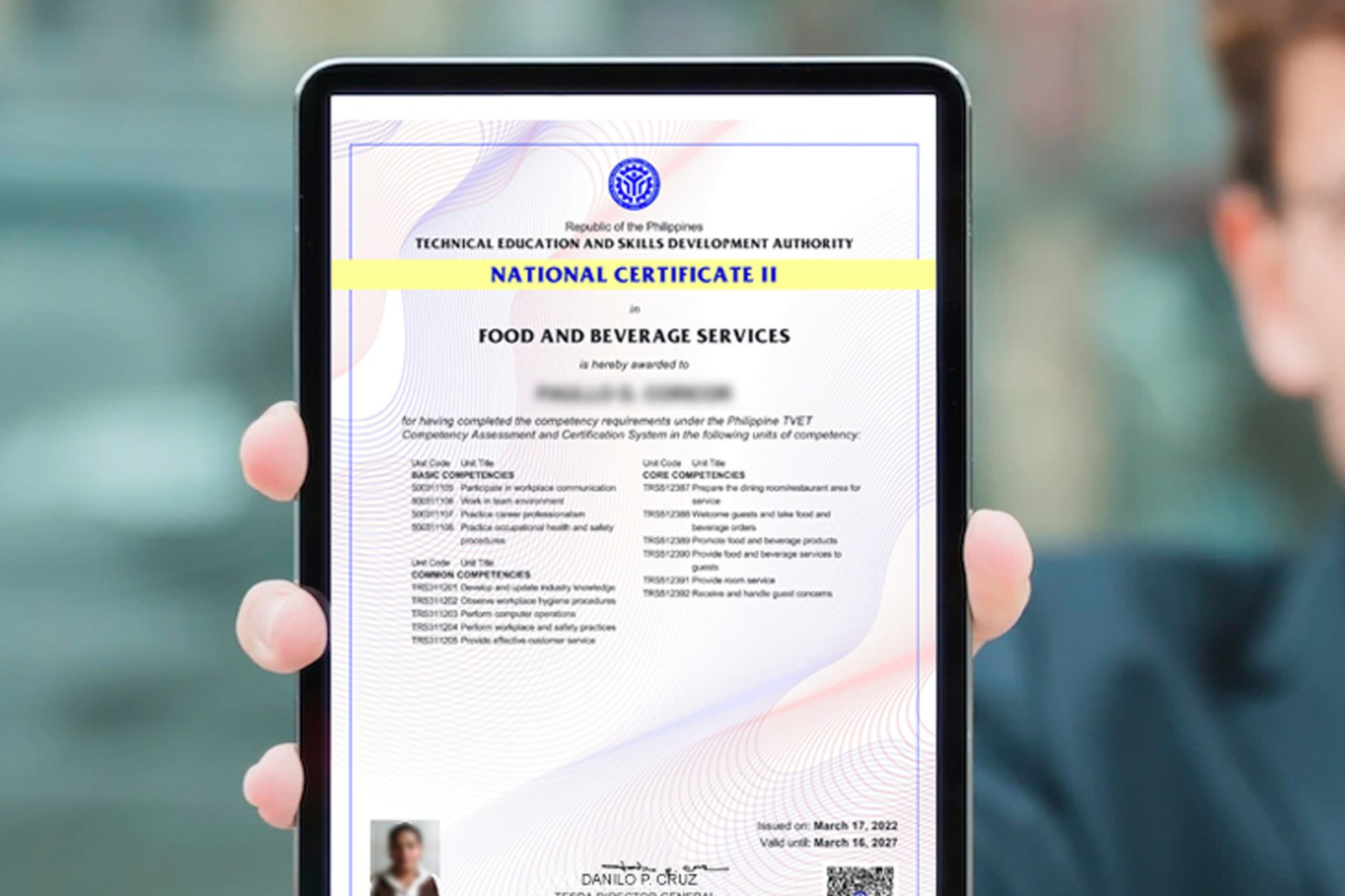
What Is an Electronic Certificate?
An electronic certificate, also known as a digital certificate or an e-certificate, is a digital document used to verify the identity of individuals, organizations, or products in the digital world. It serves as a secure and trusted form of identification, much like a physical passport or driver’s license.
An electronic certificate contains information about the certificate holder, such as their name, organization, public key, and other pertinent details. It is digitally signed by a trusted third party, known as a Certificate Authority (CA), to ensure its authenticity.
The primary purpose of an electronic certificate is to establish trust and provide secure communication over the internet. It enables users to verify the identity of the certificate holder and ensures that data exchanged between parties is encrypted and cannot be tampered with.
