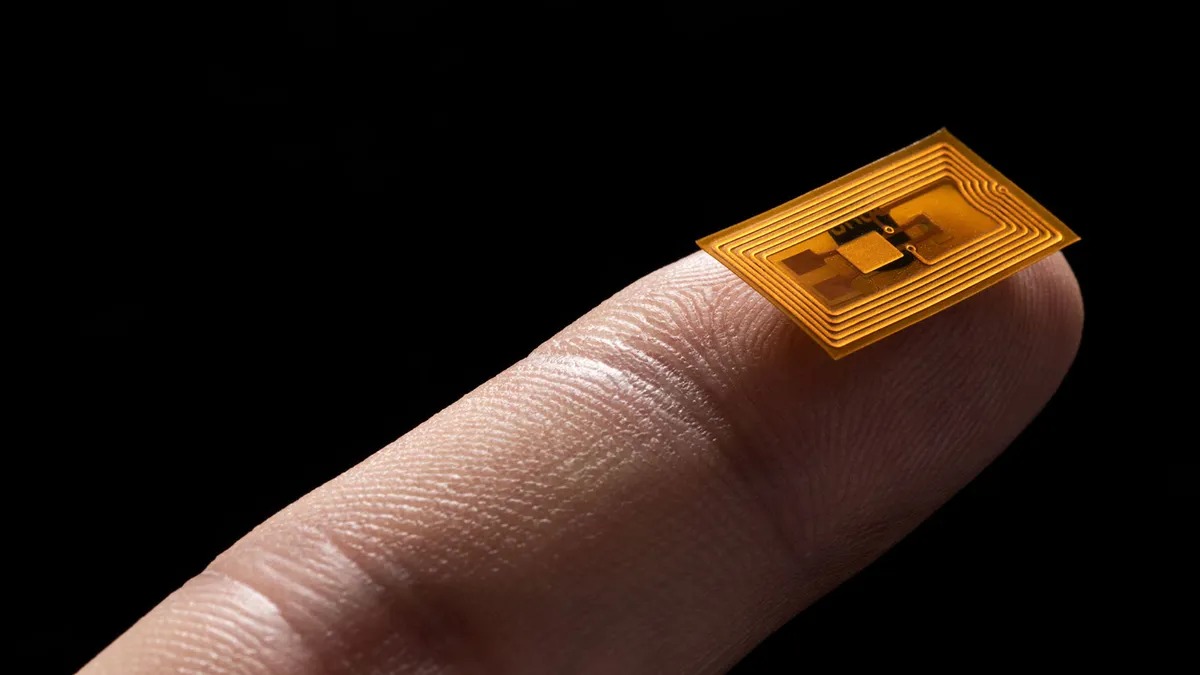
What is an NFC Tag?
NFC, or Near Field Communication, is a technology that allows for the wireless transfer of data between devices in close proximity. An NFC tag is a small, unpowered microchip that can be embedded in various items, such as stickers, key fobs, or cards. These tags can store and transmit information to NFC-enabled devices, making them versatile tools in a variety of applications.
NFC tags are equipped with a tiny antenna that enables them to communicate with NFC-enabled devices, such as smartphones, tablets, and other compatible gadgets. When an NFC-enabled device is placed near an NFC tag, the tag transmits its stored data to the device, initiating predefined actions or providing specific information.
These tags come in various forms, including passive and active. Passive NFC tags do not require a power source and rely on the energy transferred from the NFC-enabled device to function. In contrast, active NFC tags have their own power source and can initiate communication without relying on an external energy supply.
NFC tags can store a range of data, from simple text and URLs to more complex information, such as contact details, Wi-Fi configuration settings, and app launch instructions. This versatility makes NFC tags valuable in diverse settings, from marketing and advertising to access control and information sharing.
The compact size and flexibility of NFC tags make them ideal for embedding in products, promotional materials, and identification cards. They have become integral components in contactless payment systems, transportation passes, and smart packaging, enhancing convenience and efficiency in various industries.
Understanding the functions and capabilities of NFC tags is essential for harnessing their potential in different applications. As we delve deeper into the world of NFC technology, we will explore how NFC tags work, the various types available, their common uses, programming methods, and potential security concerns. This knowledge will empower individuals and businesses to leverage NFC technology effectively and securely.
How Does an NFC Tag Work?
NFC tags operate on the principles of electromagnetic induction and radio-frequency identification (RFID). When an NFC-enabled device, such as a smartphone, comes into close proximity to an NFC tag, the device’s built-in NFC reader generates a magnetic field, which in turn induces a current in the tag’s antenna. This current powers the NFC tag, enabling it to transmit data back to the NFC-enabled device.
