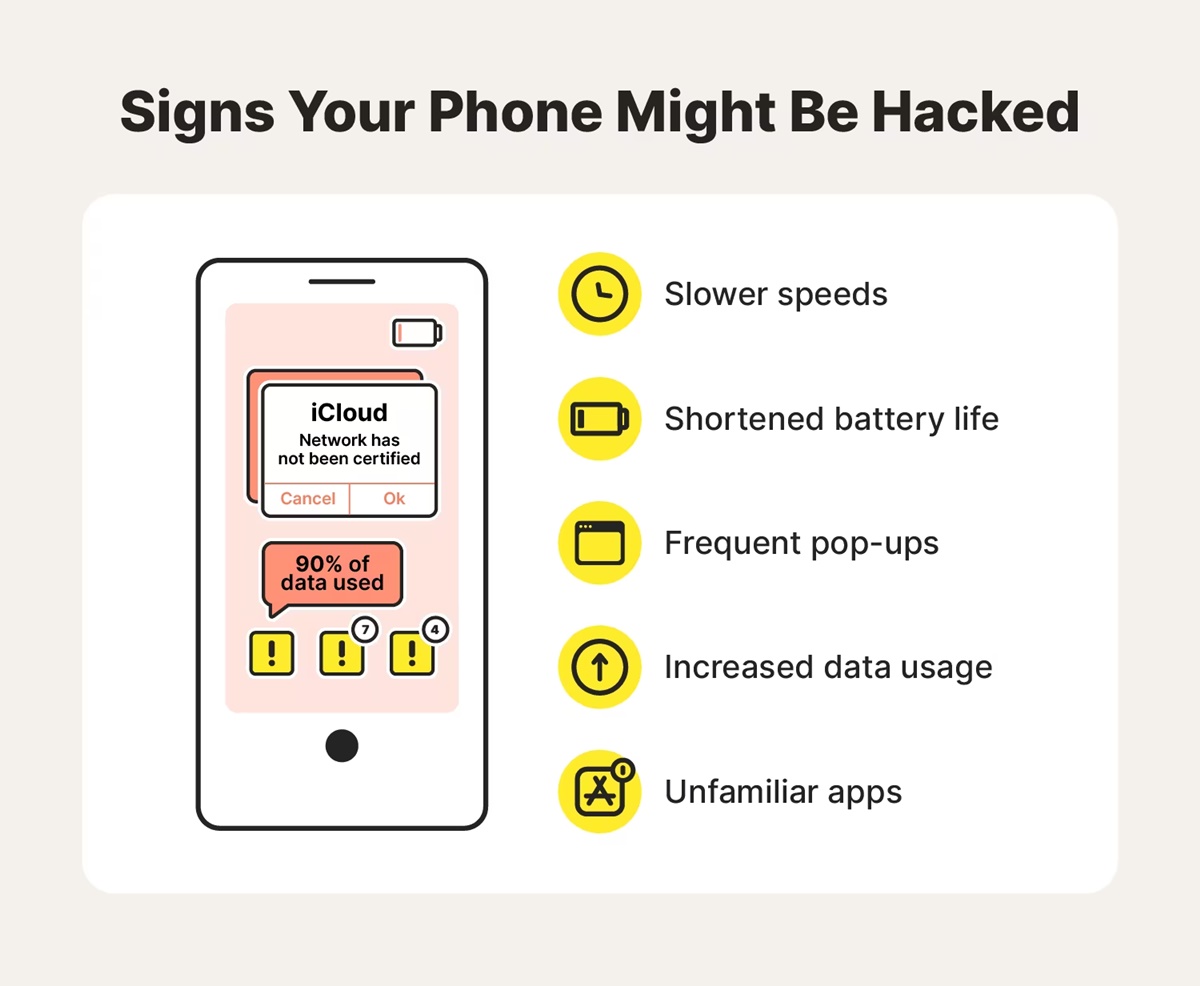
How to Identify if Your Phone Was Hacked
Discovering that your phone has been hacked can be a distressing experience. However, being proactive and vigilant can help you identify if your device has been compromised. Here are some key signs to look out for:
- Unusual Battery Drain: If your phone’s battery life has suddenly decreased significantly, it could be a sign of a hacking attempt. Malicious software running in the background can drain your battery faster than usual.
- Strange Behavior: Is your phone acting strangely? Random restarts, unexpected pop-ups, or unusual error messages could indicate that your device has been hacked.
