Understanding the Importance of Incident Response
With the rapidly evolving threat landscape, it has become imperative for organizations to prioritize effective incident response. In today’s digital age, cyber threats have the potential to disrupt operations, compromise sensitive data, and cause significant financial and reputational damage.
An incident response plan serves as a proactive approach to detect, respond to, and mitigate the impact of cyber incidents. It ensures swift action and minimizes the duration and severity of an attack. Understanding the importance of incident response is crucial for organizations of all sizes and sectors.
One key reason to prioritize incident response is the rising frequency and sophistication of cyber attacks. Hackers are constantly developing new techniques to breach security defenses, making it essential for organizations to have measures in place to detect and respond to incidents effectively.
Another critical factor is the potential legal and regulatory consequences. Organizations operating in highly regulated industries, such as healthcare or finance, face compliance requirements that mandate establishing incident response capabilities. Failing to comply with these regulations can result in severe penalties and legal repercussions.
The financial impact of cyber incidents cannot be overlooked either. The costs associated with data breaches, ransom demands, and service disruptions can be staggering. Incident response helps organizations minimize the financial losses by containing and mitigating the incident promptly, reducing the overall impact on both revenue and reputation.
Furthermore, incident response is crucial for preserving customer trust and loyalty. In the event of a cyber incident, organizations need to demonstrate their ability to handle the situation effectively, assuring customers that their data is being protected. Timely incident response builds confidence and maintains the integrity of the business.
Moreover, incident response enhances internal security and strengthens overall cybersecurity posture. Through continuous monitoring and analysis, incident response allows organizations to identify vulnerabilities and develop strategies to improve their defenses, preventing future incidents.
Assessing the Current Cyber Threat Landscape
Assessing the current cyber threat landscape is a critical step in developing an effective incident response plan. By understanding the evolving nature of cyber threats, organizations can better prepare and respond to potential attacks.
The first aspect of assessing the cyber threat landscape is to stay informed about the latest trends and emerging threats. This involves monitoring industry reports, threat intelligence feeds, and collaborating with external cybersecurity partners. By staying up to date, organizations can proactively adapt their defenses and stay one step ahead of cybercriminals.
Another vital component of threat assessment is analyzing the specific threat vectors that are relevant to the organization. Threat vectors are the pathways through which cyber attacks can infiltrate systems. These can include email phishing, social engineering, malicious websites, vulnerable applications, or even insider threats. Understanding the most common and high-risk threat vectors allows organizations to focus their efforts on preventative measures and incident response planning.
Furthermore, it is crucial to assess the level of sophistication and persistence demonstrated by cyber threat actors. This includes both individual hackers and organized cybercriminal groups. By understanding their tactics, techniques, and procedures (TTPs), organizations can tailor their defense strategies to adequately detect and respond to potential attacks.
Another key aspect of cyber threat assessment is evaluating the potential impact and consequences of different types of attacks. For instance, ransomware attacks can encrypt critical data and cripple business operations, while data breaches can result in the exposure of sensitive customer information. By understanding the potential impact, organizations can prioritize their incident response efforts and allocate resources effectively.
Lastly, organizations should consider the geopolitical and industry-specific factors that might impact their cybersecurity. This includes factors like regional regulations, geopolitical tensions, and industry-specific threat actors. This assessment helps organizations identify any additional risks or unique challenges they may face and develop appropriate incident response plans.
Identifying Potential Cyber Attacks and Threat Vectors
Identifying potential cyber attacks and threat vectors is a crucial step in developing an effective incident response plan. It involves understanding the methods and techniques that cybercriminals use to compromise systems and exploit vulnerabilities.
One of the most common threat vectors is social engineering, where attackers manipulate individuals into divulging sensitive information or performing actions that compromise security. This can include phishing emails, phone calls pretending to be from reputable organizations, or even physical attempts to gain unauthorized access. By educating employees about social engineering tactics and implementing safeguards, organizations can minimize the risk of such attacks.
Another prevalent threat vector is malware, which includes viruses, worms, Trojans, and ransomware. Malware can be spread through malicious email attachments, infected websites, or compromised software. Keeping systems updated with the latest security patches, using reputable antivirus software, and implementing email filtering can help identify and mitigate malware-based attacks.
Web application vulnerabilities present another significant threat vector. Attackers exploit weaknesses in web applications, such as cross-site scripting (XSS) or SQL injection, to gain unauthorized access or steal sensitive data. Regular security audits, code reviews, and penetration testing can help identify and address these vulnerabilities, reducing the risk of breaches.
Insider threats also pose a significant risk. These can be employees or contractors who abuse their access privileges, intentionally or accidentally. Implementing strong access controls, monitoring tools, and conducting regular security awareness training can help organizations detect and mitigate insider threats.
Mobile devices are another potential attack vector. As mobile technology continues to advance, attackers take advantage of insecure apps, weaknesses in operating systems, or phishing attacks targeting mobile users. Implementing mobile device management (MDM), enforcing strong passwords, and educating users about safe mobile practices are essential to protect against mobile-based threats.
Network vulnerabilities are an additional threat vector that attackers exploit. Weak network configurations, unsecured wireless access points, and outdated network devices can provide entry points for cybercriminals. Regular vulnerability assessments, penetration testing, and network segmentation can help identify and address these vulnerabilities, reducing the risk of network-based attacks.
Establishing an Incident Response Team
Establishing an incident response team is a crucial aspect of building an effective incident response capability within an organization. This dedicated team is responsible for detecting, investigating, and responding to cyber incidents promptly and efficiently.
The first step in forming an incident response team is identifying the key stakeholders and roles required to effectively respond to incidents. This typically includes representatives from IT, security, legal, communications, and executive management. Each team member brings a unique perspective and expertise, ensuring a well-rounded response during an incident.
Once the team is assembled, it is essential to define clear roles and responsibilities for each member. This ensures that everyone understands their specific functions and enables effective coordination during an incident. Assigning roles such as incident coordinator, forensic analyst, communications lead, and legal liaison allows the team to work together cohesively and efficiently.
Training and ongoing education play a vital role in developing and maintaining the skills of the incident response team. Team members should receive regular training on the latest threats, incident response procedures, and relevant technologies. This ensures they are equipped with the knowledge and skills needed to effectively respond to incidents.
Establishing effective communication channels and protocols is critical for the incident response team. Clear lines of communication enable rapid dissemination of information and coordination of actions during an incident. This includes both internal communication within the team and external communication with stakeholders, such as senior management, legal counsel, and external vendors.
