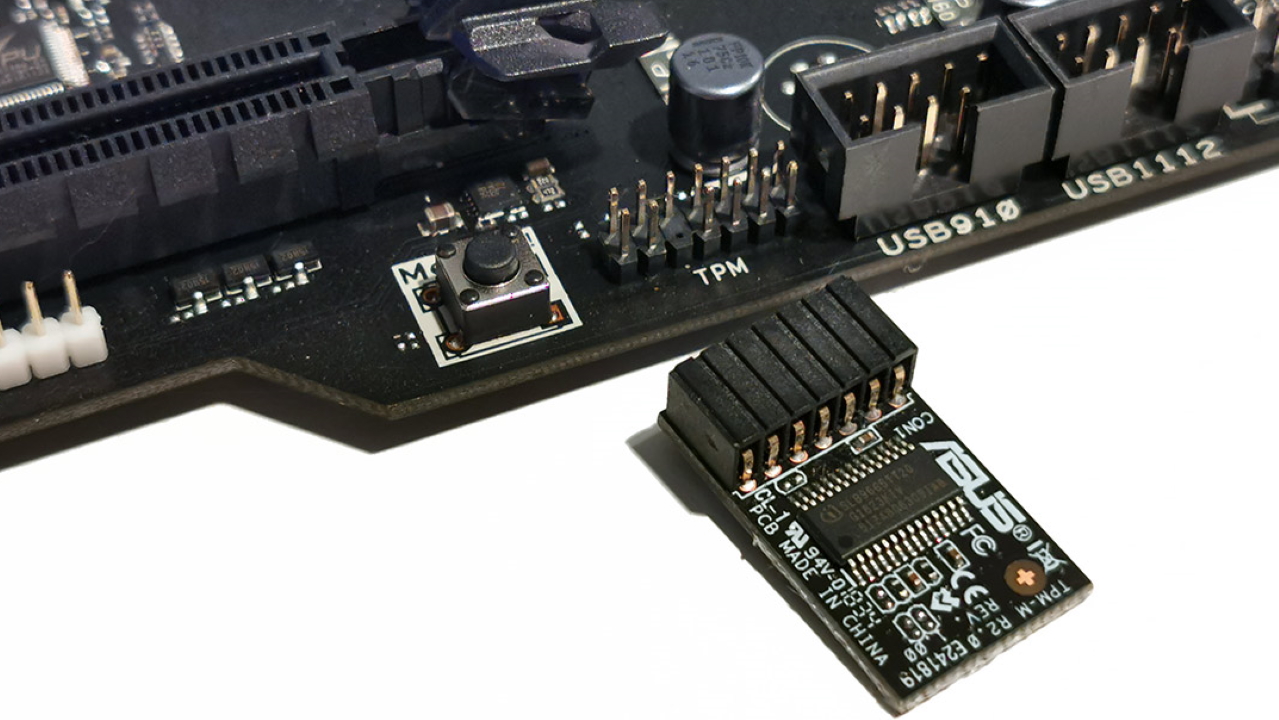
TPM Definition
TPM, short for Trusted Platform Module, is a dedicated hardware chip designed to enhance the security of computer systems. It is a tamper-resistant microcontroller that stores critical information, such as encryption keys, digital certificates, and passwords, in a secure manner. TPM acts as a secure vault, protecting sensitive data from unauthorized access and ensuring the integrity of the system.
TPM is integrated directly into a computer’s motherboard or added as a separate chip. It works independently of the operating system and provides a set of security-related functions that can be utilized by both hardware and software components of the system. These functions include secure boot, secure storage, secure key generation, and cryptographic operations.
At its core, TPM functions as a trusted root of trust, which means it establishes a foundation of trust for the system. It creates a secure environment where system integrity can be verified and trusted operations can take place. This makes TPM an essential component for establishing a trusted computing base and implementing robust security measures.
