithms and scanning techniques to identify patterns or behavior that are indicative of malware, even if they do not match known signatures. By employing heuristics in a malware sandbox, security professionals can detect and categorize potential threats based on suspicious or abnormal behavior.
By performing these different types of analysis, security teams can gain comprehensive knowledge of malware samples, enabling them to develop effective mitigation strategies, improve incident response, and enhance the overall security posture of the organization.
Limitations of Malware Sandboxing
While malware sandboxes provide valuable insights into the behavior and characteristics of malicious software, they also have certain limitations. Understanding these limitations is crucial to ensure a comprehensive approach to cybersecurity. Let’s explore some of the key limitations of malware sandboxes:
1. Evasion Techniques: Malware authors are constantly evolving their techniques to evade detection and analysis by sandboxes. They may employ anti-analysis techniques, such as checking for the presence of virtualized or sandboxing environments, delaying malicious payloads, or encrypting their communication to bypass traditional sandbox detection methods.
2. Time Constraints: Modern malware often behaves in a way that depends on specific time intervals or events to carry out its malicious activities. Some advanced malware can remain dormant for an extended period to escape detection during the sandbox analysis, making it difficult to observe its true behavior within a limited time frame.
3. Polymorphic Malware: Polymorphic malware is capable of altering its code structure or encryption techniques to evade detection. This type of malware can present a challenge for malware sandboxes as they may struggle to analyze the continually changing code, thus making it harder to detect and understand.
4. Subversion of Analysis: Sophisticated malware can detect the presence of a sandbox environment and modify its behavior accordingly or even refuse to execute at all. By doing so, the malware can evade analysis and make it difficult for security teams to understand its threat level.
5. Resource Limitations: Analyzing malware within a sandbox requires significant computing resources, including memory, processing power, and storage. Large-scale or resource-intensive malware may overwhelm the sandbox environment, leading to incomplete analysis or system instability.
6. Zero-Day Vulnerabilities: Malware sandboxes are effective in detecting known or previously identified threats. However, they may struggle to identify zero-day vulnerabilities or newly emerging malware that do not match any existing signatures or patterns. This limitation emphasizes the importance of combining sandboxes with other detection methods and ongoing threat intelligence.
7. Human Analysis: While malware sandboxes automate the analysis process, they may lack the human element required to understand a malware sample comprehensively. Human analysts can provide contextual knowledge, interpret complex behaviors, and identify unique characteristics that automated systems may overlook.
Despite these limitations, malware sandboxes remain an essential tool in an organization’s cybersecurity arsenal. By understanding these limitations and implementing supplementary security strategies, organizations can enhance their defense posture and stay ahead of emerging threats.
Features to Look for in a Malware Sandbox Solution
When selecting a malware sandbox solution, it is essential to consider several key features to ensure the effectiveness and efficiency of your malware analysis. Here are some important features to look for:
1. Isolation and Virtualization: A robust malware sandbox should provide a secure and isolated environment for executing malware samples. It should use virtualization or containerization technologies to ensure that the malware does not infiltrate or harm the host system or network.
2. Behavior Monitoring and Analysis: The sandbox should offer comprehensive behavior monitoring and analysis capabilities. This includes tracking file system modifications, registry changes, network traffic, and process activities to provide detailed insights into the behavior of the malware.
3. Dynamic Code Analysis: The ability to perform dynamic code analysis is crucial in understanding the execution flow of malware and identifying malicious actions. The sandbox should support the analysis of a variety of programming languages and provide detailed reports on code execution sequences.
4. Network Traffic Capture and Analysis: Malware often relies on network connectivity for communication and spreading. A malware sandbox should capture and analyze network traffic to identify any suspicious connections, command-and-control communication, or data exfiltration attempts.
5. Detection of Evasion Techniques: Advanced malware employs evasion techniques to avoid detection, such as checking for virtualized environments or sandbox analysis. The sandbox should have mechanisms to detect and counter these techniques to provide accurate and reliable analysis results.
6. Reporting and Alerting: A good malware sandbox solution should generate detailed reports on the behavior, indicators of compromise, and potential threats identified during analysis. It should also provide customizable alerts and notifications to keep security teams informed about critical findings.
7. Integration with Threat Intelligence: Integration with threat intelligence feeds and external security solutions enhances the malware sandbox’s effectiveness. This integration enables the sandbox to leverage up-to-date threat intelligence, enrich analysis results, and automate response actions based on identified threats.
8. Scalability and Performance: It is crucial to choose a malware sandbox solution that can handle high volumes of malware samples and scale as your organization’s needs grow. The sandbox should be capable of efficient analysis without significant performance degradation.
9. User-Friendly Interface: An intuitive and user-friendly interface simplifies the configuration, management, and analysis of malware samples. Look for a sandbox solution that offers a clean and easy-to-use interface, allowing security analysts to work efficiently and effectively.
