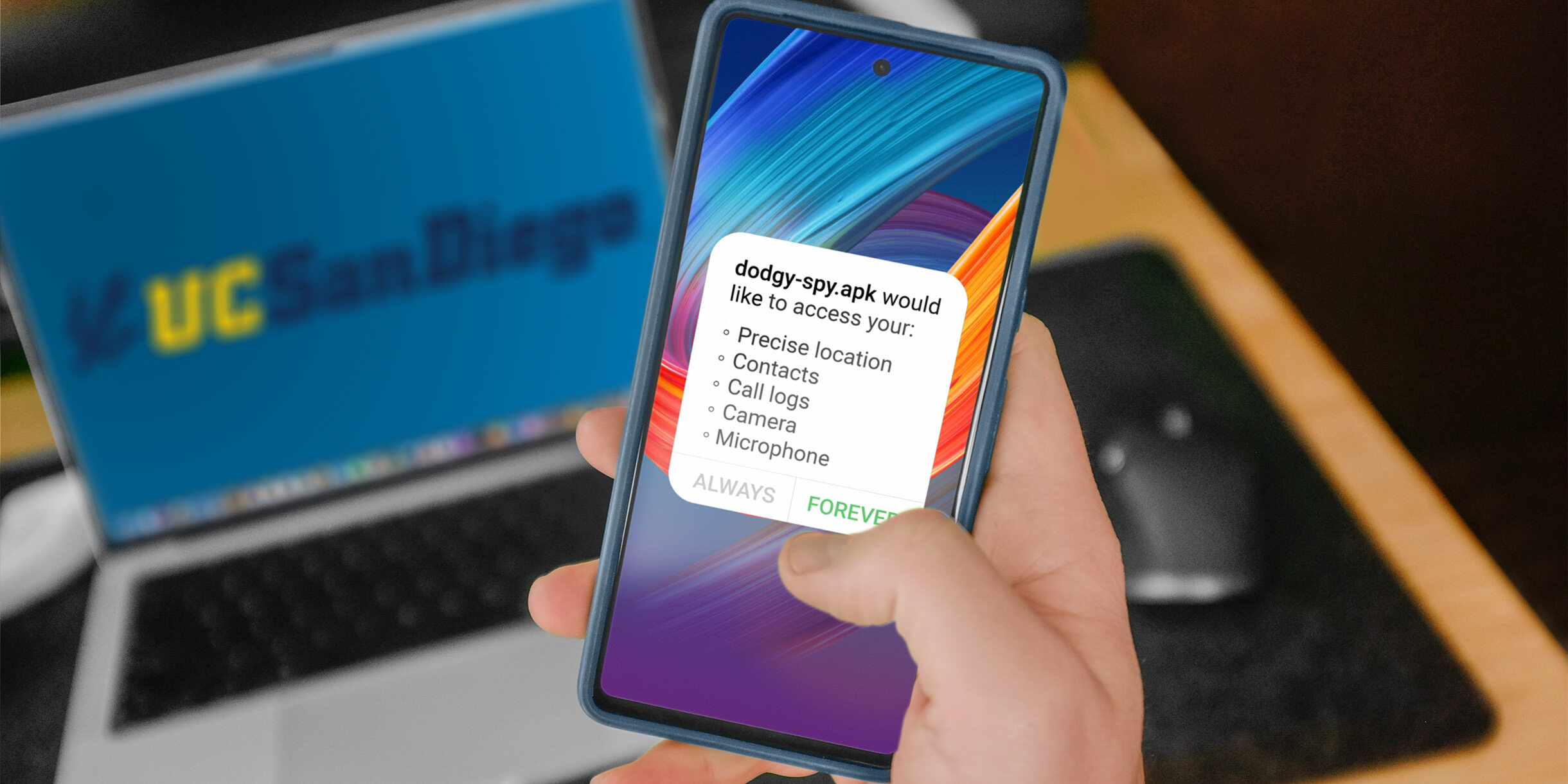
Keylogger Apps and Spyware
With the evolution of technology, smartphones have become an essential part of our lives. From communication and entertainment to banking and social media, we rely on our smartphones for various activities. However, this reliance comes with its own set of risks, especially when it comes to privacy and security. One of the most concerning threats is the use of keylogger apps and spyware.