- Excessive Data Usage: If you notice a sudden surge in data usage, it may be due to a hacker using your phone to transmit or receive data without your knowledge.
- Unfamiliar Apps: Check for any unfamiliar apps that were not installed by you. These apps could be malicious and have been installed by hackers to gain access to your personal information.
- Increased Data Traffic: A sudden increase in network activity, such as frequent data transfers or unexpectedly high data usage during idle periods, could signify that your phone has been compromised.
While these signs may indicate that your phone has been hacked, it’s important to remember that they can also be caused by other factors. Therefore, if you notice any of these signs, it’s advisable to further investigate and take the necessary steps to secure your device.
Immediate Steps to Take When You Suspect Your Phone has been Hacked
Discovering that your phone may have been hacked can be alarming, but taking immediate action is crucial in protecting your personal information. Here are the steps you should take when you suspect your phone has been compromised:
- Disconnect from the Internet: As soon as you suspect a hack, turn off your Wi-Fi and mobile data to disconnect your phone from the network. This will help prevent further unauthorized access to your device.
- Change Passwords: Secure your online accounts by changing the passwords for your email, social media, and banking apps. This step is crucial since hackers may have gained access to your login credentials.
- Enable Airplane Mode: Enabling airplane mode can further isolate your device from any potential malicious activities. It prevents unauthorized communication and limits potential damage.
- Scan for Malware: Run a malware scan on your device using reputable antivirus software. This will help identify any malicious apps or software that may have been installed without your knowledge.
- Inform Your Contacts: Notify your contacts, friends, and family about the hacking incident. This will help prevent the spread of any malicious messages or scams that may have originated from your compromised device.
Remember to stay calm and avoid clicking on any suspicious links or emails during this process. It is essential to prioritize your digital security and take the necessary steps to regain control of your phone.
Changing Your Passwords
If you suspect that your phone has been hacked, one of the most critical steps you need to take is changing your passwords. By doing so, you can prevent unauthorized access to your personal accounts and protect your information from further compromise. Here’s what you need to do:
- Start with Critical Accounts: Begin by changing the passwords for your email, online banking, and social media accounts. These accounts often contain sensitive information and are prime targets for hackers.
- Create Strong Passwords: When creating new passwords, make sure they are strong and unique. Use a combination of upper and lowercase letters, numbers, and special characters. Avoid using common words or easily guessable information like your birthday or pet’s name.
- Use a Password Manager: Consider using a reputable password manager application to generate and store complex passwords. This will help you remember and manage multiple strong passwords without compromising security.
- Enable Two-Factor Authentication: Take advantage of two-factor authentication (2FA) wherever possible. 2FA adds an extra layer of security by requiring a second form of verification, such as a fingerprint, face recognition, or a unique code sent to your phone.
- Update Security Questions: Review and update your security questions for added protection. Avoid using common or predictable answers and opt for more obscure and unique responses.
- Regularly Change Passwords: Get into the habit of changing your passwords every few months or whenever you suspect a security breach. Regular changes reduce the probability of a successful hack and enhance your overall online security.
Remember to avoid using the same password across multiple accounts, as this can further compromise your digital security. By regularly changing passwords and creating strong and unique combinations, you are proactively safeguarding your personal information.
Update your Phone Software
Keeping your phone’s software up to date is crucial for maintaining its security and protecting it against potential hacks. Software updates often include bug fixes and security patches that address known vulnerabilities. Here’s why and how you should update your phone’s software:
Why Update:
1. Security Fixes: Hackers are constantly discovering new ways to exploit vulnerabilities in operating systems and apps. Software updates help patch these vulnerabilities, making it more difficult for hackers to gain unauthorized access to your device.
2. Better Performance: Software updates often introduce optimizations and improvements, resulting in a smoother and more efficient user experience. Updating your phone’s software can help improve its overall performance and responsiveness.
3. New Features: Alongside security enhancements, software updates may also introduce new features, functionality, and improvements to existing apps. By keeping your phone’s software up to date, you can take advantage of the latest features and enhancements.
How to Update:
1. Check for Updates: Go to your phone’s Settings and look for the “Software Update” or “System Update” option. Tap on it to check for any available updates.
2. Install Updates: If an update is available, follow the on-screen instructions to download and install it. Ensure that your phone is connected to a stable Wi-Fi network, as updates can be large in size.
3. Automatic Updates: You can also enable the automatic update feature, which allows your phone to download and install software updates automatically. This ensures that your device is always up to date without manual intervention.
