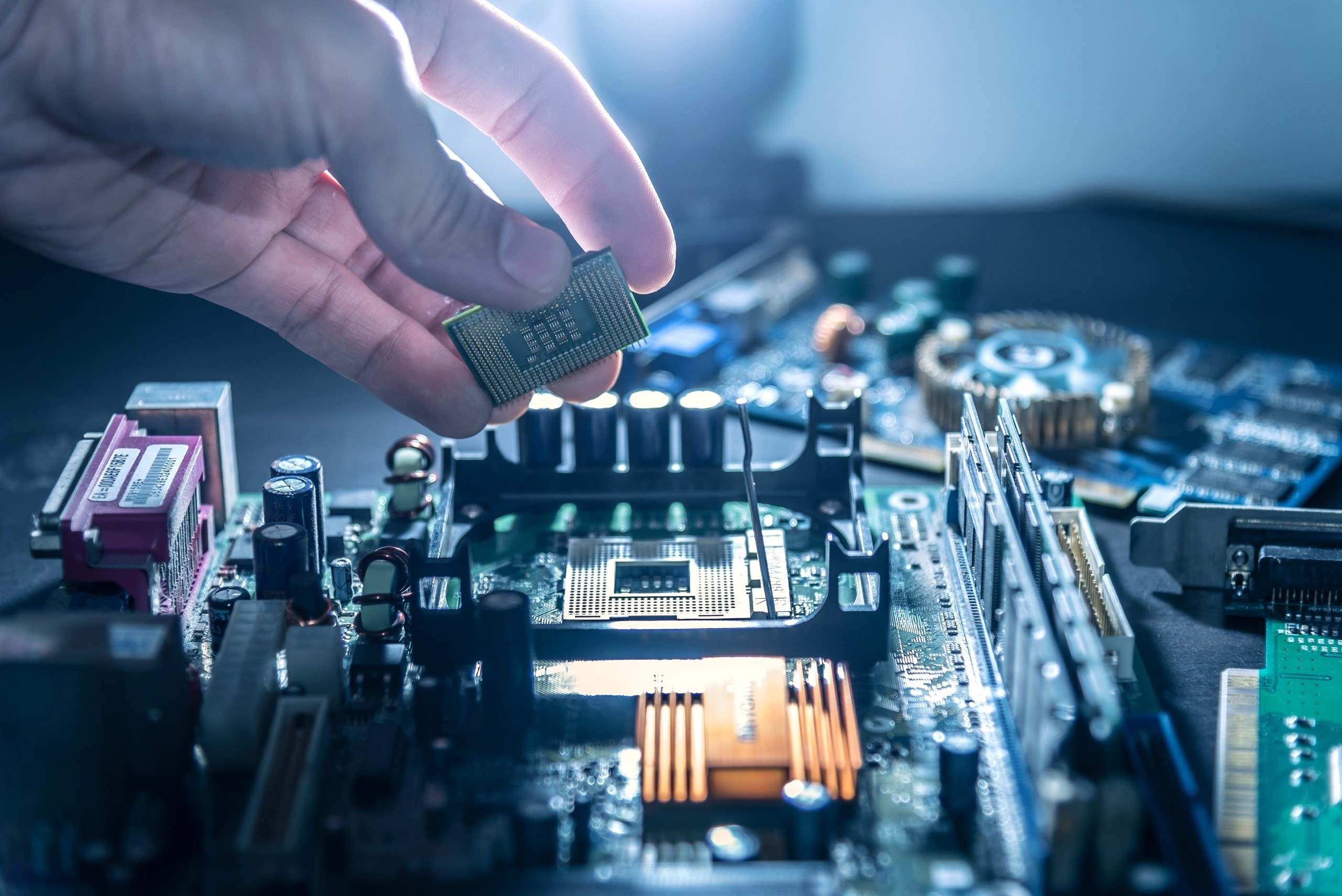
What is the TPM Connector?
The Trusted Platform Module (TPM) connector is a crucial component found on many modern motherboards. It serves as a physical interface for connecting a TPM module, which plays a pivotal role in ensuring system security and integrity. Essentially, the TPM connector enables the integration of hardware-based security features into a computer system, offering protection against various forms of attacks and unauthorized access.
The TPM module, when connected to the TPM connector, provides a secure enclave for storing cryptographic keys, passwords, and other sensitive data. This secure storage is isolated from the main CPU and memory, making it extremely difficult for malicious software or attackers to tamper with or extract the stored information. As a result, the TPM module enhances the overall security posture of the system, safeguarding sensitive data and mitigating the risks associated with unauthorized access and data breaches.
In essence, the TPM connector serves as the gateway for leveraging the capabilities of a TPM module, enabling robust security features that are integral to modern computing environments. It acts as the physical link between the motherboard and the TPM module, facilitating the seamless integration of hardware-based security measures into the system architecture. This integration is fundamental in fortifying the overall security infrastructure of the computer, making it more resilient against a wide array of potential threats.
