What is the ACID Database Model?
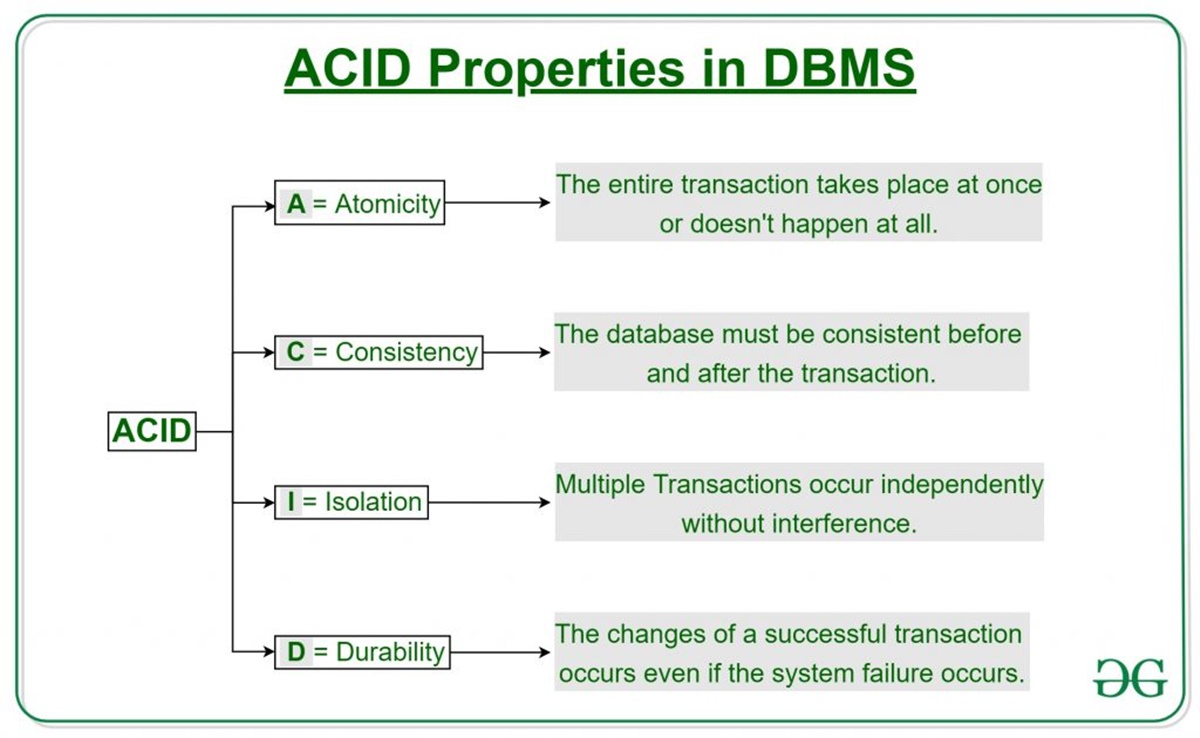
The ACID database model refers to a set of principles that ensure the reliability, consistency, and durability of data in a database system. ACID stands for Atomicity, Consistency, Isolation, and Durability, which are key properties that guarantee the integrity and correctness of data operations.
Atomicity means that a transaction is treated as a single, indivisible unit of work. It implies that all the operations within a transaction must be completed successfully for the changes to be permanently applied to the database. If any part of the transaction fails, the entire transaction is rolled back, ensuring that the database remains in a consistent state.
Consistency ensures that the database remains in a valid state before and after a transaction. It means that any changes made to the database must abide by predefined rules and constraints. For example, if there is a constraint that requires the total sum of a column to be a specific value, the database will enforce this constraint to maintain data integrity.
Isolation guarantees that concurrent transactions do not interfere with each other. When multiple transactions execute simultaneously, their operations are isolated from one another to prevent conflicts or inconsistencies. This is achieved through locking mechanisms and transaction isolation levels, ensuring that each transaction is unaware of the others until they are committed.
Durability ensures that once a transaction is committed, its changes are permanently stored and will survive any subsequent failures, such as system crashes or power outages. The changes are recorded in the database’s transaction log or other durable storage, allowing for recovery and restoring the database to a consistent state if necessary.