Electronic certificates play a vital role in various applications, including e-commerce, online banking, government services, email encryption, and more. They ensure the confidentiality, integrity, and authenticity of digital transactions.
When a user encounters an electronic certificate, it can be verified by checking its digital signature against the public key of the Certificate Authority that issued it. If the verification process is successful, the user can trust the information provided in the certificate and proceed with the transaction or communication.
Electronic certificates have revolutionized the way we interact and conduct business in the digital age. They have replaced traditional methods of identity verification, such as physical identification cards, with a more convenient and secure digital solution.
As technology continues to advance, electronic certificates are becoming even more crucial in establishing trust and security in the online world. They play a vital role in safeguarding sensitive information and protecting against cyber threats.
Advantages of Electronic Certificates
Electronic certificates offer numerous advantages over traditional forms of identification and verification. Here are some key benefits:
- Enhanced Security: Electronic certificates utilize encryption techniques to ensure the confidentiality and integrity of data. This prevents unauthorized access and protects against tampering or forgery.
- Convenience: Unlike physical documents, electronic certificates can be easily shared and transmitted digitally. They eliminate the need for physical handling and allow for quick and secure verification.
- Cost Effectiveness: The use of electronic certificates eliminates the need for printing, storage, and distribution of physical documents. This leads to cost savings for organizations and individuals alike.
- Time Efficiency: Verifying electronic certificates can be done instantly, reducing the time and effort required for manual verification. This is especially beneficial in industries that involve frequent identity checks.
- Global Recognition: Electronic certificates are recognized and accepted worldwide, making them valuable in international transactions and communications. They provide a standardized and universally accepted form of identification.
- Sustainability: By eliminating the reliance on paper documents, electronic certificates contribute to a more eco-friendly approach. They help reduce waste and promote sustainable practices.
These advantages demonstrate the transformative power of electronic certificates in enhancing security, streamlining processes, and promoting efficiency in various industries. From simplifying online transactions to facilitating secure communications, electronic certificates have become an essential component of the digital landscape.
Types of Electronic Certificates
Electronic certificates can be classified into various types based on their usage and application. Here are some common types:
- SSL/TLS Certificates: SSL/TLS certificates are used to secure websites and enable encrypted communication between the server and the user’s browser. They ensure that the website is authentic and the data exchanged is protected.
- Code Signing Certificates: Code signing certificates are used by software developers to digitally sign their code or applications. This verifies the authenticity and integrity of the software, assuring users that it has not been tampered with.
- Email Certificates: Email certificates, also known as S/MIME certificates, are used to digitally sign and encrypt emails. They provide authentication and ensure that only the intended recipient can read the encrypted message.
- Client Certificates: Client certificates are used to authenticate individuals or devices accessing a secure network or service. They enable organizations to control access and ensure that only authorized users can connect.
- Document Signing Certificates: Document signing certificates are used to digitally sign electronic documents, such as contracts, agreements, or invoices. They provide legal validity, ensuring the integrity of the document and the identity of the signer.
- ID/Passport Certificates: ID or passport certificates are digital versions of physical identification cards or passports. They offer a secure and convenient way for individuals to prove their identity in digital transactions or interactions.
These are just a few examples of the types of electronic certificates available. Each type serves a specific purpose and provides the necessary security and authentication features for its intended application.
It is worth noting that the types of electronic certificates may vary depending on the industry and the specific requirements of the organization or individual. As technology advances, new types of electronic certificates may emerge to address evolving security needs in the digital landscape.
How Electronic Certificates Work
Electronic certificates function through a process that involves encryption, digital signatures, and trusted third-party authorities. Here is an overview of how electronic certificates work:
- Creation of the Certificate: The certificate holder generates a pair of cryptographic keys: a private key and a public key. The private key is kept securely by the certificate holder, while the public key is included in the certificate.
- Verification: The certificate holder’s identity is verified by a trusted third-party authority known as a Certificate Authority (CA). The CA confirms the identity and issues the electronic certificate. The certificate includes information about the certificate holder and their public key.
- Digital Signature: The CA digitally signs the electronic certificate using its private key. This digital signature serves as proof of the certificate’s authenticity and ensures that it has not been tampered with.
- Certificate Distribution: The electronic certificate is distributed to the intended recipients, such as servers, devices, or individuals. The recipients can obtain the certificate through various means, including download from a trusted website or delivery via email.
- Certificate Validation: When a recipient encounters the electronic certificate, they can validate its authenticity by verifying the digital signature using the CA’s public key. This ensures that the certificate has not been altered and can be trusted.
