The Discovery of Stuxnet
In 2010, a cybersecurity firm stumbled upon a mysterious computer worm that would shake the world with its implications. This worm was later identified as Stuxnet, a highly sophisticated malware that targeted industrial control systems, specifically those used in nuclear facilities.
Stuxnet’s discovery was not a random occurrence – it was the result of meticulous research and analysis by cybersecurity professionals. They noticed an anomaly in the operation of certain systems and began investigating, leading them to the worm’s unprecedented complexity and scale.
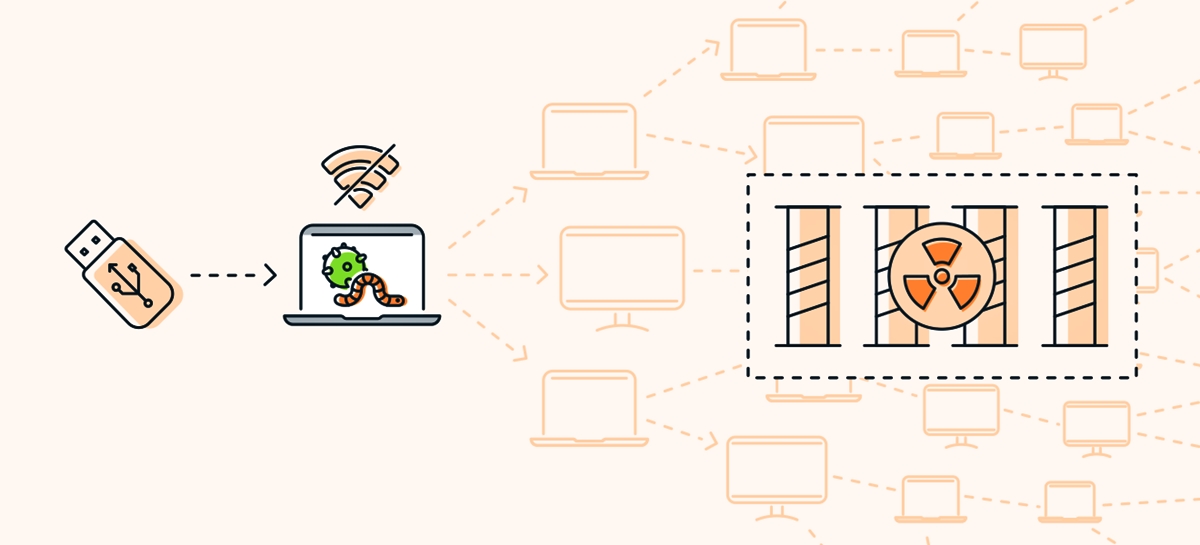
What made Stuxnet particularly remarkable was its level of stealth and intelligence. It was designed to infiltrate computers running the Windows operating system, spreading through removable drives and exploiting previously unknown vulnerabilities. Once inside a target system, it would remain dormant for a period of time, evading detection and analysis.
Stuxnet’s stealth capabilities were further enhanced by its ability to digitally sign itself using legitimate security certificates, making it appear as a trusted application. This allowed the malware to bypass many security measures undetected.
As cybersecurity experts dissected Stuxnet further, they discovered an extensive array of advanced techniques utilized by the malware. It employed rootkit-like features to hide itself from the system and manipulated the Programmable Logic Controllers (PLCs) responsible for controlling various industrial processes.
Stuxnet’s complexity and sophistication perplexed the cybersecurity community, leading many to speculate on its origin and purpose. It quickly became clear that this was no ordinary malware but a targeted cyberweapon with a specific objective in mind.
The discovery of Stuxnet was a wake-up call for governments, organizations, and individuals alike, highlighting the evolving threat landscape and the need for robust cybersecurity measures. It marked a significant turning point in the world of cybersecurity, bringing to light the potential devastation that a well-crafted and covert cyberweapon could wreak.
Stuxnet’s Target: Iran’s Nuclear Program
Upon closer inspection, it became apparent that Stuxnet was specifically designed to target Iran’s nuclear program. The malware’s primary aim was to disrupt and sabotage the country’s uranium enrichment efforts, a critical component of developing nuclear weapons.