One of the primary functionalities of TPM is to ensure the integrity of the system during the boot process. It verifies the integrity of the firmware, bootloader, and operating system before allowing them to execute. This prevents malware or unauthorized software from gaining control over the system early in the boot process.
TPM also plays a crucial role in safeguarding encryption keys. It can generate and securely store cryptographic keys, ensuring that they are protected from unauthorized access. This is particularly important for applications that rely on encryption, such as securing data transmissions or protecting sensitive information.
Furthermore, TPM enables secure hardware-based authentication. It can securely store and manage digital certificates used for authentication purposes, such as for website logins or secure remote access. This eliminates the reliance on less secure software-based authentication methods and enhances the overall security posture of the system.
How TPM Works
Trusted Platform Module (TPM) operates by implementing a combination of hardware and software-based security measures to protect computer systems. Let’s take a closer look at how TPM works:
- Secure Boot: TPM ensures that the system boots securely by verifying the integrity of the firmware, bootloader, and operating system. It checks digital signatures to ensure that only trusted and authorized software is executed during the boot process.
- Secure Storage: TPM provides a secure storage area known as the “TPM Persistent Storage” or “TPM NVRAM.” This space is isolated from the rest of the system and is used to store sensitive data, such as encryption keys, digital certificates, and passwords. The data stored in TPM NVRAM is encrypted and can only be accessed by authorized applications or processes.
- Cryptographic Operations: TPM offers a range of cryptographic capabilities, including key generation, encryption, and digital signatures. It can generate random cryptographic keys that are securely stored within the chip. These keys can be used for encryption and decryption purposes, ensuring the confidentiality and integrity of sensitive data.
- Remote Attestation: TPM enables remote attestation, which allows other entities to verify the system’s integrity. This feature allows external parties to verify that a system has booted in a secure and trusted state, ensuring that the system has not been compromised or tampered with.
- Secure Platform Measurements: TPM measures various components and software binaries during the boot process and stores these measurements in the TPM’s Platform Configuration Registers (PCRs). These measurements form a unique “PCR composite” that represents the system’s state. Any changes to the system, such as modifications to the firmware or operating system, will result in different PCR values, indicating potential tampering or compromise.
To leverage TPM’s capabilities, applications and operating systems must have TPM support and utilize the appropriate software interfaces, such as the Trusted Computing Group’s TPM Software Stack (TSS) or Microsoft’s TPM Base Services (TBS) API. These interfaces allow developers to interact with the TPM and perform operations, such as storing keys, verifying system measurements, and utilizing cryptographic functions.
By implementing TPM into computer systems, organizations can enhance their overall security posture and protect against various threats, including malware, unauthorized access, and data breaches. TPM’s combination of hardware-based security, secure storage, and cryptographic functions provides a solid foundation for establishing trust and securing critical assets.
History of TPM
The history of Trusted Platform Module (TPM) traces back to the late 1990s when various technology companies recognized the need for a dedicated hardware solution to enhance computer system security. Let’s delve into the history of TPM:
In 1999, the Trusted Computing Group (TCG), an industry consortium focused on developing open standards for trusted computing initiatives, was formed. One of the main goals of the TCG was to create a standardized hardware-based security solution that could be implemented across different systems and platforms.
As a result, in 2001, the TCG released the first version of the TPM specification, known as TPM 1.1. This specification outlined the basic functions and features of TPM, including secure boot, secure storage, and cryptographic operations. Several technology companies, including Intel, IBM, and Microsoft, showed support for TPM and incorporated it into their products.
Over the years, TPM underwent significant enhancements and refinements. In 2009, the TCG released TPM 1.2, which introduced several improvements, such as increased storage capacity, improved cryptographic algorithms, and the addition of commands for remote attestation.
In 2014, the TCG released the latest iteration of TPM, known as TPM 2.0. This version introduced a more flexible and extensible architecture, allowing for easier integration with various platforms and devices. TPM 2.0 also enhanced cryptographic capabilities, such as support for elliptic curve cryptography and more secure algorithms.