Through the TPM connector, the motherboard can effectively harness the security capabilities of the TPM module, thereby enhancing the system's ability to protect sensitive information and resist various forms of attacks. The utilization of the TPM connector and module represents a proactive approach to bolstering security, aligning with the evolving landscape of cybersecurity threats and the imperative to safeguard digital assets and privacy.
Why is the TPM Connector Important?
The TPM connector holds significant importance in the realm of computer security and data integrity. Its relevance stems from the pivotal role it plays in enabling the utilization of TPM modules, which are instrumental in fortifying the security posture of modern computer systems.
One of the primary reasons why the TPM connector is important lies in its ability to facilitate hardware-based security measures. By connecting a TPM module to the motherboard via the TPM connector, users can leverage the module’s capabilities to establish a secure environment for sensitive data and cryptographic operations. This is particularly crucial in scenarios where the protection of confidential information, such as encryption keys, is paramount. The TPM module, when integrated through the connector, empowers the system to safeguard critical data from unauthorized access and malicious exploits, thereby bolstering the overall security infrastructure.
Furthermore, the TPM connector is essential for enabling trusted computing functionalities. Through the integration of a TPM module, the system gains the ability to verify the integrity of its components and ensure that it has not been compromised by unauthorized modifications or malware. This capability is pivotal in establishing a foundation of trust within the system, allowing for secure boot processes and the validation of system state, which are integral aspects of modern security protocols.
Moreover, the TPM connector plays a crucial role in meeting compliance and regulatory requirements. In various industries and environments where data security and privacy regulations are stringent, the utilization of TPM modules via the TPM connector aids in demonstrating adherence to security standards. By implementing hardware-based security mechanisms, organizations can enhance their ability to protect sensitive information and align with industry-specific compliance mandates, thereby mitigating the risks associated with non-compliance and potential data breaches.
Overall, the TPM connector’s importance is underscored by its contribution to elevating the security posture of computer systems. By enabling the integration of TPM modules, it empowers users and organizations to establish robust security measures, fortify data protection capabilities, and align with regulatory standards, thereby fostering a more secure computing environment.
How to Identify the TPM Connector on Your Motherboard
Identifying the TPM connector on your motherboard is essential for integrating a TPM module and leveraging its security features. While the exact location and appearance of the TPM connector may vary depending on the motherboard model, there are several common methods to identify this crucial component.
- Consult the Motherboard Manual: The most reliable way to identify the TPM connector is by referring to the motherboard’s manual or documentation. Manufacturers typically provide detailed diagrams and descriptions of the motherboard’s components, including the location of the TPM connector. The manual may also outline specific instructions for connecting a TPM module to the designated connector on the motherboard.
- Visual Inspection: Inspect the motherboard visually to locate the TPM connector. It is often situated near the edge of the board, close to the I/O ports or expansion slots. The connector itself may be a 20- or 14-pin header with a specific label indicating its purpose. Some motherboards feature a dedicated silkscreen or marking near the connector, making it easier to identify amidst other components.
- Online Resources: In cases where the motherboard manual is unavailable, online resources can be valuable for identifying the TPM connector. Manufacturer websites, forums, and community-driven platforms often host discussions and resources related to motherboard specifications and component identification. By searching for the specific motherboard model, users may find detailed information and visual references to locate the TPM connector.
Additionally, it is important to note that some motherboards may not have a physical TPM connector, especially in consumer-grade models. In such instances, the motherboard may support a TPM module through alternative means, such as a TPM header that requires a separate adapter or an onboard TPM chip integrated directly into the motherboard’s circuitry. Understanding the specific TPM implementation for a given motherboard is crucial for determining how to enable and utilize TPM functionality.
By employing these methods, users can effectively identify the TPM connector on their motherboards, enabling them to proceed with the integration of a TPM module and harness the enhanced security capabilities it offers.
How to Connect a TPM Module to the TPM Connector
Connecting a TPM module to the TPM connector on a motherboard is a straightforward process that involves careful handling and precise alignment. By following the recommended steps, users can effectively integrate the TPM module, enabling the activation of hardware-based security features and enhancing the system’s overall protection against various threats.
- Locate the TPM Connector: Begin by identifying the TPM connector on the motherboard, referring to the motherboard manual or visual inspection to pinpoint the specific location of the connector.
- Prepare the TPM Module: Ensure that the TPM module is compatible with the motherboard and that it is designed to interface with the TPM connector. Verify the orientation of the module and inspect the connector pins to align with the corresponding header on the motherboard.
- Align and Connect: Carefully align the TPM module with the TPM connector, ensuring that the pin configuration matches the header on the motherboard. Apply gentle pressure to securely seat the module onto the connector, taking care to avoid bending or damaging the connector pins.
- Secure the Module: Once the TPM module is aligned and connected to the TPM connector, secure it in place according to the manufacturer’s recommendations. This may involve using screws or clips to fasten the module to the motherboard, providing additional stability and ensuring a reliable connection.