Iran’s nuclear program had long been a source of concern for the international community, with suspicions of it being used for covert military purposes. Stuxnet’s emergence shed light on an unprecedented covert attack specifically tailored to hinder Iran’s nuclear ambitions.
Stuxnet’s code indicated a deep understanding of the Industrial Control Systems (ICS) used in Iran’s nuclear facilities, particularly the Natanz uranium enrichment plant. It exploited vulnerabilities in the Siemens supervisory control and data acquisition (SCADA) systems, which were widely used in these facilities.
Stuxnet ingeniously targeted the centrifuge equipment utilized in the uranium enrichment process. By tampering with the speed of the centrifuges, it caused physical damage and disrupted the delicate balance required for effective uranium enrichment. This highly precise and subtle attack method indicated a level of knowledge and expertise not typically found in cybercriminal operations.
While exact details of Stuxnet’s impact on Iran’s nuclear program remained classified, reports suggest that it dealt a significant blow. Thousands of centrifuges were reportedly destroyed or rendered inoperable, disrupting Iran’s uranium enrichment capabilities and causing substantial setbacks.
The ability of the malware to carry out such specific and sophisticated attacks highlighted the growing convergence between cyber warfare and traditional military tactics. Stuxnet demonstrated that cyberspace could be a viable battleground for nation-states to inflict physical damage on critical infrastructure, providing a new dimension to modern warfare.
Stuxnet’s targeted attack on Iran’s nuclear program also raised concerns about the potential for other countries to follow suit. The incident served as a deterrent for nations pursuing illicit nuclear activities, as it showcased the vulnerability of their facilities and the potential consequences of such actions.
The revelation of Stuxnet’s target and its impact on Iran’s nuclear program further emphasized the need for enhanced cybersecurity in critical infrastructure sectors worldwide. It spotlighted the significance of protecting vital systems from potential cyber attacks with robust defense mechanisms and proactive measures.
Dissecting Stuxnet: How it Works
Understanding the intricacies of Stuxnet is crucial in grasping its remarkable sophistication and the extent of its capabilities. The malware employed a multi-stage attack process that involved various techniques to evade detection, propagate through networks, and compromise target systems.
Stuxnet primarily targeted Windows computers, leveraging zero-day exploits to exploit vulnerabilities in the operating system. It utilized a combination of traditional propagation methods, such as exploiting network shares and removable drives, alongside more advanced techniques, including the use of stolen digital certificates for signing its modules.
Once infected, Stuxnet employed a rootkit to mask its presence on the system, making it challenging to detect. It also employed a mechanism called “dis-assembly” to rewrite parts of the target system’s code, allowing it to manipulate and control specific processes without raising suspicion.
A key aspect of Stuxnet was its ability to identify and target specific industrial control systems, specifically those associated with uranium enrichment. By intercepting and manipulating communications between the PLCs and the supervisory systems, Stuxnet had the capability to alter the operations of the plant without being noticed.
Stuxnet’s attack on the centrifuges involved altering their rotational speeds, causing excessive vibrations and ultimately leading to physical damage. To achieve this, the malware employed precise timing and monitoring mechanisms, ensuring that the sabotage remained undetectable by operators or any traditional monitoring systems.
To maintain stealth and persistence, Stuxnet utilized a “man in the middle” approach. It intercepted and modified the data exchanged between the PLCs and the controlling computers, while simultaneously providing false feedback to the supervisory systems to mask its malicious activities.
Stuxnet’s complexity and sophistication made it extremely difficult to reverse engineer and analyze. Its modular structure allowed for updates and additional functionality to be delivered remotely, making it an evolving threat that could adapt to changing circumstances.
The dissection of Stuxnet revealed an unprecedented level of sophistication and precision in a malware designed to target specific industrial infrastructure. It showcased the convergence of cyber and physical attacks, highlighting the potential for severe consequences when the digital realm intersects with the physical world.