It is worth noting that TPM has gained significant traction in the enterprise and government sectors over the years. Many organizations now require TPM-enabled systems for securely storing encryption keys, ensuring system integrity, and meeting compliance regulations.
Furthermore, TPM’s adoption has been driven by the increasing threats of malware, data breaches, and unauthorized access. The need for a dedicated hardware solution like TPM has become more evident in today’s interconnected digital landscape.
In recent years, TPM has become a standard feature in modern computing devices, including desktops, laptops, and servers. The integration of TPM into the system’s firmware or motherboard has become a common practice, ensuring that security features are built-in from the ground up.
Overall, the history of TPM highlights the ongoing commitment of technology companies and industry organizations to improve computer system security. TPM has evolved into a trusted and widely adopted security solution, providing organizations with enhanced protection against various threats and vulnerabilities.
Importance of TPM
Trusted Platform Module (TPM) is of paramount importance in today’s digital landscape, where threats to sensitive data and system integrity are on the rise. Let’s explore the significance of TPM in computer security:
1. Enhances System Security: TPM plays a vital role in enhancing system security by providing a secure storage environment for critical information, such as encryption keys and digital certificates. It ensures that this sensitive data remains protected from unauthorized access and tampering.
2. Establishes a Foundation of Trust: TPM serves as a trusted root of trust, establishing a foundation of trust for the system. It verifies the integrity of the system during the boot process, preventing malware or unauthorized software from gaining control early on. This ensures that the system operates in a trusted and secure manner.
3. Safeguards Encryption Keys: TPM generates and securely stores cryptographic keys, protecting them from unauthorized access. Encryption is essential for securing sensitive data, and by safeguarding the encryption keys, TPM helps ensure the confidentiality and integrity of the information.
4. Enables Secure Authentication: TPM provides hardware-based secure authentication, eliminating the reliance on less secure software-based authentication methods. It can securely store and manage digital certificates used for authentication purposes, enhancing the overall security posture of the system.
5. Supports Remote Attestation: TPM enables remote attestation, allowing external parties to verify the system’s integrity. This feature is particularly valuable in scenarios where trust needs to be established between different entities, such as during remote access or cloud computing applications.
6. Assists in Regulatory Compliance: Many industry regulations and standards require the implementation of strong security measures. TPM helps organizations meet these compliance requirements by providing a hardware-based security solution that can protect critical data, detect tampering attempts, and establish a trusted computing base.
7. Mitigates Risks of Data Breaches: Data breaches can have severe consequences for organizations, leading to financial loss, reputational damage, and legal implications. TPM’s robust security features help mitigate the risks associated with data breaches by protecting sensitive information and preventing unauthorized access to the system.
8. Future-Proofs Security: TPM continues to evolve and adapt to the changing threat landscape. With the introduction of TPM 2.0, TPM is more flexible, extensible, and suitable for a wide range of platforms and devices. This future-proof nature ensures that organizations can rely on TPM for long-term security needs.
Components of TPM
Trusted Platform Module (TPM) consists of several key components that work together to provide secure and trustworthy computing. Let’s explore the essential components of TPM:
1. TPM Chip: The TPM chip, also known as the TPM microcontroller, is a dedicated hardware component that houses the cryptographic functions and secure storage capabilities. The TPM chip is either integrated directly into the computer’s motherboard or added as a separate chip.
2. Secure Storage: TPM includes a secure storage area known as the “TPM Persistent Storage” or “TPM NVRAM” (Non-Volatile Random-Access Memory). This secure storage area is isolated from the rest of the system and provides a protected space for storing sensitive information, such as encryption keys, digital certificates, and passwords.
3. Cryptographic Functions: TPM offers a range of cryptographic functions, including encryption, decryption, digital signatures, and random number generation. These functions are utilized to secure data, protect communication channels, and ensure the integrity of system operations.