Keylogger apps are malicious software that secretly record every keystroke you make on your smartphone. This means that every text message, password, and website you visit is captured and sent to the attacker. Spyware, on the other hand, is software that covertly monitors and collects information from your smartphone without your knowledge or consent. These malicious programs can be installed through deceptive links, malicious websites, or even hidden within seemingly innocent apps.
The danger of keylogger apps and spyware lies in their ability to capture sensitive information, such as login credentials, credit card details, and personal conversations. This information can then be used for various malicious purposes, including identity theft, financial fraud, and even blackmail.
Protecting yourself from keylogger apps and spyware requires a multi-layered approach. Firstly, it is crucial to only download apps from trusted sources, such as the official app stores. Be wary of downloading apps from third-party websites, as they may contain hidden malware. Additionally, regularly update your smartphone’s operating system and security patches to ensure you have the latest defenses against such threats.
Furthermore, it is essential to be cautious of suspicious links or attachments in emails, messages, or social media posts. Avoid clicking on unknown links and never download files from untrusted sources. Remember, even a single careless click can lead to the installation of keylogger apps or spyware on your device.
Lastly, consider using mobile security applications that offer real-time scanning and protection against keylogger apps and spyware. These apps can detect and remove malicious software from your smartphone, providing an additional layer of defense.
In today’s digital age, the prevalence of keylogger apps and spyware is a sobering reminder of the importance of protecting our privacy and security. By staying vigilant and implementing best practices for smartphone security, we can minimize the risk of falling victim to these intrusive tools.
Tracking and Monitoring Applications
In an era of advanced technology, tracking and monitoring applications have gained popularity among individuals and organizations alike. These apps offer the ability to monitor various activities on smartphones, such as location, messages, calls, and even social media interactions. While there may be legitimate uses for such applications, their misuse can pose serious threats to privacy and personal security.
One of the primary concerns with tracking and monitoring applications is the potential for abuse in personal relationships. Some individuals may install these apps on their partner’s smartphone without their knowledge, using them as tools for surveillance and control. This invasion of privacy can have severe emotional and psychological consequences for the targeted individual.
Similarly, employers may use tracking and monitoring applications to monitor their employees’ activities during work hours. While this can be justified as a means to enhance productivity and ensure compliance with company policies, it can also result in a hostile work environment and erode trust between employers and employees.
Beyond personal relationships and workplaces, there are also broader concerns regarding the security and ethics of these applications. The collected data is often stored on third-party servers, which raises questions about data protection and the potential for unauthorized access. Additionally, these apps can be susceptible to hacking and exploitation by cybercriminals, leading to the exposure of sensitive information.
To protect oneself from the potential dangers of tracking and monitoring applications, it is vital to remain cautious and informed. Regularly review the apps installed on your smartphone and carefully assess their permissions and access rights. Be mindful of any unusual behavior or battery drain, as these may be indications of a hidden monitoring app.
If you suspect that your smartphone is being monitored without your knowledge or consent, seek professional assistance to identify and remove any tracking and monitoring applications. It is important to approach the situation calmly and gather evidence if necessary, as the misuse of these apps may be illegal in some jurisdictions.
Furthermore, it is essential to have open and honest conversations about privacy expectations within personal relationships and workplace environments. Establish clear boundaries and respect each other’s privacy to foster healthy and trusting relationships.
While tracking and monitoring applications can have legitimate uses, their misuse can infringe upon personal privacy and security. By being aware of the risks they pose and taking proactive measures to protect ourselves, we can navigate the digital landscape with greater confidence and peace of mind.
Constant Communication and Location Sharing
In today’s interconnected world, smartphones have become our constant companions, allowing us to stay connected with others no matter where we are. While the ability to communicate and share our location instantly can be convenient, it also raises concerns about privacy and personal safety.
Constant communication through messaging apps, social media platforms, and voice calls means that our conversations and interactions are constantly being recorded, stored, and potentially analyzed by service providers. This collection of personal data raises questions about how it is being used and whether our privacy is being respected.