Regular drills and tabletop exercises are valuable for assessing the readiness of the incident response team. These simulated scenarios help identify any gaps or areas for improvement in the response process. By conducting regular exercises, the team can refine their procedures and ensure a smooth and coordinated response in a real incident.
Finally, it is essential to establish a comprehensive incident response policy and documentation framework. This includes documenting incident response procedures, escalation processes, and contact information for relevant stakeholders. Having clear and well-documented policies ensures consistency and efficiency in the incident response process.
Overall, establishing an incident response team is a critical step in building a robust incident response capability. By assembling a skilled and coordinated team, organizations can effectively detect, respond to, and mitigate cyber incidents, minimizing the impact on their operations and reputation.
Developing an Incident Response Plan
Developing an incident response plan is a crucial component of effective cybersecurity management. A well-prepared and structured plan ensures that organizations can respond swiftly and efficiently to cyber incidents, minimizing their impact and facilitating a timely recovery.
The first step in developing an incident response plan is to define the objectives and scope of the plan. This involves understanding the organization’s risk tolerance and determining the types of incidents that are within the plan’s scope. This clarity helps ensure that the plan focuses on the most critical threats and aligns with the organization’s overall business objectives.
Next, the plan should outline the incident response process, including the steps to be followed from the detection of an incident through to recovery. This includes procedures for incident identification, containment, eradication, and recovery. Well-defined processes ensure that the response is organized, consistent, and effective.
Another important aspect of the incident response plan is the establishment of communication protocols and reporting procedures. This includes internal communication within the incident response team, as well as communication with key stakeholders such as executive management, legal counsel, PR, and law enforcement, if necessary. Timely and accurate communication is vital to effectively manage the incident and maintain transparency with stakeholders.
The incident response plan should also address resource allocation and coordination. This involves determining the necessary resources, such as personnel, tools, and technologies, required to execute the plan effectively. Additionally, it is essential to establish clear lines of communication and coordination between the incident response team and other relevant parties, such as IT operations, HR, and external service providers.
Furthermore, the plan should include documentation and evidence collection procedures. This ensures that all relevant information and evidence are properly documented during the incident response process. This documentation serves as valuable evidence for investigations, legal proceedings, and post-incident analysis.
Regular plan exercises and drills are critical to test the effectiveness and readiness of the incident response plan. These simulated scenarios allow the team to practice executing the plan, identify areas for improvement, and validate the response process. These exercises also help familiarize team members with their roles and responsibilities and boost their confidence in handling real incidents.
Lastly, the incident response plan should be regularly reviewed, updated, and tested to ensure its effectiveness against the evolving threat landscape. As new threats emerge or as the organization’s technology landscape changes, the plan needs to be adjusted accordingly. Regular reviews and updates ensure that the plan remains relevant and aligned with the organization’s overall cybersecurity strategy.
Preparing for the Worst: Incident Response Testing and Simulation
Preparing for the worst-case scenario is a crucial aspect of effective incident response planning. Incident response testing and simulation play a vital role in ensuring that organizations are ready to handle cyber incidents with speed and efficiency.
One key aspect of incident response testing is conducting tabletop exercises. These exercises involve realistic scenarios that simulate different types of cyber incidents. The incident response team, along with relevant stakeholders, discusses and addresses the simulated incident according to the established response plan. This exercise helps identify any gaps in the plan, test the coordination of team members, and improve the overall response process.
Red teaming exercises are another valuable testing technique. In red teaming, a group of cybersecurity professionals plays the role of attackers, attempting to breach the organization’s security controls. This exercise allows organizations to evaluate the effectiveness of their detection and response capabilities and identify potential vulnerabilities before real incidents occur.
Penetration testing is also an essential part of incident response testing. This involves authorized attempts to exploit the organization’s systems and networks to identify weaknesses and vulnerabilities. By conducting regular penetration testing, organizations can proactively address any security gaps and strengthen their overall defenses.
Another important aspect of incident response testing is the use of simulation exercises. These exercises involve realistic simulations of cyber incidents, often conducted in an isolated environment, to evaluate the response capabilities of the incident response team. Simulations help team members familiarize themselves with the tools, technologies, and processes they will use during a real incident, enhancing their preparedness and efficiency.
Organizations should also consider incorporating threat intelligence feeds and real-time incident monitoring into their testing procedures. By simulating real-world threats and monitoring system activity, organizations can evaluate the effectiveness of their threat detection and incident response mechanisms. This allows for continuous improvement and adaptation to emerging threats.
Regularly reviewing and updating the incident response plan based on the findings and lessons learned from testing exercises is essential. This ensures that the plan remains up to date and aligned with the current threat landscape. It also helps organizations stay one step ahead of attackers by continuously improving their incident response capabilities.
Ultimately, incident response testing and simulation are critical components of effective incident response preparedness. By regularly testing and exercising the response processes, organizations can identify weaknesses, improve coordination, and build the confidence and skillset required to respond swiftly and effectively in the face of a cyber incident.
Detecting Indicators of Compromise
Detecting indicators of compromise (IOCs) is a crucial aspect of effective incident response. IOCs are artifacts or evidence that suggest a system or network has been compromised by a cyber attack. Early detection of IOCs allows organizations to respond promptly and minimize the impact of the incident.
One common type of IOC is malicious software or malware. Detecting malware involves monitoring system activities, network traffic, and file integrity. Antivirus software, intrusion detection systems (IDS), and endpoint protection technologies can help identify known malware signatures or suspicious behaviors indicative of malware infection.
Unusual network traffic patterns can also be indicators of compromise. Monitoring network traffic helps detect anomalies, such as high data transfers, unusual protocols, or communication with known malicious IP addresses. Network monitoring tools, such as intrusion detection and prevention systems (IDPS), can help identify such abnormal activities.
Unexpected system behavior or system changes can also be indicative of compromise. This can include unauthorized system access, unexpected system crashes, or sudden changes in system configurations. Monitoring system logs and implementing host-based intrusion detection systems (HIDS) can help detect such irregularities.
Unusual user behavior and login activities can also signify compromise. This can include failed login attempts, unusual login locations or times, or unauthorized user privilege escalations. Implementing user behavior analytics (UBA) and robust access controls can aid in detecting unusual user activities.
Additionally, indicators of compromise can be obtained from threat intelligence feeds. These feeds provide information about known attack campaigns, malicious IP addresses, URLs, and other IOCs. By correlating network and system logs with threat intelligence, organizations can detect activities associated with known threats.