4. Platform Configuration Registers (PCRs): TPM contains a set of Platform Configuration Registers (PCRs), which store a measurement of various components and software binaries during the boot process. These measurements form a PCR composite, representing the system’s state and integrity. Any changes to the system will result in different PCR values, indicating potential tampering or compromise.
5. Hybrid Interface Protocol (HIP): TPM communicates with the system through a standardized interface known as the Hybrid Interface Protocol (HIP). The HIP allows software applications and operating systems to interact with TPM and access its functionalities, such as secure storage, cryptographic operations, and measurement verification.
6. Trusted Software Stack (TSS): The Trusted Software Stack (TSS) is a software framework that provides APIs (Application Programming Interfaces) for developers to integrate TPM capabilities into their applications. The TSS allows developers to interact with the TPM chip, perform secure operations, and manage cryptographic keys.
7. Attestation Identity Key (AIK): TPM supports the use of Attestation Identity Keys (AIKs) to provide additional security and authentication. AIKs are cryptographic keys specific to an individual TPM and are used for remote attestation, allowing other entities to verify the integrity and authenticity of the system.
8. TPM Firmware: TPM firmware refers to the software that runs on the TPM chip. Firmware updates are periodically released by TPM manufacturers to address security vulnerabilities, add new features, and ensure compatibility with the latest industry standards.
Overall, these components work together to establish and maintain a trusted foundation for system operations. TPM’s hardware-based security features, combined with its secure storage, cryptographic functions, and measurement capabilities, provide organizations with a powerful tool to enhance their overall security posture and protect against various threats.
Uses of TPM
Trusted Platform Module (TPM) offers a wide range of applications and use cases, enabling organizations to enhance their security practices and protect sensitive data. Let’s explore some of the common uses of TPM:
1. Secure Boot: TPM plays a critical role in ensuring secure boot processes. It verifies the integrity of the firmware, bootloader, and operating system, allowing only trusted and authorized software to execute during the boot sequence. This prevents malware or unauthorized software from compromising the system early in the startup process.
2. Full Disk Encryption (FDE): TPM is often utilized in conjunction with full disk encryption solutions to protect the contents of a computer’s storage device. It securely stores the encryption keys and enables a transparent and hardware-based solution, ensuring that data on the disk remains encrypted and inaccessible in the event of theft or unauthorized access.
3. Digital Rights Management (DRM): TPM can be used to enforce access control and protect digital content. It provides a secure environment for managing cryptographic keys required for content decryption, ensuring that only authorized devices can access and view protected digital media.
4. Secure Remote Access: TPM enables secure remote access scenarios, such as virtual private networks (VPNs) and remote desktops. It can store digital certificates required for secure authentication, enhancing the security of remote connections and protecting sensitive information during data transmissions.
5. Data Protection and Integrity: TPM’s cryptographic capabilities, secure storage, and measurement verification can be utilized to protect the confidentiality, integrity, and authenticity of sensitive data. It can be used in applications like secure file encryption, digital signatures, secure email communication, and preventing unauthorized modifications to critical system files.
6. Identity and Access Management: TPM can contribute to robust identity and access management practices. It can securely store and manage cryptographic keys used for authentication and authorization purposes, reducing reliance on traditional username/password-based authentication and improving overall security posture.
7. Secure Virtualization: TPM helps enhance the security of virtualized environments by providing a trusted platform to ensure the integrity of hypervisors, virtual machines, and guest operating systems. It helps protect against virtual machine tampering, unauthorized access, and data leakage within the virtualization layer.
8. Secure Firmware Updates: TPM ensures the integrity of firmware updates by verifying the authenticity and integrity of the update packages. This prevents malicious firmware from being installed and reduces the risk of firmware-level attacks that can compromise the system’s security and stability.
Overall, the extensive uses of TPM demonstrate its versatility and importance in enhancing the security of computer systems. By leveraging TPM’s capabilities, organizations can establish a foundation of trust, protect sensitive data, and mitigate various security risks.