- Verify the Connection: After connecting the TPM module, verify the connection by inspecting the module’s alignment and ensuring that it is firmly seated on the TPM connector. Additionally, refer to the motherboard manual or BIOS settings to confirm that the TPM functionality has been recognized and activated.
It is important to exercise caution and precision when connecting a TPM module to the TPM connector, as improper handling or alignment may lead to connectivity issues or potential damage to the module or motherboard. By following the prescribed steps and heeding the manufacturer’s guidelines, users can successfully integrate the TPM module, paving the way for enhanced security features and strengthened protection against unauthorized access and security breaches.
Benefits of Using a TPM Module
Utilizing a Trusted Platform Module (TPM) module offers a myriad of benefits that contribute to bolstering the security and integrity of computer systems. By integrating a TPM module through the TPM connector on the motherboard, users can harness a range of advantages that enhance data protection, system integrity, and overall security posture.
- Enhanced Data Protection: One of the primary benefits of using a TPM module is the heightened level of data protection it affords. By leveraging hardware-based encryption and secure storage, the TPM module safeguards sensitive information, including cryptographic keys, passwords, and digital certificates, from unauthorized access and tampering. This is particularly valuable in scenarios where confidential data must be shielded from potential breaches and exploitation.
- Secure Boot Process: TPM modules play a pivotal role in enabling secure boot processes, which verify the integrity of the system’s firmware, bootloader, and operating system. By establishing a chain of trust through cryptographic measurements and signatures, the TPM module ensures that the system boots from trusted and unaltered components, mitigating the risks associated with boot-time attacks and malware infiltration.
- Trusted Computing Capabilities: TPM modules enable trusted computing functionalities, allowing the system to attest to its integrity and security posture. This capability facilitates secure remote attestation, where the system can provide cryptographic evidence of its configuration and state, bolstering trust in distributed computing environments and enhancing the ability to verify system integrity.
- Protection Against Malware and Unauthorized Access: TPM modules contribute to mitigating the risks posed by malware and unauthorized access attempts. Through features such as sealed storage and platform measurement, TPM-equipped systems can resist unauthorized modifications and unauthorized access attempts, fortifying the overall security resilience against a wide array of threats.
- Compliance with Security Standards: By utilizing TPM modules, organizations and users can align with security standards and regulatory requirements that mandate the implementation of robust security measures. The use of TPM modules aids in demonstrating adherence to industry-specific compliance mandates, enhancing the overall security posture and governance of the computing environment.
Overall, the benefits of using a TPM module extend to various facets of system security and data protection. By leveraging the capabilities afforded by TPM modules, users can establish a more resilient and secure computing environment, fortifying the integrity of critical data and mitigating the risks associated with unauthorized access and cyber threats.
Common FAQs about TPM Connectors on Motherboards
As the utilization of Trusted Platform Module (TPM) connectors becomes increasingly prevalent in modern computing environments, several common questions arise regarding their functionality, compatibility, and potential impact on system security. Addressing these frequently asked questions can provide valuable insights into the role of TPM connectors on motherboards and their implications for enhancing system security.
- What is the purpose of the TPM connector on a motherboard?
The TPM connector serves as a physical interface for connecting a TPM module to the motherboard. This facilitates the integration of hardware-based security features, such as secure data storage, cryptographic operations, and system integrity verification, which contribute to bolstering the overall security posture of the system. - How can I identify the TPM connector on my motherboard?
Identifying the TPM connector typically involves consulting the motherboard manual or documentation, visually inspecting the motherboard for a designated header, or referring to online resources and community forums for specific information related to the motherboard model. The connector is often located near the edge of the motherboard, close to the I/O ports or expansion slots. - Is a TPM module necessary for system security?
While not mandatory, a TPM module significantly enhances system security by providing hardware-based security functionalities. It offers benefits such as secure data storage, secure boot processes, and protection against unauthorized access, making it an invaluable component for fortifying the security posture of the system, especially in environments where data protection and integrity are paramount. - Can any motherboard support a TPM module through the TPM connector?
Not all motherboards are equipped with a TPM connector, especially in consumer-grade models. However, many modern business-oriented and enterprise-grade motherboards feature TPM connectors to enable the integration of TPM modules. It is essential to verify the motherboard’s specifications and compatibility with TPM modules before attempting to connect one. - What are the potential security benefits of using a TPM module via the TPM connector?
Integrating a TPM module through the TPM connector offers several security benefits, including enhanced data protection, secure boot processes, resistance against malware and unauthorized access, and compliance with security standards. The module contributes to fortifying the system’s security resilience and mitigating the risks associated with various forms of cyber threats.
By addressing these common FAQs about TPM connectors on motherboards, users and system administrators can gain a deeper understanding of the significance of TPM modules, their integration via TPM connectors, and the implications for bolstering system security and data protection.