- Secure Communication: The recipient can then use the public key from the electronic certificate to establish a secure communication channel with the certificate holder. This allows for encrypted and confidential data transmission.
The process of electronic certificates relies on the trustworthiness of the Certificate Authority, which is responsible for verifying identities and issuing certificates. The CA’s private key and digital signature ensure the integrity and authenticity of the certificates they issue.
Overall, electronic certificates enable secure and trusted communication in the digital realm. They provide a framework for verifying identities, encrypting data, and establishing secure connections, making them essential for ensuring trust and security in various online transactions and communications.
Digital Signatures and Electronic Certificates
Digital signatures are an integral component of electronic certificates, providing additional layers of security and authenticity. They play a crucial role in verifying the integrity of electronic documents and ensuring the identity of the signer. Here’s how digital signatures and electronic certificates work together:
When a document is digitally signed, a mathematical algorithm is used to generate a unique digital fingerprint of the document. This fingerprint, also known as a hash, is encrypted using the signer’s private key. The encrypted hash, along with the signer’s public key, is attached to the document, creating a digital signature.
To validate the digital signature, the recipient of the signed document can decrypt the encrypted hash using the signer’s public key. The recipient then computes a hash of the document and compares it to the decrypted hash. If the two hashes match, it confirms that the document has not been altered since it was signed and that the signer’s identity is verified.
Electronic certificates come into play in the process of verifying digital signatures. The digital signature is attached to the document along with the signer’s electronic certificate, which contains their public key. The recipient uses the public key from the electronic certificate to verify the digital signature.
Before trusting the digital signature, the recipient verifies the authenticity of the electronic certificate by checking its digital signature against the public key of the trusted Certificate Authority (CA) who issued the certificate. If the digital signature of the electronic certificate is valid, the recipient can trust the public key contained within the certificate.
By combining digital signatures and electronic certificates, the integrity and authenticity of digital documents can be assured. This ensures non-repudiation – the signer cannot deny their signature – and provides a secure and reliable method of verifying the identity of the signer.
Digital signatures and electronic certificates play a vital role in various domains, including e-commerce, legal documents, financial transactions, and government services. They enable secure and trusted communications, protect against tampering or forgery, and ensure the validity and integrity of digital documents.
It’s important to note that the strength of digital signatures and the trustworthiness of electronic certificates rely on the encryption algorithms used and the security measures implemented by the Certificate Authorities. As technology advances, it becomes crucial to maintain up-to-date cryptographic practices and stay ahead of potential vulnerabilities.
Implementing Electronic Certificates in Different Industries
Electronic certificates have gained widespread adoption across various industries due to their ability to enhance security, streamline processes, and ensure trust in digital transactions. Here’s how electronic certificates are implemented in different sectors:
- E-commerce: In the e-commerce industry, electronic certificates play a crucial role in securing online transactions and protecting consumer information. SSL/TLS certificates are used to encrypt sensitive data, such as credit card details, during online purchases, ensuring secure communication between the customer’s browser and the e-commerce website.
- Financial Services: Financial institutions utilize electronic certificates to verify the identity of their customers and secure online banking transactions. These certificates enable secure access to financial platforms, authenticate users, and ensure the confidentiality of sensitive financial information.
- Healthcare: The healthcare industry relies on electronic certificates to protect patient data and facilitate secure communications between healthcare providers. Digital signatures are used to sign medical documents and maintain data integrity, while client certificates verify the identities of medical professionals accessing electronic health records.
- Government Services: Governments use electronic certificates to provide secure access to online services, such as tax filing, e-government portals, and digital signatures on official documents. Electronic certificates enable citizens to authenticate themselves digitally, eliminating the need for physical visits and paperwork.
- Manufacturing: In the manufacturing industry, electronic certificates are used to ensure the authenticity and integrity of digital product certificates, warranty claims, and supply chain documentation. They help in detecting counterfeits, preventing fraud, and maintaining the traceability of products throughout the manufacturing process.
- Education: Educational institutions employ electronic certificates to verify academic qualifications and credentials. These certificates provide a secure and convenient way to authenticate degrees, diplomas, and other educational achievements, enabling employers and institutions to easily confirm the legitimacy of an individual’s qualifications.
These examples highlight the versatility and importance of electronic certificates in various industries. By implementing electronic certificates, organizations can enhance security, reduce fraud, streamline processes, and build trust with their customers and stakeholders.
It’s worth noting that the specific implementation of electronic certificates may vary within each industry, depending on the unique requirements and regulatory frameworks. However, the underlying principles of using electronic certificates to establish trust and secure digital communication remain consistent across industries.