TPM vs. TPM 2.0
Trusted Platform Module (TPM) has undergone significant advancements in its evolution, with TPM 2.0 representing a major upgrade over its predecessor, TPM 1.2. Let’s highlight the key differences between TPM and TPM 2.0:
1. Architectural Changes: TPM 2.0 introduces a more flexible and modular architecture compared to TPM 1.2. It provides a broader range of commands and functions that can be tailored to meet specific platform requirements. TPM 2.0 also offers enhanced cryptographic capabilities and supports newer algorithms, such as elliptic curve cryptography.
2. Command Structure: TPM 2.0 employs a new command structure that is more extensible and efficient. It includes new commands for cryptographic operations, key management, and policy-based authorization. This improved command structure allows for easier integration with diverse platforms and enhances the ability to support new security features.
3. Enhanced Cryptography: TPM 2.0 provides increased cryptographic capabilities compared to TPM 1.2. It supports a broader range of cryptographic algorithms, including more secure and efficient options such as elliptic curve cryptography. This allows for stronger encryption, more robust digital signatures, and improved secure key generation.
4. Improved Remote Attestation: TPM 2.0 enhances the remote attestation capabilities introduced in TPM 1.2. It provides better support for dynamic and flexible attestation, allowing for fine-grained measurement verification and improved integrity assessment of the system. TPM 2.0 also offers the ability to generate unique attestation keys for greater attestation security.
5. Flexible Authorization Policies: TPM 2.0 introduces policy-based authorization, enabling more fine-grained control over access to TPM resources. This enhanced flexibility enables administrators to define complex rules and conditions that govern access to TPM functions and data, providing added security and control over system operations.
6. Expanded Event Logging: TPM 2.0 incorporates an expanded event log structure compared to TPM 1.2. It allows for more detailed and granular event logging, capturing a wider range of system events and changes. This offers increased visibility into the system’s integrity and facilitates improved analysis and auditing capabilities.
7. Compatibility: While TPM 2.0 introduces several enhancements, it is important to note that it is not backward compatible with TPM 1.2. Systems designed for TPM 1.2 may require updates or hardware replacements to support TPM 2.0. However, many modern systems are now equipped with TPM 2.0 chips, ensuring compatibility with the latest industry standards.
8. Industry Support: TPM 2.0 has gained widespread industry adoption, with support from major technology companies, software vendors, and industry standards organizations. The increased support and adoption of TPM 2.0 ensure continued development, compatibility, and availability of security solutions and ecosystem support.
Benefits of TPM
Trusted Platform Module (TPM) offers a wide range of benefits that contribute to enhanced security, integrity, and trustworthiness of computer systems. Let’s explore some of the key advantages of TPM:
1. Hardware-Based Security: TPM provides a dedicated hardware chip that offers robust security features. By having a separate and tamper-resistant component, TPM enhances the overall security posture of the system, making it more resistant to attacks and unauthorized access.
2. Protection of Sensitive Data: TPM’s secure storage capability ensures the protection of sensitive data, such as encryption keys, digital certificates, and passwords. This helps safeguard confidential information from unauthorized access, improving the confidentiality and integrity of the system.
3. Secure Boot Process: TPM verifies the integrity of the system during the boot process, ensuring that only trusted and authorized software is executed. This helps prevent malware or unauthorized software from compromising the system early in the startup sequence, reducing the risk of system compromise.
4. Robust Cryptographic Capabilities: TPM offers a range of cryptographic functions, including key generation, encryption, and digital signatures. This allows for secure communications, data protection, and strong authentication, enhancing the overall security of applications and systems.
5. Remote Attestation: TPM enables remote attestation, allowing other entities to verify the integrity and trustworthiness of the system. This is particularly useful in remote access scenarios, cloud computing, or situations where trust needs to be established between different entities.