The ACID model provides a solid foundation for database systems, guaranteeing transactional consistency and reliability. It is widely used in traditional relational databases, where data integrity is of utmost importance, such as financial systems, inventory management, or healthcare applications.
The ACID Principles
The ACID principles, standing for Atomicity, Consistency, Isolation, and Durability, are fundamental concepts in the design and implementation of reliable and robust database systems. These principles ensure data integrity and reliability, making ACID-compliant databases suitable for critical applications where accuracy is paramount.
Atomicity: Atomicity guarantees that a transaction is treated as a single, indivisible unit of work. It ensures that all operations within a transaction are either fully completed or entirely rolled back. In other words, if any part of a transaction fails, all changes made by that transaction are undone, leaving the database in its original state. This property ensures that the database remains consistent and avoids any partial or incomplete modifications.
Consistency: Consistency ensures that the database remains in a valid state before and after a transaction. It enforces predefined rules, constraints, and relationships that ensure data integrity. For example, if a constraint requires a unique value for a certain attribute, the database ensures that this constraint is not violated. Consistency guarantees that only valid and allowed changes are made to the data, preserving its integrity and accuracy.
Isolation: Isolation ensures that concurrent transactions do not interfere with each other. It prohibits concurrent transactions from accessing or modifying the same data simultaneously in a way that could lead to undesirable effects like dirty reads, non-repeatable reads, or phantom reads. By enforcing isolation, ACID-compliant databases maintain the integrity and consistency of data, even when multiple transactions are executing concurrently.
Durability: Durability ensures that once a transaction is committed, its changes are permanently saved and will withstand subsequent failures or system crashes. This is typically achieved by writing the changes to stable storage, such as hard disks or flash memory, or by using transaction logs for recovery purposes. Durability guarantees that data will not be lost, enabling successful recovery and restoring the database to a consistent state in the event of a failure.
The ACID principles provide a solid foundation for maintaining data integrity and reliability in database systems. They ensure that changes to the data are handled consistently and reliably, even in the face of failures or concurrency. ACID-compliant databases are widely used in critical applications, such as financial systems, e-commerce platforms, and healthcare systems, where data accuracy and reliability are paramount.
Atomicity
In the context of the ACID database model, atomicity refers to the property of treating a transaction as a single, indivisible unit of work. It ensures that all operations within a transaction are either fully completed or entirely rolled back, maintaining the integrity and consistency of the database.
When a transaction is initiated, it can manipulate data by performing various operations such as inserts, updates, or deletions. These individual operations are grouped together as a logical unit of work, which is treated as atomic. Atomicity guarantees that if any part of a transaction fails, all changes made by that transaction are reverted, and the database is restored to its original state.
To ensure atomicity, database management systems (DBMS) use the concept of transaction logs. A transaction log keeps track of all operations performed within a transaction. Before modifying actual data, the DBMS logs the changes in the transaction log. If a failure occurs during the execution of a transaction, the DBMS can use the transaction log to roll back the changes and restore the database to a consistent state.
Atomicity provides several benefits to the database system and its users. It guarantees that data modifications are made in a consistent and predictable manner. If a transaction fails due to an error or interruption, atomicity ensures that the database is not left in an inconsistent state.
This property is particularly crucial in situations where data integrity is paramount, such as financial systems or online commerce platforms. For instance, consider an online payment transaction. If the payment process involves deducting money from one account and transferring it to another, atomicity ensures that either the entire transaction completes successfully, updating both accounts accordingly, or no changes are made at all.
Furthermore, atomicity simplifies error handling and recovery processes. In the event of a failure, the DBMS can roll back the transaction, preserving the integrity of the data. This can be especially important in mission-critical applications where data accuracy and reliability are vital requirements.
However, it’s worth noting that atomicity does not guarantee the correctness or accuracy of individual operations within a transaction. It solely ensures that the entire sequence of operations within a transaction is treated as an all-or-nothing operation, safeguarding the integrity and consistency of the database.
Consistency
The consistency principle in the ACID database model ensures that a database remains in a valid state before and after a transaction. It enforces predefined rules, constraints, and relationships that maintain data integrity and accuracy.
Consistency guarantees that any changes made to the database must adhere to the specified business rules and constraints. For example, if a table has a constraint that requires a unique value for a certain attribute, the database will enforce this constraint to prevent duplicate entries. If a transaction violates any of these rules, the entire transaction is rolled back, ensuring that the database remains consistent.
