What are NFC Tags?
NFC (Near Field Communication) tags are small, programmable chips that can store and transmit information to NFC-enabled devices when they come into close proximity. These tags are commonly used in various applications, including contactless payments, access control, and data transfer between devices. NFC tags can be embedded in products, posters, business cards, and other items to enable quick and convenient interactions with compatible devices.
NFC tags come in different forms, such as stickers, key fobs, and cards, and they can be programmed to perform specific actions when activated by an NFC-enabled device. For example, a business card with an embedded NFC tag can be programmed to share contact information, a Wi-Fi network, or a website link when tapped by a smartphone. Similarly, an NFC tag on a poster can trigger actions like opening a website, downloading an app, or connecting to a social media page.
These tags rely on electromagnetic induction to communicate with devices, allowing for seamless and secure data exchange without the need for physical contact. The technology has gained popularity due to its ease of use, versatility, and compatibility with a wide range of devices, making it an integral part of the growing Internet of Things (IoT) ecosystem.
NFC tags operate within a short range, typically within a few centimeters, which ensures that interactions are intentional and controlled. This close proximity requirement enhances the security of NFC-based transactions and interactions, as it reduces the risk of unauthorized access or interception.
Overall, NFC tags serve as convenient and versatile tools for enabling quick and effortless interactions between physical objects and digital devices, enhancing user experiences and streamlining various processes in both personal and professional settings.
Why is it Important to Wipe NFC Tags Clean?
Ensuring that NFC tags are properly wiped clean is crucial for safeguarding sensitive information, maintaining privacy, and preventing unauthorized access to stored data. When NFC tags are not properly erased, there is a risk of exposing personal or confidential information to unintended recipients, potentially leading to privacy breaches and security vulnerabilities.
One of the primary reasons to wipe NFC tags clean is to protect personal data. These tags are often used to store contact details, payment information, or access credentials, and failing to erase them before discarding or repurposing the associated items could result in the unintentional disclosure of sensitive information. By wiping NFC tags clean, individuals can mitigate the risk of identity theft, unauthorized transactions, or unauthorized access to restricted areas or systems.
Another important consideration is the protection of business-related data. NFC tags are commonly used for marketing, access control, inventory management, and other business applications. Failing to wipe these tags clean before reusing or disposing of them could lead to the inadvertent disclosure of proprietary information, trade secrets, or customer data. This could potentially damage a company’s reputation, violate privacy regulations, and compromise competitive advantages.
Furthermore, wiping NFC tags clean is essential for maintaining the integrity of automated processes and interactions. When tags are not properly erased, there is a risk of unintended actions being triggered when the tags come into contact with NFC-enabled devices. This could lead to confusion, errors, or unintended consequences, impacting user experiences and undermining the reliability of NFC-based applications.
From a security standpoint, ensuring that NFC tags are wiped clean helps prevent unauthorized access and misuse. For instance, if an NFC tag containing access credentials or sensitive commands is not properly erased, it could potentially be exploited by malicious actors to gain unauthorized entry, manipulate systems, or cause disruptions.
Methods for Wiping NFC Tags
When it comes to wiping NFC tags clean, several methods can be employed to ensure that the stored data is securely erased. These methods cater to different user preferences, technical capabilities, and available resources, offering flexibility and convenience in managing NFC tag content.
- Using an NFC-Enabled Device: Many modern smartphones and tablets are equipped with NFC capabilities, allowing users to interact with NFC tags directly. To wipe an NFC tag using a mobile device, users can simply navigate to the device’s settings or use a dedicated NFC management app to access the tag’s contents and initiate the erasure process. This method is convenient for individuals who frequently encounter NFC tags in their daily activities and prefer a straightforward approach to managing tag data.
- Using an NFC Tag Writer: NFC tag writers are specialized devices that enable users to read, write, and erase data on NFC tags. By connecting an NFC tag writer to a compatible device, users can utilize dedicated software or apps to interact with the tags and perform data erasure operations. This method is suitable for individuals who require more advanced tag management capabilities and prefer a dedicated tool for handling NFC tag content.
