Understanding NFC and RFID Technology
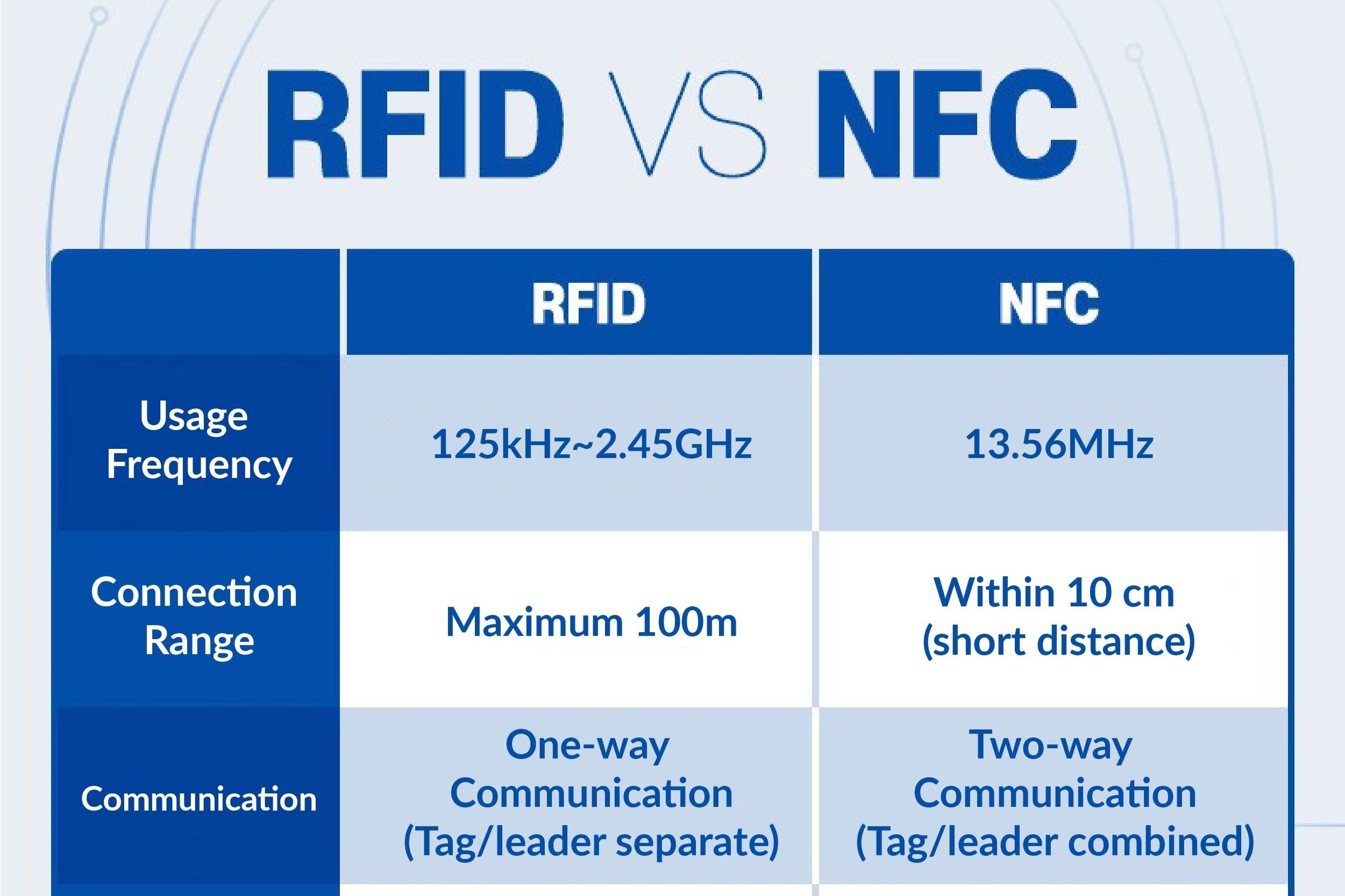
Near Field Communication (NFC) and Radio-Frequency Identification (RFID) are two closely related technologies that have revolutionized the way we interact with everyday objects. Both NFC and RFID utilize radio waves to communicate data between devices, but they differ in their range and functionality.
NFC operates within a short range, typically up to 4 centimeters, and is commonly used for contactless payment systems, access control, and data exchange between devices. It enables secure and convenient transactions with a simple tap or wave, making it a popular choice for mobile payment solutions and access cards.