Data anomalies can also serve as indicators of compromise. This includes unusual data accesses, data exfiltration attempts, or data modifications without proper authorization. Implementing data loss prevention (DLP) tools and monitoring data flows can help detect unauthorized data activities.
Implementing security information and event management (SIEM) systems can greatly enhance IOC detection. SIEM platforms aggregate and correlate logs from various sources, providing a comprehensive view of the organization’s security posture. By analyzing the collected data, organizations can identify patterns and anomalies that may indicate compromise.
Regular vulnerability assessments and penetration testing can also help identify potential IOCs. By proactively scanning systems and networks for vulnerabilities, organizations can detect any signs of compromise, such as unauthorized open ports, unpatched software, or misconfigured systems.
Essential Tools and Technologies for Cyber Threat Detection
In today’s complex and evolving threat landscape, organizations must leverage various tools and technologies to effectively detect cyber threats and respond promptly. These essential tools and technologies play a crucial role in enhancing an organization’s cybersecurity posture.
One of the fundamental tools for threat detection is an antivirus software or endpoint protection solution. These solutions scan files and systems for known malware signatures and suspicious behaviors, helping to prevent and detect malicious software.
Intrusion Detection and Prevention Systems (IDPS) are another essential tool for threat detection. IDPS continuously monitor network traffic, analyze packets, and identify any suspicious or malicious activities, providing real-time alerts to potential threats.
Security Information and Event Management (SIEM) systems are crucial for comprehensive threat detection. SIEM solutions collect and analyze data from various sources, including network logs, system logs, and security devices, to detect and correlate anomalous activities and potential security incidents.
Network Traffic Analyzers and Packet Capture tools allow organizations to monitor network traffic in real-time and capture packets for forensic analysis. These tools provide insights into network behaviors, identify anomalies, and aid in the detection of malicious activities.
Threat Intelligence platforms are valuable tools that provide organizations with up-to-date information on emerging threats, vulnerabilities, and malicious activities. By leveraging threat intelligence feeds, organizations can stay informed about the latest threats and proactively detect potential attacks.
Security Analytics platforms combine machine learning and advanced analytics to identify patterns, anomalies, and potential threats within vast amounts of data. These platforms analyze network traffic, user behavior, and system logs to detect and respond to cyber threats.
Web Application Firewalls (WAF) help protect against web-based attacks, such as SQL injections and cross-site scripting (XSS). WAFs analyze and filter incoming web traffic to detect and block malicious activities targeting web applications.
Endpoint Detection and Response (EDR) solutions focus on monitoring and analyzing activities on endpoints such as workstations, laptops, and servers. EDR tools provide real-time visibility into endpoint activities, allowing for the early detection of potential threats and quick response.
Data Loss Prevention (DLP) software helps organizations identify and protect sensitive data by monitoring data flows and identifying potential data breaches or leaks. DLP tools can also detect and block unauthorized file transfers or communications involving sensitive information.
User and Entity Behavior Analytics (UEBA) solutions analyze patterns of user behavior, such as login activities, access privileges, and data accesses, to identify anomalous behaviors that may indicate malicious activities or insider threats.
These tools and technologies, when used in combination, provide organizations with a comprehensive threat detection and response capability. However, it is crucial to tailor the selection and deployment of these tools to the specific needs and resources of the organization, ensuring a cost-effective and efficient cybersecurity strategy.
Identifying the Role of Artificial Intelligence (AI) in Cyber Threat Detection
Artificial Intelligence (AI) is revolutionizing the field of cybersecurity and has emerged as a game-changer in cyber threat detection. AI technologies enable organizations to analyze vast amounts of data, identify patterns, and detect anomalies that may indicate potential cyber threats.
One of the primary roles of AI in cyber threat detection is its ability to automate the analysis of security logs and monitor network traffic in real-time. AI-powered systems can detect and flag suspicious activities, such as unauthorized access attempts or unusual data transfer, significantly enhancing the speed and efficiency of threat detection.
AI algorithms can also identify emerging threats by analyzing data from various sources, such as threat intelligence feeds, security reports, and historical incident data. By continuously learning and adapting to new threat patterns, AI systems can stay ahead of attackers and help organizations detect and defend against evolving cyber threats.
Machine learning, a subset of AI, plays a crucial role in cyber threat detection. Machine learning algorithms train on historical data to identify patterns and anomalies that may indicate a potential threat. These algorithms can recognize complex patterns, learn from new data, and improve over time, enabling organizations to detect and respond to previously unseen threats.
Another area where AI excels in threat detection is in the analysis of user behavior. AI algorithms can establish a baseline of normal user behavior and identify deviations that may indicate a compromised account or insider threat. By analyzing anomalous user behavior, AI can identify potential cases of fraud, data breaches, or unauthorized access attempts.
AI-powered security systems can also help prioritize threats by assessing their potential impact and severity. By analyzing various factors, such as the source of the attack, the target system, and the potential consequences, AI can assist incident response teams in focusing their efforts on high-priority threats, improving response times and resource allocation.
Additionally, AI technologies enable proactive threat hunting by continuously analyzing and correlating security events and logs. Through automated monitoring and analysis, AI systems can identify hidden threats that may go unnoticed by human analysts, allowing organizations to address vulnerabilities before they are exploited.
However, it is important to note that AI-based systems are not infallible and should be used in conjunction with human expertise. While AI can automate detection and analysis, human cybersecurity professionals are still essential in interpreting and validating AI-generated alerts, conducting deeper investigations, and making critical decisions.
Common Cyber Threats and How to Detect Them
As the threat landscape continues to evolve, organizations must stay vigilant to protect themselves from a variety of common cyber threats. Detecting these threats early is crucial to minimize potential damage and respond effectively. Here are some common cyber threats and how to detect them:
1. Phishing Attacks: Phishing attacks involve tricking individuals into revealing sensitive information or downloading malicious attachments. To detect phishing attacks, organizations should educate employees about common phishing indicators, such as suspicious email addresses, grammar errors, or urgent requests. Implementing email content filters and regularly updating antivirus software can also help detect phishing emails.
2. Ransomware: Ransomware encrypts files or entire systems, demanding a ransom for their release. Organizations should regularly back up critical data and ensure these backups are stored offline or in secured locations. Monitoring network traffic for unusual patterns and implementing strong access controls, user permissions, and application whitelisting can help detect and prevent ransomware attacks.