Challenges and Risks of Electronic Certificates
While electronic certificates offer numerous benefits, there are also challenges and risks associated with their implementation. It’s crucial to be aware of these factors to mitigate potential issues. Here are some challenges and risks to consider:
- Certificate Authority Trust: The trustworthiness of Certificate Authorities (CAs) is essential for the integrity of electronic certificates. An insecure or compromised CA can undermine the trust in the entire system. It is crucial to ensure the selection of reputable and reliable CAs to issue and validate electronic certificates.
- Key Management: Proper key management is critical for the security of electronic certificates. This includes secure storage of private keys, secure key exchange protocols, and key revocation mechanisms. Any compromise in key management practices can lead to unauthorized access or the ability to forge digital signatures.
- Certificate Expiration: Electronic certificates have a limited validity period. Organizations must ensure timely renewal or replacement of certificates to prevent disruptions in secure communications or access to services. Failure to manage certificate expiration puts data security and trust at risk.
- Revocation and Validation: In the event of compromised private keys or fraudulent certificates, the ability to revoke and validate certificates becomes crucial. Revocation mechanisms need to be in place, and certificate validation should be done during each interaction to guarantee ongoing trust in the digital ecosystem.
- Interoperability: Ensuring interoperability between different systems and platforms can be challenging. Electronic certificates need to be compatible with various hardware and software environments to enable seamless integration and widespread adoption.
- Human Error: Mismanagement or mishandling of electronic certificates by individuals can pose a significant risk. Failure to protect private keys, accidental deletion, or sharing of certificates can lead to unauthorized access or misuse of sensitive information.
- Evolution of Technology: As technology advances, new vulnerabilities and threats can emerge. It is essential to stay up to date with the latest encryption algorithms, security protocols, and industry best practices to mitigate risks and adapt to evolving threats.
Addressing these challenges and risks requires implementing robust security measures, conducting regular audits, and staying informed about advancements in the field of electronic certificates. Organizations must prioritize security practices, user education, and risk management strategies to ensure the continued trust and reliability of electronic certificates.
How to Verify an Electronic Certificate
Verifying the authenticity and validity of an electronic certificate is crucial to ensure the trustworthiness of the information and the identity of the certificate holder. Here are the steps to verify an electronic certificate:
- Step 1: Obtain the Electronic Certificate: Obtain the electronic certificate from the source, such as a website, email, or digital document. Make sure the certificate is obtained from a trusted and reliable source.
- Step 2: Check the Certificate Details: Examine the details mentioned in the electronic certificate, such as the name of the certificate holder, the issuing authority, and the certificate’s validity period. Ensure that the information aligns with your expectations and requirements.
- Step 3: Verify the Digital Signature: Verify the digital signature attached to the electronic certificate. Use the public key of the Certificate Authority (CA) who issued the certificate to authenticate the digital signature. If the digital signature is valid, it confirms the authenticity and integrity of the certificate.
- Step 4: Cross-Check with the Certificate Authority: Cross-reference the details in the electronic certificate with the information provided by the Certificate Authority (CA) who issued the certificate. This can be done by visiting the CA’s website or contacting their support services. Confirm that the certificate has been issued by the legitimate CA and has not been revoked.
- Step 5: Perform Online Certificate Validation: Many Certificate Authorities offer online certificate validation tools or services. Utilize these tools by entering the electronic certificate’s details to perform real-time validation against the CA’s database. This validation process confirms the current status and authenticity of the certificate.
- Step 6: Check for Revocation: Verify if the electronic certificate has been revoked. Use the Certificate Revocation List (CRL) or Online Certificate Status Protocol (OCSP) to check the revocation status. If the certificate has been revoked, it indicates potential misuse or compromise, and trust should not be placed in the certificate.
- Step 7: Trust Your Intuition: Trust your intuition and exercise caution if something feels suspicious or unfamiliar. If the electronic certificate raises doubts or seems untrustworthy, it is advisable to refrain from engaging in transactions or interactions that rely on that certificate.
By following these steps, you can effectively verify the authenticity and validity of an electronic certificate. Taking the time to verify electronic certificates ensures secure and trustworthy communication, protects against potential fraud or misuse, and helps maintain the integrity of digital transactions.
Popular Applications of Electronic Certificates
Electronic certificates find extensive use in various industries and applications due to their ability to provide secure identification and authentication. Here are some popular applications of electronic certificates:
- E-commerce: Electronic certificates, particularly SSL/TLS certificates, are widely utilized in e-commerce to secure online transactions. They protect sensitive customer information, such as credit card details, by encrypting data exchanged between the customer’s browser and the e-commerce website.