Location sharing, another common feature of smartphones, allows us to easily share our whereabouts with friends, family, and even the general public. While this can be useful for meeting up with friends or navigating unfamiliar places, it also has implications for privacy and personal safety.
Sharing our location through social media posts or messaging apps means that our movements can be tracked and potentially exploited by those with ill intentions. It is essential to be cautious about who we share our location with and to regularly review our privacy settings to ensure that only trusted individuals have access to this information.
Furthermore, location data collected by service providers can be shared with third parties for targeted advertising or even sold to data brokers. This raises concerns about the transparency of data usage and the potential for unauthorized access to personal information.
To protect ourselves from the potential risks associated with constant communication and location sharing, it is important to be mindful of our digital footprint. Regularly review the privacy settings on social media platforms and messaging apps to ensure that you are comfortable with the information being shared.
Additionally, be selective about who you share your location with and consider using privacy features that allow you to temporarily share your location for specific events or with trusted individuals only.
Lastly, be cautious of oversharing personal information and location data on social media. Pause and consider the potential implications before posting your whereabouts for the world to see. Remember, once information is out there, it can be challenging to regain control over how it is being used.
While smartphones have undoubtedly enhanced communication and convenience in our lives, constant communication and location sharing also present potential risks to our privacy and personal safety. By adopting a thoughtful approach to our digital interactions and staying informed about privacy settings, we can strike a balance between staying connected and protecting our personal information.
Espionage through Camera and Microphone
One of the most unsettling aspects of smartphone usage is the potential for espionage through the built-in camera and microphone. While these features provide convenience and functionality, they also raise concerns about privacy and the possibility of unauthorized access to our personal lives.
In recent years, there have been instances where malicious individuals or groups have gained access to smartphone camera and microphone functions, allowing them to remotely record audio and video without the user’s knowledge or consent. This kind of invasive surveillance can be used for various purposes, ranging from gathering sensitive information to infringing upon personal privacy.
The thought of being spied on through our own devices is alarming, but there are steps we can take to protect ourselves. First and foremost, it is essential to only install apps from trusted sources and to regularly update them. App permissions should be carefully reviewed, and access to the camera and microphone should only be granted when necessary.
Another precautionary measure is to cover the smartphone camera when not in use. This can be as simple as using a piece of tape or investing in a camera cover, which provides physical protection against unwanted surveillance. Additionally, disabling features such as voice activation and background microphone access in app settings can further safeguard against unauthorized audio recording.
It is crucial to stay vigilant and be aware of any signs that our smartphone camera or microphone may have been compromised. This includes observing whether the device is behaving unusually, such as unexpected battery drainage or the appearance of a blinking light when the camera or microphone is not in use. Suspicious activity should be reported to the appropriate authorities or a trusted IT professional.
While there are legitimate uses for smartphone cameras and microphones, such as capturing memories and facilitating communication, we must remain cautious about the potential for misuse. By taking proactive steps to protect our privacy and staying informed about the latest security measures, we can minimize the risk of falling victim to espionage through our devices.
Social Engineering Attacks and Phishing Scams
In the digital age, where personal information is frequently shared online, social engineering attacks and phishing scams have become increasingly prevalent. These malicious tactics aim to manipulate individuals into divulging sensitive information, such as passwords, financial details, or personal identification data.
Social engineering attacks often take advantage of human psychology to deceive victims. They can occur through various channels, such as emails, phone calls, or even direct messages on social media. Attackers may impersonate trusted individuals or organizations, creating a sense of urgency or fear to prompt the victim into taking immediate action.
Phishing scams, a common form of social engineering attack, involve sending fraudulent emails or creating fake websites that mimic reputable companies or institutions. These emails or websites often request users to provide personal information, such as usernames, passwords, or credit card details, under the guise of a legitimate reason.
Protecting oneself from social engineering attacks and phishing scams requires vigilance and cautious behavior. It is essential to be skeptical of unsolicited emails or messages, especially those requesting personal information or containing suspicious links or attachments.
One best practice is to verify the legitimacy of any communication received. This can be done by directly contacting the purported sender through a trusted channel, such as their official website or phone number, rather than replying to the suspicious message or email. Additionally, carefully examine URLs for any inconsistencies or slight variations that may indicate a fake website.