3. Distributed Denial of Service (DDoS) Attacks: DDoS attacks overload a system or network with an influx of traffic, resulting in service disruptions. Monitoring network traffic for sudden spikes in bandwidth utilization or network congestion can indicate a DDoS attack. Implementing network traffic analysis tools and configuring firewalls and intrusion prevention systems to detect and block suspicious traffic can also help detect these attacks.
4. Insider Threats: Insider threats involve individuals within an organization abusing their access privileges, intentionally or unintentionally. Monitoring user behavior, such as excessive data accesses or downloads, unauthorized system modifications, or unusual login activities, can help detect insider threats. Implementing user activity monitoring tools, access controls, and regular security awareness training can also aid in detecting and mitigating insider threats.
5. Malware Infections: Malware, including viruses and trojans, can infect systems and compromise data or disrupt operations. Regularly updating antivirus software and performing scans on systems and files can help detect and quarantine malware infections. Monitoring system logs for unexpected system crashes, unusual network connections, or unauthorized software installations can also indicate potential malware infections.
6. Data Breaches: Data breaches involve unauthorized access to sensitive data. Implementing intrusion detection and prevention systems (IDPS), monitoring network traffic for unusual data transfers or unauthorized access attempts, and monitoring system logs for unsuccessful login attempts can help detect data breaches early. Additionally, monitoring and analyzing access logs, implementing data loss prevention (DLP) solutions, and conducting periodic penetration tests can help identify and prevent data breaches.
7. Social Engineering: Social engineering uses human manipulation to deceive individuals and gain unauthorized access or sensitive information. Educating employees about common social engineering techniques and implementing strong authentication measures, such as multi-factor authentication, can help detect and mitigate social engineering attacks. Monitoring user behavior and implementing strict access controls can also aid in detecting and preventing unauthorized access resulting from social engineering tactics.
By staying informed about these common cyber threats and implementing proactive security measures, organizations can enhance their detection capabilities and effectively respond to potential threats in a timely manner.
Monitoring and Analyzing Network Traffic for Anomalies
Monitoring and analyzing network traffic for anomalies is a critical practice in detecting and mitigating potential cyber threats. By observing the flow of data within a network, organizations can identify unusual patterns or activities that may indicate a security breach or malicious activity.
One way to monitor network traffic is by leveraging network monitoring tools, such as intrusion detection and prevention systems (IDPS), which constantly monitor and analyze network packets. These tools can detect and flag suspicious activities, such as unauthorized network scans, unusual protocols, or large data transfers. By alerting security teams to potential threats, organizations can respond promptly and prevent further damage.
Another important aspect of network traffic monitoring is the use of security information and event management (SIEM) systems. SIEM systems aggregate and correlate logs from various network devices and applications, providing a comprehensive view of the network’s security status. By analyzing log data, organizations can identify anomalies and patterns that may indicate malicious activities, such as repeated failed login attempts or unusual data access.
Deep packet inspection (DPI) is a technique used to analyze the content of network packets in real-time. DPI enables the identification of specific application-layer protocols and allows for more granular analysis of network traffic. By examining the content of packets, organizations can detect and analyze potential threats, such as the presence of malicious code or suspicious file attachments.
Behavioral monitoring is another valuable approach to detecting network anomalies. By establishing a baseline of normal network behavior, organizations can identify deviations that may indicate malicious activities. For example, sudden spikes in network traffic, connections to untrusted or suspicious IP addresses, or a change in communication patterns can be signs of a compromise. Behavioral monitoring tools can automatically analyze network behavior and provide alerts when abnormal activities are detected.
Encryption plays a significant role in ensuring secure communication, but it can also be used to hide malicious activities. Monitoring encrypted network traffic is a challenge, but organizations can leverage advanced techniques, such as SSL/TLS decryption, to inspect encrypted traffic for potential threats. By decrypting and inspecting encrypted packets, organizations can identify and prevent malicious activities that may otherwise go undetected.
Regularly conducting network traffic analysis audits and leveraging historical data can provide valuable insights. By examining historical network traffic data, organizations can identify long-term trends, patterns, or anomalies that may indicate potential threats. This retrospective analysis enables proactive measures to strengthen network security and enhance threat detection capabilities.
Ultimately, monitoring and analyzing network traffic for anomalies is an essential practice in cybersecurity. It allows organizations to detect potential threats in real-time, respond promptly to security incidents, and prevent further damage. By implementing robust monitoring tools and techniques, organizations can stay one step ahead of cyber attackers and protect their network infrastructure and sensitive data.
Evaluating User Behavior and Privileged Access
Evaluating user behavior and privileged access is a critical aspect of maintaining a strong cybersecurity posture. Understanding how users interact with systems and managing their access privileges are key factors in detecting and preventing potential security threats.
One of the key steps in evaluating user behavior is establishing a baseline of normal behavior. By monitoring and analyzing user actions, organizations can establish patterns of typical user behavior within their systems. Deviations from this baseline can then be identified as potential security threats or signs of suspicious activity.
Implementing user activity monitoring tools can provide real-time visibility into user behavior. These tools track user actions, including file accesses, system logins, and network activities. Anomalous behavior, such as excessive data access or unauthorized system modifications, can indicate a compromised account or potential insider threat.
Privileged access, whether granted to system administrators, IT personnel, or other high-level users, requires careful evaluation. Establishing strict access controls, limiting privilege escalation, and practicing the principle of least privilege help minimize the risk associated with privileged accounts. Regularly reviewing and auditing privileged access rights helps ensure that employees have only the necessary permissions required to perform their roles.
An important aspect of evaluating user behavior is the use of user behavior analytics (UBA). UBA systems use machine learning algorithms to detect patterns and anomalies in user actions. By establishing a baseline of normal behavior and continuously assessing deviations, UBA tools can flag potentially risky behavior, such as an employee accessing sensitive data outside of their regular work hours.
Implementing multi-factor authentication (MFA) adds an extra layer of security to user accounts. By requiring additional verification methods, such as a fingerprint scan or SMS code, organizations reduce the risk of unauthorized access, even if passwords are compromised. MFA should be enforced for critical systems and privileged accounts to mitigate potential security risks.
Regularly reviewing user access privileges is crucial. This includes reviewing the permissions assigned to user accounts, removing unnecessary access privileges, and periodically re-certifying user access rights. By regularly evaluating and adjusting user access, organizations can minimize the risk of unauthorized access and potential insider threats.