The consistency principle works in conjunction with other ACID principles, such as atomicity and isolation, to maintain the integrity of the data. By enforcing consistency, the database ensures that only valid changes are made, and the integrity of the data is preserved.
To provide consistency, the database management system (DBMS) enforces a set of predefined rules and constraints. These can include primary key constraints, foreign key constraints, unique constraints, and check constraints. These rules are defined when creating the database schema, and the DBMS ensures that all data modifications comply with these rules.
For example, consider a banking application where transferring funds from one account to another requires that the total balance remains unchanged. The DBMS enforces this consistency constraint by not allowing a transaction to proceed if it would violate this rule. If an attempted transaction would result in a negative balance or an incorrect total balance, the consistency principle ensures that the transaction is rolled back, preventing any inconsistencies.
Consistency is critical in various domains, such as financial systems, inventory management systems, and e-commerce platforms. By maintaining data integrity and accuracy, consistency ensures the reliability and correctness of the information stored in the database.
However, it’s important to note that consistency in the ACID model is different from consistency in eventual consistency models, such as the BASE model. ACID consistency focuses on immediate consistency within a transaction, whereas eventual consistency models place more emphasis on distributed systems and the synchronization of data across multiple nodes.
Overall, the consistency principle ensures that the database remains in a valid and consistent state, adhering to predefined rules and constraints. It guarantees that any changes to the database are made in a manner that preserves data integrity and accuracy.
Isolation
The isolation principle in the ACID database model ensures that concurrent transactions do not interfere with each other, maintaining the integrity and consistency of the database. It enables multiple transactions to execute simultaneously without causing conflicts or inconsistencies.
Isolation provides the illusion that each transaction is executed in isolation, unaware of other concurrently executing transactions. It prevents interference between transactions through various mechanisms, such as locks and transaction isolation levels.
Concurrency in database systems introduces the possibility of conflicts when multiple transactions access and modify the same data simultaneously. These conflicts can lead to issues such as dirty reads, non-repeatable reads, and phantom reads.
The isolation principle ensures that the outcome of concurrent operations is the same as if they were executed sequentially, one after another. It guarantees that the changes made by one transaction are not visible to other transactions until the changes are committed.
Transaction isolation levels, such as Read Uncommitted, Read Committed, Repeatable Read, and Serializable, are used to control the level of isolation provided by the database management system (DBMS). These isolation levels define the visibility of changes made by concurrent transactions.
For example, at the Read Committed isolation level, a transaction can only see changes committed by other transactions. It avoids dirty reads by ensuring that only committed data is visible. At a higher level, such as Serializable, transactions are executed completely isolated, guaranteeing the highest level of data consistency but potentially impacting performance due to locking.
The isolation principle helps ensure that concurrent transactions do not interfere with each other, maintaining data integrity and consistency. By enforcing proper isolation, the ACID model allows multiple transactions to execute simultaneously without compromising data accuracy.
However, it’s important to strike a balance between isolation and performance. Strong isolation levels, such as Serializable, might result in increased locking, potentially affecting the scalability and concurrency of the database system. Hence, the appropriate isolation level should be chosen based on the specific requirements of the application.
Overall, the isolation principle in the ACID model provides a crucial mechanism for handling concurrent transactions while maintaining data integrity. It guarantees that the execution of multiple transactions remains isolated from each other, preventing conflicts and ensuring the consistency of the database.
Durability
In the context of the ACID database model, durability refers to the property that ensures once a transaction is committed, its changes are permanently saved and will withstand subsequent failures or system crashes.
The durability principle guarantees that the changes made to the database by committed transactions are durable and will not be lost, even in the event of power outages, hardware failures, or other types of system crashes. This durability is achieved by persistently storing the changes to secondary storage, such as hard drives or solid-state drives, or using transaction logs for recovery purposes.
When a transaction is committed, the DBMS ensures that all changes made by that transaction are written to stable storage, making them durable even if the system crashes. The durable storage ensures that the changes will survive any subsequent failures and can be recovered when the system is back online. Durability is a critical property for databases, as it guarantees that the data remains intact and accessible after a failure without any loss of information.