Remember to back up your device before installing any updates, as a backup will help protect your data in case of any unforeseen issues during the update process.
By regularly updating your phone’s software, you can stay ahead of potential security risks and enjoy the latest features and improvements offered by your device’s manufacturer.
Remove Suspicious Apps from your Phone
If you suspect that your phone has been hacked, it’s crucial to identify and remove any suspicious apps from your device. Some malicious apps may have been installed without your knowledge and could compromise your privacy and security. Follow these steps to remove suspicious apps from your phone:
1. Review Installed Apps:
Go through the list of installed apps on your phone and look for any unfamiliar or suspicious ones. Pay particularly close attention to apps that you don’t remember downloading or ones with generic or nonsensical names.
2. Check Permissions:
Review the permissions granted to each app on your device. Suspicious apps often request excessive permissions that are unnecessary for their functionality. If you notice an app with overly intrusive or suspicious permissions, it is best to uninstall it.
3. Research the App:
If you are unsure about an app’s legitimacy, do some research online. Look for reviews and information from reputable sources to determine if the app is trustworthy. If you find negative reviews or reports of malicious behavior, it’s advisable to uninstall the app immediately.
4. Uninstall Suspicious Apps:
To uninstall an app, go to the Settings menu on your phone, select “Apps” or “Applications,” and then locate the suspicious app. Tap on it and select the option to uninstall. Follow the on-screen instructions to remove the app from your device.
5. Clear Cached Data:
After uninstalling suspicious apps, it’s a good idea to clear the cached data on your device. This step can help remove any remnants of the malicious app and ensure a clean, secure system. You can find this option in the “Storage” or “Storage & Cache” section of your device settings.
Regularly reviewing and removing suspicious apps from your phone is an essential step in maintaining your device’s security. By being diligent and proactive, you can protect your personal information and minimize the risk of further compromise.
Enable Two-Factor Authentication
Two-Factor Authentication (2FA) is an additional layer of security that can significantly enhance the protection of your accounts and devices. By enabling 2FA, you add an extra step to the login process, making it more difficult for hackers to gain unauthorized access to your personal information. Here’s why and how you should enable 2FA:
Why Enable 2FA:
1. Added Security: With traditional login methods, a password alone is often the only requirement to access your accounts. However, if your password is compromised, it poses a significant risk. 2FA adds an extra layer of security by requiring a second factor, such as a unique code sent to your phone, a fingerprint scan, or a trusted device.
2. Protection Against Password Theft: 2FA helps mitigate the risk of password theft. Even if a hacker manages to obtain your password, they would still need the second factor, which is typically something only you possess, such as your phone or a biometric identifier.
3. Prevents Unauthorized Access: Enabling 2FA ensures that only authorized individuals can access your accounts. Even if someone manages to obtain your password, they won’t be able to log in without the second authentication factor.
How to Enable 2FA:
1. Check Account Settings: Go to the account settings of the app or website you want to enable 2FA for. Look for the security or two-factor authentication options.
2. Select 2FA Method: Choose the 2FA method that suits your preferences and the options available. This may include receiving a unique code via SMS, using an authenticator app, or utilizing biometric authentication.
3. Follow Setup Instructions: Follow the on-screen instructions to set up 2FA for your account. This often involves linking your phone number, installing an authenticator app, or registering your biometric information.
4. Save Backup Codes: Some 2FA methods allow you to generate backup codes. Ensure that you save these codes in a secure location, as they can be used to regain access to your account if you lose or replace your device.
Remember to enable 2FA for all your critical accounts, such as email, social media, and financial services. By doing so, you significantly enhance the security of your accounts and protect your personal information from unauthorized access. Keep in mind that while 2FA provides an added layer of security, it is still important to use strong, unique passwords for each of your accounts.
Check for Unusual Data Usage
Monitoring your data usage can help you identify any unusual activity on your phone that may indicate a hacking attempt or unauthorized access. If you notice a sudden spike in data usage, it’s important to investigate further to protect your privacy and security. Here’s what you can do to check for unusual data usage:
1. Monitor Data Usage:
Check your phone’s settings or data usage section to monitor your data usage. Most smartphones have built-in tools that allow you to track how much data you consume over a specific period.
2. Understand Normal Usage:
Get familiar with your typical data consumption patterns. This includes knowing how much data you usually consume for activities such as browsing the internet, streaming videos, or using social media.
3. Look for Unexplained Spikes:
Review your data usage history to identify any sudden, unexplained spikes in data consumption. Pay close attention to days or periods where the usage is significantly higher than your usual patterns.