6. Improved Identity and Access Management: With TPM’s secure storage and cryptographic capabilities, organizations can enhance their identity and access management practices. TPM can securely store and manage cryptographic keys used for authentication and authorization, reducing the reliance on less secure username/password-based authentication methods.
7. Compliance with Security Standards: TPM helps organizations meet security standards and compliance requirements. Many industry regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Federal Information Processing Standards (FIPS), require the implementation of strong security measures, which TPM can help address.
8. Protection against Firmware-Level Attacks: TPM’s secure boot process and measurement capabilities help protect against firmware-level attacks, where malware or unauthorized modifications to the system firmware can compromise the system’s security. TPM ensures that the firmware remains secure and untampered, reducing the risk of such attacks.
By leveraging the benefits of TPM, organizations can establish a foundation of trust, protect sensitive data, enhance the security of their systems, and meet the ever-increasing demands of the digital landscape.
TPM in Different Industries
Trusted Platform Module (TPM) has found applications across various industries, where the need for robust security and protection of sensitive data is paramount. Let’s explore how TPM is utilized in different sectors:
1. Banking and Finance: The banking and finance industry relies heavily on TPM to protect sensitive customer data and ensure secure financial transactions. TPM enables secure online banking, protects cryptographic keys, and enhances the integrity and confidentiality of financial systems and transactions.
2. Healthcare: In the healthcare sector, TPM plays a crucial role in securing patient records, protecting sensitive health information, and ensuring compliance with privacy regulations such as the Health Insurance Portability and Accountability Act (HIPAA). TPM helps safeguard electronic health records, encrypt communication channels, and protect against unauthorized access to patient data.
3. Government and Defense: TPM is widely used in government and defense organizations to secure classified information, protect critical infrastructure, and ensure the integrity of sensitive systems. TPM’s secure boot process, secure storage, and cryptographic capabilities are crucial in safeguarding national security, preventing unauthorized access, and deterring cyber threats.
4. IT and Cloud Service Providers: TPM is of great importance for IT and cloud service providers who need to offer highly secure and trusted services. TPM enhances the security of virtualization environments, protects cloud-based applications and data, and ensures the integrity of virtual machines and hosted services.
5. Industrial Control Systems (ICS): Industries that rely on critical infrastructure and industrial control systems, such as energy, manufacturing, and transportation, utilize TPM to secure process control systems and protect against unauthorized access or tampering. TPM enhances the trustworthiness of these systems, ensuring the integrity and availability of essential services.
6. Education: TPM is increasingly being adopted in educational institutions to secure student and faculty data, protect sensitive research information, and ensure the integrity of online learning platforms. TPM helps prevent unauthorized access, safeguard intellectual property, and promote a secure digital learning environment.
7. Retail and E-commerce: Retailers and e-commerce businesses utilize TPM to secure customer transactions, protect payment card data, and ensure the integrity of online shopping platforms. TPM enhances the security of point-of-sale systems, encrypts sensitive data during transmission, and helps prevent unauthorized access and data breaches.
8. Internet of Things (IoT): With the proliferation of IoT devices, TPM is becoming increasingly important in securing connected devices and protecting IoT ecosystems. TPM enables secure device authentication, ensures data privacy and integrity, and guards against unauthorized access and tampering in IoT deployments.
Overall, TPM’s versatile and robust security features enable its widespread adoption across diverse industries, addressing the unique security challenges faced by each sector. TPM’s applications range from protecting sensitive data to securing critical infrastructure, facilitating trusted transactions, and ensuring compliance with industry regulations.
Challenges of Implementing TPM
Implementing Trusted Platform Module (TPM) can bring significant benefits to organizations, but it also comes with its set of challenges. Let’s explore some of the key challenges involved in implementing TPM:
1. Hardware and Firmware Requirements: One of the main challenges of implementing TPM is ensuring compatibility with existing hardware and firmware. TPM may require specific hardware components or a firmware update to enable TPM functionality. Organizations need to assess their systems’ compatibility and ensure that the necessary hardware and firmware requirements are met.