Behavioral analytics and anomaly detection play a significant role in evaluating user behavior. By combining user activity logs, authentication data, and other relevant information, organizations can identify unusual or suspicious behavior that may indicate a compromised account or an insider threat. Analyzing log data and correlating it with other security events can help identify potential security incidents and expedite incident response efforts.
Lastly, security awareness training is critical for improving user behavior and minimizing security risks. Regular training sessions should educate employees on best practices for password management, identifying phishing attempts, and reporting suspicious activities. By fostering a culture of security awareness, organizations strengthen their first line of defense against cyber threats.
Evaluating user behavior and privileged access empowers organizations to detect and prevent potential security threats. By implementing robust monitoring tools, access controls, and user behavior analytics, organizations can minimize the risk of unauthorized access, insider threats, and other security breaches. Regular evaluation and adjustment of user privileges ensure that access rights are granted only when necessary and reduce the risk of compromising sensitive data or system integrity.
Leveraging Threat Intelligence for Early Detection
Leveraging threat intelligence is a crucial practice in early threat detection and proactive cybersecurity. Threat intelligence provides organizations with valuable insights into emerging threats, known vulnerabilities, and the tactics, techniques, and procedures (TTPs) employed by cybercriminals. By harnessing this intelligence, organizations can enhance their security defenses and detect potential threats before they cause significant harm.
One way to leverage threat intelligence is by subscribing to threat intelligence feeds and services. These feeds deliver timely and relevant information about the latest threats, attack campaigns, and indicators of compromise (IOCs). By integrating threat intelligence feeds into security systems, organizations can automatically cross-reference incoming network traffic, system events, and user activities against known IOCs, providing early warnings of potential malicious activities.
Open-source intelligence (OSINT) is another valuable source of threat intelligence. OSINT involves collecting and analyzing publicly available information, such as online forums, hacker communities, and social media platforms, to gain insights into potential threats. By monitoring these sources, organizations can gather information about new attack campaigns, vulnerabilities, or emerging threat actors, enabling them to enhance their defenses accordingly.
Collaborating with trusted partners and sharing threat intelligence can significantly strengthen an organization’s early threat detection capabilities. Information sharing platforms, such as Information Sharing and Analysis Centers (ISACs) or Threat Intelligence Platforms (TIPs), allow organizations to exchange relevant threat intelligence and benefit from collective knowledge. By participating in these sharing communities, organizations can gain insight into the latest threats and potential mitigation strategies.
Threat intelligence can also inform the proactive monitoring of threat actors targeting specific industries or organizations. By researching and understanding the TTPs employed by threat actors, organizations can adapt their detection and response mechanisms accordingly. This could involve monitoring for specific malware strains, observing patterns of attack campaigns, or tracking known threat actor activities.
Automation and machine learning algorithms can be utilized to process and analyze vast amounts of threat intelligence data, making it actionable and relevant for detection purposes. These technologies can categorize and prioritize threat intelligence, allowing security teams to focus on high-priority threats and respond swiftly to emerging risks.
Regularly updating and patching systems and applications based on threat intelligence recommendations is crucial for staying ahead of potential attacks. Threat intelligence often includes information on vulnerabilities and patches. By promptly applying these updates, organizations reduce the chances of exploitation by threat actors who may be targeting known vulnerabilities.
Lastly, threat intelligence should be integrated into the incident response process. By correlating incoming security events, network logs, and user activities with threat intelligence data, organizations can contextualize incidents and respond more effectively. This integration enables the identification of potential threats, quick isolation of compromised systems, and initiation of incident response actions.
By leveraging threat intelligence, organizations can gain advanced knowledge of potential threats and stay one step ahead of cybercriminals. It allows for early detection, effective incident response, and proactive defense strategies, ultimately reducing the risk of successful attacks and protecting critical assets and data.
Implementing Endpoint Detection and Response (EDR) Solutions
Implementing Endpoint Detection and Response (EDR) solutions is crucial for organizations looking to enhance their cybersecurity posture and detect potential threats at the endpoint level. EDR solutions provide real-time monitoring and response capabilities, allowing organizations to swiftly detect, investigate, and mitigate advanced threats that may infiltrate their endpoints.
EDR solutions operate by continuously monitoring endpoint devices, such as workstations, laptops, and servers, for suspicious activities and behaviors. By collecting and analyzing endpoint data, EDR solutions can detect indicators of compromise (IOCs) and identify potential threats that traditional antivirus software may miss.
One of the key features of EDR solutions is their ability to monitor endpoint behaviors and activities for unusual patterns. Through machine learning algorithms and behavioral analytics, EDR solutions establish baselines of normal endpoint behavior and identify deviations that may indicate a security breach or malicious activity.
EDR solutions also provide comprehensive visibility into endpoint activity, allowing organizations to gain insights into malicious processes, file modifications, or unauthorized system changes. This visibility extends to identifying and monitoring potentially risky behaviors, such as privilege escalation or lateral movement within the network.
Another benefit of EDR solutions is their ability to respond rapidly to detected threats. They enable organizations to investigate the root cause of incidents and enact appropriate response actions, such as isolating compromised endpoints or initiating remediation measures.
EDR solutions often leverage advanced techniques, such as file reputation analysis, sandboxing, and threat intelligence integration, to enhance their threat detection capabilities. These techniques aid in identifying known malware strains and suspicious files, analyzing their behavior in a safe environment, and correlating endpoint activities with up-to-date threat intelligence.
Implementing EDR solutions requires careful planning and configuration to ensure efficient threat detection without impacting endpoint performance. Organizations should establish clear policies and procedures for data collection, privacy, and incident response to align with industry best practices and compliance requirements.
Integration with other security solutions, such as Security Information and Event Management (SIEM) systems or Network Detection and Response (NDR) tools, is essential to create a comprehensive security ecosystem. This integration allows for the correlation of endpoint data with network events and facilitates a more coordinated and effective incident response.
EDR solutions require regular updates and continuous monitoring to remain effective against evolving threats. It is crucial to keep the system up to date with the latest threat intelligence and software patches to defend against new vulnerabilities and attack techniques.
Lastly, employee education and awareness are vital components of a successful EDR implementation. Training employees on security best practices, recognizing phishing attempts, and reporting suspicious activities can help build a strong human firewall and enhance the overall effectiveness of EDR solutions.
Overall, implementing EDR solutions plays a significant role in strengthening an organization’s endpoint security. By establishing real-time monitoring, behavioral analytics, and swift response capabilities, EDR solutions empower organizations to proactively detect and mitigate potential threats at the endpoint level, reducing the risk of successful cyberattacks.