- Email Encryption: Electronic certificates, specifically S/MIME certificates, are widely employed for securing email communication. By digitally signing and encrypting emails, electronic certificates ensure the authenticity and confidentiality of email content, minimizing the risk of unauthorized access or tampering.
- Banking and Financial Services: Financial institutions use electronic certificates to establish secure connections with customers accessing online banking services. By verifying the identity of users through client certificates, financial organizations protect customer data and prevent unauthorized access to accounts.
- Government Services: Electronic certificates facilitate secure government services, enabling citizens to authenticate themselves digitally. From online tax filing to accessing government portals, electronic certificates provide a trusted means of identification, eliminating the need for physical visits and paperwork.
- Healthcare: Healthcare institutions rely on electronic certificates to ensure the integrity and confidentiality of patient data. Electronic certificates are used to sign medical documents, authenticate healthcare professionals accessing electronic health records, and enable secure communication among healthcare providers.
- Software Distribution: In the software industry, code signing certificates are widely utilized to digitally sign software applications. This ensures that users can trust the authenticity and integrity of the software they download, reducing the risk of malware or tampered code.
- E-government: Governments worldwide use electronic certificates for various e-government services. These include digitally signing official documents, issuing digital IDs and passports, and facilitating secure communication between government agencies and citizens.
- Education and Academic Institutions: Electronic certificates play a vital role in verifying academic qualifications and credentials. They enable educational institutions to issue and verify digital certificates for degrees, diplomas, and other educational achievements, simplifying the authentication process for employers and institutions.
- Manufacturing and Supply Chain: In the manufacturing industry, electronic certificates help ensure product authenticity and maintain trust in the supply chain. They provide verifiable documentation, such as product certificates, warranties, and quality assurance records, protecting against counterfeits and ensuring traceability.
These examples demonstrate the versatility and importance of electronic certificates across different sectors. By leveraging electronic certificates, organizations can establish secure connections, authenticate individuals, protect sensitive data, and build trust in digital transactions and communications within their respective industries.
Future of Electronic Certificates
The future of electronic certificates holds promising advancements as technology continues to evolve and the need for secure digital transactions grows. Here are some potential developments in the future of electronic certificates:
- Blockchain Integration: Blockchain technology offers decentralized and immutable record-keeping capabilities. Integrating electronic certificates with blockchain can enhance the transparency, tamper resistance, and trustworthiness of digital identities and transactions.
- Mobile Device Integration: With the prevalence of smartphones and mobile devices, the future of electronic certificates lies in seamless integration with mobile platforms. Mobile wallets and digital identity applications can revolutionize the way electronic certificates are stored, managed, and presented, enhancing convenience and accessibility.
- Internet of Things (IoT) Security: As the number of internet-connected devices increases, electronic certificates will play a vital role in securing the IoT ecosystem. Authenticating and encrypting communication between IoT devices using electronic certificates will help safeguard data and maintain the integrity of IoT networks.
- Enhanced Biometric Integration: Incorporating biometric authentication, such as facial recognition or fingerprint scanning, into electronic certificates can further strengthen identity verification. This advancement can provide an additional layer of security, making electronic certificates even more resistant to fraudulent activities.
- Standardization and Interoperability: Efforts to standardize electronic certificate formats and protocols will simplify cross-platform and cross-industry implementations. This will allow for seamless interoperability of electronic certificates across different systems and enhance their widespread adoption.
- Continuous Authentication: Traditional electronic certificates have a fixed validity period. Future developments may involve real-time monitoring and continuous authentication, ensuring that the certificate holder’s identity and authorization are always verified throughout the duration of a digital transaction or interaction.
- Enhanced Trust in IoT Devices: As the number of IoT devices continues to grow, ensuring trust and security in these devices is paramount. Electronic certificates can play a pivotal role in verifying the authenticity and integrity of IoT devices, protecting against device spoofing and unauthorized access.
- Advancements in Quantum Computing: Quantum computing poses both challenges and opportunities for electronic certificates. While it may break current encryption algorithms, it also opens doors to new cryptographic techniques. Future electronic certificates will need to incorporate quantum-resistant algorithms to withstand potential quantum-based attacks.
The future of electronic certificates lies in their adaptability to emerging technologies and evolving security requirements. As the digital landscape evolves, electronic certificates will continue to play a crucial role in establishing trust, ensuring secure communication, and protecting against cyber threats in various industries and applications.