Durability is typically achieved by utilizing transaction logs, which record the changes made by each transaction in a sequential manner. These logs serve as a fallback mechanism that can be used to recover the database to a consistent state in the event of a failure. By replaying the logged changes, the DBMS can restore the data to its state at the time of the last successful checkpoint or backup.
Ensuring durability is vital for databases that handle important and sensitive data, such as financial systems, healthcare records, or critical infrastructure management. In these domains, even a small loss of data or an inability to recover from failures could have severe consequences.
It is worth noting that achieving durability may involve a trade-off with system performance. Writing changes to stable storage can incur additional overhead, as it involves disk I/O operations that are slower compared to in-memory operations. Therefore, the durability level can be adjusted based on the specific requirements of the application and the importance of the data being stored.
ACID vs BASE
The ACID (Atomicity, Consistency, Isolation, Durability) and BASE (Basically Available, Soft state, Eventually consistent) models represent two different approaches to database design and management, each suited for specific types of applications and use cases.
The ACID model, as discussed earlier, emphasizes strong consistency and reliability. It ensures that a transaction is correctly processed and that the database remains in a valid state at all times. ACID-compliant databases are commonly used in areas where data integrity and accuracy are critical, such as financial systems or healthcare applications.
On the other hand, the BASE model is designed for systems that prioritize high availability and scalability over strong consistency. BASE provides a more relaxed approach to consistency, targeting distributed systems and applications with large-scale data and high concurrency.
The key principles of the BASE model are:
- Basically Available: The system guarantees a high level of availability for users, even in the presence of failures or concurrent access. It sacrifices strong consistency for availability.
- Soft state: The state of the system may change over time, even without input, due to eventual consistency. Soft state allows for transient inconsistencies that can be resolved over time.
- Eventually consistent: While the system may not provide immediate consistency, it eventually achieves consistency over time. It acknowledges and allows for temporary inconsistencies across distributed nodes.
BASE systems often rely on techniques like replication, partitioning, and distributed data storage to achieve high scalability and fault tolerance. By allowing for eventual consistency, these systems can handle large amounts of data and provide high availability under heavy loads.
When deciding whether to use the ACID or BASE model, it’s important to consider the specific requirements of the application. ACID is suitable for scenarios where consistency and reliability are essential, but it may come at the cost of scalability and availability. BASE, on the other hand, is a good fit for applications that prioritize availability and partition tolerance over immediate consistency.
It’s worth mentioning that the choice between ACID and BASE is not always binary. Many real-world systems employ a hybrid approach, combining elements of both models to strike a balance between consistency, availability, and scalability. This allows for tailored solutions that meet the specific needs of the application and its users.
ACID Compliance in Different Database Systems
The ACID (Atomicity, Consistency, Isolation, Durability) principles serve as a foundation for ensuring data integrity and reliability in database systems. While ACID compliance is widely associated with traditional relational databases, it can also be found in other types of databases, albeit with some variations and trade-offs.
Traditional Relational Database Management Systems (RDBMS) like Oracle Database, MySQL, and PostgreSQL are known for their strong ACID compliance. These systems adhere strictly to the ACID principles, providing a high level of transactional consistency, isolation, and durability. Their robustness and reliability make them suitable for applications that require strict data integrity, such as financial systems or healthcare databases.
NoSQL databases, which are designed to handle large-scale distributed data and provide high availability, often take a more relaxed approach to ACID compliance. While NoSQL databases do not fully adhere to ACID principles, they offer various degrees of guarantees for consistency, isolation, and durability, depending on the specific database model and configuration.
For instance, document-oriented NoSQL databases like MongoDB or CouchDB trade immediate consistency for better scalability and availability. These databases often follow the BASE (Basically Available, Soft state, Eventually consistent) model, allowing for eventual consistency and eventual durability. However, they do provide some level of consistency and isolation through mechanisms like read and write quorums or consistency levels.
Graph databases, such as Neo4j, focus on traversing and analyzing highly connected data. While these databases prioritize data relationships, they also provide transactional guarantees, ensuring atomicity and consistency. However, the degree of isolation and durability may vary based on the specific graph database implementation.