RFID, on the other hand, can operate over longer distances, ranging from a few centimeters to several meters, depending on the frequency used. This technology is widely employed in inventory management, supply chain tracking, and asset identification. RFID tags can be passive, drawing power from the RFID reader, or active, with an onboard power source, allowing for diverse applications across industries.
Both NFC and RFID technologies rely on electromagnetic fields to transfer data, with NFC being a subset of RFID that operates at a shorter range. They are integral to the Internet of Things (IoT) ecosystem, enabling seamless connectivity and data exchange between physical objects and digital systems. Understanding the capabilities and limitations of NFC and RFID is crucial for harnessing their potential in various domains, from retail and logistics to healthcare and smart infrastructure.
Types of NFC and RFID Cards
NFC and RFID technology encompass a variety of cards designed for specific applications, each offering unique features and capabilities. Understanding the different types of NFC and RFID cards is essential for selecting the most suitable solution for a particular use case.
1. NFC Cards:
- Standard NFC Cards: These cards comply with NFC Forum standards and are widely used for contactless payments, access control, and public transportation systems. They are compatible with NFC-enabled smartphones and tablets, facilitating seamless interactions.
- NFC Tags: These are small, passive NFC devices that can store and transmit information to NFC-enabled devices. They are commonly used for smart posters, product authentication, and location-based services.
- NFC-enabled Smart Cards: These cards integrate NFC technology with traditional smart card functionality, offering enhanced security and versatility for applications such as identification, ticketing, and loyalty programs.
2. RFID Cards:
- Passive RFID Cards: These cards do not have an internal power source and rely on the electromagnetic field generated by an RFID reader to transmit data. They are widely used for inventory management, access control, and asset tracking due to their cost-effectiveness and durability.
- Active RFID Cards: Equipped with a battery or power source, active RFID cards have extended read ranges and are suitable for real-time location tracking, vehicle identification, and high-value asset monitoring.
- UHF RFID Cards: Operating in the ultra-high frequency range, these cards offer long read ranges and high data transfer speeds, making them ideal for logistics, retail, and supply chain applications.
Understanding the characteristics and capabilities of each type of NFC and RFID card is crucial for deploying efficient and secure solutions across diverse industries and use cases. Whether it’s enabling seamless mobile payments, enhancing inventory visibility, or streamlining access control, the right choice of NFC and RFID cards can significantly impact operational efficiency and user experience.
Identifying NFC and RFID Cards
Identifying NFC and RFID cards is essential for verifying their authenticity, understanding their capabilities, and ensuring compatibility with specific systems or applications. Several methods can be employed to identify these cards, ranging from visual inspection to advanced diagnostic tools.
1. Visual Inspection:
One of the simplest ways to identify NFC and RFID cards is through visual examination. NFC cards often feature the NFC logo, indicating their compatibility with NFC-enabled devices. RFID cards may display the frequency band at which they operate, such as low-frequency (LF), high-frequency (HF), or ultra-high frequency (UHF), providing initial insights into their functionality.
2. Smartphone Apps:
For NFC cards, smartphone apps equipped with NFC reading capabilities can be used to identify and read the data stored on the cards. These apps enable users to access information embedded in NFC tags, such as URLs, contact details, or product specifications, empowering them to interact with NFC-enabled objects seamlessly.
3. RFID Readers:
RFID readers, available in various form factors and frequency ranges, are indispensable for identifying RFID cards. By using an RFID reader, the unique identifier (UID) and additional data stored on the RFID cards can be retrieved, allowing for precise identification and integration into RFID-enabled systems.
4. Diagnostic Tools:
Advanced diagnostic tools, including NFC and RFID analyzers, provide comprehensive insights into the technical parameters and performance characteristics of NFC and RFID cards. These tools can assess signal strength, data transfer rates, and protocol compatibility, assisting in troubleshooting and optimizing the functionality of the cards.
5. Manufacturer Documentation:
Manufacturer documentation and specifications offer valuable information for identifying NFC and RFID cards, including their supported standards, data storage capacities, and encryption protocols. By referring to the documentation provided by card manufacturers, users can gain a deeper understanding of the cards’ capabilities and technical specifications.
Identifying NFC and RFID cards through a combination of visual inspection, technological tools, and manufacturer resources is crucial for leveraging their potential in diverse applications, from secure access control and contactless payments to IoT deployments and asset tracking. By employing the appropriate identification methods, users can harness the full capabilities of NFC and RFID cards while ensuring seamless interoperability and security.