Furthermore, it is crucial to maintain strong security measures on smartphones, such as using secure and unique passwords, enabling two-factor authentication, and regularly updating software and applications. These measures help to mitigate the risk of falling victim to social engineering attacks and phishing scams.
Educating ourselves about common tactics used in social engineering attacks can also be beneficial. By staying informed about the latest techniques employed by hackers, we can recognize and avoid potential threats more effectively.
Risks of Public Wi-Fi
Public Wi-Fi networks have become ubiquitous in our modern society, offering convenient internet access in various locations such as coffee shops, airports, and hotels. While these networks provide convenience, they also pose significant risks to our privacy and security.
One of the primary concerns with public Wi-Fi is the lack of encryption. Unlike secure networks, public Wi-Fi networks often do not require passwords or encryption protocols, making it easier for cybercriminals to intercept and access data transmitted over the network. This means that any information you send or receive, such as login details, emails, or financial transactions, could potentially be intercepted by hackers.
Another threat arises from the presence of malicious actors on the same network. Cybercriminals can leverage public Wi-Fi to launch man-in-the-middle attacks, where they position themselves between your device and the websites or services you are accessing. These attackers can intercept your data, inject malicious code, or redirect you to fake websites designed to steal your information.
To protect yourself from the risks of public Wi-Fi, it is crucial to exercise caution and take preventive measures. First, consider avoiding sensitive activities on public networks, such as logging into sensitive accounts or making financial transactions. If you must engage in these activities, it is advisable to use a virtual private network (VPN) that encrypts your internet traffic and creates a secure connection between your device and the VPN server.
Additionally, ensure that your device’s firewall is enabled to provide an extra layer of protection against potential attacks. Keep your operating system and applications updated with the latest security patches, as software vulnerabilities can be exploited by hackers.
When using public Wi-Fi, be skeptical of unfamiliar networks and avoid connecting to networks with generic names, such as “Free Wi-Fi.” These networks could be set up by cybercriminals to lure unsuspecting users. Instead, choose networks provided by reputable establishments and verify the official network name with the staff if needed.
Lastly, consider using your smartphone’s mobile hotspot feature or a portable Wi-Fi hotspot device when you need to connect to the internet in public. By creating your own secure network, you can reduce the risks associated with using public Wi-Fi.
While public Wi-Fi networks offer convenience, it is crucial to be aware of the risks they pose. By employing precautionary measures and making informed choices about our online activities, we can better protect our privacy and security when using public Wi-Fi.
Inadequate Security Measures
In an increasingly interconnected world, smartphones have become a gateway to our personal and sensitive information. However, despite the growing awareness of the need for robust security measures, many smartphones still fall short when it comes to protecting our data.
One of the most significant concerns is the lack of strong authentication methods. Many smartphones still rely solely on traditional passcodes or simple PINs for unlocking the device, making them vulnerable to brute-force attacks and unauthorized access. Stronger authentication methods, such as biometric technologies like fingerprint or facial recognition, provide an additional layer of security and should be implemented whenever possible.
Inadequate encryption is another critical security shortcoming. Encryption helps protect the confidentiality of our data, but not all smartphones provide robust encryption by default. Some devices may use outdated encryption algorithms or may require users to manually enable encryption settings. This leaves our personal information vulnerable to being accessed or intercepted by malicious actors.
Furthermore, smartphones often come with pre-installed apps and bloatware that not only take up storage space but also introduce potential security risks. These apps may have vulnerabilities or contain malicious code that can compromise the security of the device. In some cases, these pre-installed apps cannot be uninstalled or updated, leaving users exposed to potential security breaches.
Regular software updates are essential for keeping smartphones secure. However, inadequate security measures can result in delayed or absent updates, leaving devices susceptible to known vulnerabilities. This puts users at risk of falling victim to cyberattacks that exploit these vulnerabilities to gain unauthorized access or steal sensitive information.
Manufacturers and software developers have a responsibility to prioritize security and provide timely updates to address potential risks. However, fragmented operating systems and the lack of standardized security protocols can hinder the seamless delivery of security patches and updates to all devices.