By considering these key features, organizations can choose a malware sandbox solution that meets their specific analysis requirements, enhances detection capabilities, and strengthens their overall cybersecurity defenses.
How to Use a Malware Sandbox Effectively
Using a malware sandbox effectively requires a systematic approach and adherence to best practices. Here are some key steps to ensure optimal utilization of a malware sandbox:
1. Proper Configuration: Configure the sandbox environment to closely mimic your production network setup. This includes emulating the operating system versions, system configurations, and network topologies that closely resemble your organization’s environment.
2. Collection of Relevant Samples: Gather a diverse range of malware samples, including known malware, suspicious files, and zero-day threats. This helps in building a comprehensive library that can be used for analysis and understanding evolving threats.
3. Analyze Both Static and Dynamic Properties: Utilize both static and dynamic analysis techniques to gain a complete picture of the malware’s behavior. Static analysis focuses on examining the file’s attributes, while dynamic analysis observes its behavior during execution in the sandbox environment.
4. Monitor and Document Behavior: Carefully monitor and document the behavior and actions of the malware within the sandbox. Capture detailed information about its file system modifications, registry changes, network communications, and suspicious activities to aid in analysis and future threat detection.
5. Monitor Network Communications: Analyze the network traffic generated by the malware within the sandbox. Identify any abnormal or malicious connections, data transfers, or command-and-control communications. This helps in understanding the malware’s network behavior and potential impact on your organization.
6. Perform Payload Analysis: If the malware contains payloads, such as downloaded files or scripts, extract and analyze them separately. Investigate the nature and purpose of the payloads to gain deeper insights into the malware’s intentions and potential impact.
7. Integrate with Threat Intelligence: Connect the malware sandbox with threat intelligence feeds and security solutions. This integration enhances the analysis process by cross-referencing indicators of compromise and enriching the understanding of malware behavior and associated risks.
8. Collaborate and Share Findings: Foster collaboration among security analysts and teams by sharing findings and lessons learned from malware sandbox analysis. This promotes knowledge sharing, enables faster response to emerging threats, and strengthens overall cybersecurity measures.
9. Continuous Learning and Improvement: Malware evolves rapidly, so it is essential to stay updated with emerging trends, attack techniques, and evolving malware. Continuously refine and improve the malware sandboxing process and analysis methodologies to adapt to new threats effectively.
By following these best practices and adopting a proactive approach, organizations can leverage malware sandboxes effectively to detect, analyze, and understand the behavior of malicious software, reinforcing their cybersecurity defenses and mitigating potential risks.
Integrating Malware Sandboxing into Your Cybersecurity Strategy
Integrating malware sandboxing into your cybersecurity strategy is a crucial step in enhancing your organization’s defense against evolving threats. Here are some key considerations for effectively integrating malware sandboxes into your cybersecurity strategy:
1. Identify Key Use Cases: Determine the specific use cases where malware sandboxing can provide the most value for your organization. Whether it’s analyzing suspicious email attachments, testing new software, or examining potential threats from external sources, identify the areas where malware sandboxing can have the most significant impact.
2. Select the Right Sandbox Solution: Choose a malware sandbox solution that aligns with your organization’s needs, infrastructure, and budget. Consider factors such as capabilities, scalability, ease of use, integration with existing security tools, and ongoing support when evaluating different sandboxing solutions.
3. Define Clear Objectives and Workflows: Establish clear objectives for malware sandboxing within your cybersecurity strategy. Determine how the analysis results will be used, who will be responsible for analyzing the output, and how the findings will be incorporated into incident response procedures and ongoing threat intelligence efforts.
4. Integrate with Existing Security Infrastructure: Ensure seamless integration of the malware sandbox with your existing security infrastructure. Integrate with threat intelligence feeds, security information and event management (SIEM) systems, and other security solutions to enrich analysis results, automate response actions, and provide a holistic view of your organization’s security posture.
5. Establish Data Sharing and Collaboration: Foster an environment of collaboration among security teams and analysts. Encourage the sharing of analysis findings, threat intelligence, and lessons learned from sandboxing to strengthen the collective knowledge and response capabilities of your organization.
6. Automate Analysis and Response: Leverage automation capabilities within the malware sandbox solution to streamline the analysis process and improve response times. Define rules and triggers that automatically initiate analysis, generate alerts, and trigger response actions based on identified threats or suspicious behavior.
7. Continuously Monitor and Update: Regularly monitor and update your malware sandboxing environment. Keep the sandbox solution up to date with the latest threat intelligence feeds, malware signatures, and software updates to ensure optimal detection and analysis capabilities.
8. Regularly Review and Improve: Conduct periodic reviews of your malware sandboxing strategy to identify areas for improvement. Analyze the effectiveness of the sandbox solution, assess the accuracy of analysis results, and refine your workflows and procedures based on lessons learned and emerging threat trends.
By integrating malware sandboxing into your cybersecurity strategy, you can proactively detect and analyze threats, gain valuable insights into malware behavior, and enhance your overall defense against evolving cyber threats.