- Using an App to Erase NFC Tags: Various mobile apps are available for both Android and iOS platforms, offering NFC tag management features, including data erasure. These apps provide intuitive interfaces for scanning, viewing, and erasing NFC tag contents, catering to users who prefer the convenience of managing tags through their smartphones. Additionally, some apps offer additional features such as tag cloning, data encryption, and tag customization, expanding the utility of NFC tags in various scenarios.
Each of these methods offers a viable approach to wiping NFC tags clean, allowing users to choose the most suitable option based on their preferences, device compatibility, and specific requirements. Whether it’s leveraging the built-in NFC capabilities of a smartphone, utilizing a dedicated tag writer, or utilizing feature-rich mobile apps, the goal remains consistent: to ensure that NFC tag data is securely and reliably erased when needed.
Using an NFC-Enabled Device
Utilizing an NFC-enabled device to wipe NFC tags clean offers a convenient and accessible method for managing tag content. With the widespread integration of NFC technology in modern smartphones and tablets, users can leverage the built-in NFC functionality to interact with and erase data from NFC tags seamlessly.
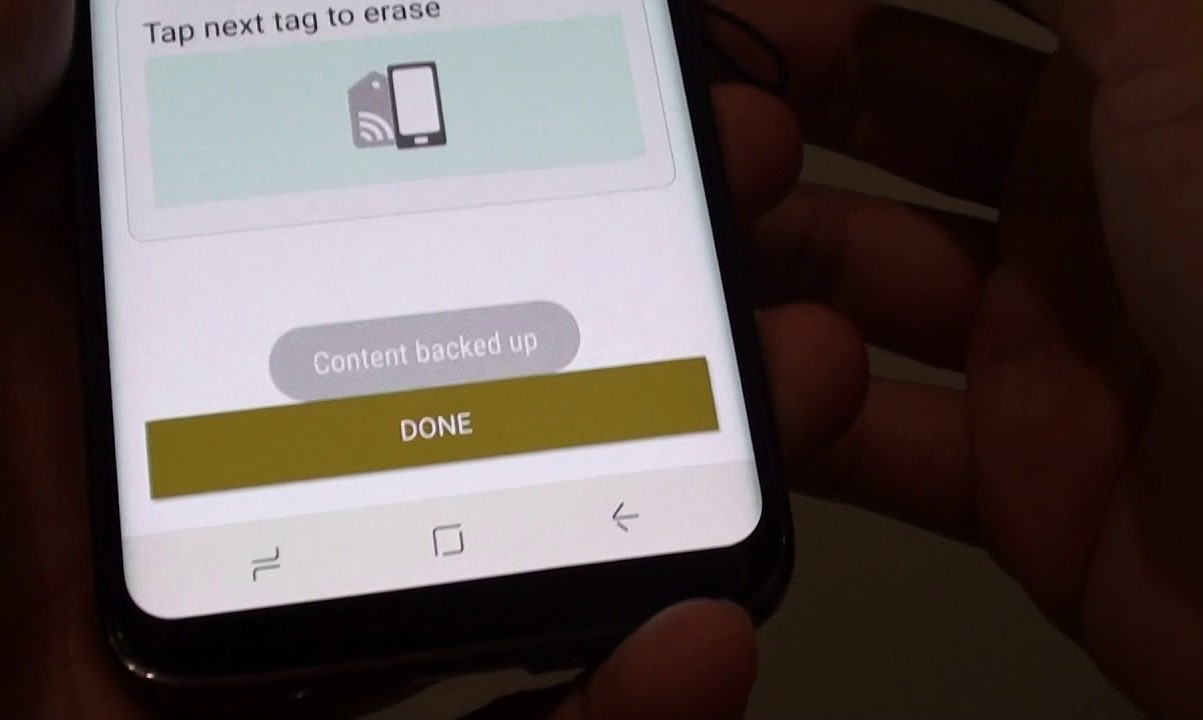
To begin the process of wiping an NFC tag using a mobile device, users can access the device’s settings or download a compatible NFC management app from the app store. Once the appropriate interface is accessed, users can initiate the tag erasure process by placing the NFC-enabled device in close proximity to the tag, allowing the device to establish a connection and access the tag’s contents.