4. Identify the Culprit:
If you notice unusual data usage, investigate further to determine the cause. It could be due to a malicious app running in the background, unauthorized data transfers, or excessive advertising and tracking activities.
5. Check App Data Usage:
Review the data usage of individual apps on your phone. This will help you pinpoint specific apps that may be consuming an abnormal amount of data. Look for any apps that you do not recognize or ones that have unexpectedly high data usage.
6. Uninstall Suspicious Apps:
If you find any suspicious apps consuming excessive data or that you do not recognize, uninstall them immediately. These apps could be malicious and may be using your data for unauthorized purposes.
7. Reset Data Usage Statistics:
To accurately monitor your data usage going forward, reset the data usage statistics on your phone. This will provide a fresh baseline to track any future spikes or unusual activity.
By regularly checking for unusual data usage, you can quickly identify any potential hacking attempts or unauthorized access to your device. Taking prompt action is crucial in preventing further compromise of your personal information.
Secure Your Phone’s Wi-Fi Connection
Securing your phone’s Wi-Fi connection is essential to protect your device and your personal information from potential hacking attempts. Hackers can exploit vulnerabilities in unsecured Wi-Fi networks to gain unauthorized access to your device or intercept your data. Here are some steps you can take to secure your phone’s Wi-Fi connection:
1. Use a Strong and Unique Wi-Fi Password:
Set a strong and unique password for your Wi-Fi network. Avoid using common phrases, easily guessable information like your address or date of birth, and change it regularly to maintain security.
2. Enable Wi-Fi Encryption:
Ensure that your Wi-Fi network is encrypted with the WPA2 (Wi-Fi Protected Access 2) security protocol. This encrypts the data transmitted between your phone and the Wi-Fi router, making it harder for hackers to intercept and decipher the information.
3. Change the Default Router Admin Password:
Many Wi-Fi routers come with default administrator passwords, which are easily accessible to hackers. Change the default admin password to a strong and unique one, providing an additional layer of protection for your Wi-Fi network.
4. Disable Remote Management:
Disable remote management capabilities on your Wi-Fi router. This prevents unauthorized individuals from remotely accessing and controlling your router’s settings, minimizing the risk of any unwanted changes.
5. Enable Network Encryption:
Whenever possible, use websites and online services that have encryption enabled. Look for the “https://” prefix in the website address, indicating that your connection is secured with SSL/TLS encryption.
6. Be Cautious with Public Wi-Fi:
Avoid connecting to public Wi-Fi networks unless necessary. Public Wi-Fi networks are often unsecured, making your device vulnerable to hacking attempts. If you must connect to a public Wi-Fi network, utilize a Virtual Private Network (VPN) for an added layer of security.
7. Disable Automatic Wi-Fi Connections:
Disable your phone’s automatic connection to open or unsecured Wi-Fi networks. This prevents your device from connecting to unknown networks that could potentially be set up by hackers to capture your data.
By implementing these measures, you can significantly enhance the security of your phone’s Wi-Fi connection, reducing the risk of unauthorized access and protecting your personal information from potential threats.
Install a Reliable Antivirus App
Installing a reliable antivirus app on your phone is crucial for protecting your device and data from potential malware, viruses, and other security threats. Antivirus software scans, detects, and removes malicious software that may have been installed without your knowledge. Here’s why and how you should install a reliable antivirus app:
Why Install an Antivirus App:
1. Malware Protection: Malware can pose serious threats to your phone’s security and privacy. Antivirus apps provide real-time protection against malware, preventing unauthorized access and data breaches.
2. App and File Scanning: Antivirus apps scan apps, files, and downloads for any malicious content. This helps identify and remove potentially harmful files before they can cause damage to your device or compromise your personal information.
3. Web Browsing Protection: Some antivirus apps offer web browsing protection by detecting and blocking malicious websites and phishing attempts. This ensures that you can safely browse the internet without falling victim to scams or malicious activities.
How to Install an Antivirus App:
1. Research and Choose a Reliable App: Look for reputable antivirus apps in your app store. Read user reviews and opt for well-established apps with a proven track record of quality and effectiveness.
2. Download and Install the App: Visit your device’s app store, search for the chosen antivirus app, and follow the on-screen instructions to download and install it. Ensure that you download the official version from a trusted source.
3. Configure App Settings: After installation, open the antivirus app and configure the settings according to your preferences. Enable features such as real-time scanning, automatic updates, and scheduled scans for optimal protection.