Recognizing Signs of Data Breaches and Unauthorized Access
Data breaches and unauthorized access to sensitive information can have severe consequences for organizations, including financial loss, damage to reputation, and legal liabilities. Recognizing the signs of data breaches and unauthorized access is crucial for organizations to respond swiftly and mitigate the impact. Here are key indicators to be aware of:
1. Unusual Network Traffic: A sudden increase in network traffic or unexpected data transfers may indicate unauthorized access or exfiltration of data. Monitoring network traffic for abnormal patterns can help identify potential breaches and data leaks.
2. Unauthorized Account Access: Unexpected login attempts or user activity from unfamiliar or suspicious IP addresses can signify unauthorized access. Monitoring authentication logs and implementing multi-factor authentication can help detect and prevent unauthorized account access.
3. Privilege Escalation: Unusual changes in user permissions or unauthorized elevation of privileges can suggest an attempted compromise. Regularly reviewing and managing user access rights can help identify unauthorized privilege escalation.
4. Anomalous User Behavior: Unusual or unauthorized user actions, such as accessing sensitive data outside of regular working hours or downloading a large volume of data, may indicate compromised accounts or insider threats. Monitoring user behavior and implementing user behavior analytics (UBA) can aid in detecting such activities.
5. Unfamiliar System Modifications: Unexplained system changes, such as new user accounts, modified configurations, or deployed software not authorized by IT, can be signs of unauthorized access. Regularly reviewing system logs and implementing change management processes can help identify and prevent unauthorized modifications.
6. Unexpected Data Encryption or Data Tampering: If files or folders suddenly become encrypted or data integrity is compromised, it could indicate a ransomware attack or data tampering. Monitoring for unauthorized encryption or checksum changes can help detect such incidents.
7. Incoming Security Alerts: Notifications from intrusion detection systems (IDS), intrusion prevention systems (IPS), or security information and event management (SIEM) systems can indicate suspicious activities, indicating a potential breach. Promptly investigating and responding to security alerts is crucial for early detection and mitigation.
8. Unusual Outbound Communication: Outbound communication attempts to known malicious IP addresses, command-and-control servers, or suspicious domains can indicate a compromised system. Monitoring outbound network connections and deploying firewalls with advanced threat intelligence can help detect and block such communication.
9. Abnormal System Performance or Service Disruption: Unexpected system slowdowns, crashes, or service disruptions may be signs of a data breach or unauthorized access. Monitoring system performance and conducting regular vulnerability assessments can help identify potential security incidents.
10. Customer Complaints or Unusual Account Activity: Customer complaints about unauthorized transactions, modified account details, or unusual activity can be indicators of a data breach. Having mechanisms in place to receive and investigate customer complaints is essential in recognizing potential breaches.
Organizations should implement a robust incident response plan, regularly audit access controls, conduct vulnerability assessments, and provide security awareness training to employees. A proactive and vigilant approach to detecting signs of data breaches and unauthorized access can help organizations respond swiftly, minimize damage, and protect sensitive information.
The Role of Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems play a crucial role in modern cybersecurity by providing organizations with a centralized platform for managing and analyzing security events and data from various sources. SIEM acts as a central nervous system for security operations, enabling organizations to detect, investigate, and respond to security incidents effectively.
One of the primary functions of SIEM is log collection and correlation. SIEM systems collect log data from various sources, including network devices, servers, applications, and security appliances, and correlate this information in real-time. By aggregating and analyzing log data, SIEM enables the identification of security events and anomalies that may indicate potential threats.
SIEM enhances threat detection capabilities through advanced analytics and correlation rules. It applies predefined correlation rules to analyze event patterns and identify potential security incidents. SIEM systems can also leverage machine learning and behavioral analytics to detect anomalies and recognize abnormalities in user behavior, network traffic, or system activities.
Real-time alerting and notification is another essential feature of SIEM. When a potential security incident is identified, SIEM systems generate alerts, enabling security teams to respond promptly. Alerts can be configured based on predefined rules or customized thresholds, ensuring that security events requiring immediate attention are promptly communicated to the appropriate personnel.
Incident response and forensics are facilitated by the capabilities of SIEM systems. SIEM provides a historical record of security events and log data, allowing for the investigation of past incidents. This data can help identify the root cause of an incident, understand its scope and impact, and aid in the development of appropriate response measures.
Compliance reporting and auditing are simplified by SIEM systems. Many regulatory frameworks require organizations to demonstrate compliance by collecting and analyzing security event logs. SIEM systems provide the necessary tools and capabilities to generate reports, track user activity, and facilitate audits, ensuring adherence to industry regulations and compliance requirements.
Integrating various security technologies with SIEM enhances its capabilities. SIEM can ingest data from intrusion detection and prevention systems (IDPS), firewalls, antivirus software, and other security solutions, consolidating information from multiple sources. This integration enables security teams to view a comprehensive, correlated picture of the organization’s security posture and quickly respond to threats.
Threat intelligence integration is another critical aspect of SIEM functionality. By incorporating threat feeds and intelligence data into the SIEM platform, organizations gain real-time insights into emerging threats, known vulnerabilities, and indicators of compromise (IOCs). This integration enhances the ability to detect and respond to potential threats in a more proactive manner.