Users, on their part, can take steps to mitigate the risks posed by inadequate security measures. It is crucial to keep devices updated with the latest software versions and security patches. Regularly review and remove unnecessary apps, especially those that have known security vulnerabilities or questionable permissions.
To enhance security, consider using mobile security apps that offer features such as anti-malware scanning, app permissions monitoring, and safe browsing. These apps can provide an additional layer of defense against potential security breaches.
Cybercriminals Exploiting Vulnerabilities
The rapid advancement of technology has brought about numerous benefits and conveniences. However, it has also opened the door for cybercriminals to exploit vulnerabilities in smartphones, exposing users to various risks and threats.
One of the primary ways cybercriminals target smartphones is through software vulnerabilities. Operating systems, applications, and even hardware components may contain flaws that can be exploited by hackers to gain unauthorized access or control over the device. These vulnerabilities can range from weak encryption protocols to outdated software versions.
Once a vulnerability is identified, cybercriminals can develop and deploy malicious software, such as malware or ransomware, to exploit the weakness. Malware can infiltrate smartphones through various means, such as malicious websites, email attachments, or even fake apps. These malicious programs can gain control over the device, steal sensitive information, or disrupt its normal functioning.
Ransomware, on the other hand, can lock users out of their devices or encrypt their data, demanding a ransom payment in exchange for restoring access or decrypting the files. These attacks can cause significant financial losses, compromised personal information, and may even disrupt important work or personal activities.
Another technique employed by cybercriminals is social engineering. By manipulating individuals through psychological tactics and deceptive techniques, cybercriminals can trick users into revealing personal information or downloading malicious content. Phishing scams, fake websites, and email scams are common social engineering techniques used to deceive users and gain access to their smartphones.
Moreover, cybercriminals target smartphone users by exploiting the allure of third-party app stores or unauthorized app downloads. These apps may contain malicious code, offering hackers a backdoor into the device. Additionally, counterfeit or compromised versions of legitimate apps can also be used to gain access to sensitive information.
To protect oneself from cybercriminals exploiting vulnerabilities, it is essential to prioritize the security of smartphones. Regularly update the operating system, applications, and security patches to ensure that known vulnerabilities are addressed. Be cautious when downloading apps and only use trusted sources such as official app stores.
Invest in a reliable mobile security solution that provides real-time protection against malware and keeps a lookout for potential threats. This can help detect and mitigate any malicious activities before they can cause harm.
Furthermore, practicing good digital hygiene is crucial. Be wary of suspicious emails, messages, or links, and avoid clicking on unknown or unverified sources. Educate yourself about common phishing tactics and stay informed on the latest cybersecurity threats to minimize the risk of falling victim to cybercriminals.
As technology continues to evolve, cybercriminals will likely continue to exploit vulnerabilities in smartphones. By staying vigilant, adopting preventive measures, and keeping security a priority, we can mitigate the risks and protect ourselves from falling victim to these malicious activities.
Government Surveillance and Mass Data Collection
In an age of increased connectivity, concerns about government surveillance and mass data collection have become significant topics of discussion. With smartphones being an integral part of our lives, these devices have become a potential gateway for governments to access and collect vast amounts of personal information.
Government surveillance involves the monitoring and collection of data on individuals, often with the aim of maintaining national security or combating criminal activities. However, the extent and methods of this surveillance can raise concerns about infringements on privacy and civil liberties.
One issue is the collection of metadata, which includes information about who we communicate with, when, and for how long, rather than the actual content of the communication. This metadata can be used to create a detailed profile of individuals, their relationships, and their activities, allowing governments to track and analyze patterns of behavior.
Mass data collection refers to the collection and storage of vast amounts of information, often without individuals’ knowledge or consent. This can include everything from internet browsing history and social media activity to location data and financial transactions.
The storage and analysis of such data raise concerns about its potential misuse or unauthorized access. There have been cases where government agencies or contractors have been implicated in the inappropriate or unauthorized use of personal data, leading to breaches of privacy and damage to individuals’ reputations.