Key-value stores, like Redis or Amazon DynamoDB, typically prioritize high availability and partition tolerance over strong consistency. These databases often sacrifice strict consistency in favor of eventual consistency and provide options for controlling consistency levels. However, they still maintain some level of durability by persisting data to disk or taking regular backups.
Pros and Cons of the ACID Model
The ACID (Atomicity, Consistency, Isolation, Durability) model provides a solid foundation for ensuring data integrity and reliability in database systems. However, like any approach, it has both advantages and disadvantages that should be considered when designing and implementing database solutions.
Let’s explore the pros and cons of the ACID model:
Pros:
- Data Integrity: The ACID model guarantees transactional consistency and adherence to predefined rules and constraints, ensuring data integrity and accuracy.
- Reliability: ACID-compliant databases provide a high level of reliability and robustness. The durability principle ensures that committed changes are permanently saved and survive system failures.
- Consistency: The ACID model ensures strong consistency within transactions, preventing partial or inconsistent modifications to the data.
- Transaction Control: Atomicity and isolation allow for effective transactional control, ensuring that transactions are treated as indivisible units of work and preventing interference between concurrent transactions.
- Domain Suitability: ACID compliance is suitable for applications where data accuracy and correctness are critical, such as financial systems, healthcare databases, or inventory management.
Cons:
- Performance Overhead: The strict ACID guarantees can introduce performance overhead. Locking mechanisms and synchronization mechanisms may impact concurrency and scalability.
- Complexity: Ensuring ACID compliance can make database design and development more complex, requiring careful consideration of transaction boundaries, isolation levels, and recovery mechanisms.
- Less Availability: Strong consistency and durability requirements can impact availability. ACID-compliant systems may need to wait for locks to be released or rely on disk I/O, potentially affecting responsiveness and availability under high loads.
- Not Ideal for all Use Cases: The ACID model may not be the best fit for all applications. Systems that prioritize high availability, scalability, or eventual consistency might require alternative approaches like BASE or eventual consistency models.
When considering the adoption of the ACID model, it is essential to weigh the benefits against the potential trade-offs. While ACID compliance provides strong guarantees for data integrity and reliability, it may require careful tuning and balancing of performance and availability, especially in highly concurrent or distributed environments.
Use Cases for the ACID Model
The ACID (Atomicity, Consistency, Isolation, Durability) model is well-suited for various use cases where data integrity and reliability are of utmost importance. Let’s explore some common scenarios where the ACID model is beneficial:
Financial Systems: ACID compliance is crucial in financial systems that handle transactions, account balances, and sensitive customer information. Guaranteeing atomicity ensures that financial transactions are processed accurately, maintaining the consistency of account balances and preventing unauthorized changes.
Healthcare Applications: Healthcare systems deal with critical patient data, medical records, and sensitive information. ACID compliance ensures that medical transactions, such as patient admissions, diagnoses, or prescription updates, are recorded accurately and consistently, guaranteeing the integrity and confidentiality of patient data.
Inventory Management: In industries like retail and manufacturing, inventory management systems must maintain accurate stock levels, orders, and deliveries. The ACID model ensures that inventory updates are performed correctly and consistently, preventing issues like overselling, incorrect stock counts, or incorrect order fulfillment.
Transactional Systems: Any system that relies on transactional consistency, such as e-commerce platforms or banking applications, benefits from the ACID model. ACID guarantees ensure that customers’ purchases, refunds, and order updates are processed correctly and consistently, providing a seamless and reliable transactional experience.
Enterprise Resource Planning (ERP): ERP systems integrate various departments and processes within an organization. The ACID model ensures that updates across different modules, such as finance, procurement, and human resources, are coordinated correctly and consistently, maintaining data integrity and preventing discrepancies or data corruption.
Regulatory Compliance: Industries with strict regulatory requirements, such as finance, healthcare, or government agencies, often rely on the ACID model to ensure compliance. ACID guarantees provide a foundation for data integrity audits, traceability, and adherence to regulatory standards.
While the ACID model is highly beneficial in the mentioned use cases, it’s important to note that not all applications require strict ACID compliance. For systems with different priorities, such as high scalability, availability, or distributed architectures, alternative approaches like BASE or eventual consistency models may be more suitable.
To determine whether the ACID model is the right fit for a particular use case, organizations should evaluate their specific requirements, scalability needs, and the trade-offs associated with ACID compliance.