Upon successfully detecting the NFC tag, users can navigate through the device’s interface to view the tag’s stored data and initiate the erasure operation. This typically involves selecting the specific tag to be wiped and confirming the action, ensuring that the data is securely and permanently removed from the tag’s memory. The process is designed to be user-friendly, requiring minimal technical expertise and providing clear prompts to guide users through the erasure procedure.
Furthermore, using an NFC-enabled device to wipe NFC tags clean offers the advantage of portability and accessibility. Since most individuals carry their smartphones with them throughout the day, they can quickly respond to the need to erase NFC tags encountered in various contexts, such as in the workplace, at events, or during personal interactions. This flexibility empowers users to proactively manage tag content and maintain data security without relying on external devices or specialized equipment.
Additionally, the seamless integration of NFC tag management features into mobile devices enhances the user experience, aligning with the trend of leveraging smartphones for diverse tasks and interactions. By harnessing the capabilities of NFC-enabled devices, users can streamline the process of erasing NFC tags, ensuring that sensitive information is promptly and effectively removed when necessary.
In essence, leveraging an NFC-enabled device to wipe NFC tags clean reflects the evolution of mobile technology, empowering users to manage NFC tag content with ease and efficiency. This method exemplifies the seamless integration of NFC capabilities into everyday devices, offering a user-friendly approach to maintaining data privacy and security in the context of NFC interactions.
Using an NFC Tag Writer
Employing an NFC tag writer provides a specialized and versatile approach to managing NFC tags, offering users advanced capabilities for reading, writing, and erasing tag data. NFC tag writers are dedicated devices designed to interact with NFC tags, enabling users to perform a wide range of operations, including the secure erasure of tag contents.
Using an NFC tag writer typically involves connecting the device to a compatible smartphone, tablet, or computer, allowing users to access dedicated software or apps that facilitate tag management. Through the intuitive interface provided by the tag writer’s software, users can identify and select the specific NFC tag to be erased, initiating the erasure process with precision and control.
One of the key advantages of utilizing an NFC tag writer for erasing tags is the enhanced functionality and flexibility it offers. These devices often provide comprehensive features for managing tag data, such as the ability to create, edit, and erase multiple types of NFC tags, including various formats and data structures. This level of versatility caters to users with diverse needs, whether they are managing NFC tags for personal use, business applications, or specialized projects.
Furthermore, NFC tag writers empower users with the ability to perform detailed data management tasks, ensuring that tag contents are securely erased without compromising the integrity of the tags themselves. The dedicated software or apps associated with NFC tag writers often offer advanced options for verifying the successful erasure of data, providing users with confidence in the thoroughness and reliability of the erasure process.
Another notable benefit of using an NFC tag writer is the potential for heightened security and control over tag management. These devices are designed to offer robust authentication and encryption features, safeguarding sensitive data and preventing unauthorized access to tag contents. By incorporating advanced security measures, NFC tag writers enable users to maintain the confidentiality and integrity of stored information, addressing the evolving needs of data privacy and protection.
Using an App to Erase NFC Tags
Utilizing a dedicated mobile app to erase NFC tags presents a convenient and user-friendly method for managing tag content directly from a smartphone or tablet. With the availability of NFC tag management apps on both Android and iOS platforms, users can leverage these applications to interact with NFC tags, view their contents, and initiate secure erasure operations with ease.