Furthermore, the transparency and accountability surrounding government surveillance programs and data collection practices have come under scrutiny. Many argue that there should be clearer legal frameworks, judicial oversight, and greater public awareness and debate about the balance between security and privacy.
To protect oneself from government surveillance and mass data collection, individuals can take several steps. Using encryption tools, such as secure messaging apps or virtual private networks (VPNs), can help safeguard the privacy of communications and protect sensitive data from being intercepted.
Being aware of privacy settings and permissions on smartphones is essential. Reviewing and adjusting app permissions to limit what data is shared with third parties can help minimize the amount of personal information available for government surveillance or mass data collection.
Supporting advocacy groups and organizations that promote privacy rights and work to improve transparency and accountability can also make a difference. By supporting initiatives that advocate for stronger privacy laws and government transparency, individuals can contribute to the ongoing dialogue and efforts to strike the right balance between privacy and security.
It is essential to stay informed about legal frameworks and regulations regarding government surveillance and data collection. Familiarize yourself with your rights and understand the limitations and safeguards in place to protect privacy.
Government surveillance and mass data collection are complex and evolving topics. Striking the right balance between security and privacy requires ongoing dialogue, legislation, and public awareness. By staying informed and taking steps to protect our privacy, we can help ensure that our rights and liberties are respected in an increasingly connected world.
The Dark Side of Apps and Permissions
In the digital age, smartphone apps have become an integral part of our daily lives. From social media and productivity tools to entertainment and shopping, apps offer convenience and functionality. However, the proliferation of apps has brought forth concerns about privacy and the potential misuse of personal information.
One of the primary issues is the extensive permissions that apps require to access various aspects of our smartphones, such as contacts, location, photos, and microphone. While some permissions are necessary for app functionality, others may be excessive or unrelated to the app’s purpose. This raises concerns about the misuse or unauthorized access to personal data.
Apps collect and store a significant amount of data about users, often using it for targeted advertising or sharing it with third-party entities. This data collection can include sensitive information such as location, browsing history, and even biometric data. The potential for this data to be misused, exploited, or even breached by hackers is a significant privacy concern.
Additionally, apps may employ deceptive practices that manipulate users into granting excessive permissions. This can include providing misleading information about the need for certain permissions or making permissions a prerequisite for using the app, even when they are unnecessary for its core functionality.
Another issue arises when apps request access to personal contacts or the ability to send messages on behalf of the user. These permissions can lead to unsolicited contact with friends and family or even the spreading of malware through social engineering tactics.
To protect oneself from the potential risks associated with apps and permissions, it is important to be mindful when granting permissions to apps. Before installing an app, carefully review the requested permissions and consider if they are necessary for the app’s intended purpose. If the permissions seem excessive or unrelated, consider alternative apps that require fewer permissions.
Regularly review the permissions granted to installed apps and revoke any that are no longer necessary or that you are uncomfortable with. Many smartphones offer granular control over app permissions, allowing users to manage each app’s access to specific features or data.
Be cautious when downloading apps from third-party sources or untrusted app stores, as these apps may have more lenient security measures or be more likely to contain malicious code. Stick to official app stores that have rigorous security checks and maintain a reputation for vetting apps.
Education is also crucial. Stay informed about the privacy policies of app developers and understand how your data is collected, used, and shared. Being aware of common deceptive practices and staying informed about privacy best practices can help you make informed decisions when it comes to apps and permissions.
The dark side of apps and permissions highlights the need for vigilance and user empowerment in managing privacy and personal data. By being cautious, informed, and proactive in managing app permissions, users can mitigate the risks and protect their privacy in the digital landscape.
Personal Information Leaked by Companies
In an era where personal information is increasingly valuable, the leaking of personal data by companies has become a significant concern for individuals. Despite the implementation of various data protection measures, data breaches and leaks continue to occur, putting sensitive information at risk.
Companies collect and store vast amounts of personal data, including names, addresses, email addresses, phone numbers, and even financial information. This information is often gathered for legitimate purposes, such as providing services or targeted advertising. However, when companies fail to adequately protect this data, it can be compromised and accessed by unauthorized individuals.