Upon receiving power from the NFC-enabled device, the NFC tag sends out the data it stores using radio waves. These radio waves carry the tag’s information, which can include URLs, text, commands, or other types of data. The NFC-enabled device then interprets this data and can perform specific actions based on the information received from the tag.
One of the key features of NFC technology is its ability to facilitate quick and seamless communication between devices. Unlike Bluetooth or Wi-Fi, NFC does not require manual pairing or complex setup processes. Instead, the close proximity of the NFC-enabled device to the tag triggers the data exchange, making it a convenient and user-friendly technology.
Furthermore, NFC tags can be read and reprogrammed multiple times, allowing for flexibility in their use. This reusability makes NFC tags suitable for applications where dynamic or frequently updated information needs to be shared, such as in retail promotions, event management, and access control systems.
As NFC technology continues to evolve, newer iterations of NFC tags offer enhanced capabilities, such as increased storage capacity and improved data transfer speeds. These advancements open up opportunities for more sophisticated and data-rich applications, further expanding the potential uses of NFC tags in various industries.
Understanding the underlying mechanisms of how NFC tags function is crucial for maximizing their utility in diverse scenarios. By grasping the fundamental workings of NFC technology, individuals and businesses can harness its capabilities to streamline processes, enhance user experiences, and unlock innovative solutions across different domains.
Types of NFC Tags
NFC tags come in various types, each offering distinct features and capabilities tailored to specific applications. Understanding the different types of NFC tags is essential for selecting the most suitable option for a particular use case. The following are some of the common types of NFC tags:
- Passive NFC Tags: These tags do not require an internal power source and rely on the energy transferred from the NFC-enabled device to operate. They are cost-effective and widely used in applications such as product authentication, marketing, and access control.
- Active NFC Tags: In contrast to passive tags, active NFC tags have their own power source, typically a battery. This allows them to initiate communication with NFC-enabled devices without relying on external energy. Active tags are suitable for applications that require longer read ranges and more frequent data transmissions, such as asset tracking and smart sensor networks.
- Read/Write NFC Tags: These tags enable both reading and writing of data. They allow for dynamic data updates and reprogramming, making them suitable for applications where information needs to be modified or updated regularly, such as inventory management and interactive marketing campaigns.
- Read-Only NFC Tags: As the name suggests, these tags are pre-programmed with data during manufacturing and cannot be modified or rewritten. They are commonly used for applications where static information, such as product details or serial numbers, needs to be accessed but not altered, such as in supply chain management and authentication processes.
- High-Frequency NFC Tags: These tags operate at 13.56 MHz, the standard frequency for NFC technology. They are compatible with most NFC-enabled devices and are suitable for a wide range of applications, including contactless payment systems, access control, and smart packaging.
- Low-Frequency NFC Tags: Operating at frequencies below 135 kHz, low-frequency NFC tags are primarily used in proximity card applications, such as keyless entry systems and identification badges. While they offer limited data transfer rates compared to high-frequency tags, they are well-suited for specific access control and security applications.
By understanding the characteristics and functionalities of different types of NFC tags, businesses and individuals can make informed decisions when implementing NFC technology in their operations. Selecting the appropriate NFC tag type based on the specific requirements of a given application is crucial for optimizing performance and achieving desired outcomes.
Common Uses of NFC Tags
NFC tags find diverse applications across various industries, offering convenient and efficient solutions for a wide range of use cases. Some common uses of NFC tags include:
- Mobile Payments: NFC tags are integral to contactless payment systems, allowing users to make secure transactions by simply tapping their NFC-enabled smartphones or cards on payment terminals. This technology has revolutionized the way consumers make payments, offering speed and convenience at retail outlets, public transportation, and other point-of-sale locations.
- Marketing and Advertising: NFC tags are utilized in marketing campaigns to deliver interactive and personalized experiences to consumers. By tapping an NFC-enabled device on a tagged item, users can access promotional content, product details, and exclusive offers, enhancing engagement and driving brand awareness.
- Access Control and Security: NFC tags are employed in access control systems for secure entry to buildings, facilities, and events. They enable efficient authentication and authorization processes, providing a seamless and reliable method for granting access to authorized personnel.
- Smart Packaging and Product Authentication: NFC tags embedded in product packaging enable consumers to access product information, verify authenticity, and engage with brand-specific content. This enhances transparency in supply chains and empowers consumers to make informed purchasing decisions.
- Information Sharing and Connectivity: NFC tags facilitate seamless sharing of information, such as contact details, Wi-Fi network configurations, and location-based services. They streamline connectivity between devices, simplifying tasks such as pairing Bluetooth accessories and accessing digital content.
- Event Management and Ticketing: NFC tags are utilized in event management for ticketing, attendee registration, and access control. They offer a convenient and secure method for managing entry to venues and tracking attendee participation.