By understanding how Stuxnet worked, security experts were able to develop countermeasures and improve cybersecurity defenses to protect against similar targeted attacks in the future. This case served as a catalyst for enhancing the resiliency of critical infrastructure systems and signaling the importance of proactive cybersecurity measures.
A Covert Weapon: Stuxnet as a Cyberweapon
Stuxnet’s discovery and analysis revealed a new era in cyber warfare, where malware could function as a covert weapon capable of inflicting physical damage on critical infrastructure systems. The level of sophistication and precision exhibited by Stuxnet made it clear that cyber weapons had entered the realm of nation-state capabilities.
Stuxnet demonstrated that a cyberattack did not have to be limited to stealing information or causing disruption in the virtual realm. It could now directly impact physical assets and compromise the integrity of industrial processes, creating potential havoc in critical sectors such as energy, transportation, and manufacturing.
One of the most significant aspects of Stuxnet as a cyber weapon was its ability to remain undetected for an extended period. It employed advanced evasion techniques, exploiting multiple vulnerabilities to bypass security measures and hide its malicious intent. This covert aspect of Stuxnet highlighted the potential for cyber weapons to be used for strategic and asymmetric warfare, where an attacker could cause significant damage without being easily traced.
The complexity and level of expertise required to create Stuxnet indicated that it was likely developed by a nation-state or a well-funded organization. Its deployment also suggested the involvement of an intelligence agency with an in-depth knowledge of Iran’s nuclear program. This realization raised concerns about the potential for other state-sponsored cyber weapons and their potential targets.
Stuxnet marked a turning point in the world of cybersecurity and international relations. It served as a stark reminder that traditional geopolitical tensions could spill over into cyberspace, where the consequences of a well-executed cyberattack could have significant geopolitical implications.
The emergence of Stuxnet as a cyberweapon also accelerated the global arms race in cyber capabilities. Nations worldwide began investing in the development and enhancement of their own cyber arsenals, aiming to defend against potential attacks and maintain an offensive edge.
The use of Stuxnet as a covert weapon demonstrated the need for international discussions and agreements on cyber warfare. The incident highlighted the challenges of attributing cyber attacks to specific actors and the potential for unintended escalation of conflicts in the digital realm.
Stuxnet was a wake-up call for nations, organizations, and individuals to prioritize cybersecurity, not only for protection but also as a critical element of national security. It underscored the importance of robust defense mechanisms, intelligence sharing, and international collaboration to counter the evolving threat landscape in cyberspace.
Sabotaging Uranium Enrichment: Stuxnet’s Primary Function
Stuxnet’s primary objective was to sabotage Iran’s uranium enrichment efforts by targeting the centrifuges used in the process. This targeted focus made it one of the most sophisticated and precise cyber weapons ever discovered.
Uranium enrichment is a crucial step in the development of nuclear weapons. Stuxnet specifically targeted the centrifuges responsible for this process, aiming to disrupt the delicate balance required for effective enrichment. By tampering with the speed and operation of the centrifuges, it caused physical damage and hindered Iran’s nuclear ambitions.
Stuxnet’s attack on the centrifuges was a multi-stage process that required a deep understanding of the industrial control systems used in Iran’s nuclear facilities. The malware exploited vulnerabilities in the Siemens SCADA systems, which were extensively used in these facilities, to gain access and control over the centrifuges.
Once inside the system, Stuxnet monitored the operations of the centrifuges and manipulated their rotational speeds. By subtly altering the speed, it was able to introduce excessive vibrations, putting a strain on the delicate machinery. This resulted in the destruction of centrifuges or rendering them inoperable, disrupting Iran’s uranium enrichment capabilities.
What made Stuxnet’s sabotage of the centrifuges particularly remarkable was its ability to do so without raising suspicion. The malware incorporated feedback mechanisms to provide false readings to the supervisory systems, making it appear as if everything was functioning normally. This level of precision and stealth ensured that the tampering went undetected for an extended period.
While the exact extent of the damage caused by Stuxnet remains classified, reports suggest that it dealt a severe blow to Iran’s nuclear program. Thousands of centrifuges were reportedly destroyed or affected, leading to significant setbacks in Iran’s pursuit of nuclear weapons.