Data breaches can occur due to various factors. Weak cybersecurity practices, misconfigured systems, or even insider threats can lead to personal information being exposed. Additionally, the increasing sophistication of cybercriminals and the constant evolution of hacking techniques pose ongoing challenges for companies’ security measures.
The consequences of personal information leaks can be severe. Individuals may fall victim to identity theft, financial fraud, or even harassment. Personal information can be sold on the dark web, leading to a loss of privacy and potential consequences that can affect individuals for years to come.
Companies have a responsibility to protect the personal data they collect. This includes implementing robust security measures, regularly updating software, and conducting thorough risk assessments to identify vulnerabilities. Encrypted storage and transmission of data can also add an extra layer of protection.
Transparency and clear communication are essential in maintaining the trust of customers. Companies should provide clear privacy policies and keep individuals informed about how their data is being collected, used, and shared. Promptly notifying customers in the event of a data breach is crucial to help individuals take necessary steps to protect themselves.
From an individual standpoint, being cautious and proactive is vital in mitigating the risks associated with personal information leaks. Regularly monitor financial accounts and credit reports for any irregularities or unauthorized activity. Use strong, unique passwords for online accounts and consider using a password manager to securely generate and store passwords.
Limit the sharing of personal information online and be skeptical of unsolicited requests for personal information. Verify the legitimacy of websites and applications before providing sensitive data and consider using privacy-enhancing tools, such as virtual private networks (VPNs) or browser extensions that block tracking.
Individuals should also consider staying up-to-date on news and updates about data breaches and security practices. By staying informed, they can take appropriate action and protect themselves from potential risks.
The leaking of personal information by companies is a serious concern, and both companies and individuals have crucial roles to play in safeguarding this data. By adopting stringent security practices and taking proactive steps to protect personal information, we can collectively work towards a safer and more secure digital landscape.
Protecting Yourself from Smartphone Spying
In today’s digital world, where smartphones have become an extension of our personal and professional lives, the need to protect ourselves from smartphone spying has never been greater. Whether it’s malicious individuals, hackers, or even government surveillance, taking steps to safeguard our privacy is crucial.
First and foremost, secure your smartphone with a strong passcode, pattern, or biometric authentication, such as fingerprints or facial recognition. This ensures that unauthorized individuals cannot access your device without your explicit permission.
Regularly update your smartphone’s operating system and applications to enhance security. Companies frequently release updates that address vulnerabilities and strengthen security measures, so staying up to date is vital in protecting against potential spying threats.
Be cautious when downloading apps. Stick to reputable sources, such as official app stores, and carefully review app permissions before installation. If an app requests unnecessary access to your personal information or device features, consider alternative apps or contact the app developer for clarification.
Consider using a trusted mobile security app that provides real-time scanning for malware and other security threats. These apps can help detect and remove malicious software that could be used for spying or unauthorized access to your smartphone.
Check your smartphone’s app settings and permissions regularly. Review the permissions granted to installed apps and revoke any that are no longer necessary or that you are uncomfortable with. Be mindful of apps that request access to your location, camera, microphone, or contacts, and only grant those permissions to trusted and essential apps.
Be vigilant when connecting to public Wi-Fi networks. Public networks are often unsecured, leaving your smartphone vulnerable to potential spying attempts. Avoid accessing sensitive information or transmitting personal data on public Wi-Fi networks. Consider using a virtual private network (VPN) to encrypt your internet traffic and protect your privacy.
Avoid clicking on suspicious links or downloading files from unknown sources, as they may contain malware or spyware. Be cautious of phishing attempts through text messages, emails, or social media. Remember, legitimate organizations will never ask for your personal information or login credentials via unsolicited messages.
Regularly monitor your smartphone for any signs of unusual behavior, such as sudden battery drain, unexpected data usage, or new apps appearing without your knowledge. These could be indicators of malware or spyware on your device.
Lastly, be mindful of your physical surroundings. Avoid leaving your smartphone unattended in public places and be cautious of people or devices that could attempt to gain access to your smartphone without your knowledge.
Protecting yourself from smartphone spying requires a combination of proactive measures and ongoing vigilance. By implementing these strategies and staying informed about the latest threats and security practices, you can strengthen your privacy and ensure that your smartphone remains a secure tool in your daily life.