The versatility of NFC tags extends beyond these common uses, with applications in healthcare, logistics, education, and IoT (Internet of Things) ecosystems, among others. As NFC technology continues to evolve, new and innovative applications for NFC tags are constantly emerging, further expanding their utility in diverse domains.
Understanding the prevalent uses of NFC tags provides insights into the potential benefits and opportunities they offer in different contexts. By leveraging the capabilities of NFC tags, businesses and organizations can enhance customer experiences, streamline operations, and unlock new avenues for innovation and growth.
Programming an NFC Tag
Programming an NFC tag involves configuring the tag to store specific data or execute predefined actions when it interacts with an NFC-enabled device. This process enables individuals and businesses to customize the functionality of NFC tags to suit their requirements. Programming NFC tags typically involves the following steps:
- Choosing the Right NFC Tag: Selecting the appropriate type of NFC tag based on the intended application is the first step in programming. Factors such as memory capacity, reusability, and compatibility with target devices should be considered when choosing an NFC tag.
- Defining Data and Actions: Determine the type of data to be stored on the NFC tag, such as URLs, text, contact information, or commands. Additionally, specify the actions to be triggered when the tag is scanned, such as opening a website, launching an application, or configuring device settings.
- Using NFC Tag Programming Apps: There are various mobile applications available for programming NFC tags. These apps allow users to encode data onto the NFC tag and configure the desired actions. They provide user-friendly interfaces for defining the tag’s behavior and content.
- Encoding Data onto the NFC Tag: Once the data and actions are defined, the chosen NFC tag can be encoded with the desired information using an NFC-enabled smartphone or dedicated NFC writer. The encoding process typically involves tapping the NFC tag with the device and following the instructions provided by the programming app.
- Testing and Validation: After programming the NFC tag, it is essential to test its functionality to ensure that the programmed data and actions work as intended. This involves scanning the tag with an NFC-enabled device to verify that it triggers the expected responses.
It is important to note that the programming capabilities of NFC tags may vary based on the tag type and the features supported by the target devices. Some NFC tags allow for more complex programming, such as conditional logic and multiple data sets, while others may have limitations on the types of data that can be stored.
Understanding the programming process for NFC tags empowers users to leverage the full potential of these versatile tools. By customizing NFC tags to deliver specific content and functionalities, individuals and businesses can create tailored experiences for users, optimize processes, and enhance engagement across a wide range of applications.
Security Concerns with NFC Tags
While NFC technology offers numerous benefits, it also raises certain security considerations that need to be addressed to ensure the safe and reliable use of NFC tags. Some of the primary security concerns associated with NFC tags include:
- Data Privacy and Unauthorized Access: NFC tags can store sensitive information, such as personal data, payment credentials, and access privileges. Unauthorized access to this data can lead to privacy breaches and financial risks. Implementing robust encryption and access control measures is essential to safeguard the confidentiality of data stored on NFC tags.
- Counterfeit and Cloning: NFC tags used for product authentication and anti-counterfeiting purposes are susceptible to cloning and tampering. Malicious actors may attempt to replicate NFC tags or alter their contents to deceive consumers. Employing secure authentication mechanisms and tamper-evident features can mitigate the risks associated with counterfeit NFC tags.
- Malware and Phishing Attacks: NFC tags that trigger actions such as opening URLs or launching applications can be exploited to deliver malware or initiate phishing attacks. Users scanning malicious NFC tags may unknowingly expose their devices to security threats. Implementing measures to validate the integrity of NFC tag content and providing user prompts for actions initiated by scanned tags can mitigate the risk of malware and phishing attacks.
- Interference and Relay Attacks: NFC communication can be susceptible to relay attacks, where unauthorized devices intercept and relay communication between an NFC tag and a legitimate reader. This can lead to unauthorized transactions and unauthorized access. Employing secure protocols, distance limitations, and anti-interference measures can help mitigate the risk of relay attacks.
- Secure NFC Tag Initialization and Management: Ensuring the integrity of NFC tags during the manufacturing and provisioning stages is crucial to prevent unauthorized tampering and data manipulation. Secure initialization processes, unique tag identifiers, and cryptographic protections can enhance the trustworthiness of NFC tags from the point of origin.
Addressing these security concerns requires a multi-faceted approach that encompasses secure tag programming, robust encryption, tamper-resistant packaging, and user education on safe NFC tag interactions. Additionally, ongoing advancements in NFC security standards and technologies contribute to strengthening the overall security posture of NFC-based systems.
By proactively addressing security concerns and implementing best practices, organizations and users can leverage the benefits of NFC technology while mitigating potential risks. Embracing a security-first mindset in the deployment and utilization of NFC tags is essential for fostering trust, protecting user privacy, and ensuring the integrity of NFC-enabled applications.