The successful deployment of Stuxnet’s sabotage techniques raised concerns globally about the potential for cyber weapons to target critical infrastructure. It spotlighted the vulnerabilities of industrial control systems and the potential consequences of a well-executed cyberattack on such facilities.
The significance of Stuxnet’s ability to sabotage uranium enrichment went beyond its impact on Iran’s nuclear program. It demonstrated how cyber weapons could directly and definitively impact a nation’s pursuit of weapons of mass destruction, blurring the lines between traditional military strategies and covert cyber operations.
The success of Stuxnet in sabotaging uranium enrichment facilities served as a powerful example of the potential for cyber weapons to disrupt critical infrastructure. It highlighted the need for enhanced cybersecurity measures in the face of evolving threats, especially in sectors involving sensitive technologies and national security interests.
Stuxnet’s Impact on Iran’s Nuclear Program
The discovery and deployment of Stuxnet had a significant impact on Iran’s nuclear program, causing substantial setbacks and disruptions. While the exact extent of the damage remains classified, it is widely believed that Stuxnet dealt a severe blow to Iran’s uranium enrichment capabilities.
Stuxnet’s targeted attack on the centrifuges used in uranium enrichment led to the destruction or disabling of thousands of these crucial pieces of equipment. By tampering with their rotational speeds and causing excessive vibrations, the malware rendered the centrifuges inoperable or caused physical damage, disrupting the delicate enrichment process.
This extensive damage resulted in significant setbacks for Iran’s nuclear program. Reports suggest that the malware successfully delayed Iran’s progress in enriching uranium to the levels required for the development of nuclear weapons.
The impact of Stuxnet on Iran’s nuclear program extended beyond the physical damage caused to the centrifuges. It also resulted in financial setbacks and delays, as the country had to invest time and resources in repairing and replacing the affected equipment.
Moreover, Stuxnet served as a wake-up call for Iran, highlighting the vulnerabilities of its nuclear infrastructure to cyber attacks. The incident prompted the country to acknowledge and prioritize cybersecurity concerns, leading to the development of indigenous capabilities in this field.
Stuxnet also had broader geopolitical implications. It raised international concerns about Iran’s nuclear ambitions and the potential for cyber weapons to be used as a means of delaying or disrupting such programs. This led to increased scrutiny and diplomatic pressure on Iran’s nuclear activities.
The success of Stuxnet in targeting Iran’s nuclear program sparked a global debate on the use of cyber weapons as a means of affecting geopolitical dynamics. It highlighted the potential for cyber attacks to impact critical infrastructure and create significant disruptions in national security efforts.
In response to Stuxnet, Iran has taken steps to enhance its cybersecurity and develop stronger defenses against potential cyber attacks. The incident served as a catalyst for Iran to invest in indigenous cybersecurity capabilities and enhance its resilience in the face of future threats.
The impact of Stuxnet on Iran’s nuclear program underscored the complex relationship between cyber operations, national security, and international politics. It raised questions about the rules of engagement in cyberspace and the potential for covert cyber operations to shape global power dynamics.
Overall, Stuxnet left an indelible mark on Iran’s nuclear program, causing significant disruptions and delays. It highlighted the vulnerability of critical infrastructure to cyber attacks and the potential for cyber weapons to impact geopolitical dynamics.
A State-Sponsored Attack: Assumptions and Attribution
The discovery of Stuxnet sparked intense speculation about its origin and the entity behind its development. The complexity and sophistication displayed by the malware pointed towards the involvement of a nation-state or a well-funded organization with significant resources and expertise.
While no official attribution has been formally announced, there have been widespread assumptions regarding the source of Stuxnet. Many experts believe that the United States and Israel collaborated in the development and deployment of the malware, targeting Iran’s nuclear program as a covert operation.
Several factors contributed to these assumptions. First, Stuxnet specifically targeted Iran’s nuclear facilities, indicating a strategic objective aligned with the national security interests of countries concerned about Iran’s nuclear ambitions. This targeting suggested the involvement of a state actor with a vested interest in disrupting Iran’s nuclear program.