Tools for Identifying NFC and RFID Cards
Identifying NFC and RFID cards requires the use of specialized tools and technologies tailored to the unique characteristics of these contactless communication devices. From portable handheld devices to software applications, a range of tools is available to facilitate the precise identification and analysis of NFC and RFID cards.
1. NFC-Enabled Smartphones:
Many modern smartphones are equipped with NFC capabilities, allowing them to read and interact with NFC tags and cards. By utilizing NFC-enabled smartphones, users can easily identify NFC cards, access embedded information, and verify their functionality through dedicated NFC reading apps available on app marketplaces.
2. RFID Readers and Scanners:
RFID readers and scanners are essential tools for identifying and interrogating RFID cards across different frequency bands, including low-frequency (LF), high-frequency (HF), and ultra-high frequency (UHF). These devices provide real-time access to the unique identifiers and data stored on RFID cards, enabling seamless integration into RFID-enabled systems and applications.
3. NFC Diagnostic Apps:
Specialized diagnostic apps designed for NFC technology offer comprehensive features for identifying and analyzing NFC cards. These apps can read NFC card data, assess signal strength, verify compatibility with NFC standards, and provide insights into the technical parameters of NFC-enabled objects, making them valuable tools for NFC card identification and troubleshooting.
4. RFID Analyzers:
Advanced RFID analyzers are instrumental in identifying and evaluating RFID cards, offering in-depth analysis of signal strength, modulation schemes, and protocol compatibility. These analyzers enable users to assess the performance characteristics of RFID cards, diagnose communication issues, and optimize the configuration of RFID systems for seamless card identification and data exchange.
5. Manufacturer-Specific Tools:
Some NFC and RFID card manufacturers provide proprietary tools and software applications tailored for identifying and configuring their products. These manufacturer-specific tools offer specialized functionalities for card identification, data retrieval, and performance optimization, ensuring seamless integration and interoperability within the manufacturer’s ecosystem.
By leveraging a combination of NFC-enabled smartphones, RFID readers, diagnostic apps, analyzers, and manufacturer-specific tools, users can effectively identify, analyze, and optimize the performance of NFC and RFID cards across a wide range of applications. These tools play a critical role in ensuring the seamless operation and interoperability of NFC and RFID technology in diverse environments, from retail and logistics to access control and IoT deployments.
Testing NFC and RFID Cards
Thorough testing of NFC and RFID cards is essential to validate their functionality, interoperability, and security features across various use cases. By employing rigorous testing procedures, organizations and users can ensure the reliability and performance of these contactless communication devices in real-world scenarios.
1. Functionality Testing:
Functionality testing involves verifying the core operations of NFC and RFID cards, including data transmission, authentication, and response to reader commands. This testing phase ensures that the cards perform as intended, enabling seamless communication with compatible devices and systems.
2. Compatibility Testing:
Testing NFC and RFID cards for compatibility with a diverse range of readers, smartphones, and access control systems is crucial for ensuring interoperability. Compatibility testing validates the cards’ ability to function across different platforms and environments, minimizing integration challenges and enhancing user experience.
3. Security Testing:
Security testing assesses the resilience of NFC and RFID cards against unauthorized access, data interception, and cloning attempts. By subjecting the cards to security testing, organizations can identify potential vulnerabilities and implement robust encryption and authentication measures to safeguard sensitive information.
4. Performance Testing:
Performance testing evaluates the speed, range, and reliability of NFC and RFID cards under varying environmental conditions and usage scenarios. This testing phase provides insights into the cards’ read range, data transfer rates, and resilience to interference, ensuring consistent performance in real-world deployments.
5. Durability Testing:
For RFID cards used in harsh or demanding environments, durability testing is crucial to assess their resistance to physical stress, temperature extremes, and environmental factors. Durability testing validates the cards’ longevity and reliability, especially in applications such as asset tracking and industrial automation.
6. Interoperability Testing:
Interoperability testing focuses on validating the seamless interaction between NFC and RFID cards and a wide array of devices, readers, and systems. This testing phase ensures that the cards conform to industry standards and protocols, enabling smooth integration and communication within complex IoT ecosystems.
By conducting comprehensive functionality, compatibility, security, performance, durability, and interoperability testing, organizations and users can confidently deploy NFC and RFID cards in diverse applications, ranging from access control and payment systems to inventory management and smart infrastructure. Thorough testing mitigates risks, enhances user trust, and maximizes the potential of NFC and RFID technology in the digital era.