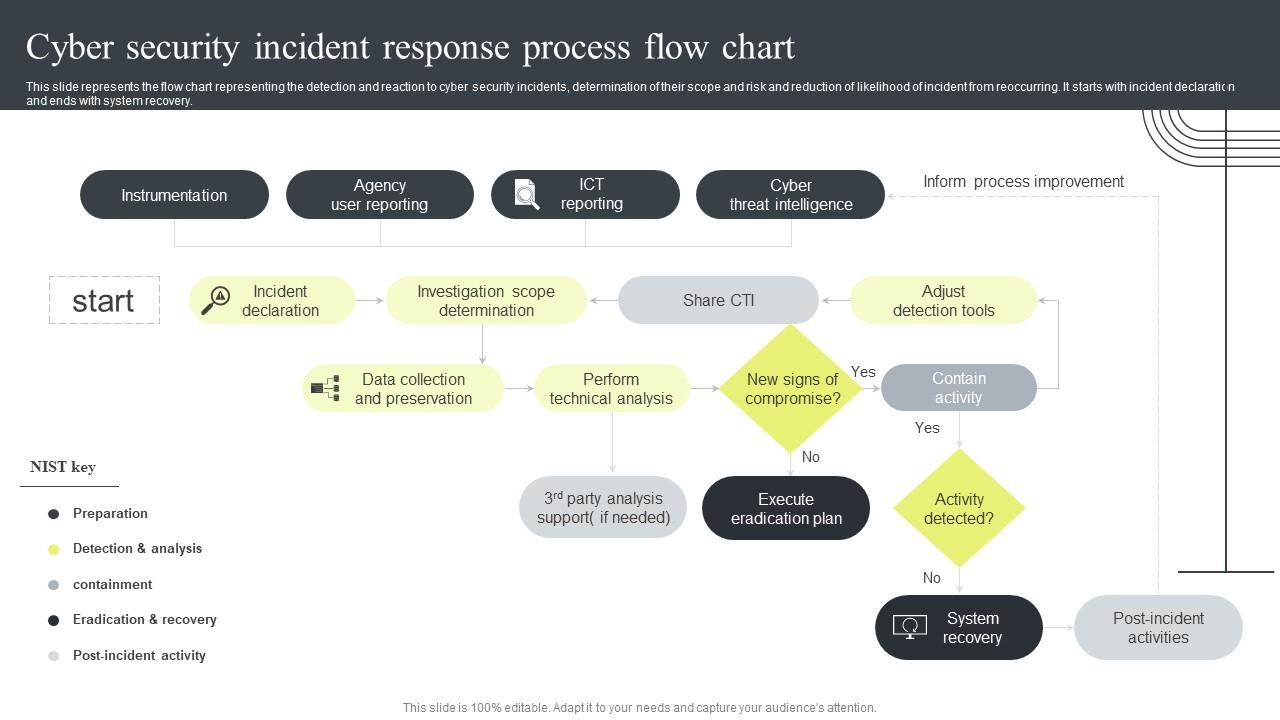
Responding to a Detected Cyber Threat: Incident Response Procedures
Responding to a detected cyber threat effectively is crucial to minimizing the impact on an organization’s operations, reputation, and sensitive data. Incident response procedures outline the necessary steps and actions to be taken when a cyber threat is identified, enabling organizations to respond promptly and mitigate potential damage.
The first step in incident response is to activate the incident response team and establish clear lines of communication. This includes notifying key stakeholders, such as executive management, IT personnel, legal counsel, and relevant third-party vendors. Prompt communication ensures that all necessary parties are aware of the incident and can coordinate their response efforts.
Once the incident is identified, the immediate priority is to contain and isolate the threat to prevent further damage. This may involve disconnecting affected systems from the network, disabling compromised user accounts, or quarantining infected files. By containing the incident, organizations limit its potential impact and restrict the attacker’s ability to access critical resources.
Simultaneously, the incident response team should conduct an investigation to identify the root cause and extent of the incident. This involves analyzing system logs, examining network traffic, and reviewing any available forensic evidence. The goal is to understand how the threat actor infiltrated the system, what information may have been compromised, and if any indicators of a broader breach exist.
During the investigation, evidence preservation is critical. This includes capturing and documenting all relevant information, such as screenshots, log files, and network traffic captures. Preserving evidence ensures that it is available for further analysis, potential law enforcement involvement, or legal action.
Once the investigation is complete, the incident response team must make informed decisions on remediation and recovery. This includes developing a plan to remove the threat from the system, patch any vulnerabilities, restore affected systems from backups, and implement measures to prevent a similar incident from occurring in the future.
Communication remains vital throughout the incident response process. Regular updates to stakeholders, including executive management, employees, customers, and regulatory authorities (if required), help manage expectations and maintain transparency. Clear and timely communication builds trust and confidence among stakeholders during challenging situations.
Post-incident activities are equally important. Conducting a post-incident review and analysis enables organizations to identify lessons learned, document improvements, and refine incident response procedures. This includes evaluating the effectiveness of the response, assessing any deficiencies or gaps, and implementing necessary changes to enhance future incident response capabilities.
Organizations should also consider reporting the incident to the appropriate authorities, such as law enforcement or regulatory agencies, as required by legal obligations or industry regulations. Reporting incidents not only helps in potential investigations but also contributes to a broader collective effort to combat cybercrime.
Regular testing and evaluation of incident response procedures are integral to maintaining an effective cybersecurity posture. Conducting periodic drills and tabletop exercises allows the incident response team to practice their roles, refine their procedures, and continuously improve the organization’s ability to respond to future cyber threats.
Overall, incident response procedures are designed to guide organizations through the critical steps necessary to respond to a detected cyber threat effectively. By following established procedures, organizations can mitigate the impact of incidents, minimize the potential damage, and strengthen their overall cybersecurity resilience.
Incident Containment and Damage Control
Incident containment and damage control are critical components of effective incident response, aimed at minimizing the impact of a cyber threat on an organization’s systems, data, and operations. Successful containment and control measures are essential to prevent further compromise and mitigate potential damage.
The first step in incident containment is to isolate the affected systems or network segments to prevent the spread of the threat. By disconnecting compromised systems from the network or segmenting affected areas, organizations limit the potential impact and block further unauthorized access or data exfiltration.
Once containment is achieved, organizations can focus on damage control. This involves assessing the extent of the damage, both immediate and potential, caused by the incident. For example, determining if sensitive data has been compromised, if systems have been rendered inaccessible, or if critical business operations have been disrupted.
Damage control strategies may include restoring systems from clean backups, applying software patches or updates to close vulnerabilities, or mitigating the impact caused by an unauthorized access incident. Additionally, organizations should consider implementing temporary measures to ensure business continuity while the investigation and remediation process takes place.
During the incident response, it is critical to document all relevant information related to the incident. This includes logging activities, capturing screenshots, preserving forensic evidence, and maintaining a detailed timeline of the incident. Proper documentation is essential for ongoing analysis, potential legal proceedings, and post-incident analysis to prevent similar incidents in the future.
Communication is vital during the incident containment and damage control phase. Relevant stakeholders, such as executive management, IT personnel, legal counsel, and public relations teams, should be kept informed about the incident, its impact, and the steps being taken to mitigate the damage. Transparent and consistent communication helps manage expectations and maintain trust with stakeholders.
Organizations should conduct thorough analysis and forensic investigations to identify the root cause of the incident and determine the extent of the damage. This includes examining logs, examining network traffic, analyzing compromised systems, and exploring any indicators of a broader breach. The findings from investigations provide valuable insights into vulnerabilities, attack vectors, or potential areas of improvement to enhance future incident response capabilities.