The level of technical sophistication displayed by Stuxnet also pointed towards the involvement of a nation-state. The malware’s advanced propagation techniques, evasion mechanisms, and precise targeting of industrial control systems indicated access to significant resources and a deep understanding of cybersecurity and nuclear technology.
Furthermore, leaked reports and testimonials from individuals involved in the operation have provided hints regarding the involvement of the US and Israel. While these reports do not provide definitive proof, they have fueled the belief that Stuxnet was indeed a joint effort by these two nations.
Attributing cyber attacks to specific actors is notoriously challenging, as attackers can obfuscate their origins and employ misleading tactics to divert suspicion. The nature of cyberspace allows for plausible deniability, making it difficult to definitively attribute attacks to particular individuals or governments.
Nonetheless, the assumptions surrounding Stuxnet’s origin and the involvement of a state-sponsored operation have had significant implications. The incident has sparked both condemnation and admiration, with some viewing it as a groundbreaking example of strategic cyber warfare and others raising concerns about the escalation of cyber conflicts.
The presumed involvement of nation-states in the development and deployment of Stuxnet has contributed to the ongoing international dialogue surrounding cyber warfare and the need for norms and regulations in this domain. It has prompted discussions on international law, ethical considerations, and the potential consequences of clandestine cyber operations.
Regardless of the specific attribution, the emergence of Stuxnet highlighted the increasing prevalence of state-sponsored cyber attacks and their potential impact on global security. It underscored the need for robust cybersecurity measures and international cooperation to mitigate the risks posed by advanced cyber threats.
Stuxnet’s Legacy: Impact on Cybersecurity and International Relations
The emergence of Stuxnet had far-reaching implications for both cybersecurity and international relations, leaving a lasting legacy that continues to shape the global landscape in these areas.
From a cybersecurity perspective, Stuxnet served as a wake-up call for governments, organizations, and individuals, highlighting the potential devastation that a well-crafted and covert cyber weapon could inflict. Its sophistication and precision demonstrated that traditional security measures were no longer sufficient to protect critical infrastructure from advanced cyber threats.
The incident prompted a shift in mindset, with a greater emphasis on proactive defense strategies, intelligence sharing, and continual investment in cybersecurity research and development. Industries and governments worldwide began to recognize the importance of robust defense mechanisms, rapid response capabilities, and comprehensive cybersecurity frameworks to counter evolving threats.
The impact of Stuxnet also transcended the realm of cybersecurity and had significant ramifications for international relations. It challenged traditional notions of warfare, showcasing the potential for cyber weapons to disrupt and damage critical infrastructure. This raised concerns among nations about the vulnerability of their own systems and the need for robust defenses against such attacks.
The incident also highlighted the potential for cyber operations to affect geopolitical dynamics, with states employing cyber weapons as a means of achieving strategic objectives while maintaining plausible deniability. This led to increased scrutiny, diplomatic tensions, and discussions surrounding international norms and rules of engagement in cyberspace.
Stuxnet’s legacy can be seen in the growing global arms race in cyber capabilities. Nations worldwide have invested heavily in developing and enhancing their own cyber arsenals, aiming to maintain offensive capabilities and protect against potential cyber threats from adversaries.
The incident also accelerated the evolution of cybersecurity as a field of study and practice. Stuxnet exposed the need for specialized expertise in industrial control systems, threat intelligence analysis, and incident response. It led to advancements in cybersecurity research, the development of new defense mechanisms, and increased collaboration among industry professionals and researchers.
Stuxnet’s impact on international relations extended to efforts to establish norms and regulations in cyberspace. The incident highlighted the need for international cooperation and agreements to mitigate the risks posed by state-sponsored cyber attacks. It catalyzed discussions on defining acceptable behavior in cyberspace and addressing the challenges of attribution and deterrence.
Overall, Stuxnet left a lasting legacy in both cybersecurity and international relations. It has fundamentally changed the way nations view cyber threats, prompting a shift towards proactive defense strategies and increased investments in cybersecurity. It has also fueled discussions and debates surrounding the rules of engagement and the development of norms in the realm of cyber warfare.