Real-World Examples of Malware Sandbox Use
Malware sandboxes have been widely adopted by organizations across various industries to detect and analyze malicious software. Here are a few real-world examples highlighting the practical applications of malware sandboxing:
1. Advanced Persistent Threat (APT) Detection: A financial institution implemented a malware sandbox solution to detect advanced targeted attacks. Through sandbox analysis, the organization identified and analyzed unknown malware samples that were used in a sophisticated APT campaign. This enabled the security team to understand the techniques employed by the threat actors and implement appropriate countermeasures.
2. Malware Behavior Analysis: A manufacturing company regularly runs suspicious files through a malware sandbox to analyze their behavior. On one occasion, a seemingly harmless document was discovered to be a dropper for a cryptomining malware. The sandbox analysis demonstrated the malicious behavior of the file, identifying its propagation method and the potential damage it could cause if executed.
3. Zero-Day Threat Identification: A cybersecurity firm utilized a malware sandbox to detect and study zero-day threats. In one instance, they observed a unique malware sample exhibiting behavior that matched the characteristics of a previously undisclosed vulnerability. The sandbox analysis helped the researchers develop a patch for the vulnerability and provide early warnings to their clients.
4. Spear Phishing Campaign Analysis: A large enterprise utilized a sandbox solution to analyze suspicious email attachments from suspected spear phishing campaigns. By executing the attachments within the sandbox, the security team identified hidden malicious payloads and analyzed their behavior, contributing to the organization’s proactive stance against targeted attacks.
5. IoT Device Vulnerability Assessment: A technology company leveraged a malware sandbox to assess the security of their Internet of Things (IoT) devices. By running firmware updates and patches through the sandbox, they were able to identify any potential vulnerabilities and ensure that the devices were not compromised by malware before deploying them to customer networks.
6. Analysis of Ransomware Variants: A healthcare organization employed a malware sandbox solution to analyze different strains of ransomware. By executing ransomware samples within the sandbox, they were able to identify the encryption behavior and communication patterns of each variant. This information assisted in developing robust incident response and recovery plans in the case of a ransomware attack.
These real-world examples demonstrate the practical significance of malware sandboxing in detecting, analyzing, and mitigating various types of malware. By utilizing this approach, organizations can enhance their cybersecurity strategies and stay ahead of emerging threats.
The Future of Malware Sandboxing
The field of malware sandboxing continues to evolve as cyber threats become more sophisticated and prevalent. The future of malware sandboxing promises advancements in technology, techniques, and integration with other cybersecurity solutions. Here are some key areas that represent the future of malware sandboxing:
1. Machine Learning and Artificial Intelligence: The integration of machine learning and artificial intelligence (AI) into malware sandboxing holds great potential. By leveraging these technologies, sandboxes can become more adept at automatically detecting and analyzing new and evolving malware variants, reducing the need for manual intervention and increasing the speed and accuracy of threat detection.
2. Enhanced Evasion Detection: Malware authors will continue to develop advanced evasion techniques to bypass traditional sandboxing mechanisms. To counter this, future sandbox solutions will employ advanced evasion detection methods, including improved monitoring of system behaviors, application of heuristics, and the use of network traffic analysis to identify evasive malware.
3. Cloud-Based Sandboxing: Cloud-based malware sandboxes provide scalability, flexibility, and on-demand resources. In the future, organizations will increasingly adopt cloud-based sandbox solutions to handle the growing volume of malware samples and benefit from the collaborative threat intelligence that can be shared among cloud-based sandboxes.
4. Deeper Malware Analysis: Future sandboxes will focus on conducting more comprehensive analysis of malware samples. This will involve deeper inspection of vulnerabilities, advanced code analysis techniques, and emulation of the targeted environments to simulate the potential impact of the malware if it were to successfully infiltrate the actual systems.
5. Integration with Threat Intelligence: Integration with threat intelligence platforms and systems will be further enhanced to provide real-time updates on emerging threats, IoCs (Indicators of Compromise), and global threat landscape insights. This integration will enrich the sandbox analysis results and improve proactive threat detection and response capabilities.
6. Collaboration and Information Sharing: Increased collaboration among security organizations will drive the future of malware sandboxing. Sharing sandboxed analysis results, malware signatures, and threat intelligence will enable collective defense against rapidly evolving threats and help the global security community stay one step ahead of malicious actors.
7. Enhanced User Experience: The user experience will play a significant role in the future of malware sandboxing. Sandbox solutions will focus on providing intuitive interfaces, streamlined workflows, and automated analysis features to make it easier for security analysts to leverage the full capabilities of the sandbox and make faster and more informed decisions.
The future of malware sandboxing is driven by the constant evolution of cyber threats and the need for innovative solutions to detect and analyze these threats effectively. By embracing advancements in technology and collaborative approaches, organizations can strengthen their cybersecurity defenses and stay ahead of emerging malware and attack vectors.