Regular monitoring and ongoing assessment of systems and networks are essential to ensure that the incident response measures remain effective and that new vulnerabilities or threats are promptly addressed. Organizations should evaluate their security controls, patch management processes, employee training, and overall security posture to identify areas for improvement and implement necessary changes.
Incident containment and damage control should be followed by a post-incident review and analysis, where organizations assess the effectiveness of their incident response procedures. This includes evaluating the response’s timeliness, identifying areas of improvement, and refining incident response plans to enhance future incident response capabilities. Lessons learned from the incident should be documented, and recommendations for preventive measures or process enhancements should be implemented.
Incident containment and damage control are critical for mitigating the impact of a cyber threat. By promptly isolating compromised systems, assessing and mitigating the damage caused, and continuously improving incident response capabilities, organizations can minimize the impact of incidents and enhance their overall cybersecurity resilience.
Investigating the Incident: Documentation and Analysis
Investigating a cyber incident is a crucial step in the incident response process, allowing organizations to gather critical information about the incident, understand the scope of the compromise, and facilitate a comprehensive response. Proper documentation and thorough analysis are key components of the investigation, helping to identify the root cause and mitigate future incidents.
Documentation is essential throughout the investigation process. Detailed records should be kept of all relevant information, including the nature of the incident, the systems or networks affected, the date and time of the incident, and any initial observations. Recording this information ensures that crucial details are preserved, contributing to the accuracy and integrity of the investigation.
Timelines play a crucial role in documenting the incident. Creating a timeline of events helps establish the sequence of activities, identify potential entry points, and highlight any significant changes or actions taken during the incident. A clear and accurate timeline serves as a valuable resource during the investigation and facilitates comprehensive reporting.
Forensic evidence preservation is a critical aspect of the investigation. This involves collecting and documenting evidence from various sources, such as system logs, network traffic captures, and file system metadata. Preserving evidence ensures that it is available for further analysis, potential legal proceedings, or collaboration with law enforcement authorities. Chain of custody protocols should be followed to maintain the integrity and admissibility of the evidence.
Thorough analysis of the incident data is essential to understand the attack vectors, identify vulnerabilities or weaknesses exploited by the attacker, and determine the extent of the compromise. This can involve examining system logs, network traffic, firewall configurations, and any other relevant sources of data. Analysis techniques may include correlation of events, pattern recognition, and detection of abnormalities or deviations from normal behavior.
Collaboration and information sharing are instrumental in incident investigations. Internal and external stakeholders, such as IT teams, security providers, or industry peers, should be involved in the analysis to leverage their expertise and perspectives. Sharing information and collaborating can expedite the investigation process, reveal additional insights, and strengthen an organization’s overall cybersecurity posture.
Communication and reporting are critical during the investigation phase. Regular updates should be provided to key stakeholders, including executive management, IT teams, legal counsel, and any other relevant parties. Clear and concise reporting ensures that the investigation findings are effectively communicated, allowing decision-makers to make informed choices regarding incident response, mitigation measures, and potential notifications.
Post-incident analysis is an integral part of the investigation process. Evaluating the effectiveness of the response, identifying areas for improvement, and implementing necessary changes help enhance incident response capabilities. Lessons learned from the analysis should be documented and incorporated into incident response plans to prevent similar incidents in the future.
Proper documentation and thorough analysis during an incident investigation are vital for understanding the scope and impact of a cyber incident. By accurately capturing critical information, preserving forensic evidence, conducting comprehensive analysis, and sharing findings with relevant stakeholders, organizations can facilitate effective incident response, strengthen their security defenses, and mitigate future incidents.
Post-Incident Actions: Remediation and Recovery
Post-incident actions are crucial for organizations to recover and remediate after a cyber incident. Once the immediate threat is contained and the investigation is complete, organizations should focus on remediation and recovery efforts. These actions involve addressing vulnerabilities, restoring affected systems, and implementing measures to prevent similar incidents in the future.
Remediation starts with identifying the root cause of the incident, often revealed during the investigation. This involves understanding the attack vectors, vulnerabilities, or weaknesses that allowed the incident to occur. By patching vulnerabilities, addressing misconfigurations, or implementing additional security controls, organizations can mitigate the risk of a similar incident happening again.
Restoring affected systems and data is a critical step in the recovery process. This may involve restoring systems from clean backups, verifying data integrity, and ensuring that all systems and applications are functioning correctly. Organizations should follow incident response and disaster recovery plans to systematically restore operations to their pre-incident state.
Strong password reset policies should be enforced to prevent unauthorized access using compromised credentials. Passwords for affected accounts, as well as those within the scope of the incident, should be reset to ensure the security of those accounts. Implementing multi-factor authentication and regular password rotation practices can further enhance security measures.
Recovery efforts should also involve improving monitoring and detection capabilities. By enhancing intrusion detection systems, security event monitoring, and log analysis, organizations can better detect and respond to potential incidents in real-time. Continuous monitoring and analysis provide valuable insights into ongoing threats and allow for swift action.
Employee training and awareness programs should be reinforced to educate users about the incident, share lessons learned, and increase cybersecurity awareness. Training should cover policies and best practices for data handling, email and web browsing security, password hygiene, and incident reporting. Regular training keeps employees informed and ensures they remain an active line of defense against future incidents.
Regulatory requirements and legal obligations should be addressed during the post-incident phase. Organizations must assess if they are obligated to report the incident to regulatory bodies, industry-specific authorities, or affected individuals. The incident response team should work closely with legal counsel to understand the reporting requirements and navigate the compliance landscape appropriately.
Lessons learned from the incident and analysis should be incorporated into incident response plans and risk management strategies. Organizations should document the specifics of the incident, the response actions taken, and the outcomes to create a reference for future incidents. Adjustments and improvements to policies, procedures, and technologies should be made to enhance incident response capabilities and strengthen overall security posture.
Post-incident actions should conclude with a post-mortem review and analysis conducted by the incident response team. This evaluation involves assessing the effectiveness of the response, identifying areas for improvement, and refining incident response plans. The review should be comprehensive, addressing both technical and procedural aspects, and serve as a foundation for continual improvement.
By promptly addressing vulnerabilities, restoring affected systems, implementing stronger safeguards, and learning from incidents, organizations can recover and strengthen their resilience. Effective remediation and recovery efforts minimize the impact of incidents, improve overall security, and prepare organizations for future cyber threats.