2. Integration into Existing Systems: Integrating TPM into existing systems can be complex, especially for legacy systems or systems with diverse hardware configurations. Organizations must consider factors such as compatibility with different operating systems and applications, potential conflicts with existing security solutions, and the need for driver updates or software modifications.
3. User Education and Training: TPM implementation often involves educating and training users on its features, benefits, and best practices. Users need to understand how TPM affects their day-to-day operations, such as system boot processes or secure storage practices. User awareness programs and training sessions should be conducted to enhance understanding and ensure proper usage of TPM.
4. Key Management and Recovery: Managing cryptographic keys stored in TPM can be challenging. Organizations must establish proper key management practices, including secure backup, rotation, and recovery processes. Lost or damaged keys can lead to data loss or system lockouts, so a robust key management strategy is essential to mitigate these risks.
5. Interoperability and Vendor Support: TPM interoperability can be a challenge, particularly when working with multiple vendors’ systems or devices. Organizations should ensure that their chosen TPM solution follows industry standards and has support from trusted vendors. Supervising the interoperability between different TPM versions and ensuring seamless integration across platforms can mitigate potential issues.
6. Performance and Scalability: Depending on the system’s workload, TPM operations could impact performance. Organizations should carefully assess the processing requirements and potential performance impacts of enabling TPM features. Additionally, considerations should be given to scalability, ensuring that TPM can handle increased workloads and system demands as the organization grows.
7. Regulatory Compliance Considerations: Implementing TPM may involve compliance with industry-specific regulations, such as data protection or privacy laws. Organizations must assess and ensure that the implementation of TPM aligns with regulatory requirements, such as handling encryption-related obligations or privacy considerations when storing sensitive data.
8. Cost and Return on Investment: Implementing TPM may require investment in hardware, firmware updates, software licenses, and training. Organizations need to assess the cost-benefit ratio and evaluate the potential return on investment in terms of improved security, reduced risks, and compliance benefits. Calculating the total cost of ownership and conducting a thorough cost-analysis helps in determining feasibility.
Addressing these challenges through proper planning, stakeholder engagement, robust training programs, and close collaboration with hardware and software vendors can help organizations overcome obstacles and successfully implement TPM for improved security and trust in their systems.
Best Practices for TPM Implementation
Implementing Trusted Platform Module (TPM) requires careful planning and adherence to best practices to ensure its successful integration into an organization’s security framework. Let’s explore some key best practices for TPM implementation:
1. Conduct a Security Assessment: Before implementing TPM, conduct a comprehensive security assessment to identify risks, vulnerabilities, and security requirements specific to your organization. This assessment will help determine how TPM can address security gaps and align with your overall security strategy.
2. Establish Clear Objectives: Clearly define the objectives and desired outcomes of TPM implementation. Identify the specific security goals you aim to achieve, such as secure boot, secure storage, or enhanced authentication. Clearly defined objectives will guide the implementation process and facilitate effective evaluation of its success.
3. Ensure Hardware and Firmware Compatibility: Verify that the existing hardware and firmware in your systems are TPM-compatible. Evaluate potential hardware upgrades or firmware updates required to enable TPM functionality. Collaborate with hardware vendors and ensure TPM compliance before proceeding with implementation.
4. Develop Key Management Processes: Establish strong key management practices for the cryptographic keys stored in TPM. Implement processes for key generation, backup, rotation, and recovery. Ensure that keys are securely stored, and access control mechanisms are in place to protect against unauthorized use or loss.
5. User Education and Training: Provide comprehensive user education and training programs to ensure that employees understand the purpose, benefits, and proper usage of TPM. Educate users on secure boot processes, the importance of secure storage, and the handling of cryptographic keys. Regularly update training materials to address any changes or updates in TPM functionality.