4. Keep the App Updated: Regularly check for updates to your antivirus app. Developers release updates to address new security threats and provide enhanced protection. Keeping your antivirus app up to date ensures that your device is safeguarded against the latest risks.
Remember that while antivirus apps are an essential security measure, they should not be the only line of defense. Practice safe browsing habits, download apps from trusted sources, and stay vigilant against potential threats.
By installing a reliable antivirus app and following best practices for mobile security, you can effectively protect your phone and personal data from various cyber threats.
Recovering Your Data After a Phone Hack
Experiencing a phone hack can be a distressing situation, but it’s important to act quickly and take steps to recover your data. While the process may vary depending on the extent of the hack, here are some general steps you can take to regain control and recover your data:
1. Disconnect from the Network:
As soon as you suspect a hack, disconnect your device from the internet. Turn off Wi-Fi and mobile data to prevent any further unauthorized access or data transmission.
2. Assess the Damage:
Take stock of what data may have been compromised or lost. Determine the extent of the hack by assessing the type of information accessed or any changes made to your accounts or settings.
3. Change Passwords and Enable 2FA:
Change the passwords for all your accounts, starting with critical ones such as email, social media, and banking. Enable Two-Factor Authentication (2FA) wherever possible for added security.
4. Contact Support:
If the hack affected specific accounts, contact the support teams of those platforms or services. Inform them of the situation and follow their instructions to secure your accounts and regain access.
5. Restore from Backup:
If you regularly back up your phone, restore your device to a previous backup point. This can help recover lost or compromised data, returning your device to a previous, secure state.
6. Scan for Malware and Remove:
Run a comprehensive scan with a reputable antivirus app to detect and remove any remaining malware from your device. This step ensures a clean and secure system going forward.
7. Monitor Accounts and Report Suspicious Activity:
Keep a close eye on your accounts for any abnormal activity. Report any suspicious transactions or changes to the respective platforms and financial institutions to protect yourself from further harm.
8. Strengthen Security Measures:
Review and enhance your device’s security measures. Update your operating system and apps to the latest versions, enable automatic updates, and install reputable security apps to prevent future hacking attempts.
Recovering from a phone hack can be a complex and time-consuming process. It’s important to be patient and thorough in your recovery efforts, ensuring the safety of your data and the security of your device.
How to Prevent Future Hacking Incidents
Preventing future hacking incidents is crucial for safeguarding your personal information and maintaining the security of your phone. By implementing these preventive measures, you can reduce the risk of falling victim to hacking attempts. Here’s what you can do:
1. Keep Your Software Updated:
Regularly update your phone’s operating system, apps, and antivirus software. Software updates often include security patches that address known vulnerabilities. Staying up to date ensures that you have the latest protections against emerging threats.
2. Use Strong and Unique Passwords:
Create strong, complex passwords that are unique for each of your accounts. Use a combination of upper and lowercase letters, numbers, and special characters. Avoid using easily guessable information or common phrases. Consider using a password manager to securely store and generate strong passwords.
3. Enable Two-Factor Authentication (2FA):
Utilize the additional layer of security provided by 2FA. Enable 2FA on all your accounts that offer this feature. This will require a second form of verification, such as a unique code sent to your phone, to access your accounts.
4. Be Cautious of Phishing Attempts:
Be wary of suspicious emails, messages, or calls asking for personal or financial information. Avoid clicking on links or downloading attachments from unknown sources. Verify the authenticity of requests before providing any sensitive information.
5. Install Apps from Trusted Sources:
Download and install apps only from reputable sources such as official app stores. Avoid sideloading apps from unknown sources, as they may contain malware or malicious code.
6. Be Mindful of Public Wi-Fi:
Avoid connecting to unsecured public Wi-Fi networks, especially when accessing sensitive information or making financial transactions. If you must use public Wi-Fi, consider using a Virtual Private Network (VPN) for encrypted and secure internet browsing.
7. Regularly Backup Your Data:
Regularly backup your device’s data to an external storage device or cloud storage. This ensures that in the event of a hack or data loss, you can quickly restore your information without significant impact.
8. Educate Yourself about Security Best Practices:
Stay informed about the latest security threats and best practices to protect your device. Keep yourself updated on common hacking techniques and scams, so you can recognize and avoid them. Regularly seek credible sources of information and resources for security education.
By actively implementing these preventive measures, practicing good digital hygiene, and staying vigilant, you can significantly reduce the risk of future hacking incidents and enhance the overall security of your phone and personal information.