When using an app to erase NFC tags, users can begin by downloading a compatible NFC tag management app from the respective app store. Once installed, the app provides an intuitive interface for scanning and identifying nearby NFC tags, enabling users to access the stored data and perform erasure operations as needed. This streamlined process eliminates the need for additional hardware or complex setup, offering a convenient solution for individuals seeking a portable and accessible method for managing NFC tags.
Furthermore, NFC tag management apps often offer additional features beyond basic tag erasure, enhancing the utility and versatility of the mobile platform for interacting with NFC tags. Users may have the option to customize tag settings, clone existing tags, or encrypt tag data, expanding the scope of potential applications for NFC tags in various contexts. This flexibility empowers users to tailor their NFC tag management experience to suit specific requirements and preferences.
Another advantage of using an app to erase NFC tags is the seamless integration with the mobile device’s native functionalities and user interface, ensuring a cohesive and familiar experience for users. By leveraging the capabilities of smartphones and tablets, NFC tag management apps align with the trend of optimizing mobile devices for diverse tasks, empowering users to manage tag content on the go without relying on external devices or specialized equipment.
Moreover, the accessibility and user-friendly nature of NFC tag management apps contribute to a more inclusive and widespread adoption of NFC technology. By offering a simplified and intuitive method for interacting with NFC tags, these apps cater to a broad user base, including individuals, businesses, and organizations seeking practical solutions for managing NFC tag content in various scenarios.
In essence, using an app to erase NFC tags exemplifies the seamless integration of NFC tag management into the mobile ecosystem, providing users with a versatile and portable solution for maintaining data privacy and security. This approach reflects the evolving landscape of mobile technology, empowering users to leverage the inherent capabilities of their devices to interact with and manage NFC tags effectively.
Best Practices for Wiping NFC Tags Clean
When it comes to ensuring the secure and effective erasure of NFC tags, adhering to best practices is essential to maintain data privacy, security, and integrity. By following established guidelines and recommendations, users can mitigate the risk of unintentional data exposure and uphold the reliability of NFC tag interactions.
- Verify Erasure: After initiating the erasure process for an NFC tag, it is advisable to verify that the data has been successfully removed. This can be done by attempting to read the tag with an NFC-enabled device to confirm that no residual information is accessible. Verifying erasure helps ensure that sensitive data is thoroughly eliminated and that the tag is ready for reuse or disposal.
- Use Trusted Tools and Apps: When engaging in NFC tag management, it is important to utilize trusted and reputable tag writers, apps, and devices for erasing tag data. By relying on established tools and applications with a track record of reliability and security, users can minimize the risk of data breaches, unauthorized access, or technical issues that could compromise the erasure process.
- Backup Critical Data: Prior to erasing NFC tags that contain important or irreplaceable information, it is advisable to create backups of the data to prevent accidental loss. By maintaining duplicate copies of critical data, users can safeguard against potential errors during the erasure process and preserve valuable information for future use or reference.
- Understand Data Retention Policies: In scenarios where NFC tags are used for business or organizational purposes, it is essential to be aware of data retention policies and regulatory requirements. By understanding the guidelines governing the storage and erasure of specific types of data, users can ensure compliance with industry standards and legal obligations when managing NFC tag content.
- Securely Dispose of Unused Tags: When NFC tags are no longer needed or are scheduled for replacement, it is important to securely dispose of or repurpose the tags. This may involve physically damaging the tags to render them unreadable or utilizing specialized procedures for data destruction, particularly when dealing with sensitive or confidential information.
- Maintain Tag Inventory and Documentation: For organizations and businesses utilizing NFC tags in various applications, maintaining an inventory of deployed tags and documenting their lifecycle, including erasure and disposal processes, is crucial. This practice ensures accountability, traceability, and compliance with data management protocols, contributing to efficient tag governance and risk mitigation.
By embracing these best practices, individuals and organizations can uphold the security and reliability of NFC tag interactions while effectively managing tag content in alignment with privacy, compliance, and operational requirements.