Common Uses of NFC and RFID Cards
NFC and RFID cards are versatile tools that find widespread application across various industries and everyday scenarios, offering seamless interaction, secure authentication, and efficient data exchange. The following are common uses of NFC and RFID cards, showcasing their diverse utility and impact:
1. Access Control and Security:
NFC and RFID cards are extensively used for access control systems in corporate environments, educational institutions, and residential complexes. These cards enable secure entry and exit, employee identification, and visitor management, enhancing overall security and operational efficiency.
2. Contactless Payments:
NFC cards are integral to contactless payment solutions, allowing consumers to make swift and secure transactions at retail outlets, public transport systems, and entertainment venues. With a simple tap or wave, NFC cards facilitate convenient and hygienic payment experiences.
3. Transportation and Ticketing:
NFC and RFID cards are employed for public transportation access and ticketing, enabling commuters to seamlessly board buses, trains, and subways while reducing queuing times and enhancing the overall transit experience.
4. Inventory Management:
RFID cards play a pivotal role in inventory management and supply chain optimization, providing real-time visibility into the movement and status of products, assets, and components. RFID-enabled inventory systems streamline operations and minimize stock discrepancies.
5. Asset Tracking and Identification:
RFID cards are utilized for tracking and identifying assets in diverse industries, including healthcare, manufacturing, and logistics. By affixing RFID tags to equipment, tools, and high-value items, organizations can monitor their location and usage, mitigating loss and optimizing resource allocation.
6. Loyalty Programs and Marketing:
NFC-enabled smart cards are leveraged for loyalty programs and interactive marketing initiatives, allowing businesses to engage customers with personalized offers, digital content, and loyalty rewards through NFC-enabled interactions.
7. Smart Home and IoT Applications:
NFC and RFID cards contribute to smart home automation and IoT deployments, enabling users to control connected devices, share data, and configure settings with a simple tap or swipe, enhancing convenience and connectivity.
8. Healthcare and Patient Identification:
RFID cards are utilized for patient identification, medication administration, and medical asset tracking in healthcare facilities, ensuring accurate patient care and efficient management of medical resources.
By embracing the diverse applications of NFC and RFID cards, organizations and individuals can streamline operations, enhance security, and deliver seamless user experiences across retail, healthcare, transportation, and IoT ecosystems. The versatility and reliability of NFC and RFID technology continue to drive innovation and efficiency in the digital era.
Security Concerns with NFC and RFID Cards
While NFC and RFID cards offer unparalleled convenience and efficiency, they also raise important security considerations that must be addressed to safeguard sensitive data and prevent unauthorized access. Understanding and mitigating these security concerns is crucial for fostering trust and reliability in the deployment of NFC and RFID technology.
1. Unauthorized Access and Cloning:
One of the primary security concerns with NFC and RFID cards is the risk of unauthorized access and cloning. Without robust encryption and authentication measures, malicious actors may intercept card data or clone cards, leading to unauthorized entry, data theft, and fraudulent transactions.
2. Data Privacy and Protection:
The storage and transmission of personal or confidential data on NFC and RFID cards raise concerns regarding data privacy and protection. Inadequate security measures may expose sensitive information to unauthorized entities, compromising individual privacy and regulatory compliance.
3. Relay Attacks and Skimming:
NFC and RFID cards are susceptible to relay attacks and skimming, where attackers intercept communication between a card and a reader, potentially leading to unauthorized transactions or unauthorized access. Implementing countermeasures against relay attacks is essential to mitigate this risk.
4. Physical Tampering and Damage:
Physical tampering and damage to NFC and RFID cards can compromise their functionality and security. Cards that are easily tampered with or damaged may lead to operational disruptions, unauthorized modifications, or data loss.
5. Lack of Standardized Security Protocols:
The absence of standardized security protocols across all NFC and RFID card implementations poses a challenge for ensuring consistent and robust security measures. Variations in security standards and implementations may create vulnerabilities that can be exploited by attackers.
6. Over-the-Air (OTA) Attacks:
OTA attacks targeting NFC and RFID cards leverage vulnerabilities in wireless communication protocols to compromise the integrity and confidentiality of card data. Mitigating OTA attacks requires comprehensive security measures at the protocol and application layers.
Addressing these security concerns necessitates the implementation of robust encryption, authentication mechanisms, and access control policies to protect NFC and RFID cards from unauthorized access and malicious exploitation. Additionally, ongoing security assessments, threat modeling, and compliance with industry standards are critical for ensuring the resilience and trustworthiness of NFC and RFID technology in diverse applications.
By proactively addressing security concerns and adopting best practices for secure deployment and usage, organizations and individuals can harness the transformative potential of NFC and RFID cards while maintaining a steadfast commitment to data protection and privacy.