6. Implement Strong Access Controls: Configure TPM to enforce strong access controls and policies. Implement multi-factor authentication, such as combining TPM with strong passwords, smart cards, or biometric authentication. Leverage TPM’s features to enforce secure access to critical systems and ensure only authorized entities can interact with TPM functions.
7. Regularly Update Firmware: Stay up-to-date with TPM firmware updates provided by the manufacturer. These updates often include security patches, bug fixes, and additional features that enhance TPM’s security capabilities. Regularly apply firmware updates to address known vulnerabilities and ensure ongoing protection.
8. Monitor and Audit TPM activity: Implement logging and auditing mechanisms to monitor TPM activities and detect any suspicious or unauthorized access attempts. Regularly review and analyze these logs to identify any potential security incidents or anomalies. Incorporate TPM activity monitoring into your organization’s overall security monitoring framework.
9. Periodic Security Assessments: Conduct periodic security assessments to evaluate the effectiveness and compliance of your TPM implementation. Assess the overall security posture, perform vulnerability assessments, and ensure TPM remains aligned with evolving security requirements and industry best practices.
By following these best practices, organizations can ensure a smooth and secure TPM implementation that enhances the overall security posture, protects against potential threats, and establishes a foundation of trust in their systems.
Future of TPM
The Trusted Platform Module (TPM) has evolved significantly since its introduction, and its future continues to hold promise in enhancing security and trust in computer systems. Let’s explore some key aspects that indicate the future of TPM:
1. Continued Industry Adoption: As the importance of securing digital assets grows, industry adoption of TPM is expected to increase. More organizations across diverse sectors are recognizing the value of TPM in protecting sensitive data, establishing a foundation of trust, and meeting regulatory compliance requirements.
2. Improved Integration and Interoperability: TPM is likely to witness improved integration and interoperability capabilities as it becomes more standardized across platforms and devices. Interoperability enhancements will simplify TPM integration into a wide range of hardware configurations, operating systems, and software applications.
3. Advancements in Hardware Security: Hardware security solutions are continuously evolving to counter emerging threats. TPM is expected to keep pace with these advancements, incorporating more robust physical security measures in future iterations, such as advanced tamper resistance mechanisms and improved protection against physical attacks.
4. Enhanced Secure Boot Mechanisms: Secure boot, a critical feature of TPM, will continue to be refined to address evolving threats, such as firmware-level attacks and bootkits. Future TPM iterations may introduce stronger mechanisms to detect and prevent unauthorized modifications to the boot process, ensuring the integrity and trustworthiness of the system.
5. Extended Security Capabilities: TPM is likely to expand its security capabilities beyond its current features. Future TPM versions may include enhancements such as improved protection against side-channel attacks, support for post-quantum cryptographic algorithms, and enhanced measures for protecting sensitive user data and credentials.
6. Integration with Emerging Technologies: As emerging technologies like cloud computing, Internet of Things (IoT), and artificial intelligence (AI) continue to evolve, the integration of TPM into these technologies will become more prevalent. This integration will help establish trust in these ecosystems and address the unique security challenges they present.
7. Privacy and Data Protection: The increasing focus on privacy and data protection is expected to influence the future of TPM. TPM may evolve to include features that enable stronger privacy controls, enhanced encryption techniques, and improved protection of user data from unauthorized access or misuse.
8. Standardization and Global Regulations: Efforts towards standardizing TPM and its usage are likely to continue. Collaboration among industry organizations, technology vendors, and regulatory bodies is expected to lead to standardized guidelines and frameworks for TPM implementation, ensuring consistent security practices and facilitating global adoption.
With the ever-evolving threat landscape, TPM’s evolution will remain pivotal in addressing emerging security challenges and raising the bar for secure computing. As technology advances and security demands grow, TPM will continue to serve as a cornerstone in establishing trust, protecting sensitive information, and ensuring the integrity of computer systems.